ICMP隐蔽隧道攻击分析与检测(四)
• ICMP隧道攻击通讯特征和特征提取
一、ICMP Ping正常通讯特征总结
- 一个正常的 ping 每秒最多只会发送两个数据包,而使用 ICMP隧道的服务器在同一时间会产生大量 ICMP 数据包
- 正常的icmp数据包里,请求数据包与对应的响应数据包内容一样
- 数据包中payload的大小固定,Windows下为32bytes,Linux下为48bytes
- 数据包中payload的内容固定,Windows下为 "abcdefghijklmnopqrstuvwabcdefghi" ,Linux下为 " !”#$%&’()+,-./01234567" ,如果指定ping发送的长度,则为不断重复的固定字符串
- type类型只有2种,8和0,8为请求数据,0为响应数据
二、ICMP隧道攻击通讯特征总结
- 一个正常的 ping 每秒最多只会发送两个数据包,而使用 ICMP 隧道的服务器在同一时间会产生大量 ICMP 数据包
- 请求数据包与对应的响应数据包内容不一样
- 数据包中 payload 的大小可以是任意大小,通常大于64bytes,当然 icmptunnel 可以配置限制所有数据包的 payload 为64bytes
- 个别ICMP隧道工具产生的数据包内容前面会增加 'TUNL' 标记以用于识别隧道
三、ICMP隧道攻击检测思路
- 检测同一来源数据包的数量:正常ping每秒只会发送2个数据包,而ICMP隧道可以每秒发送多个
- 检测数据包中 Payload 的大小:正常ping产生的数据包Payload的大小是固定的,而ICMP隧道数据包大小可以任意
- 检测响应数据包中 Payload 跟请求数据包是否不一致:正常Ping产生的数据包请求响应内容一致,而ICMP隧道请求响应数据包基本不一致
- 检测数据包中 Payload 的内容:正常ping产生的Payload为固定字符串,ICMP隧道的payload可以为任意
- 检测数据包的协议标签可能存在特殊字段:icmptunnel 会在所有的 ICMP Data 前面增加 'TUNL' 标记以用于识别隧道
- 检测数据包 ICMP Data 里面可能存在一些系统命令:'whoami','ls','ipconfig',......
四、IDS检测规则落地
1、禁止 ping ???
2、ICMP Data 字段形成一个白名单,不在白名单内的告警
pass: 匹配到规则后,suricata停止扫描数据包,并跳到所有规则末尾(仅针对当前数据包)
dsize: 匹配一个指定payload大小的数据包
itype: 匹配指定的ICMP类型值
icode: 匹配指定的ICMP代码值
nocase: 匹配内容不区分大小写
pass icmp any any -> any any (msg:"Whitecap: OSX or Linux ICMP Echo Request"; icode:0; itype:8; dsize:56; content:"!\"#$%&'()*+,-./01234567"; classtype:misc-activity; sid:5110001; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: OSX or Linux ICMP Echo Reply"; icode:0; itype:0; dsize:56; content:"!\"#$%&'()*+,-./01234567"; classtype:misc-activity; sid:5110002; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Windows XP/7/8 ICMP Echo Request"; icode:0; itype:8; dsize:32; content:"abcdefghijklmnopqrstuvwabcdefghi"; classtype:misc-activity; sid:5110003; rev:1; nocase;)
pass icmp any any -> any any (msg:"Whitecap: Windows XP/7/8 ICMP Echo Reply"; icode:0; itype:0; dsize:32; content:"abcdefghijklmnopqrstuvwabcdefghi"; classtype:misc-activity; sid:5110004; rev:1; nocase;)
