Docker container network configuration
http://xmodulo.com/networking-between-docker-containers.html
How to set up networking between Docker containers
As you may be aware, Docker container technology has emerged as a viable lightweight alternative to full-blown virtualization. There are a growing number of use cases of Docker that the industry adopted in different contexts, for example, enabling rapid build environment, simplifying configuration of your infrastructure, isolating applications in multi-tenant environment, and so on. While you can certainly deploy an application sandbox in a standalone Docker container, many real-world use cases of Docker in production environments may involve deploying a complex multi-tier application in an ensemble of multiple containers, where each container plays a specific role (e.g., load balancer, LAMP stack, database, UI).
There comes the problem of Docker container networking: How can we interconnect different Docker containers spawned potentially across different hosts when we do not know beforehand on which host each container will be created?
One pretty neat open-source solution for this is weave. This tool makes interconnecting multiple Docker containers pretty much hassle-free. When I say this, I really mean it.
In this tutorial, I am going to demonstrate how to set up Docker networking across different hosts using weave.
How Weave Works
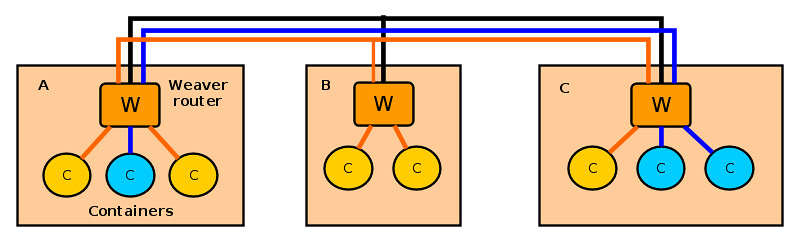
Let's first see how weave works. Weave creates a network of "peers", where each peer is a virtual router container called "weave router" residing on a distinct host. The weave routers on different hosts maintain TCP connections among themselves to exchange topology information. They also establish UDP connections among themselves to carry inter-container traffic. A weave router on each host is then connected via a bridge to all other Docker containers created on the host. When two containers on different hosts want to exchange traffic, a weave router on each host captures their traffic via a bridge, encapsulates the traffic with UDP, and forwards it to the other router over a UDP connection.
Each weave router maintains up-to-date weave router topology information, as well as container's MAC address information (similar to switch's MAC learning), so that it can make forwarding decision on container traffic. Weave is able to route traffic between containers created on hosts which are not directly reachable, as long as two hosts are interconnected via an intermediate weave router on weave topology. Optionally, weave routers can be set to encrypt both TCP control data and UDP data traffic based on public key cryptography.
Prerequisite
Before using weave on Linux, of course you need to set up Docker environment on each host where you want to run Docker containers. Check out these tutorials on how to create Docker containers on Ubuntu or CentOS/Fedora.
Once Docker environment is set up, install weave on Linux as follows.
$ chmod a+x weave
$ sudo cp weave /usr/local/bin
Make sure that /usr/local/bin is include in your PATH variable by appending the following in /etc/profile.
export PATH="$PATH:/usr/local/bin"
Repeat weave installation on every host where Docker containers will be deployed.
Weave uses TCP/UDP 6783 port. If you are using firewall, make sure that these port numbers are not blocked by the firewall.
Launch Weave Router on Each Host
When you want to interconnect Docker containers across multiple hosts, the first step is to launch a weave router on every host.
On the first host, run the following command, which will create and start a weave router container.
The first time you run this command, it will take a couple of minutes to download a weave image before launching a router container. On successful launch, it will print the ID of a launched weave router.
