Nmap扫描与Tcpdump抓包分析
扫描与抓包分析
3.1 问题
本案例要求熟悉Linux主机环境下的常用安全工具,完成以下任务操作:
- 使用NMAP扫描来获取指定主机/网段的相关信息
- 使用EtterCAP截获明文通信的密码、检测非加密通信的脆弱性
- 使用Tcpdump分析FTP访问中的明文交换信息
3.2 方案
使用两台RHEL6虚拟机,其中svr5作为扫描、嗅探、抓包的操作用机,而mail作为测试用的靶机;另外准备一台Windows客户机pc120,也可以作为靶机
3.3 步骤
实现此案例需要按照如下步骤进行。
步骤一:使用NMAP扫描来获取指定主机/网段的相关信息
1)检查目标主机mail所开启的TCP服务
[root@svr5 ~]# nmap 192.168.4.100
Starting Nmap 5.51 ( http://nmap.org ) at 2015-05-17 17:55 CST
Nmap scan report for 192.168.4.100
Host is up (.00028s latency).
Not shown: closed ports
PORT STATE SERVICE
/tcp open ftp
/tcp open ssh
/tcp open smtp
/tcp open http
/tcp open pop3
/tcp open rpcbind
/tcp open imap
/tcp open https
/tcp open imaps
/tcp open pop3s
MAC Address: :0C:::BE: (VMware)
Nmap done: IP address ( host up) scanned in 1.31 seconds
2)检查192.168.4.0/24网段内哪些主机开启了FTP、SSH服务
[root@svr5 ~]# nmap -p - 192.168.4.0/
Starting Nmap 5.51 ( http://nmap.org ) at 2015-05-17 18:00 CST
Nmap scan report for 192.168.4.1
Host is up (.000025s latency).
PORT STATE SERVICE
/tcp open ftp
/tcp open ssh
Nmap scan report for 192.168.4.5
Host is up.
PORT STATE SERVICE
/tcp filtered ftp
/tcp filtered ssh
Nmap scan report for 192.168.4.120
Host is up (.00052s latency).
PORT STATE SERVICE
/tcp open ftp
/tcp open ssh
MAC Address: :0C:::BE: (VMware)
Nmap scan report for pc110.tarena.com (192.168.4.110)
Host is up (.00038s latency).
PORT STATE SERVICE
/tcp closed ftp
/tcp closed ssh
MAC Address: :::C0:: (VMware)
Nmap scan report for 192.168.4.120
Host is up (.00051s latency).
PORT STATE SERVICE
/tcp closed ftp
/tcp closed ssh
MAC Address: :0C::DB:: (VMware)
Nmap done: IP addresses ( hosts up) scanned in 4.88 seconds
3)检查192.168.4.0/24网段内哪些主机可以ping通
[root@svr5 ~]# nmap -n -sP 192.168.4.0/
Starting Nmap 5.51 ( http://nmap.org ) at 2015-05-17 18:01 CST
Nmap scan report for 192.168.4.1
Host is up.
Nmap scan report for 192.168.4.5
Host is up.
Nmap scan report for 192.168.4.120
Host is up (.00027s latency).
MAC Address: :0C:::BE: (VMware)
Nmap scan report for 192.168.4.110
Host is up (.00016s latency).
MAC Address: :::C0:: (VMware)
Nmap scan report for 192.168.4.120
Host is up (.00046s latency).
MAC Address: :0C::DB:: (VMware)
Nmap done: IP addresses ( hosts up) scanned in 3.57 seconds
4)全面分析目标主机192.168.4.100、192.168.4.120的操作系统信息
[root@svr5 ~]# nmap -A 192.168.4.100,
Starting Nmap 5.51 ( http://nmap.org ) at 2015-05-17 18:03 CST
Nmap scan report for 192.168.4.100 //主机mail的扫描报告
Host is up (.0016s latency).