pass icmp any any -> any any (msg:"Whitecap: Nmap ICMP Echo Request"; icode:0; itype:8; dsize:0; classtype:misc-activity; sid:5110005; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Nmap ICMP Echo Reply"; icode:0; itype:0; dsize:0; classtype:misc-activity; sid:5110006; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Group Policy Slow Link Detection"; icode:0; itype:8; dsize:>1400; content:"WANG2"; classtype:misc-activity; sid:5110007; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Group Policy Slow Link Detection"; icode:0; itype:0; dsize:>1400; content:"WANG2"; classtype:misc-activity; sid:5110008; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Solarwinds Status Query"; icode:0; itype:8; dsize:23; content:"SolarWinds Status Query"; classtype:misc-activity; sid:5110009; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Solarwinds Status Query"; icode:0; itype:0; dsize:23; content:"SolarWinds Status Query"; classtype:misc-activity; sid:5110010; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Domain Controller ICMP Traffic"; icode:0; itype:8; dsize:1; content:"?"; classtype:misc-activity; sid:5110011; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Domain Controller ICMP Traffic"; icode:0; itype:0; dsize:1; content:"?"; classtype:misc-activity; sid:5110012; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: McAfee ICMP ping Request"; icode:0; itype:8; dsize:36; content:"EEEEEEEEEEEEEEEEEEEEEEEEEEEEEEE"; offset:3; classtype:misc-activity; sid:5110013; rev:2;)
pass icmp any any -> any any (msg:"Whitecap: McAfee ICMP ping Reply"; icode:0; itype:0; dsize:36; content:"EEEEEEEEEEEEEEEEEEEEEEEEEEEEEEE"; offset:3; classtype:misc-activity; sid:5110014; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Lots of Xs"; icode:0; itype:8; dsize:32; content:"xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"; classtype:misc-activity; sid:5110015; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Lots of Xs"; icode:0; itype:0; dsize:32; content:"xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"; classtype:misc-activity; sid:5110016; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: DHCP ICMP Duplicate IP Check"; icode:0; itype:8; dsize:11; content:"DhcpIcmpChk"; classtype:misc-activity; sid:5110017; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: DHCP ICMP Duplicate IP Check"; icode:0; itype:0; dsize:11; content:"DhcpIcmpChk"; classtype:misc-activity; sid:5110018; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Solarwinds ICMP Version 5"; icode:0; itype:8; dsize:<80; content:"SolarWinds.Net ICMP Version 5.0.4.16Copyright 1995-2005 