RSA 加密及一些攻击方式
本文章转载自个人博客seandictionary.top同步更新可能不及时
原理
随机生成两个素数,p , q
令n = p*q
由欧拉公式计算出φ(n) = (p-1)(q-1)
规定e,使得e满足1<e<φ(n),且gcd(e,φ(n)) = 1,一般e=65537或0x10001
此时就有了公钥=(e,n)
计算私钥
计算d,使得d满足ed≡1mod φ(n),即称d是e在模φ(n)下的逆元
得到私钥=(d,n)
有关欧拉公式
- $n=p^{e_1}_1p^{e_2}_2\dots p^{e_k}_k$
- $\varphi(n)=n(1-\frac{1}{p_1})(1-\frac{1}{p_2})\dots (1-\frac{1}{p_k})$
- $\varphi(n)=p^{e_1-1}_1p^{e_2-1}_2\dots p^{e_k-1}_k(p_1-1)(p_2-1)\dots (p_k-1)$
- 当$gcd(n,x)=1$时,满足$x^{\varphi(n)}\equiv 1\ mod\ n$
RSA加密和解密
规定m表示明文,c表示密文
加密:c≡me mod n
解密:m≡cd mod n
解密方式
正常解密
- 此方法适用于已知$p,q,e,c$的情况下
可以使用RSA Tool 2工具解密或者编写如下脚本
from Crypto.Util.number import *
p = ?
q = ?
e = ?
c = ?
n = p*q
d = inverse(e,(p-1) * (q-1))
m = pow(c,d,n)
print(long_to_bytes(m))dp,dq泄露
- 此方法使用于已知$p,q,d_{p},d_{q},c$的情况下
- 然而使用此方法前可以先尝试常用e值,在发现无法确定e值的情况下再使用
理论推导
- dp,dq泄露
- 理论推导 红色字 为重要结论
$$\because m \equiv c^d(mod\ n)$$
$$\therefore m = c^d+kn = c^d+k\cdot pq$$
$$m_{1} \equiv c^d(mod\ p)\ ①\ ,\ m_{2} \equiv c^d(mod\ q)\ ②$$
$$①\Rightarrow c^d=m_{1}+tp$$
$$代入②\Rightarrow m_{2}\equiv m_{1}+tp(mod\ q)$$
$$\therefore m_{2}=m_{1}+t\cdot p+r\cdot q\ \Rightarrow m_{2}-m_{1}=t\cdot p+r\cdot q$$
$$\therefore m_{2}-m_{1}=t\cdot p(mod\ q)$$
$$\therefore (m_{2}-m_{1})\cdot p^{-1}\equiv t(mod\ q)$$
$$\Rightarrow t=(m_{2}-m_{1})\cdot p^{-1}(mod\ q)$$
$$\therefore c^d=[(m_{2}-m_{1})\cdot p^{-1}(mod\ q)]p+m_{1}$$
$$\because m\equiv c^d(mod\ n)$$
$$\therefore {\color{Red} m\equiv [[(m_{2}-m_{1})\cdot p^{-1}(mod\ q)]p+m_{1}]mod\ n}$$
$$d\equiv d_{p}mod(p-1)\ , \ d\equiv d_{q}mod(q-1)$$
$$m_{1} \equiv c^dmod\ p\ ,\ m_{2} \equiv c^dmod\ q$$
$$\Rightarrow m_{1} \equiv c^\left .d_{p}\ +k_{1}\cdot (p-1)\right.\ mod\ p\ ,\ m_{2} \equiv c^\left .d_{q}\ +k_{2}\cdot (q-1)\right.\ mod\ p$$
$$\because c^\left.p-1\right.\equiv 1\ mod\ p$$
$$\Rightarrow {\color{Red} m_{1}\equiv c^\left .d_{p}\right . mod\ p\ ,\ m_{2}\equiv c^\left .d_{q}\right . mod \ q}$$
使用脚本解密
from Crypto.Util.number import *
p = ?
q = ?
dp = ?
dq = ?
c = ?
mp = pow(c,dp,p)
mq = pow(c,dq,q)
pi = inverse(p,q)
m = ((((mq-mp)pi)%q)p+mp)%(p*q)
print(long_to_bytes(m))dp泄露
- 此方法使用于已知$e,n,d_{p},c$的情况下
理论推导
- dp泄露
- 理论推导 红色字 为重要结论
$$d_{p} \equiv d mod (p-1)$$
$$\Rightarrow d\cdot e = k_{1}(p-1)+d_{p}\cdot e$$
$$\because d\cdot e = 1mod(p-1)(q-1) \Rightarrow d\cdot e=k_{2}(p-1)(q-1)+1$$
$$\therefore {\color{Red} (p-1)(k_{2}(q-1)-k_{1})+1 = d_{p}e}$$
$$\because d_{p}<d$$
$$\therefore (k_{2}(q-1)-k_{1})=x\in (1,e)$$
from Crypto.Util.number import *
e = 65537
n = ?
dp = ?
c = ?