Not shown: closed ports
PORT STATE SERVICE VERSION
/tcp open ftp vsftpd 2.2.
| ftp-anon: Anonymous FTP login allowed (FTP code )
| -rw-r--r-- Aug : UserB.pub
| -rw-r--r-- Aug : dl.txt
| drwxr-xr-x Aug : pub
| -rw-rw-r-- Aug : tools-1.2..tar.gz
|_-rw-rw-r-- Aug : tools-1.2..tar.gz.sig
/tcp open ssh OpenSSH 5.3 (protocol 2.0)
| ssh-hostkey: :be:d6::c1:2d:d9:1f::2f::d1:af:a8:d3:c6 (DSA)
|_2048 :0a:::fa:bb::1d:cc:ab::::f9::4f (RSA)
/tcp open smtp Postfix smtpd
/tcp open http Apache httpd 2.2. ((Red Hat))
|_http-methods: No Allow or Public header in OPTIONS response (status code )
| http-title: Found
|_Did not follow redirect to https://192.168.4.100//
/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: USER CAPA UIDL TOP OK(K) RESP-CODES PIPELINING STLS SASL(PLAIN)
/tcp open rpcbind
/tcp open imap Dovecot imapd
|_imap-capabilities: LOGIN-REFERRALS STARTTLS IMAP4rev1 ENABLE AUTH=PLAIN LITERAL+ IDLE SASL-IR ID
/tcp open ssl/http Apache httpd 2.2. ((Red Hat))
| http-methods: Potentially risky methods: TRACE
|_See http://nmap.org/nsedoc/scripts/http-methods.html
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
/tcp open ssl/imap Dovecot imapd
|_imap-capabilities: IMAP4rev1 AUTH=PLAIN ENABLE ID LITERAL+ IDLE SASL-IR LOGIN-REFERRALS
/tcp open ssl/pop3 Dovecot pop3d
|_pop3-capabilities: OK(K) CAPA RESP-CODES UIDL PIPELINING USER TOP SASL(PLAIN)
MAC Address: :0C:::BE: (VMware)
No exact OS matches for host (If you know what OS is running on it, see http://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=5.51%D=/%OT=%CT=%CU=%PV=Y%DS=%DC=D%G=Y%M=000C29%TM=
OS:11ED90%P=x86_64-redhat-linux-gnu)SEQ(SP=%GCD=%ISR=10B%TI=Z%CI=Z%II=I
OS:%TS=A)OPS(O1=M5B4ST11NW6%O2=M5B4ST11NW6%O3=M5B4NNT11NW6%O4=M5B4ST11NW6%O
OS:=M5B4ST11NW6%O6=M5B4ST11)WIN(W1=%W2=%W3=%W4=%W5=%W6
OS:=)ECN(R=Y%DF=Y%T=%W=%O=M5B4NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=%S=O
OS:%A=S+%F=AS%RD=%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=%W=%S=A%A=Z%F=R%O=%RD=
OS:%Q=)T5(R=Y%DF=Y%T=%W=%S=Z%A=S+%F=AR%O=%RD=%Q=)T6(R=Y%DF=Y%T=%W=%
OS:S=A%A=Z%F=R%O=%RD=%Q=)T7(R=Y%DF=Y%T=%W=%S=Z%A=S+%F=AR%O=%RD=%Q=)U1(
OS:R=Y%DF=N%T=%IPL=%UN=%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=
OS:N%T=%CD=S)
Network Distance: hop
Service Info: Host: mail.tarena.com; OS: Unix
TRACEROUTE
HOP RTT ADDRESS
1.55 ms 192.168.4.100
Nmap scan report for 192.168.4.120 //主机pc120的扫描报告
Host is up (.00047s latency).
Not shown: closed ports
PORT STATE SERVICE VERSION
/tcp open msrpc Microsoft Windows RPC
/tcp open netbios-ssn
/tcp open microsoft-ds Microsoft Windows XP microsoft-ds
MAC Address: :0C::DB:: (VMware)
Device type: general purpose
Running: Microsoft Windows XP
OS details: Microsoft Windows XP SP2 - SP3
Network Distance: hop
Service Info: OS: Windows
Host script results:
|_nbstat: NetBIOS name: PC-, NetBIOS user: <unknown>, NetBIOS MAC: :0c::db:: (VMware)
|_smbv2-enabled: Server doesn't support SMBv2 protocol
| smb-os-discovery:
| OS: Windows XP (Windows LAN Manager)
| Name: WORKGROUP\PC-
|_ System time: -- :: UTC+
TRACEROUTE
HOP RTT ADDRESS
0.47 ms 192.168.4.120
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: IP addresses ( hosts up) scanned in 43.01 seconds
步骤二:使用EtterCAP截获明文通信的密码,检测非加密通信的脆弱性
1)安装EtterCAP嗅探工具
下载(或老师提供)软件包ettercap、依赖包libnet,执行rpm安装。
[root@svr5 ~]# cd /var/ftp/pub
[root@svr5 ~]# rpm -ivh libnet-1.1.-.el6.x86_64.rpm\
> ettercap-0.7.-.el6..20120906gitc796e5.x86_64.rpm
warning: libnet-1.1.-.el6.x86_64.rpm: Header V3 RSA/SHA256 Signature, key ID 0608b895: NOKEY
Preparing... ########################################### [%]
:libnet ########################################### [ %]
:ettercap ########################################### [%]
2)EtterCAP工具的命令行模式
执行ettercap命令,嗅探主机192.168.4.120与主机192.168.4.100的FTP服务(21端口)之间的数据通信,收集用户名、密码信息。
[root@svr5 ~]# ettercap -Tzq /192.168.4.100//21 /192.168.4.120//
ettercap 0.7. copyright - Ettercap Development Team
Listening on:
eth0 -> :0C::AA::
192.168.4.5/255.255.255.0
fe80::20c:29ff:feaa:/
SSL dissection needs a valid 'redir_command_on' script in the etter.conf file
Privileges dropped to UID GID ...