SolarWinds.Net"; classtype:misc-activity; sid:5110019; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Solarwinds ICMP Version 5"; icode:0; itype:0; dsize:<80; content:"SolarWinds.Net ICMP Version 5.0.4.16Copyright 1995-2005 SolarWinds.Net"; classtype:misc-activity; sid:5110020; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Solarwinds Sonar ICMP Scan"; icode:0; itype:8; dsize:24; content:"Orion Network Sonar Scan"; classtype:misc-activity; sid:5110021; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: Solarwinds Sonar ICMP Scan"; icode:0; itype:0; dsize:24; content:"Orion Network Sonar Scan"; classtype:misc-activity; sid:5110022; rev:1;)
pass icmp any any -> $DNS_SERVERS any (msg:"Whitecap: ICMP to DNS Servers"; icode:0; itype:8; dsize:<57; classtype:misc-activity; threshold:type limit, track by_src, count 1, seconds 60; sid:5110500; rev:2;)
pass icmp any any -> $DNS_SERVERS any (msg:"Whitecap: ICMP to DNS Servers"; icode:0; itype:0; dsize:<57; classtype:misc-activity; threshold:type limit, track by_src, count 1, seconds 60; sid:5110501; rev:2;)
pass icmp any any -> any any (msg:"Whitecap: Domain controller to domain controller"; icode:0; itype:8; dsize:32; content:"|00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00|"; classtype:misc-activity; threshold:type limit, track by_src, count 1, seconds 60; sid:5110502; rev:2;)
pass icmp any any -> any any (msg:"Whitecap: Domain controller to domain controller"; icode:0; itype:0; dsize:32; content:"|00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00|"; classtype:misc-activity; threshold:type limit, track by_src, count 1, seconds 60; sid:5110503; rev:2;)
pass icmp any any -> any any (msg:"Whitecap: All As"; icode:0; itype:8; dsize:64; content:"|AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA|"; classtype:misc-activity; sid:5110504; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: All As"; icode:0; itype:0; dsize:64; content:"|AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA|"; classtype:misc-activity; sid:5110505; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: All 0s"; icode:0; itype:8; dsize:56; content:"|00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00|"; classtype:misc-activity; sid:5110506; rev:1;)
