【洛谷3546_BZOJ2803】[POI2012]PRE-Prefixuffix(String Hash)
Problem:
Analysis:
I gave up and saw other's solution when I had nearly thought of the method ... What a pity
Let's define a border of string \(s\) as a prefix \(p\) of \(s\) that \(p\) is also a suffix of \(s\), and \(p\) is not longer than half of \(s\). What the problem asked us to look for is a number \(L\), that the prefix of length \(L\) can be divided into two string \(s1\) and \(s2\) , and the suffix of length \(L\) can be divided into two string \(s2\) and \(s1\), so that this pair of prefix and suffix is cyclically equivalent. Obviously, \(s1\) is a border of string \(s\). Another fact is, if \(s1\) is of length \(len\), \(s2\) is a border of the substring \([len, n - len - 1]\). Define \(f[len]\) as the length of the maximum border of the substring \([len, n - len - 1]\) . Let's enumerate the length of \(s1\) as \(len\) brutely, and for all legal \(len\) ("legal" means the prefix of length \(len\) is a border of \(s\). We can check it by hashing in \(O(1)\) time), the answer is \(len + f[len]\).
Now the problem is how to calculate \(f[len]\). Brute force takes \(O(n^2)\) complexity, but the useful fact below can decrease the complexity to \(O(n)\) :
\]
To make it easy, look at the (beautiful) picture below.
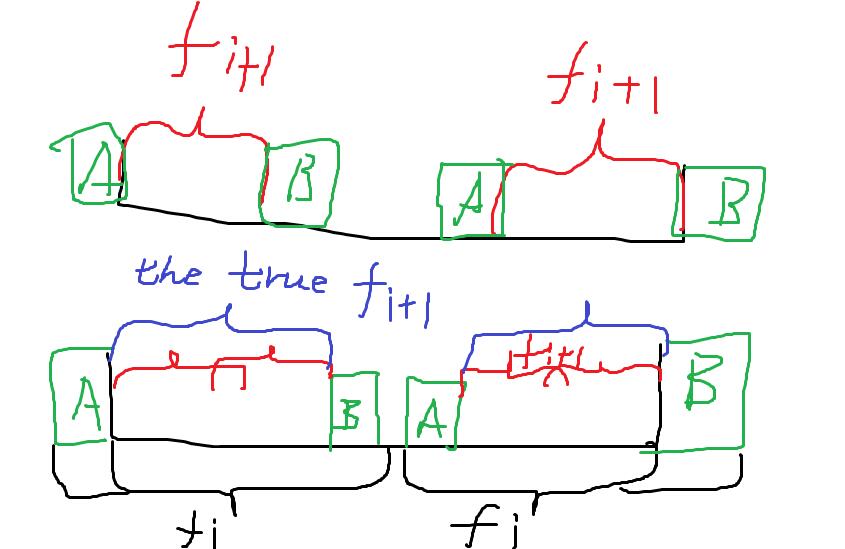
The first picture shows the situation when \(f[i]=f[i+1]+2\), and the second picture shows if \(f[i]\) (the black ones) is more than \(f[i+1]\) (the red ones) plus \(2\) , the \(f[i+1]\) must be wrong, for there's a longer border (the blue ones) of substring \([i+1, n-i-2]\).
Because of this fact, we can solve \(f[len]\) in \(O(n)\) time. We initialize \(f[i]\) as \(f[i+1]+2\), and decrease it until the substring \([i, n-i-1]\) has a border of length \(f[i]\). The proof of the complexity is similar to the one of solving \(height\) array by Suffix Array.