a = dp*e-1
for x in range(2,e):
if a%x == 0:
p = a//x+1
if n%p == 0:
q = n//p
break
d = inverse(e,(p-1)*(q-1))
m = pow(c,d,n)
print(long_to_bytes(m))共模攻击
- 此方法使用于已知$n,e_{1},e_{2},c_{1},c_{2}$的情况下
- 且$gcd(e_{1},e_{2})=1$
理论推导
- 共模攻击
- 理论推导 红色字 为重要结论
- 存在两种密钥对同一明文进行加密
- 下述为针对此题特殊情况下的特殊推导,需满足$gcd(e_{1},e_{2})=1$
$$c_{1}=m^\left. e_{1}\right. mod\ n\ \&\ m=c_{1}^\left.d_{1}\right.mod\ n$$
$$c_{2}=m^\left. e_{2}\right. mod\ n\ \&\ m=c_{2}^\left.d_{2}\right.mod\ n$$
$$构造一对(s_{1},s_{2})满足e_{1}s_{1}+e_{2}s_{2}=1其中s_{1},s_{2}\in Z,s_{1}>0,s_{2}<0$$
$$c_{1}=m^\left. e_{1}\right. mod\ n \Rightarrow c_{1}^\left. s_{1}\right. =m^\left. e_{1}s_{1}\right. mod\ n ①$$
$$c_{2}=m^\left. e_{2}\right. mod\ n \Rightarrow c_{2}^\left. s_{2}\right. =m^\left. e_{2}s_{2}\right. mod\ n ②$$
$$①\times ②\Rightarrow c_{1}^\left. s_{1}\right. c_{2}^\left. s_{2}\right. mod\ n = m^\left. e_{1}s_{1}+e_{2}s_{2}\right. mod\ n$$
$$\Rightarrow c_{1}^\left. s_{1}\right. c_{2}^\left. s_{2}\right. mod\ n=m\ mod\ n$$
$$\because m=c^d mod\ n \therefore m<n$$
$$\therefore {\color{red}m=c_{1}^\left. s_{1}\right. c_{2}^\left. s_{2}\right. mod\ n}$$
$$需要注意的是推论到上面就结束了,但是实际计算中上述式子计算过于复杂,所以应当使用下述式子$$
$${\color{red}m=(c_{1}^\left. s_{1}\right. mod\ n\cdot c_{2}^\left. s_{2}\right. mod\ n)mod\ n}$$
$$以及在计算s_{1},s_{2}过程中可以采用逆元的方式$$
$$(e_{1}-e{2})s_{1}+e{2}(s_{1}+s_{2})=1$$
$$(e_{1}-e{2})s_{1}\equiv 1\ mod\ e_{2}$$
$$s_{1}=(e_{1}-e{2})^\left. -1\right. $$
- 由此计算出一对$(s_{1},s_{2})$,进而算出明文m
- 编写脚本
from Crypto.Util.number import *
n = ?
c1 = ?
c2 = ?
e1 = ?
e2 = ?
e1_e2 = e1-e2
s1 = inverse(e1_e2,e2)
s2 = (1-e1*s1)//e2
m = pow(c1,s1,n)*pow(c2,s2,n)%n
print(long_to_bytes(m))维纳攻击
- 此方法使用于$e$过大或过小的情况下
- 本质:满足$d < \frac{1}{3} N^{\frac{1}{4} }$则一定可以分解$N$
- 大致解密过程是用RSAwienerHacker库来攻击得到d
- 原理太复杂了要翻论文了-链接
- 板子
from RSAwienerHacker import *
n = ?
e = ?
d = hack_RSA(e,n)扩展维纳攻击
两个低解密指数
from Crypto.Util.number import *
e1 = ?
e2 = ?
N = ?
a = 5/14
D = diagonal_matrix(ZZ, [N, int(N^(1/2)), int(N^(1+a)), 1])
M = matrix(ZZ, [[1, -N, 0, N^2], [0, e1, -e1, -e1*N], [0, 0, e2, -e2*N], [0, 0, 0, e1*e2]])*D
L = M.LLL()
t = vector(ZZ, L[0])
x = t * M^(-1)
phi = int(x[1]/x[0]*e1)
d = inverse(e,phi)三个低解密指数
e1 = ?
e2 = ?
e3 = ?
n = ?
