linux c 及 c++打印调用者函数caller function的方法,包括arm c平台
一般情况下,编译的时候可能需要加 -g 选项,对于android ndk的-g选项添加请参见android类目下的另一篇文章。
以下文章中的__builtin_return_address() 宏,若要确认它是否在编译器源码中存在,可以在编译器源码中搜索 return_address, 若找到则可以直接使用(不同架构的编译器调用方法可能不同),而且同时也搜索到了需要包含哪些头文件。
__builtin_return_address() 宏简单好用,如果只支持层级0,则只有不断的循环用0来找调用者的调用者了。
http://codingrelic.geekhold.com/2009/05/pre-mortem-backtracing.html
A backtrace is often the first step in debugging a problem. Generating a backtrace is generally thought of as a function of the debugger, on a core file after a process has died. However it is sometimes quite useful to generate a live backtrace while a process runs. For example, crashing the process in the field may not be acceptable if a problem is survivable. Logging a backtrace and other information can provide enough to locate the root cause, without having to trigger any customer downtime.
gcc backtrace support
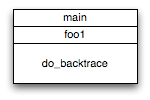 The simplest way to get a crude backtrace is the __builtin_return_address() macro supplied by gcc. You provide the frame number you want to retrieve, and get the return address for that stack frame:
The simplest way to get a crude backtrace is the __builtin_return_address() macro supplied by gcc. You provide the frame number you want to retrieve, and get the return address for that stack frame:
void do_backtrace2()
{
void *pc0 = __builtin_return_address(0);
void *pc1 = __builtin_return_address(1);
void *pc2 = __builtin_return_address(2);
void *pc3 = __builtin_return_address(3); printf("Frame 0: PC=%p\n", pc0);
printf("Frame 1: PC=%p\n", pc1);
printf("Frame 2: PC=%p\n", pc2);
printf("Frame 3: PC=%p\n", pc3);
}
This code will produce the following output:
Frame 0: PC=0x80483ca
Frame 1: PC=0x80483e1
Frame 2: PC=0x62079d
Frame 3: PC=0x80482b9
__builtin_return_address() has significant limitations. It constructs code at compile time to walk back through the stack frames. That means you cannot use a variable in a loop, you can only use integer constants like the 0,1,2,3 shown above. Also on some architectures, including my beloved MIPS, only __builtin_return_address(0) works. MIPS has no frame pointer, making it difficult to walk back up the stack. Frame 0 can use the return address register directly.
glibc's backtrace()
glibc contains a simple backtrace function, which is somewhat more powerful than __builtin_return_address(). The backtrace() call populates an array with the program counter of each calling function, while a separate backtrace_symbols() call can look up the symbolic names for each address:
#include <execinfo.h> #define BACKTRACE_SIZ 64
void do_backtrace()
{
void *array[BACKTRACE_SIZ];
size_t size, i;
char **strings; size = backtrace(array, BACKTRACE_SIZ);
strings = backtrace_symbols(array, size); for (i = 0; i < size; i++) {
printf("%p : %s\n", array[i], strings[i]);
} free(strings); // malloced by backtrace_symbols
}
The output shows the backtrace with the address of each function call site:
# gcc -g -o backtrace ./backtrace.c
# ./backtrace
0x8048422 : ./backtrace(backtrace_symbols+0xd6) [0x8048422]
0x80484be : ./backtrace(backtrace_symbols+0x172) [0x80484be]
0x80484d5 : ./backtrace(backtrace_symbols+0x189) [0x80484d5]
0x071479d : /lib/tls/libc.so.6(__libc_start_main+0xed) [0x71479d]
0x804837d : ./backtrace(backtrace_symbols+0x31) [0x804837d]
To get useful symbolic names, the -rdynamic option must be passed to the linker:
# gcc -g -rdynamic -o backtrace ./backtrace.c
# ./backtrace
0x804874a : ./backtrace(do_backtrace+0x1a) [0x804874a]
0x80487e6 : ./backtrace(foo1+0xb) [0x80487e6]
0x80487fd : ./backtrace(main+0x15) [0x80487fd]
0x012679d : /lib/tls/libc.so.6(__libc_start_main+0xed) [0x12679d]
0x80486a5 : ./backtrace(backtrace_symbols+0x31) [0x80486a5]
There is also a backtrace_symbols_fd() function, which nicely prints the output to a file descriptor without having to malloc a table of strings. If thats all you're trying to do, it is a simpler API.