To check the status of the router, use this command:
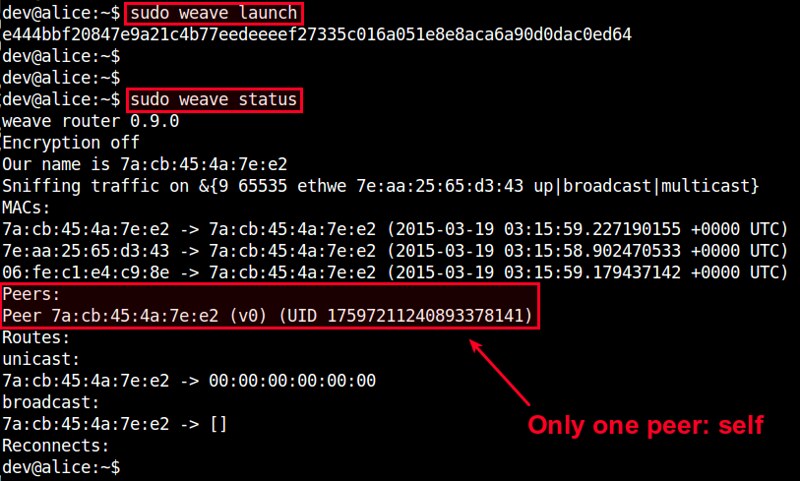
Since this is the first weave router launched, there will be only one peer in the peer list.
You can also verify the launch of a weave router by using docker command.

On the second host, run the following command, where we specify the IP address of the first host as a peer to join.
When you check the status of the router, you will see two peers: the current host and the first host.
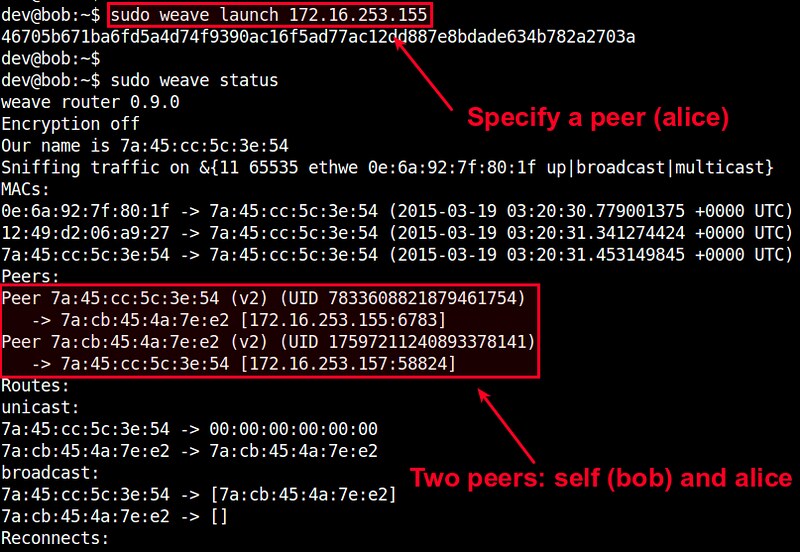
As you launch more routers on subsequent hosts, the peer list will grow accordingly. When launching a router, just make sure that you specify any previously launched peer's IP address.
At this point, you should have a weave network up and running, which consists of multiple weave routers across different hosts.
Interconnect Docker Containers across Multiple Hosts
Now it is time to launch Docker containers on different hosts, and interconnect them on a virtual network.
Let's say we want to create a private network 10.0.0.0/24, to interconnect two Docker containers. We will assign random IP addressses from this subnet to the containers.
When you create a Docker container to deploy on a weave network, you need to use weave command, not dockercommand. Internally, the weave command uses docker command to create a container, and then sets up Docker networking on it.
Here is how to create a Ubuntu container on hostA, and attach the container to 10.0.0.0/24 subnet with an IP addresss 10.0.0.1.
On successful run, it will print the ID of a created container. You can use this ID to attach to the running container and access its console as follows.
Move to hostB, and let's create another container. Attach it to the same subnet (10.0.0.0/24) with a different IP address 10.0.0.2.
Let's attach to the second container's console as well:
At this point, those two containers should be able to ping each other via the other's IP address. Verify that from each container's console.