a = 2/5
D = diagonal_matrix(ZZ,[int(n^1.5), n, int(n^(a+1.5)), int(n^0.5), int(n^(a+1.5)), int(n^(a+1)), int(n^(a+1)), 1])
L = Matrix(ZZ,[[1, -n, 0, n^2, 0, 0, 0, -n^3],
[0, e1, -e1, -n*e1, -e1, 0, n*e1, n^2*e1],
[0, 0, e2, -n*e2, 0, n*e2, 0, n^2*e2],
[0, 0, 0, e1*e2, 0, -e1*e2, -e1*e2, -n*e1*e2],
[0, 0, 0, 0, e3, -n*e3, -n*e3, n^2*e3],
[0, 0, 0, 0, 0, e1*e3, 0, -n*e1*e3],
[0, 0, 0, 0, 0, 0, e2*e3, -n*e2*e3],
[0, 0, 0, 0, 0, 0, 0, e1*e2*e3]]) * D
Ge = L.LLL()[0]
x = vector(ZZ, Ge) / L
phi = int(x[1]/x[0]*e1)
d = inverse(e,phi)通用情况
from Crypto.Util.number import *
isdigit = lambda x: ord('0') <= ord(x) <= ord('9')
def my_permutations(g, n):
sub = []
res = []
def dfs(s, prev):
if len(s) == n:
res.append(s[::])
for i in g:
if i in s or i < prev:
continue
s.append(i)
dfs(s, max(prev, i))
s.remove(i)
dfs(sub, 0)
return res
class X3NNY(object):
def __init__(self, exp1, exp2):
self.exp1 = exp1
self.exp2 = exp2
def __mul__(self, b):
return X3NNY(self.exp1 * b.exp1, self.exp2 * b.exp2)
def __repr__(self):
return '%s = %s' % (self.exp1.expand().collect_common_factors(), self.exp2)
class X_Complex(object):
def __init__(self, exp):
i = 0
s = '%s' % exp
while i < len(s):
if isdigit(s[i]):
num = 0
while i < len(s) and isdigit(s[i]):
num = num*10 + int(s[i])
i += 1
if i >= len(s):
self.b = num
elif s[i] == '*':
self.a = num
i += 2
elif s[i] == '/':
i += 1
r = 0
while i < len(s) and isdigit(s[i]):
r = r*10 + int(s[i])
i += 1
self.b = num/r
else:
i += 1
if not hasattr(self, 'a'):
self.a = 1
if not hasattr(self, 'b'):
self.b = 0
def WW(e, d, k, g, N, s):
return X3NNY(e*d*g-k*N, g+k*s)
def GG(e1, e2, d1, d2, k1, k2):
return X3NNY(e1*d1*k2- e2*d2*k1, k2 - k1)
def W(i):
e = eval("e%d" % i)
d = eval("d%d" % i)
k = eval("k%d" % i)
return WW(e, d, k, g, N, s)
def G(i, j):
e1 = eval("e%d" % i)
d1 = eval("d%d" % i)
k1 = eval("k%d" % i)
e2 = eval("e%d" % j)
d2 = eval("d%d" % j)
k2 = eval("k%d" % j)
return GG(e1, e2, d1, d2, k1, k2)
def R(e, sn): # min u max v
ret = X3NNY(1, 1)
n = max(e)
nn = len(e)
l = set(i for i in range(1, n+1))
debug = ''
u, v = 0, 0
for i in e:
if i == 1:
ret *= W(1)
debug += 'W(%d)' % i
nn -= 1
l.remove(1)
u += 1
elif i > min(l) and len(l) >= 2*nn:
ret *= G(min(l), i)
nn -= 1
debug += 'G(%d, %d)' % (min(l), i)
l.remove(min(l))
l.remove(i)
v += 1
else:
ret *= W(i)
l.remove(i)
debug += 'W(%d)' % i
nn -= 1
u += 1
# print(debug, end = ' ')
return ret, u/2 + (sn - v) * a
def H(n):
if n == 0:
return [0]
if n == 2:
return [(), (1,), (2,), (1, 2)]
ret = []
for i in range(3, n+1):
ret.append((i,))
for j in range(1, i):
for k in my_permutations(range(1, i), j):
ret.append(tuple(k + [i]))
return H(2) + ret
def CC(exp, n):
cols = [0 for i in range(1<<n)]
# split exp
texps = ('%s' % exp.exp1.expand()).strip().split(' - ')
ops = []
exps = []
for i in range(len(texps)):
if texps[i].find(' + ') != -1:
tmp = texps[i].split(' + ')
ops.append(0)
exps.append(tmp[0])
for i in range(1, len(tmp)):
ops.append(1)
exps.append(tmp[i])
else:
ops.append(0)
exps.append(texps[i])
if exps[0][0] == '-':
for i in range(len(exps)):
ops[i] = 1-ops[i]
exps[0] = exps[0][1:]
else:
ops[0] = 1
# find e and N
l = []
for i in range(len(exps)):
tmp = 1 if ops[i] else -1
en = []
j = 0
while j < len(exps[i]):
if exps[i][j] == 'e':
num = 0
j += 1
while isdigit(exps[i][j]):
num = num*10 + int(exps[i][j])
j += 1
tmp *= eval('e%d' % num)
en.append(num)
elif exps[i][j] == 'N':
j += 1
num = 0
if exps[i][j] == '^':
j += 1
while isdigit(exps[i][j]):
num = num*10 + int(exps[i][j])
j += 1
if num == 0:
num = 1
tmp *= eval('N**%d' % num)
else:
j += 1
if tmp == 1 or tmp == -1:
l.append((0, ()))
else:
l.append((tmp, tuple(sorted(en))))
# construct h
mp = H(n)
for val, en in l:
cols[mp.index(en)] = val
# print(cols)
return cols
def EWA(n, elist, NN, alpha):
mp = H(n)
var('a')
S = [X_Complex(n*a)]
cols = [[1 if i == 0 else 0 for i in range(2^n)]]
for i in mp[1:]:
eL, s = R(i, n)
cols.append(CC(eL, n))
S.append(X_Complex(s))
alphaA,alphaB = 0, 0
for i in S:
alphaA = max(i.a, alphaA)
alphaB = max(i.b, alphaB)
# print(alphaA, alphaB)
D = []
for i in range(len(S)):
# print((alphaA-S[i].a), (alphaB - S[i].b))
D.append(
int(NN^((alphaA-S[i].a)*alpha + (alphaB - S[i].b)))
)
kw = {'N': NN}
for i in range(len(elist)):
kw['e%d' % (i+1)] = elist[i]
B = Matrix(ZZ, Matrix(cols).T(**kw)) * diagonal_matrix(ZZ, D)
L = B.LLL(0.5)
v = Matrix(ZZ, L[0])
x = v * B**(-1)
phi = int(x[0,1]/x[0,0]*elist[0])
return phi
def attack(NN, elist, alpha):
phi = EWA(len(elist), elist, NN, alpha)
print(phi)
return phi
n = ? # n是d的比特位数
NN = ?