plugin ec_sslstrip.so cannot be loaded...
plugins
protocol dissectors
ports monitored
mac vendor fingerprint
tcp OS fingerprint
known services
Starting Unified sniffing... //进入标准监听状态
Text only Interface activated...
Hit 'h' for inline help
处于监听状态以后,从测试机pc120访问主机mail的vsftpd服务,如图-10所示。
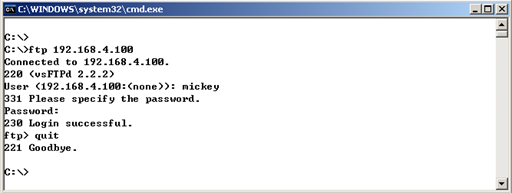

图-10
然后查看执行中的ettercap命令行界面,将会发现收集到的用户名、密码信息。
.. ..
Text only Interface activated...
Hit 'h' for inline help
FTP : 192.168.4.120: -> USER: mickey PASS: pwd123
3)EtterCAP工具的图形模式
在GNOME桌面环境下, 执行ettercap -G即可打开窗口程序。选择菜单“Sniffer”-->“Unified Sniffer”监听,指定网卡eth0;然后添加两个主机192.168.4.100、192.168.4.120作为嗅探目标(Targets),选择“Start”-->“Sniffing“即可进入监听状态。
参考前面的测试操作,再次从客户机pc120访问主机mail的vsftpd服务。然后查看执行中的ettercap监听窗口程序,同样可以收集到用户名、密码信息,如图-11所示。
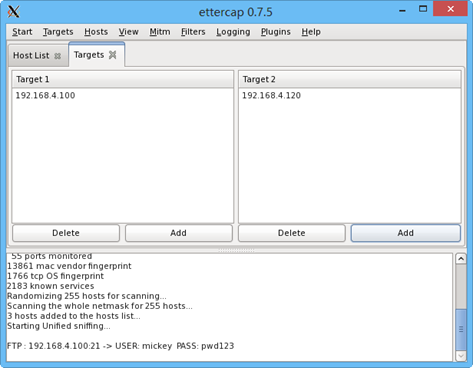

图-11
步骤三:使用Tcpdump分析FTP访问中的明文交换信息
1)启用tcpdump命令行抓包
执行tcpdump命令行,添加适当的过滤条件,只抓取访问主机192.168.4.100的21端口的数据通信 ,并转换为ASCII码格式的易读文本。
[root@svr5 ~]# tcpdump -A host 192.168.4.100 and tcp port
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size bytes
.. .. //进入等待捕获数据包的状态
2)执行FTP访问,并观察tcpdump抓包结果
参考前面的测试操作,再次从客户机pc120访问主机mail的vsftpd服务。然后查看执行中tcpdump程序的输出,仔细分析FTP连接的建立过程、确认收集到的用户名和口令信息。
.. ..
::25.964110 IP 192.168.4.120.novation > 192.168.4.100.ftp: Flags [S], seq , win , options [mss ,nop,wscale ,nop,nop,sackOK], length
E....@.@......x...d.*..G.\b........;...............
::25.964268 IP 192.168.4.100.ftp > 192.168.4.120.novation: Flags [S.], seq , ack , win , options [mss ,nop,nop,sackOK,nop,wscale ], length
E....@.@......d...x...*.1BaG.\c..9.7...............