Code:
#include <cstdio>
#include <algorithm>
#include <cstring>
#include <cctype>
using namespace std;
namespace zyt
{
template<typename T>
inline bool read(T &x)
{
char c;
bool f = false;
x = 0;
do
c = getchar();
while (c != EOF && c != '-' && !isdigit(c));
if (c == EOF)
return false;
if (c == '-')
f = true, c = getchar();
do
x = x * 10 + c - '0', c = getchar();
while (isdigit(c));
if (f)
x = -x;
return true;
}
inline bool read(char *const s)
{
return ~scanf("%s", s);
}
template<typename T>
inline void write(T x)
{
static char buf[20];
char *pos = buf;
if (x < 0)
putchar('-'), x = -x;
do
*pos++ = x % 10 + '0';
while (x /= 10);
while (pos > buf)
putchar(*--pos);
}
const int N = 1e6 + 10;
int f[N], n;
// f[i] is the maximum length of the border of substr[i, n - i - 1]
char str[N];
namespace Hash
{
typedef long long ll;
typedef pair<int, int> pii;
typedef pii hash_t;
hash_t h[N], pow[N];
const hash_t seed = hash_t(61, 67), p = hash_t(1e9 + 7, 1e9 + 9);
hash_t operator + (const hash_t &a, const hash_t &b)
{
return hash_t((a.first + b.first) % p.first, (a.second + b.second) % p.second);
}
hash_t operator - (const hash_t &a, const hash_t &b)
{
return hash_t((a.first - b.first + p.first) % p.first,
(a.second - b.second + p.second) % p.second);
}
hash_t operator * (const hash_t &a, const hash_t &b)
{
return hash_t(int((ll)a.first * b.first % p.first),
int((ll)a.second * b.second % p.second));
}
void init()
{
pow[0] = make_pair(1, 1);
for (int i = 1; i < N; i++)
pow[i] = pow[i - 1] * seed;
}
inline int ctoi(const char c)
{
return c - 'a';
}
void get(const char *const s)
{
h[0] = make_pair(ctoi(s[0]), ctoi(s[0]));
for (int i = 1; i < n; i++)
h[i] = h[i - 1] * seed + make_pair(ctoi(s[i]), ctoi(s[i]));
}
hash_t extract(const int l, const int r)
{
return l ? (h[r] - h[l - 1] * pow[r - l + 1]) : h[r];
}
}
using namespace Hash;
void mk_f()
{
f[n >> 1] = 0;
for (int i = (n >> 1) - 1; i >= 0; i--)
{
f[i] = min(f[i + 1] + 2, (n >> 1) - i);
while (f[i] && extract(i, i + f[i] - 1) != extract(n - i - f[i], n - i - 1))
--f[i];
}
}
int work()
{
read(n), read(str);
init();
get(str);
mk_f();
int ans = 0;
for (int i = 1; i <= (n >> 1); i++)
if (extract(0, i - 1) == extract(n - i, n - 1))
ans = max(ans, i + f[i]);
write(ans);
return 0;
}
}
int main()
{
return zyt::work();
}
【洛谷3546_BZOJ2803】[POI2012]PRE-Prefixuffix(String Hash)的更多相关文章
- 洛谷P3538 [POI2012]OKR-A Horrible Poem [字符串hash]
题目传送门 A Horrible Poem 题目描述 Bytie boy has to learn a fragment of a certain poem by heart. The poem, f ...
- 洛谷P3237 米特运输 [HNOI2014] hash/二进制分解
正解:hash/二进制分解 解题报告: 传送门! umm首先提取下题意趴QAQ 大概是说给一棵树,每个点有一个权值,要求修改一些点的权值,使得同一个父亲的儿子权值相同,且父亲的权值必须是所有儿子权值之 ...
- 洛谷P1117 优秀的拆分【Hash】【字符串】【二分】【好难不会】
题目描述 如果一个字符串可以被拆分为AABBAABB的形式,其中 A和 B是任意非空字符串,则我们称该字符串的这种拆分是优秀的. 例如,对于字符串aabaabaaaabaabaa,如果令 A=aabA ...
- 洛谷 P3539 [POI2012]ROZ-Fibonacci Representation 解题报告
P3539 [POI2012]ROZ-Fibonacci Representation 题意:给一个数,问最少可以用几个斐波那契数加加减减凑出来 多组数据10 数据范围1e17 第一次瞬间yy出做法, ...