elist = [e1,e2,e3, ...,en]
alpha = n / int(NN).bit_length()
for i in range(1, len(elist)+1):
var("e%d" % i)
var("d%d" % i)
var("k%d" % i)
g, N, s = var('g'), var('N'), var('s')
for i in range(len(elist)):
elist[i] = Integer(elist[i])
phi = attack(NN, elist, alpha)
d = inverse(e, phi)Boneh Durfee攻击
- 这是维纳攻击的一种延伸,拓展了可以攻击的d的范围
- $d<n^{0.292}$
GitHub仓库,在此基础上修改
import time
from Crypto.Util.number import *
"""
Setting debug to true will display more informations
about the lattice, the bounds, the vectors...
"""
debug = True
"""
Setting strict to true will stop the algorithm (and
return (-1, -1)) if we don't have a correct
upperbound on the determinant. Note that this
doesn't necesseraly mean that no solutions
will be found since the theoretical upperbound is
usualy far away from actual results. That is why
you should probably use `strict = False`
"""
strict = False
"""
This is experimental, but has provided remarkable results
so far. It tries to reduce the lattice as much as it can
while keeping its efficiency. I see no reason not to use
this option, but if things don't work, you should try
disabling it
"""
helpful_only = True
dimension_min = 7 # stop removing if lattice reaches that dimension
############################################
# Functions
##########################################
# display stats on helpful vectors
def helpful_vectors(BB, modulus):
nothelpful = 0
for ii in range(BB.dimensions()[0]):
if BB[ii,ii] >= modulus:
nothelpful += 1
print (nothelpful, "/", BB.dimensions()[0], " vectors are not helpful")
# display matrix picture with 0 and X
def matrix_overview(BB, bound):
for ii in range(BB.dimensions()[0]):
a = ('%02d ' % ii)
for jj in range(BB.dimensions()[1]):
a += '0' if BB[ii,jj] == 0 else 'X'
if BB.dimensions()[0] < 60:
a += ' '
if BB[ii, ii] >= bound:
a += '~'
print (a)
# tries to remove unhelpful vectors
# we start at current = n-1 (last vector)
def remove_unhelpful(BB, monomials, bound, current):
# end of our recursive function
if current == -1 or BB.dimensions()[0] <= dimension_min:
return BB
# we start by checking from the end
for ii in range(current, -1, -1):
# if it is unhelpful:
if BB[ii, ii] >= bound:
affected_vectors = 0
affected_vector_index = 0
# let's check if it affects other vectors
for jj in range(ii + 1, BB.dimensions()[0]):
# if another vector is affected:
# we increase the count
if BB[jj, ii] != 0:
affected_vectors += 1
affected_vector_index = jj
# level:0
# if no other vectors end up affected
# we remove it
if affected_vectors == 0:
print ("* removing unhelpful vector", ii)
BB = BB.delete_columns([ii])
BB = BB.delete_rows([ii])
monomials.pop(ii)
BB = remove_unhelpful(BB, monomials, bound, ii-1)
return BB
# level:1
# if just one was affected we check
# if it is affecting someone else
elif affected_vectors == 1:
affected_deeper = True
for kk in range(affected_vector_index + 1, BB.dimensions()[0]):
# if it is affecting even one vector
# we give up on this one
if BB[kk, affected_vector_index] != 0:
affected_deeper = False
# remove both it if no other vector was affected and
# this helpful vector is not helpful enough
# compared to our unhelpful one
if affected_deeper and abs(bound - BB[affected_vector_index, affected_vector_index]) < abs(bound - BB[ii, ii]):
print ("* removing unhelpful vectors", ii, "and", affected_vector_index)
BB = BB.delete_columns([affected_vector_index, ii])
BB = BB.delete_rows([affected_vector_index, ii])
monomials.pop(affected_vector_index)
monomials.pop(ii)
BB = remove_unhelpful(BB, monomials, bound, ii-1)
return BB
# nothing happened
return BB
"""
Returns:
* 0,0 if it fails
* -1,-1 if `strict=true`, and determinant doesn't bound
* x0,y0 the solutions of `pol`
"""
def boneh_durfee(pol, modulus, mm, tt, XX, YY):
"""
Boneh and Durfee revisited by Herrmann and May
finds a solution if:
* d < N^delta
* |x| < e^delta
* |y| < e^0.5
whenever delta < 1 - sqrt(2)/2 ~ 0.292
"""
# substitution (Herrman and May)
PR.<u, x, y> = PolynomialRing(ZZ)
Q = PR.quotient(x*y + 1 - u) # u = xy + 1
polZ = Q(pol).lift()
UU = XX*YY + 1
# x-shifts
gg = []
for kk in range(mm + 1):
for ii in range(mm - kk + 1):
xshift = x^ii * modulus^(mm - kk) * polZ(u, x, y)^kk
gg.append(xshift)
gg.sort()