As an aside: notice how the address of __libc_start_main varies in the examples above, 0x62079d versus 0x71479d versus 0x12679d? That is address space randomization in action. libc is mapped at a randomized base address every time a binary is started. The offset of __libc_start_main within the page is a constant 0x79d, but the upper bits of the address will vary from one run to the next. This helps prevent buffer overflow and other code injection attacks, by randomizing the address of library routines.
libunwind
libunwind is a library for extracting call chain information. It supports many different CPU architectures. Here is an example of using libunwind to accomplish a similar result as glibc's backtrace() function:
#include <libunwind.h> void do_backtrace2()
{
unw_cursor_t cursor;
unw_context_t context; unw_getcontext(&context);
unw_init_local(&cursor, &context); while (unw_step(&cursor) > 0) {
unw_word_t offset, pc;
char fname[64]; unw_get_reg(&cursor, UNW_REG_IP, &pc); fname[0] = '\0';
(void) unw_get_proc_name(&cursor, fname, sizeof(fname), &offset); printf ("%p : (%s+0x%x) [%p]\n", pc, fname, offset, pc);
}
}
The output:
0x80486b3 : (foo+0xb) [0x80486b3]
0x80486ca : (main+0x15) [0x80486ca]
0x016379d : (__libc_start_main+0xed) [0x16379d]
0x80484c9 : (_start+0x21) [0x80484c9]
That is quite a bit more code to get a simple backtrace, but libunwind offers more capability to examine the program state at each frame. For example, one can print the saved register values:
#include <libunwind.h> void do_backtrace2()
{
unw_cursor_t cursor;
unw_context_t context; unw_getcontext(&context);
unw_init_local(&cursor, &context);
while (unw_step(&cursor) > 0) {
unw_word_t offset;
unw_word_t pc, eax, ebx, ecx, edx;
char fname[64]; unw_get_reg(&cursor, UNW_REG_IP, &pc);
unw_get_reg(&cursor, UNW_X86_EAX, &eax);
unw_get_reg(&cursor, UNW_X86_EDX, &edx);
unw_get_reg(&cursor, UNW_X86_ECX, &ecx);
unw_get_reg(&cursor, UNW_X86_EBX, &ebx); fname[0] = '\0';
unw_get_proc_name(&cursor, fname, sizeof(fname), &offset);
printf ("%p : (%s+0x%x) [%p]\n", pc, fname, offset, pc);
printf("\tEAX=0x%08x EDX=0x%08x ECX=0x%08x EBX=0x%08x\n",
eax, edx, ecx, ebx);
}
}
The output:
0x80486b3 : (foo1+0xb) [0x80486b3]
EAX=0x00000000 EDX=0x00b548b0 ECX=0x00000000 EBX=0x00000000
0x80486ca : (main+0x15) [0x80486ca]
EAX=0x00000000 EDX=0x00b548b0 ECX=0x00000000 EBX=0x00000000
0x044879d : (__libc_start_main+0xed) [0x44879d]
EAX=0x00000000 EDX=0x003368b0 ECX=0x00000000 EBX=0x00000000
0x80484c9 : (_start+0x21) [0x80484c9]
EAX=0x00000000 EDX=0x00b548b0 ECX=0x00000000 EBX=0x00000000
When would this be useful? Given the relative costs, it is not unusual to have an embedded CPU with considerably more RAM than flash. In the event of a crash there may not be enough flash to save a full core file. Having the process deliberately catch SIGSEGV and dump its own backtrace with register values means you'd at least have something to work with even if there is no core file.
Conclusion
Over time I think I have used __builtin_return_address(0) more often than any of the other techniques. Whether constructing simple performance instrumentation or logging problems from the field, knowing the caller has often been sufficient. For more extensive backtrace functionality I end up using libunwind. The backtrace() function in glibc always seems to be too heavy for the simple stuff yet not sufficient for the complex stuff.
linux c 及 c++打印调用者函数caller function的方法,包括arm c平台的更多相关文章
- 【Linux开发】为qt-embedded添加jpeg库的交叉编译方法for arm
看了一个文章: =====================================谢论坛内各位的帮助,我的qt/e2.3.10和qtopia2.1.1终于全部编译通过. 下面是jpeg和uui ...