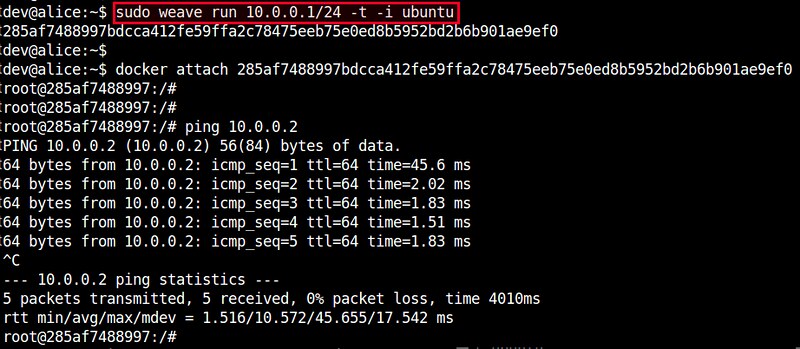
If you check the interfaces of each container, you will see an interface named "ethwe" which is assigned an IP address (e.g., 10.0.0.1 and 10.0.0.2) you specified.
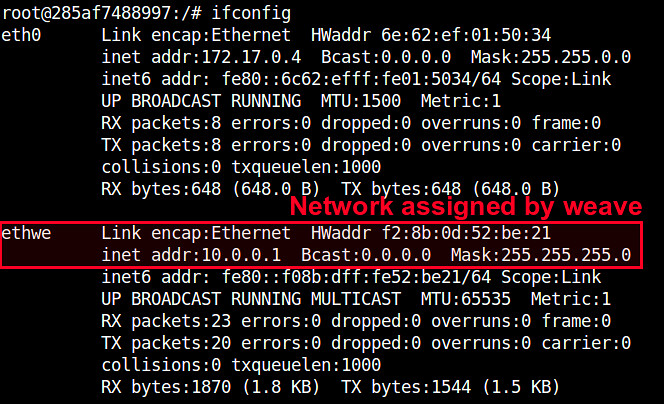
Other Advanced Usages of Weave
Weave offers a number of pretty neat features. Let me briefly cover a few here.
Application Isolation
Using weave, you can create multiple virtual networks and dedicate each network to a distinct application. For example, create 10.0.0.0/24 for one group of containers, and 10.10.0.0/24 for another group of containers, and so on. Weave automatically takes care of provisioning these networks, and isolating container traffic on each network. Going further, you can flexibly detach a container from one network, and attach it to another network without restarting containers. For example:
First launch a container on 10.0.0.0/24:
Detach the container from 10.0.0.0/24:
Re-attach the container to another network 10.10.0.0/24:

Now this container should be able to communicate with other containers on 10.10.0.0/24. This is a pretty useful feature when network information is not available at the time you create a container.
Integrate Weave Networks with Host Network
Sometimes you may need to allow containers on a virtual weave network to access physical host network. Conversely, hosts may want to access containers on a weave network. To support this requirement, weave allows weave networks to be integrated with host network.
For example, on hostA where a container is running on network 10.0.0.0/24, run the following command.
This will assign IP address 10.0.0.100 to hostA, so that hostA itself is also connected to 10.0.0.0/24 network. Obviously, you need to choose an IP address which is not used by any other containers on the network.
At this point, hostA should be able to access any containers on 10.0.0.0/24, whether or not the containers are residing on hostA. Pretty neat!
Conclusion
As you can see, weave is a pretty useful Docker networking tool. This tutorial only covers a glimpse of its powerful features. If you are more ambitious, you can try its multi-hop routing, which can be pretty useful in multi-cloud environment, dynamic re-routing, which is a neat fault-tolerance feature, or even its distributed DNS service which allows you to name containers on weave networks. If you decide to use this gem in your environment, feel free to share your use case!
Docker container network configuration的更多相关文章
- docker的网络-Container network interface(CNI)与Container network model(CNM)
Overview 目前围绕着docker的网络,目前有两种比较主流的声音,docker主导的Container network model(CNM)和社区主导的Container network in ...