# x-shifts list of monomials
monomials = []
for polynomial in gg:
for monomial in polynomial.monomials():
if monomial not in monomials:
monomials.append(monomial)
monomials.sort()
# y-shifts (selected by Herrman and May)
for jj in range(1, tt + 1):
for kk in range(floor(mm/tt) * jj, mm + 1):
yshift = y^jj * polZ(u, x, y)^kk * modulus^(mm - kk)
yshift = Q(yshift).lift()
gg.append(yshift) # substitution
# y-shifts list of monomials
for jj in range(1, tt + 1):
for kk in range(floor(mm/tt) * jj, mm + 1):
monomials.append(u^kk * y^jj)
# construct lattice B
nn = len(monomials)
BB = Matrix(ZZ, nn)
for ii in range(nn):
BB[ii, 0] = gg[ii](0, 0, 0)
for jj in range(1, ii + 1):
if monomials[jj] in gg[ii].monomials():
BB[ii, jj] = gg[ii].monomial_coefficient(monomials[jj]) * monomials[jj](UU,XX,YY)
# Prototype to reduce the lattice
if helpful_only:
# automatically remove
BB = remove_unhelpful(BB, monomials, modulus^mm, nn-1)
# reset dimension
nn = BB.dimensions()[0]
if nn == 0:
print ("failure")
return 0,0
# check if vectors are helpful
if debug:
helpful_vectors(BB, modulus^mm)
# check if determinant is correctly bounded
det = BB.det()
bound = modulus^(mm*nn)
if det >= bound:
print ("We do not have det < bound. Solutions might not be found.")
print ("Try with highers m and t.")
if debug:
diff = (log(det) - log(bound)) / log(2)
print ("size det(L) - size e^(m*n) = ", floor(diff))
if strict:
return -1, -1
else:
print ("det(L) < e^(m*n) (good! If a solution exists < N^delta, it will be found)")
# display the lattice basis
if debug:
matrix_overview(BB, modulus^mm)
# LLL
if debug:
print ("optimizing basis of the lattice via LLL, this can take a long time")
BB = BB.LLL()
if debug:
print ("LLL is done!")
# transform vector i & j -> polynomials 1 & 2
if debug:
print ("looking for independent vectors in the lattice")
found_polynomials = False
for pol1_idx in range(nn - 1):
for pol2_idx in range(pol1_idx + 1, nn):
# for i and j, create the two polynomials
PR.<w,z> = PolynomialRing(ZZ)
pol1 = pol2 = 0
for jj in range(nn):
pol1 += monomials[jj](w*z+1,w,z) * BB[pol1_idx, jj] / monomials[jj](UU,XX,YY)
pol2 += monomials[jj](w*z+1,w,z) * BB[pol2_idx, jj] / monomials[jj](UU,XX,YY)
# resultant
PR.<q> = PolynomialRing(ZZ)
rr = pol1.resultant(pol2)
# are these good polynomials?
if rr.is_zero() or rr.monomials() == [1]:
continue
else:
print ("found them, using vectors", pol1_idx, "and", pol2_idx)
found_polynomials = True
break
if found_polynomials:
break
if not found_polynomials:
print ("no independant vectors could be found. This should very rarely happen...")
return 0, 0
rr = rr(q, q)
# solutions
soly = rr.roots()
if len(soly) == 0:
print ("Your prediction (delta) is too small")
return 0, 0
soly = soly[0][0]
ss = pol1(q, soly)
solx = ss.roots()[0][0]
#
return solx, soly
def example(N,e,delta):
############################################
# How To Use This Script
##########################################
#
# Lattice (tweak those values)
#
# you should tweak this (after a first run), (e.g. increment it until a solution is found)
m = 4 # size of the lattice (bigger the better/slower)
# you need to be a lattice master to tweak these
t = int((1-2*delta) * m) # optimization from Herrmann and May
X = 2*floor(N^delta) # this _might_ be too much
Y = floor(N^(1/2)) # correct if p, q are ~ same size
#
# Don't touch anything below
#
# Problem put in equation
P.<x,y> = PolynomialRing(ZZ)
A = int((N+1)/2)
pol = 1 + x * (A + y)
#
# Find the solutions!
#
# Checking bounds
if debug:
print ("=== checking values ===")
print ("* delta:", delta)
print ("* delta < 0.292", delta < 0.292)
print ("* size of e:", int(log(e)/log(2)))
print ("* size of N:", int(log(N)/log(2)))
print ("* m:", m, ", t:", t)
# boneh_durfee
if debug:
print ("=== running algorithm ===")
start_time = time.time()
solx, soly = boneh_durfee(pol, e, m, t, X, Y)
# found a solution?
if solx > 0:
print ("=== solution found ===")
if False:
print ("x:", solx)
print ("y:", soly)
d = int(pol(solx, soly) / e)
print ("private key found:", d)
else:
print ("=== no solution was found ===")
if debug:
print("=== %s seconds ===" % (time.time() - start_time))
return d
if __name__ == "__main__":
n = ?
e = ?
c = ?