pass icmp any any -> any any (msg:"Whitecap: All 0s"; icode:0; itype:0; dsize:56; content:"|00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00|"; classtype:misc-activity; sid:5110507; rev:1;)
pass icmp [$ICMP_SRC_HOSTS_IGNORE] any -> any any (msg:"ICMP Pass: Ignore Hosts"; icode:0; itype:8; classtype:misc-activity; sid:5111000; rev:1;)
pass icmp [$ICMP_SRC_HOSTS_IGNORE] any -> any any (msg:"ICMP Pass: Ignore Hosts"; icode:0; itype:0; classtype:misc-activity; sid:5111001; rev:1;)
pass icmp any any -> [$ICMP_DST_HOSTS_IGNORE] any (msg:"ICMP Pass: Ignore Hosts"; icode:0; itype:8; classtype:misc-activity; sid:5111002; rev:1;)
pass icmp any any -> [$ICMP_DST_HOSTS_IGNORE] any (msg:"ICMP Pass: Ignore Hosts"; icode:0; itype:0; classtype:misc-activity; sid:5111003; rev:1;)
3, 检测包大于多少,或者发送频率高于某个数,报警
alert icmp any any -> any any (msg:"Whitecap Echo Request Payload > 100 bytes"; icode:0; itype:8; dsize:>100; classtype:misc-activity; sid:5113000; rev:1;)
alert icmp any any -> any any (msg:"Whitecap Echo Reply Payload > 100 bytes"; icode:0; itype:0; dsize:>100; classtype:misc-activity; sid:5113001; rev:1;)
4、检测 Data 里面包含的特殊字段报警(例如检测 base64、操作系统常见命令等)
alert icmp any any -> any any (msg:"LOCAL ICMP Large ICMP Packet (Base64)"; dsize:>800; content:"="; pcre:"/^(?:[A-Za-z0-9+/]{4})*(?:[A-Za-z0-9+/]{2}==|[A-Za-z0-9+/]{3}=|[A-Za-z0-9+/]{4})$/"; classtype:misc-activity; sid:1000028; rev:1;)
五、基于统计分析ICMP隧道攻击
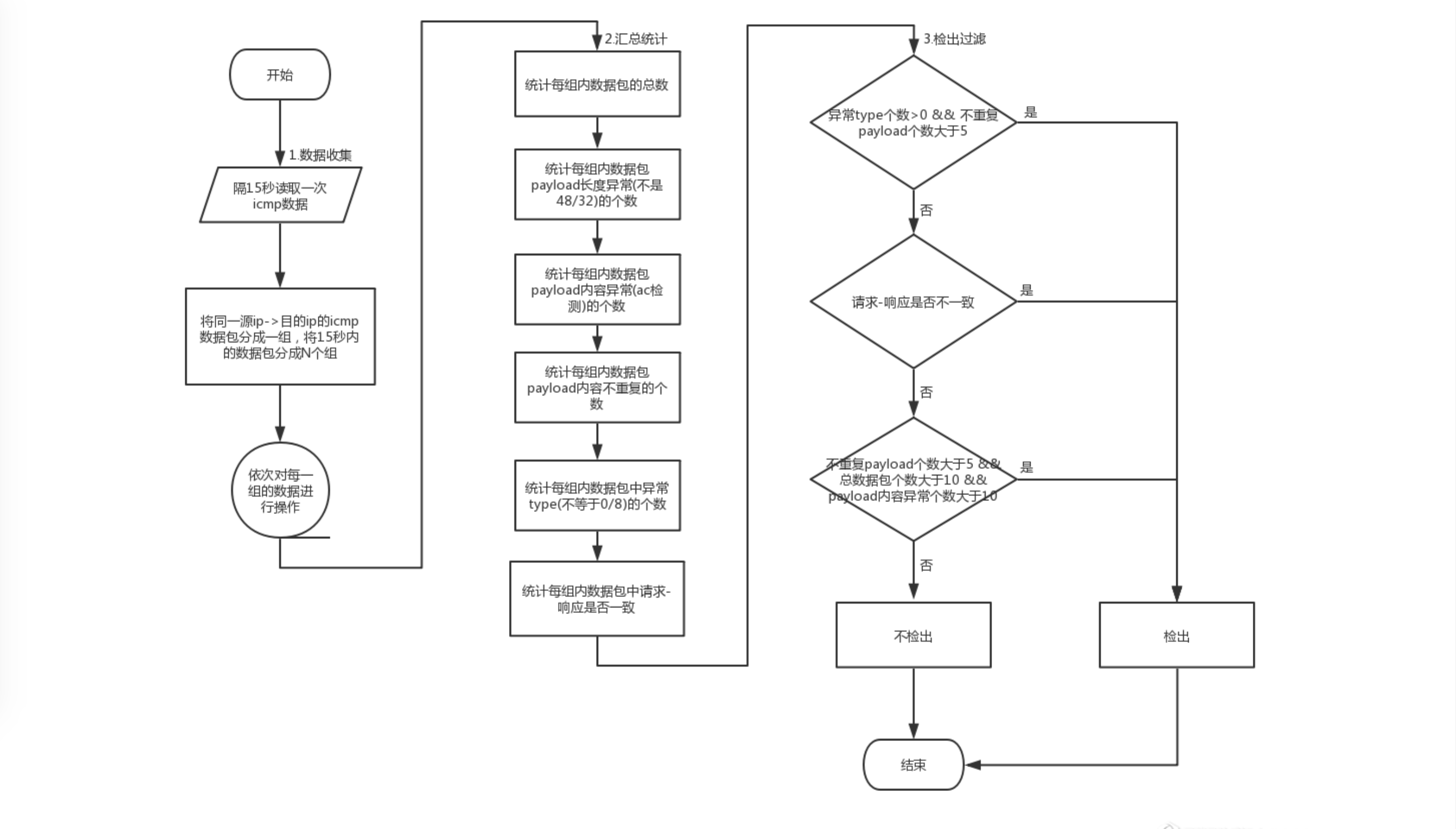
数据收集
- 读入实时流量数据,设置15秒处理一次数据
- 根据数据包的源ip、目的ip大小排序拼接后进行分组,将同一个ip向目的ip发送的请求/响应数据包分到一个组中
- 分组字段time_sort_sip_dip 加上时间戳timestamp
- 为了过滤掉上一次15秒内该源ip、目的ip之间的数据包,保证每个15秒内只处理当前15秒内的同一ip、目的ip的数据
汇总统计
根据分组后的数据,分别统计以下特征指标,作为最终是否检出的依据:
- 在一个时间窗内,ICMP请求响应的数据包数量
- 捕获到的ICMP请求响应中,其payload部分是否是操作系统的正常长度
- 序号相同的ICMP数据包应当属于一对ICMP请求响应消息,他们的payload是否一致
- ICMP请求响应的payload内容是否正常
- ICMP请求是否是畸形Ping报文(Type是否异常)
ICMP隐蔽隧道攻击分析与检测(四)的更多相关文章
- dns隧道攻击原理及常用工具流量分析
DNS协议是一种请求应答协议,也是一种可用于应用层的隧道技术.虽然DNS流量的异常变化可能会被发现,但是在基于传统socket隧道已经濒临淘汰,TCP.UDP通信大量被安全设备拦截的大背景下,DNS. ...
- Dshell----开源攻击分析框架
前言 随着互联网的高速发展,网络安全问题变得至关重要,随着网络的不断规模化和复杂化,网络中拒绝服务(Denial of Service,DoS)攻击和分布式拒绝服务(Distributed Denia ...
- .NET应用架构设计—面向对象分析与设计四色原型模式(彩色建模、领域无关模型)(概念版)
阅读目录: 1.背景介绍 2.问自己,UML对你来说有意义吗?它帮助过你对系统进行分析.建模吗? 3.一直以来其实我们被一个缝隙隔开了,使我们对OOAD遥不可及 4.四色原型模式填补这个历史缝隙,让我 ...
- [web安全]Web应用漏洞攻击分析与防范
网站攻击主要分为以下几类: (1) sql注入攻击 SQL Injection:就是通过把SQL命令插入到Web表单递交或输入域名或页面请求的查询字符串,最终达到欺骗服务器执行恶意的SQL命令.它是利 ...