- Docker Network Configuration 高级网络配置
Network Configuration TL;DR When Docker starts, it creates a virtual interface named docker0 on the ...
- 【Network】Calico, Flannel, Weave and Docker Overlay Network 各种网络模型之间的区别
From the previous posts, I have analysed 4 different Docker multi-host network solutions - Calico, F ...
- Docker: docker container常用命令实战
容器管理,容器常用选项 选项 描述 -i, –interactive 交互式 -t, –tty 分配一个伪终端 -d, –detach 运行容器到后台 -e, –env 设置环境变量 -p, –pub ...
- Docker4Windows -- 从外部(非本机host)访问 由docker container运行的程序
背景 当我们在windows 上面运行docker container的时候,我们需要借助于模拟器(例如,Virtual box/Hyper V),她的目的主要是在我们的windows系统上面模拟出一 ...
- bridge br0 docker 网络问题 Docker Container与Docker Host
Docker学习笔记:Docker 网络配置 - docker ppt - docker中文社区http://www.docker.org.cn/dockerppt/111.html Bridge t ...
- Docker源码分析(八):Docker Container网络(下)
1.Docker Client配置容器网络模式 Docker目前支持4种网络模式,分别是bridge.host.container.none,Docker开发者可以根据自己的需求来确定最适合自己应用场 ...
- Docker源码分析(七):Docker Container网络 (上)
1.前言(什么是Docker Container) 如今,Docker技术大行其道,大家在尝试以及玩转Docker的同时,肯定离不开一个概念,那就是“容器”或者“Docker Container”.那 ...
- (转)Docker - 创建 Docker overlay network (containers 通信)
原文链接: http://www.cnblogs.com/AlanWalkOn/p/6101875.html --- 创建基于Key-Value的Docker overlay network. 这样运 ...
随机推荐
- 【HDOJ】4162 Shape Number
循环串的最小表示法. /* */ #include <iostream> #include <string> #include <map> #include < ...
- FRM-40401 No changes to save error
FAQ: I have updated a table from the form and written a update statement in the when-button-pressed ...
- JQuery datepicker 用法
JQuery datepicker 用法 jQuery UI很强大,其中的日期选择插件Datepicker是一个配置灵活的插件,我们可以自定义其展示方式,包括日期格式.语言.限制选择日期范围.添加 ...
- 如何使用eclipse进行嵌入式Linux的开发
如何使用eclipse进行嵌入式Linux的开发 作者:曾宏安,华清远见嵌入式学院高级讲师. 如何使用eclipse进行嵌入式Linux的开发 习惯了在windows环境下开发的程序员在转到Linux ...
- FZU2236 第十四个目标 dp+树状数组优化
分析:这种题烂大街,n^2,然后数据结构优化下到nlogn,离散化 #include <cstdio> #include <cstring> #include <queu ...
- VS2010+WINDBG+VMWARE9.0和fatal error RC1106: invalid option: -ologo错误
提供属性配置文件一份: http://pan.baidu.com/s/1iS1Ix <?xml version="1.0" encoding="utf-8" ...
- 【JS】Intermediate8:jQuery:AJAX
1.$.ajax is the main method, allowing you to manually construct your AJAX request 2.eg: gets some da ...
- HDU3727 - Jewel(主席树)
题目大意 对一个序列进行以下四种操作: 1.Insert x 在序列尾部插入x 2.Query_1 s t k 查询区间[s,t]的第k小 3.Query_2 x 查询x的在序列中排名 4.Query ...
- 问题-Delphi不能进行调试模式
问题现象:delphi不能进行调试模式 问题原因:可能是防火墙的原因,我有一次在电脑清理时,把delphi的调试程序名放在了360的黑名单中,按F9后,无法调试. 问题处理:你懂的(要不白名单,要不你 ...
- Android学习之 博客专栏 与 资料
android | Android Developers Android学习系列 - 谦虚的天下 - 博客园 android基础 - 生如夏花之灿烂 - 博客园 Android开发 - 皓月繁星 - ...