- Linux 内核启动信息的打印 --- dev_driver_string函数/dev_name函数
内核启动时,常会打印出一些信息:开头是 "驱动模块的名字: + 具体的信息" 如:在运行的linux系统设备上,插入鼠标,就会打印出鼠标的相关信息; [ 402.134068] i ...
- 使用linux backtrace打印出错函数堆栈信息
一般察看函数运行时堆栈的方法是使用GDB(bt命令)之类的外部调试器,但是,有些时候为了分析程序的BUG,(主要针对长时间运行程序的分析),在程序出错时打印出函数的调用堆栈是非常有用的. 在glibc ...
- linux 内核(驱动)常用函数
2.4.1 内存申请和释放 include/linux/kernel.h里声明了kmalloc()和kfree().用于在内核模式下申请和释放内存. void *kmalloc(unsigned ...
- PHP 打印调用函数入口地址(堆栈)
今天网站出现一个BUG,然后直接在数据库类里面写日志,看是哪条SQL出了问题,SQL语句到是找到了,但是不知道这条SQL语句来自何处,于是就想啊,如果能有一个办法,查看当前正在运行的这个方法是被哪个方 ...
- linux下c程序调用reboot函数实现直接重启【转】
转自:http://www.blog.chinaunix.net/uid-20564848-id-73878.html linux下c程序调用reboot函数实现直接重启 当然你也可以直接调用syst ...
- PHP 打印调用函数入口地址(堆栈),方便调式
今天网站出现一个BUG,然后直接在数据库类里面写日志,看是哪条SQL出了问题,SQL语句到是找到了,但是不知道这条SQL语句来自何处,于是就想啊,如果能有一个办法,查看当前正在运行的这个方法是被哪个方 ...
- linux网络编程九:splice函数,高效的零拷贝
from:http://blog.csdn.net/jasonliuvip/article/details/22600569 linux网络编程九:splice函数,高效的零拷贝 最近在看<Li ...
- Linux pwn入门教程(10)——针对函数重定位流程的几种攻击
作者:Tangerine@SAINTSEC 本系列的最后一篇 感谢各位看客的支持 感谢原作者的付出一直以来都有读者向笔者咨询教程系列问题,奈何该系列并非笔者所写[笔者仅为代发]且笔者功底薄弱,故无法解 ...
随机推荐
- Python按照索引访问list
由于list是一个有序集合,所以,我们可以用一个list按分数从高到低表示出班里的3个同学: >>> L = ['Adam', 'Lisa', 'Bart'] 那我们如何从list中 ...
- 17款code review工具
本文是码农网原创翻译,转载请看清文末的转载要求,谢谢合作! 好的代码审查器可以大大地帮助程序员提高代码质量,减少错误几率. 虽然现在市场上有许多可用的代码审查工具,但如何挑选也是一个艰巨的任务.在咨询 ...
- Maven仓库详解
转载自:Maven入门指南④:仓库 1 . 仓库简介 没有 Maven 时,项目用到的 .jar 文件通常需要拷贝到 /lib 目录,项目多了,拷贝的文件副本就多了,占用磁盘空间,且难于管理.Ma ...
- css3360度旋转动画
@-webkit-keyframes Parallaxs{ from { -webkit-transform: rotate(180deg) ; -moz-transform: rotate(180d ...
- 浅谈 iOS 之 Crash log 符号化
其实,对于做移动 APP 开发的同学来说,质量和体验都是同等重要的.一个 APP 应用如果经常「闪退」,是产品质量很差的一个体现,那么用户体验就更不用再提了. *** 上面是笔者截取的国外一家公司对用 ...
- 对CURL的一些研究
http://www.kuqin.com/article/23candcplusplus/586014.html 前两天看到有人求客户端socket 发HTTP包的代码,受flw版主启发找了一些per ...
- Nginx完整配置说明
http://blog.csdn.net/marising/article/details/3979493 可以参考如下的完整例子 http://wiki.codemongers.com/NginxF ...
- c# 捕捉键盘按键
//esc退出窗体 protected override bool ProcessCmdKey(ref System.Windows.Forms.Message msg , System.Windo ...
- CC_UNUSED_PARAM 宏含义的解释
#define CC_UNUSED_PARAM(unusedparam) (void)unusedparam 这个宏完全没有执行任何命令,这样写的原因主要是历史遗留原因,ojb-c不存在纯虚函数并且传 ...
- [jobdu]包含min函数的栈
老题,两个stack.其中一个维护min值就行了. #include <iostream> #include <stack> using namespace std; int ...
