CTF杂项之BubbleBabble加密算法
这题很坑,刚开始我拿到就分析不出来了(/无奈),关键是不知道是什么加密算法,后来看题目描述的bubble,猜测是bubble
这种算法(听都没听说过。。。)
上图
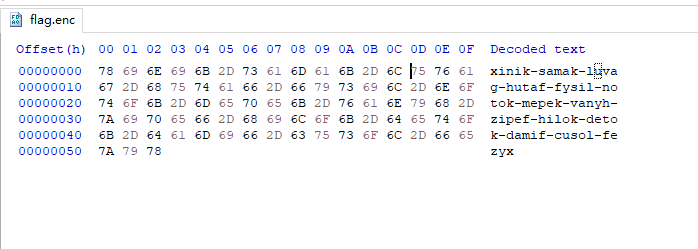
这串编码
xinik-samak-luvag-hutaf-fysil-notok-mepek-vanyh-zipef-hilok-detok-damif-cusol-fezyx
百度也没找到哪里有,后面看到有大佬写的writeup,于是就借鉴一下下,233
这里是这种加密算法的解释(为了方便大家,加密算法我复制到文末),链接传送:http://wiki.yak.net/589/Bubble_Babble_Encoding.txt
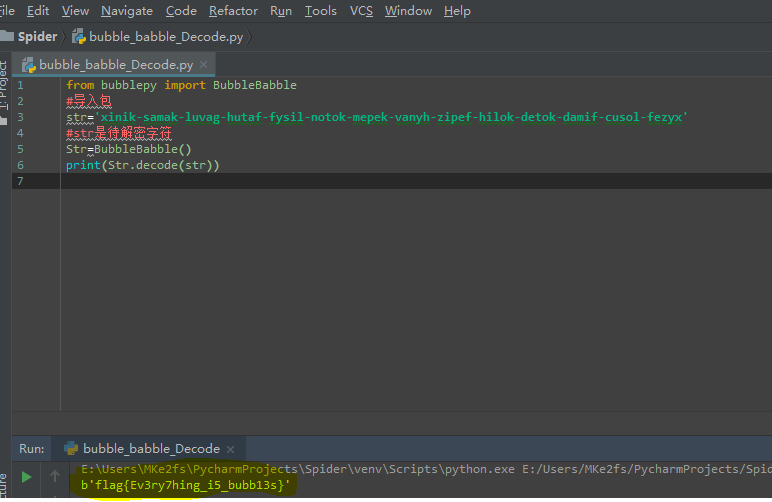
附上解题代码,楼主用的python3.7,另外bubblepy这个库需要导入一下,网址附上https://pypi.python.org/pypi/bubblepy/
from bubblepy import BubbleBabble
#导入包bubblepy
str='xinik-samak-luvag-hutaf-fysil-notok-mepek-vanyh-zipef-hilok-detok-damif-cusol-fezyx'
#str是待解密字符
Str=BubbleBabble()
print(Str.decode(str))
最后,get Flag
这里是BubbleBabble加密算法
authors==Huima
status==Experimental
title==The Bubble Babble Binary Data Encoding
number==Internet Draft
date==April 2000
Network Working Group Antti Huima
Internet Draft SSH Communications Security
draft-huima-babble-01.txt April 2000 The Bubble Babble Binary Data Encoding Status of this Memo This memo provides information for the Internet community. It does
not specify an Internet standard of any kind. Distribution of this
memo is unlimited. Copyright Notice Copyright (C) The Internet Society (2000). All Rights Reserved. Abstract This document describes a new encoding method for binary data that is
intended to be used in conjunction with fingerprints of
security-critical data. 1. Introduction Hash values of certificates and public keys, known as fingerprints
or thumbprints, are commonly used for verifying that a received
security-critical datum has been received correctly. Fingerprints
are binary data and typically encoded as series of hexadecimal
digits. However, long strings hexadecimal digits are difficult for
comprehend and cumbersome to translate reliably e.g. over phone. The Bubble Babble Encoding encodes arbitrary binary data into
pseudowords that are more natural to humans and that can be
pronounced relatively easily. The encoding consumes asymptotically
the same amount of space as an encoding of the form HH HH HH HH ... where `H' is a hexadecimal digit, i.e. carries 16 bits in six
characters. However, the Bubble Babble Encoding includes a
checksumming method that can sometimes detect invalid encodings.
The method does not increase the length of the encoded data. 2. Encoding Below, _|X|_ denotes the largest integer not greater than X. Let the data to be encoded be D[1] ... D[K] where K is the length
of the data in bytes; every D[i] is an integer from 0 to 2^8 - 1.