::25.964436 IP 192.168.4.120.novation > 192.168.4.100.ftp: Flags [.], ack , win , length
E..(..@.@.. ...x...d.*..G.\c.1BbP.............
::25.967592 IP 192.168.4.100.ftp > 192.168.4.120.novation: Flags [P.], seq :, ack , win , length
E..<FJ@.@.jE...d...x...*.1BbG.\cP...V... (vsFTPd 2.2.)
::26.117057 IP 192.168.4.120.novation > 192.168.4.100.ftp: Flags [.], ack , win , length
E..(..@.@......x...d.*..G.\c.1BvP.............
::27.960530 IP 192.168.4.120.novation > 192.168.4.100.ftp: Flags [P.], seq :, ack , win , length
E....@.@......x...d.*..G.\c.1BvP.......USER mickey
::27.960544 IP 192.168.4.100.ftp > 192.168.4.120.novation: Flags [.], ack , win , length
E..(FK@.@.jX...d...x...*.1BvG.\pP.............
::27.960783 IP 192.168.4.100.ftp > 192.168.4.120.novation: Flags [P.], seq :, ack , win , length
E..JFL@.@.j5...d...x...*.1BvG.\pP...i~.. Please specify the password.
::28.085168 IP 192.168.4.120.novation > 192.168.4.100.ftp: Flags [.], ack , win , length
E..(..@.@......x...d.*..G.\p.1B.P.............
::29.657364 IP 192.168.4.120.novation > 192.168.4.100.ftp: Flags [P.], seq :, ack , win , length
E....@.@......x...d.*..G.\p.1B.P.......PASS pwd123
::29.696968 IP 192.168.4.100.ftp > 192.168.4.120.novation: Flags [.], ack , win , length
E..(FM@.@.jV...d...x...*.1B.G.\}P.............
::29.702671 IP 192.168.4.100.ftp > 192.168.4.120.novation: Flags [P.], seq :, ack , win , length
E..?FN@.@.j>...d...x...*.1B.G.\}P....... Login successful.
::29.835258 IP 192.168.4.120.novation > 192.168.4.100.ftp: Flags [.], ack , win , length
E..(..@.@......x...d.*..G.\}.1B.P.............
::31.716375 IP 192.168.4.120.novation > 192.168.4.100.ftp: Flags [P.], seq :, ack , win , length
E.....@.@......x...d.*..G.\}.1B.P... ...QUIT
::31.716532 IP 192.168.4.100.ftp > 192.168.4.120.novation: Flags [.], ack , win , length
E..(FO@.@.jT...d...x...*.1B.G.\.P....}........
::31.716634 IP 192.168.4.100.ftp > 192.168.4.120.novation: Flags [P.], seq :, ack , win , length
E..6FP@.@.jE...d...x...*.1B.G.\.P....... Goodbye.
::31.716677 IP 192.168.4.100.ftp > 192.168.4.120.novation: Flags [F.], seq , ack , win , length
E..(FQ@.@.jR...d...x...*.1B.G.\.P....n........
::31.717053 IP 192.168.4.120.novation > 192.168.4.100.ftp: Flags [.], ack , win , length
E..(..@.@......x...d.*..G.\..1B.P.............
::31.718796 IP 192.168.4.120.novation > 192.168.4.100.ftp: Flags [F.], seq , ack , win , length
E..(..@.@......x...d.*..G.\..1B.P.............
::31.719097 IP 192.168.4.100.ftp > 192.168.4.120.novation: Flags [.], ack , win , length
E..(..@.@......d...x...*.1B.G.\.P....m........
Nmap扫描与Tcpdump抓包分析的更多相关文章
- Wireshark和TcpDump抓包分析心得
Wireshark和 TcpDump抓包分析心得 1. Wireshark与tcpdump介绍 Wireshark是一个网络协议检测工具,支持Windows平台和Unix平台,我一般只在Window ...
- 转:tcpdump抓包分析(强烈推荐)
转自:https://mp.weixin.qq.com/s?__biz=MzAxODI5ODMwOA==&mid=2666539134&idx=1&sn=5166f0aac71 ...
- 转 Wireshark和TcpDump抓包分析心得
1. Wireshark与tcpdump介绍 Wireshark是一个网络协议检测工具,支持Windows平台和Unix平台,我一般只在Windows平台下使用Wireshark,如果是Linux的话 ...
- 使用 tcpdump 抓包分析 TCP 三次握手、四次挥手与 TCP 状态转移
目录 文章目录 目录 前文列表 TCP 协议 图示三次握手与四次挥手 抓包结果 抓包分析 TCP 三次握手 数据传输 四次挥手 TCP 端口状态转移 状态转移 前文列表 <常用 tcpdump ...