# the hypothesis on the private exponent (the theoretical maximum is 0.292)
delta = 0.28 # this means that d < N^delta
d = example(n,e,delta)
print(long_to_bytes(int(pow(c,d,n))))e和φ不互质
1.二次剩余+CRT
- 此方法适用于$e$非质,即$gcd(e,\varphi )=2$
- 要求解任意模数二次剩余先要求解奇素数模数二次剩余–具体理论查看此链
- 据此推导过程编写脚本
实例[0xGame 2024] Number-Theory-CRT
from Crypto.Util.number import *
import sympy
from sympy.ntheory.modular import crt
c = ?
e = ?
n = ?
p = ?
q = ?
phi = (p-1) * (q-1)
print(GCD(e,phi)) # 发现公约数2,分析得到二次剩余
def find_quadratic_residues(a, p):
# 首先检查 a 是否是模 p 下的二次剩余
if not sympy.is_quad_residue(a, p):
return None # 如果 a 不是二次剩余,返回 None
# 使用 sympy 的 nthroot_mod 找到一个解
x = sympy.nthroot_mod(a, 2, p, all_roots=False)
# 计算另一个解
second_solution = p - x
return (x, second_solution)
x1 = find_quadratic_residues(c,p) # 求解模p下的二次剩余
x2 = find_quadratic_residues(c,q) # 求解模q下的二次剩余
for i in x1:
for j in x2:
remainders = [i,j]
mods = [p,q]
m_ = crt(mods, remainders)[0] # CRT合并得到模n的二次剩余解
c_ = m_%n
e_ = e//2
d = inverse(e_,phi)
m = pow(c_,d,n)
print(long_to_bytes(m))2.用Sage求解有限域上开方
- 理论来说应该可以解决任意公约数的不互质问题,但是运行时间较长
- 自认为Method 1适用于gcd小、n大的情况,Method 2适用于gcd大、n小的情况
from Crypto.Util.number import *
from sympy.ntheory.modular import crt
p = ?
q = ?
n = ?
c = ?
e = ?
phi = (p-1)*(q-1)
gcd = GCD(e,phi)
d = inverse(e//gcd,phi)
# Method 1 求解同余方程
R.<x> = PolynomialRing(Zmod(p))
f = x^gcd - c
res1 = f.roots(multiplicities=False)
R.<x> = PolynomialRing(Zmod(q))
f = x^gcd - c
res2 = f.roots(multiplicities=False)
# Method 2 开根号
res1 = Zmod(p)(c).nth_root(gcd, all=True)
res2 = Zmod(q)(c).nth_root(gcd, all=True)
for i in res1:
for j in res2:
m = crt([p,q],[int(i),int(j)])
if m is not None:
try:
print(long_to_bytes(int(pow(m[0],d,n))).decode())
except Exception as e:
continueRabin加密
- 可以看作是RSA中$e=2$的特殊情况,且$p\equiv q\equiv 3\ mod\ 4$
- 解法原理同上e和φ不互质
给定一些关于$p,q$计算后的值
- 已知$n,x_1p+y_1q,x_2p+y_2q$
- 已知$n,(xp+yq)^{n-p-q}mod\ n$
- 已知$p^2+q^2$
# SageMath
N = ?
f = ZZ[I](N)
divisors_f = divisors(f)
for d in divisors_f:
a,b = d.real(), d.imag()
if a**2 + b**2 == N:
p = abs(int(a))
q = abs(int(b))
if is_prime(p) and is_prime(q):
print("p =",p)
print("q =",q)
break- 已知$p^q\ mod\ n$
- 易得$p^q\ mod\ n = p$
部分泄露
已知p高位
Coppersmith 攻击
对于512位素数,需要未知至多227位
对于1024位素数,需要未知至多454\455位,可能性大致对半开
如果无法满足上述条件,可以爆破几位数
from Crypto.Util.number import *
n = ?
c = ?
e = 65537
p_high = ?
R.<x> = PolynomialRing(Zmod(n))
f = p_high + x
res = f.small_roots(X = 2^256,beta = 0.4)
if res != []:
p = p_high + int(res[0])
q = n // p
d = inverse(e,(p-1)*(q-1))
m = pow(c,d,n)
print(long_to_bytes(int(m)))已知m高位
似乎此题的e通常为3,实测0x10001运行几分钟都没结果
from Crypto.Util.number import long_to_bytes
n = ?
c = ?
e = 3
m1 = ?
bits = ?