First define the checksum series C[1] ... C[_|K/2|_] where C[1] = 1 C[n] = (C[n - 1] * 5 + (D[n * 2 - 3] * 7 + D[n * 2 - 2])) mod 36 The data is then transformed into _|K/2|_ `tuples'
T[1] ... T[_|K/2|_] and one `partial tuple' P so that T[i] = <a, b, c, d, e> where a = (((D[i * 2 - 3] >> 6) & 3) + C[i]) mod 6
b = (D[i * 2 - 3] >> 2) & 15
c = (((D[i * 2 - 3]) & 3) + _|C[i] / 6|_) mod 6
d = (D[i * 2 - 2] >> 4) & 15; and
e = (D[i * 2 - 3]) & 15. The partial tuple P is P = <a, b, c> where if K is even then a = (C[i]) mod 6
b = 16
c = _|C[i] / 6|_ but if it is odd then a = (((D[K] >> 6) & 3) + C[i]) mod 6
b = (D[K] >> 2) & 15
c = (((D[K]) & 3) + _|C[i] / 6|_) mod 6 The `vowel table' V maps integers between 0 and 5 to vowels as 0 - a
1 - e
2 - i
3 - o
4 - u
5 - y and the `consonant table' C maps integers between 0 and 16 to
consonants as 0 - b
1 - c
2 - d
3 - f
4 - g
5 - h
6 - k
7 - l
8 - m
9 - n
10 - p
11 - r
12 - s
13 - t
14 - v
15 - z
16 - x The encoding E(T) of a tuple T = <a, b, c, d, e> is then the string V[a] C[b] V[c] C[d] `-' C[e] where there are five characters, and `-' is the literal hyphen. The encoding E(P) of a partial tuple P = <a, b, c> is the
three-character string V[a] C[b] V[c]. Finally, the encoding of the whole input data D is obtained as `x' E(T[1]) E(T[2]) ... E(T[_|K/2|_]) E(P) `x' where `x's are literal characters. 3. Decoding Decoding is obviously the process of encoding reversed. To check the checksums, when a tuple <a, b, c, d, e> or partial
tuple <a, b, c> has been recovered from the encoded string, an
implementation should check that ((a - C[i]) mod 6) < 4 and that
((c - C[i]) mod 6) < 4. Otherwise the encoded string is not a valid
encoding of any data and should be rejected. 4. Checksum Strength Every vowel in an encoded string carries 0.58 bits redundancy; thus
the length of the `checksum' in the encoding of an input string
containing K bytes is 0.58 * K bits. 5. Test Vectors ASCII Input Encoding
------------------------------------------------------------------
`' (empty string) `xexax'
`1234567890' `xesef-disof-gytuf-katof-movif-baxux'
`Pineapple' `xigak-nyryk-humil-bosek-sonax' 6. Author's Address Antti Huima
SSH Communications Security, Ltd.
[XXX] 7. Full Copyright Statement Copyright (C) The Internet Society (2000). All Rights Reserved. This document and translations of it may be copied and furnished to
others, and derivative works that comment on or otherwise explain
it or assist in its implementation may be prepared, copied,
published and distributed, in whole or in part, without restriction
of any kind, provided that the above copyright notice and this
paragraph are included on all such copies and derivative works.
However, this document itself may not be modified in any way, such
as by removing the copyright notice or references to the Internet
Society or other Internet organizations, except as needed for the
purpose of developing Internet standards in which case the
procedures for copyrights defined in the Internet Standards process
must be followed, or as required to translate it into languages
other than English. The limited permissions granted above are perpetual and will not be
revoked by the Internet Society or its successors or assigns. This document and the information contained herein is provided on
an "AS IS" basis and THE INTERNET SOCIETY AND THE INTERNET
ENGINEERING TASK FORCE DISCLAIMS ALL WARRANTIES, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTY THAT THE USE OF
THE INFORMATION HEREIN WILL NOT INFRINGE ANY RIGHTS OR ANY IMPLIED
WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
CTF杂项之BubbleBabble加密算法的更多相关文章
- CTF杂项思路工具分享————2019/5/30
分享碰到的一些奇奇怪怪的杂项解题方式: 键盘坐标密码: 题目给出一段字符串:11 21 31 18 27 33 34 对照上面的表格,就可以很清晰的看出来密文为:QAZIJCV 猪圈码: 题目为: 一 ...
- CTF杂项之音频隐写
题目来自bugku 二话不说,直接上图 由题目可以看出,这题需要用到一个KEY,加上又是一段音频,很容易联想到一个著名的音频隐写解密软件Mp3stego 直接上工具 ok,成功Get Flag
- 【CTF杂项】常见文件文件头文件尾格式总结及各类文件头
文件头文件尾总结 JPEG (jpg), 文件头:FFD8FF 文件尾:FF D9PNG (png), 文件头:89504E47 文件尾:AE 42 60 82GIF (gif), 文件头:47494 ...