- Nmap 常用命令及抓包分析
1.主机发现:主机发现也称为ping扫描,但是Nmap中主机发现的技术已经不是简单的采用ping工具发送简单的ICMP回声请求报文.用户完全可以通过使用列表扫描(-sL)或者通过关闭ping(-P0) ...
- TCP三次握手与Tcpdump抓包分析过程
一.TCP连接建立(三次握手) 过程 客户端A,服务器B,初始序号seq,确认号ack 初始状态:B处于监听状态,A处于打开状态 A -> B : seq = x (A向B发送连接请求报文段,A ...
- linux下使用tcpdump抓包分析tcp的三次握手
首先贴上tcp 三次握手的原理图服务器开启ftp服务并执行tcpdump抓包服务器:192.168.3.14 ftp服务客户端:192.168.3.100 服务器执行以下命令,客户端访问服务器ftp: ...
- [转]Linux操作系统tcpdump抓包分析详解
PS:tcpdump是一个用于截取网络分组,并输出分组内容的工具,简单说就是数据包抓包工具.tcpdump凭借强大的功能和灵活的截取策略,使其成为Linux系统下用于网络分析和问题排查的首选工具. t ...
- tcpdump抓包分析具体解释
說實在的,對於 tcpdump 這個軟體來說,你甚至能够說這個軟體其實就是個駭客軟體, 因為他不但能够分析封包的流向,連封包的內容也能够進行『監聽』, 假设你使用的傳輸資料是明碼的話,不得了,在 ro ...
随机推荐
- go导入包
go导入包 go有很多内置的函数,例如println,不需要引用即可使用.但是如果不借助go的标准库或者第三方库,我们能做的事情有限.在go中,使用关键字import在代码中导入一个包并使用. 修改我 ...
- jsp中提供的四种属性范围
参考:http://www.cnblogs.com/xdp-gacl/p/3781056.html 1.当前页:一个属性只能在一个页面中取得,跳转到其他页面无法取得 2.一次服务器请求:一个页面中设置 ...
- tarjan求强连通+缩点——cf1248E
这题好像是DEF里最水的,, /* 建图:如果a认识b,那么从a->b连一条边,将点分成两个集合A,B,没有从A->B的边 求出强连通分量,再造一张新图,新图中任取一个的出度为0的点作为集 ...
- springboot之停止与启动服务的脚本
最近要开始自动化部署了,我们要编写杀死服务的脚本. 我在windows写好的脚本拷贝到linux,就是不行,好像是因为转义字符吧. 然后,我就手敲了这个下面脚本: pid=`ps -ef|grep / ...
- postgresql数字类型
postgresql的数据类型很多,也可以使用create type命令创建自定义数据类型,但常用的数据类型是以下三种: l 数字数据类型 l 字符串数据类型 l 日期/时间数据类型 数字数据类 ...
- thinkphp+layui多图上传(1)thinkphp5+layui实现多图上传保存到数据库,可以实现图片自由排序,自由删除。
公共css代码 <style> .layui-upload-img { width: 90px; height: 90px; margin: 0; } .pic-more { width: ...
- 正则表达式替换字符串中的html标签
正则表达式替换字符串中的html标签 ··· var newStr = str.replace(/<[^>]+>/g, ''); ···
- DOS和DDOS攻击
1.什么是DOS攻击 首先注意这里是DOS(Denial Of Service)攻击,并非DoS.DoS是微软早期的系统版本. DoS即Denial Of Service,拒绝服务的缩写.DoS是指故 ...
- ( 转)WPF面板布局介绍Grid、StackPanel、DockPanel、WrapPanel
回顾 上一篇,我们介绍了基本控件及控件的重要属性和用法,我们本篇详细介绍WPF中的几种布局容器及每种布局容器的使用场景,当 然这些都是本人在实际项目中的使用经验,可能还存在错误之处,还请大家指出. 本 ...
- 将本地已有的一个项目上传到新建的git仓库的方法
将本地已有的一个非git项目上传到新建的git仓库的方法一共有两种. 一. 克隆+拷贝 第一种方法比较简单,直接用把远程仓库拉到本地,然后再把自己本地的项目拷贝到仓库中去.然后push到远程仓库上去即 ...