- 洛谷P3533 [POI2012]RAN-Rendezvous
P3533 [POI2012]RAN-Rendezvous 题目描述 Byteasar is a ranger who works in the Arrow Cave - a famous rende ...
- 洛谷P3531 [POI2012]LIT-Letters
题目描述 Little Johnny has a very long surname. Yet he is not the only such person in his milieu. As it ...
- BZOJ2801/洛谷P3544 [POI2012]BEZ-Minimalist Security(题目性质发掘+图的遍历+解不等式组)
题面戳这 化下题面给的式子: \(z_u+z_v=p_u+p_v-b_{u,v}\) 发现\(p_u+p_v-b_{u,v}\)是确定的,所以只要确定了一个点\(i\)的权值\(x_i\),和它在同一 ...
- 洛谷P3539 [POI2012] ROZ-Fibonacci Representation
题目传送门 转载自:five20,转载请注明出处 本来看到这题,蒟蒻是真心没有把握的,还是five20大佬巨orz 首先由于斐波拉契数的前两项是1,1 ,所以易得对于任何整数必能写成多个斐波拉契数加减 ...
- 洛谷P3537 [POI2012]SZA-Cloakroom(背包)
传送门 蠢了……还以为背包只能用来维护方案数呢……没想到背包这么神奇…… 我们用$dp[i]$表示当$c$的和为$i$时,所有的方案中使得最小的$b$最大时最小的$b$是多少 然后把所有的点按照$a$ ...
随机推荐
- docker插件
import docker c = docker.Client(base_url='unix://var/run/docker.sock',version='1.15',timeout=10) pri ...
- jmeter录制火狐浏览器
昨天看youtube,居然发现有这功能,啊哈哈 听不懂英语 也能有收获. 一.Jmeter 文件中选择Templates->Recording 二.创建之后,自动出现一个模板: 1. Threa ...
- python 配置文件 ConfigParser模块
ConfigParser模块 用于生成和修改常见配置文档,当前模块的名称在 python 3.x 版本中变更为 configparser. 来看一个好多软件的常见文档格式如下 [DEFAULT] Se ...
- Turtle-可视化界面画圣诞树
圣诞节(Christmas)又称耶诞节.耶稣诞辰,译名为“基督弥撒”,是西方传统节日,起源于基督教,在每年公历12月25日.弥撒是教会的一种礼拜仪式.圣诞节是一个宗教节,因为把它当作耶稣的诞辰来庆祝, ...
- [置顶]
Linux学习总结(20)——Linux 文件夹结构和作用
/bin 二进制可执行命令 /dev 设备特殊文件 /etc 系统管理和配置文件 /etc/rc.d 启动的配置文件和脚本 /home 用户主目录的基点,比如用户user的主目录就是/home/us ...
- Leetcode 135.分糖果
分发糖果 老师想给孩子们分发糖果,有 N 个孩子站成了一条直线,老师会根据每个孩子的表现,预先给他们评分. 你需要按照以下要求,帮助老师给这些孩子分发糖果: 每个孩子至少分配到 1 个糖果. 相邻的孩 ...
- codeforces gym 100357 K (表达式 模拟)
题目大意 将一个含有+,-,^,()的表达式按照运算顺序转换成树状的形式. 解题分析 用递归的方式来处理表达式,首先直接去掉两边的括号(如果不止一对全部去光),然后找出不在括号内且优先级最低的符号.如 ...
- [bzoj2097][Usaco2010 Dec]Exercise 奶牛健美操_贪心_树形dp_二分
Exercise bzoj-2097 Usaco-2010 Dec 题目大意:题目链接 注释:略. 想法:题目描述生怕你不知道这题在考二分. 关键是怎么验证?我们想到贪心的删边. 这样的策略是显然正确 ...
- Ubuntu 16.04安装uGet替代迅雷,并在Chrome中设置为默认下载器
uGet是采用aria2作为下载后端,所以两个软件都必须同时安装. 1.安装uGet sudo add-apt-repository ppa:plushuang-tw/uget-stable sudo ...
- react-浏览后的想法