- CTF杂项题解题思路
下载压缩包解压 如果是图片就先查看图片信息 没有有用信息查看图片看是否是一个图片 如果不是图片就将文件进行还原 从还原文件中查找有用信息 例:这是一张单纯的图片 http://123.206.87.2 ...
- ctf杂项之easy_nbt
下载附件查看 除了几个文件之外,没有思路 搜索nbt可知,可以使用nbtexplorer工具 果断下载,然后打开题目下载的目录 crrl+f搜索flag 猜测kflag{Do_u_kN0w_nbt?} ...
- BugKu CTF(杂项篇MISC)-贝斯手
打开是以下内容 先看一下给了哪些提示 1.介绍 没了?不,拉到最底下还有 2.女神剧照 密码我4不会告诉你的,除非你知道我的女神是哪一年出生的(细品) 大致已经明白了,四位数密码,出生年份 文件是以下 ...
- bugku ctf 杂项 旋转跳跃 (熟悉的声音中貌似又隐藏着啥,key:syclovergeek)
做这道题之前先给出工具 MP3Stego 下载地址 链接:https://pan.baidu.com/s/1W2mmGJcrm570EdJ6o7jD7g 提取码:1h1b 题目下载加压后 是一个 ...
- CTF 介绍及杂项
CTF(Capture The Flag)中文一般译作夺旗赛,在网络安全领域中指的是网络安全技术人员之间进行技术竞技的一种比赛形式.CTF起源于1996年DEFCON全球黑客大会,以代替之前黑客们通过 ...
- 实验吧CTF练习题---安全杂项---异性相吸解析
---恢复内容开始--- 实验吧安全杂项之异性相吸 地址:http://www.shiyanbar.com/ctf/1855 flag值:nctf{xor_xor_xor_biubiubiu} ...
随机推荐
- oppo8.0系统怎么无需Root激活Xposed框架的经验
在较多部门的引流,或业务操作中,基本都需要使用安卓的神一般的xposed框架,近期我们部门购来了一批新的oppo8.0系统,基本都都是基于7.0以上版本,基本都不能够刷入root的su权限,虽说一部分 ...
- c/c++ open函数的阻塞和非阻塞
调用open函数时,可以指定是以阻塞方式还是以非阻塞方式打开一个文件描述符. 阻塞方式打开: int fd = open("/dev/tty", O_RDWR|O_NONBLOCK ...
- 常见dos命令行
查找本地端口占用情况 是否8080端口被占用netstat -aon|findstr "8080" 在1.txt文档当中查找java字符串type 1.txt|findstr 'j ...
- 原生的 django 分页
原始的 django 分页 # 基本 写法 class Paginator(object): def __init__(self, object_list, per_page, orphans=0, ...
- 二、使用docker-compose搭建AspNetCore开发环境
1 使用docker-compose搭建开发环境 我们的目标很简单:使用docker-compose把若干个docker容器组合起来就成了. 首先使用Nginx代理所有的Web程序,这样只需要在主机上 ...
- Linux运维老司机:CentOS6.9配置安装并配置Rsync
一.rsync简介 rsync全称remote sync,是一种更高效.可以本地或远程同步的命令,之所以高效是因为rsync会对需要同步的源和目的进度行对比,只同步有改变的部分,所以比scp命令更高效 ...
- spring-boot-starter-mail技术总结
1. spring-boot-starter-mail技术总结 1.1. 配置读取类SMTPTransport 在application中需要配置的信息,在此类中都可以看到,可以在此类打断点查看 1. ...
- 5. VIM 系列 - 文件管理
目录 目录树 文件检索 ctrlp.vim fzf.vim 目录树 安装 nerdtree.vim 插件 Plug 'scrooloose/nerdtree', { 'on': 'NERDTreeTo ...
- 【Git之旅】1.Git常用命令
1.创建初始化版本库 git init 2.将文件添加到版本库中 git add index.html (添加到暂存区) git add . 命令让Git把当前目录及目录中的文件都添加到版本库里 gi ...
- 中缀表达式得到后缀表达式(c++、python实现)
将中缀表达式转换为后缀表达式的算法思想如下: 从左往右开始扫描中缀表达式 遇到数字加入到后缀表达式 遇到运算符时: 1.若为‘(’,入栈 2.若为’)‘,把栈中的运算符依次加入后缀表达式,直到出现'( ...