- 手机自动化测试:appium源码分析之bootstrap四
手机自动化测试:appium源码分析之bootstrap四 Orientation是调整屏幕方向的操作 package io.appium.android.bootstrap.handler; i ...
- 带你走进二进制-一次APT攻击分析
原文:https://osandamalith.com/2017/06/04/apt-attack-in-bangladesh/ 由prison翻译整理,首发i春秋 引言; 这是一次来自遥远国 ...
- 《Linux内核分析》 第四节 扒开系统调用的三层皮(上)
<Linux内核分析> 第四节 扒开系统调用的三层皮(上) 张嘉琪 原创作品转载请注明出处 <Linux内核分析>MOOC课程http://mooc.study.163.com ...
- 分享下今天研究的流量上限DDos攻击分析和解决方式
分享下今天研究的流量上限DDos攻击分析和解决方式 常常听到或者碰到某个站点被攻击.一般都是流量攻击.今天自己写了个程序測下相关的上限,程序仅仅简单做了个get html操作(不包括图片等资源文件). ...
- Linux内核分析 - 网络[十四]:IP选项
Linux内核分析 - 网络[十四]:IP选项 标签: linux内核网络structsocketdst 2012-04-25 17:14 5639人阅读 评论(1) 收藏 举报 分类: 内核协议栈 ...
- ntp流量放大攻击分析
最近,听说挂在网络上的设备进行时间同步成功率低,YS需要架设自己的NTP服务器,这玩意第一时间能让人想到NTP流量放大攻击,这也是一种比较古老的攻击方式,检测了一下发现所使用的OS默认已经进行了加固, ...
随机推荐
- You Don't Know JS阅读笔记
JS特性查漏补缺 [1,2,3]=="1,2,3" //true 前者会隐式转换,用逗号组合成字符串 212>'22' //true 有一个值不是number就会隐式转换成n ...
- Debug --> 使用USTC-TK2016工具对USTC-TFC2016数据集进行处理
文件介绍: https://blog.csdn.net/u010916338/article/details/86511009?spm=1001.2101.3001.6661.1&utm_me ...
- vue项目浏览器ioc小图标
1 先有一个需要图片,png .jpg ...格式都可以 2 把图片转换成 .con 格式的图标 ,http://www.bitbug.net/使用比特虫转换 ,目标尺寸:16*16 或者 32*3 ...
- git在linux安装步骤详解!!
linux上安装,以centos 7.x为例 yum命令安装 yum install gityum install 安装的git不是最新版本,如需最新版本需要自行编译 到下面的网站下载合适的版本 ht ...
- sqlserver数据备份
sqlserver数据库 导入方法 第一种方法 1.打开SQL Server,写好登录名和密码点击连接. 2.打开数据库,右键某一个数据库,选择"新建查询(Q)". 3.再代码界面 ...
- vue3.0的生命周期函数
stetup(){}在 生命周期函数 系列中的优先级 〇setup(){ //优先级最高 处于created生命周期之前的函数,是无法访问data,methods中的数据是无法访问到的,setup中的 ...
- 2020/03/24 HTML基础复习笔记
2020-03-24 15:49:30 下午好! 这是我开通博客的第二天也是在钉钉上网课的又一天,为了应对考试现在复习到了HTML基础知识,本打算用VS敲想了想还是用了XMind(真的好用!!!)文件 ...
- 寄存器与RAM的区别
转自:https://blog.csdn.net/qq_18191333/article/details/106912668 概述 寄存器是"存储设备",主要用于存储和检查微型计算 ...
- FreeType 矢量字体 测试移植(1)
之前有做过 ascii 和汉字库的字体点阵在lcd上显示的例子,都是按照指定大小的字库的点阵来显示的,所以一但选定了字体文件后,就固定了大小,不可变化,当然也可以存放各种 大小的字体文件,但这样的话就 ...
- EVE如何提升名望值
目录 背景介绍 简介 名望值划分 军团名望值 利弊 背景介绍 玩eve将近3个星期,开着毒蜥级刷1级代理人任务感觉没有一点难度,想尽快刷3.4级代理任务,而我目前能够接到的最高代理任务也就才1级. ...