R.<x> = PolynomialRing(Zmod(n))
f = (m1 + x)^e - c
res = f.small_roots(X = 2^bits,beta = 1)已知d高位
d高位低位泄露的主要推导基于此论文-An Attack on RSA Given a Small Fraction of the Private Key Bits
d高位泄露
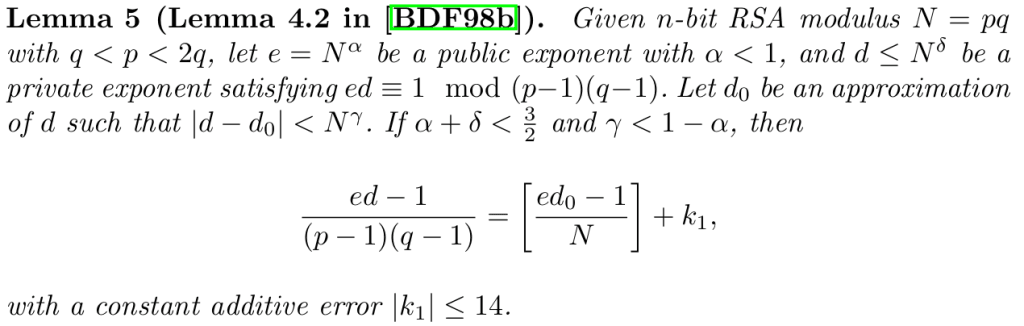
满足上述条件时可以计算出$\tilde{k}$然后通过恒定附加误差爆破即可得到正确$k$
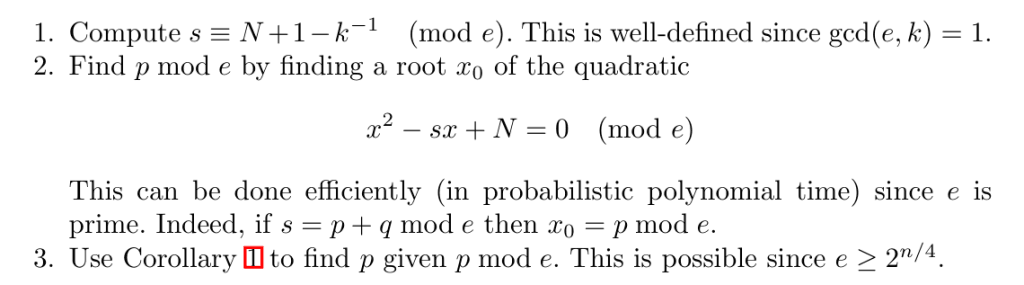
再依据上述结论计算出$x= p\ mod\ e$
剪枝
p^(q>>nbits)
p = getPrime(lenth)
q = getPrime(lenth)
n = p*q
gift = p ^ (q >> bits)主要思路是计算p和q,基于以下两个已知事实,去遍历确定每个比特位
- 将 p、q 未确定的比特位全填 0,乘积应小于 n
- 将 p、q 未确定的比特位全填 1,乘积应大于 n
n = ?
gift = ?
bits = ?
lenth = ?
p = bin(gift)[2:2+bits]
q = ""
for i in range(lenth-bits):
tmp = int(bin(gift)[2:][bits+i])
for a in range(2):
b = tmp^a
if (int(p+str(a),2)<<(lenth-bits-1-i)) * (int(q+str(b),2)<<(lenth-1-i)) < n and ((int(p+str(a),2)<<(lenth-bits-1-i)) + 2**(lenth-bits-1-i) - 1) * ((int(q+str(b),2)<<(lenth-1-i)) + 2**(lenth-1-i) - 1) > n:
p = p+str(a)
q = q+str(b)
break
p = int(p,2)
assert n%p == 0
q = n//pRSA Leak Oracle
RSA Byte Oracle
如果有一个预言机可以提供RSA解密操作,但是只会返回最后一个字节。可以在$log_256n$的时间内计算出明文$m$
已知$c=m^e\ mod\ n$和$n,e$
显然由于RSA是乘法同态的加密算法,于是可以构造一个已知的明文,加密后和密文相乘,使得解密后的明文乘上构造的明文,即
$$a = (256^i)^e\ mod\ n$$
$$ac^d \equiv 256^im\ mod\ n=256^im-kn$$
由于预言机只能给出最后一个字节所以我们实际上得到的是$output = -kn\ mod\ 256$
易得$k\equiv -n^{-1}output\ mod\ 256$
很容易注意到这里$k$是对256取模的,也就是说当$i>1$时显然$k<256^i$并不能准确计算出$k$
但是能发现当$i=1$的时候很容易计算得到此时的$k_1=-n^{-1}output_1$有$k_1n\le 256c\le (k_1+1)n$
那么当$i=2$时,有$k_2n\le 256^2c\le (k_2+1)n$,这两个范围肯定有并集因此可以有
$$ \left\{\begin{matrix} 256k_1n\le 256^2c\le 256(k+1)n\\ k_2n\le 256^2c\le (k_2+1)n \end{matrix}\right. \Rightarrow \left\{\begin{matrix} 256k_1<(k_2+1)\\ k_2<256(k_1+1) \end{matrix}\right. $$
$$\Rightarrow k_2=256k_1+t$$
很amazing啊,推广后能发现k除以256的商正好就是上一轮的k而且余数也是能通过上述推导得来的,因此就能计算出k从而确定明文了。
MatrixRSA
咕咕ing
*论文题
关键字:RSA、相同私钥、格基规约、格、同一明文多次加密、LLL
RSA 加密及一些攻击方式的更多相关文章
- RSA加密常用的填充方式 以及 常见错误
一.RSA加密常用的填充方式 1.RSA_PKCS1_PADDING 输入:比 RSA modulus 短至少11个字节.如果输入的明文过长,必须切割,然后填充 输出:和modulus一样长 根据这个 ...
- OpenSSL中的大数接口与基于其的自用RSA加密接口设计
本文记录了初次接触OpenSSL中的大数模块,重温了RSA加密流程,使用OpenSSL的接口包装成自用RSA加密接口,并且利用自己的接口演示了Alice与Bob通过RSA加密进行通讯的一个示例. 概览 ...
- rsa加密--选择padding模式需要注意的问题。。。
最近在做一个项目中需要,在android对一个密码字段首先进行 一次md5加密后再进行一次rsa加密,然后把加密的结果通过 json协议传输给nginx服务器进行解密.在android中,可以直接 使 ...
- 简单RSA攻击方式
RSA攻击方式总结 1.模数分解 1).解题思路 a).找到RSA算法中的公钥(e,n) b).通过n来找到对应的p和q,然后求得φ(n) c).通过gmpy2.invert或者gmpy2 ...
- IOS RSA 加密方式
采用RSA加密方式,主要是生成公钥和私钥,公钥用来加密,私钥用来解密,至于其中如何实现的,网上有很多原理. 参见如下: https://github.com/jslim89/RSA-objc PS: ...
- thinkphp整合系列之支付宝RSA加密方式
thinkphp整合系列之支付宝RSA加密方式上篇博客写的是MD5加密方式:thinkphp整合系列之支付宝MD5加密方式扫码支付http://baijunyao.com/article/75 但是呢 ...
- RSA加密原理使用方式签名验证
RSA加密原理使用方式签名验证 加密是网络传输中非常重要的一环,它保证了信息的安全性,让他人无法通过抓包来获取通讯的信息也无法通过伪造信息而实现对系统的入侵.其中最为常用的信息传递加密方式就是RS ...
- ThinkPHP3.2 整合支付宝RSA加密方式
RSA核心加密验证算法 <?php /** * RSA签名 * @param $data 待签名数据 * @param $private_key 商户私钥字符串 * return 签名结果 */ ...
- RSA加密的方式和解密方式
RSAsecurity.java package com.mstf.rsa; import java.security.KeyFactory; import java.security.KeyPair ...
- 一篇搞定RSA加密与SHA签名|与Java完全同步
基础知识 什么是RSA?答:RSA是一种非对称加密算法,常用来对传输数据进行加密,配合上数字摘要算法,也可以进行文字签名. RSA加密中padding?答:padding即填充方式,由于RSA加密算法 ...
随机推荐
- ubuntu mysql 通过ip登录指南
详细步骤: 1. 安装mysql 首先,在ubuntu上安装mysql,打开终端,并执行以下命令: 1 sudo apt-get update 2 sudo apt-get install mysql ...
- KKRT-PSI
KKRT库:https://github.com/osu-crypto/BaRK-OPRF 文章:Efficient Batched Oblivious PRF with Applications t ...
- 安装WindowsXP系统
重点 1.虚拟磁盘类型必须选IDE,不然会找不到磁盘 2.下载地址:链接 ,提取码: 592u 3.可以将这个系统作成一个装机PE[大白菜] 4.安装成功后,调节分辨率时,安装VWmare Tool工 ...
- Tesseract-OCR使用有感
这玩意儿就只有一个Tesseract.dll 就算有其它的加上x64目录下的另外两个dll leptonica-1.80.0.dll tesseract41.dll也不过几兆而已,但是 但是 但是 ...
- 无耳科技 Solon v3.0.7 发布(2025农历新年版)
Solon 框架! Solon 框架由杭州无耳科技有限公司(下属 Noear 团队)开发并开源.是新一代,面向全场景的 Java 企业级应用开发框架.从零开始构建(非 java-ee 架构),有灵活的 ...
- PHP常量与数据类型
PHP常量与数据类型 PHP常量 在PHP中,常量是值在脚本执行期间不会改变的量.常量使用define()函数或const关键字来定义. 使用define()函数: define("GREE ...
- Q:Linux查看进程启动服务的精确时间
输入命令 获取进程号 #1#获取进程号ps -ef|grep java|grep 进程名#2#获取启动时间ps -p 进程号 -o lstart 展示启动时间:星期 月 日 小时:分钟:秒 年 一键 ...
- 洛谷B3843 [GESP202306 三级] 密码合规 题解
原题传送门 前言 咳咳,由于本人最近在备考GESP三级,所以可能会有很多水的题解.(见谅--见谅--) 由于今天刚刚重新刷了一遍此题,所以记忆犹新.(太菜了!一个测试点都能 WA ) 题目解析 简单的 ...
- Android应用借助LinearLayout实现垂直水平居中布局
首先说的是LinearLayout布局下的居中一般是这样的: (注意:android:layout_width="fill_parent" android:layout_heigh ...
- PowerShell实现读取照片并做灰度处理
Powershell一直是我的学习目标.做一个小例子.PowerShell实现读取照片并做灰度处理.还想要保存这张灰度照片并直接打开查看. 分析需求: [读取照片] 需要借助.net framewo ...
