Poem Codes - 攻防世界(Decrypt-the-Message)
Poem Codes
Poem Code 最显著的特点就是一首诗歌。 详情请戳这里
让我们一起来过滤一遍这个神奇的加密过程~
① 给出一首诗歌
for my purpose holds to sail beyond the sunset, and the baths of all the western stars until I die.
② 给出5个关键单词。
“for”, “sail”, “all”, “stars”, “die.”
对其进行拆散:
f o r s a i l a l l s t a r s d i e
接下来按照 字母表顺序 进行编号,若遇相同字母,则继续 +1
| f | o | r | s | a | i | l | a |
|---|---|---|---|---|---|---|---|
| 6 | 12 | 13 | 15 | 1 | 7 | 9 | 2 |
| l | l | s | t | a | r | s | d |
| 10 | 11 | 16 | 18 | 3 | 14 | 17 | 4 |
| i | e | ||||||
| 8 | 5 |
③ 将要传递的消息进行加密。
We have run out of cigars, situation desperate。
先对对其进行编码。因为给出的5个关键词,其长度为18.所以以18为一组。
若一组长度不满18,则用abc(不要求有序)进行补充。

将排好的消息,按照之前给出的诗歌字母编号写下密文。
for my purpose holds to sail beyond the sunset, and the baths of all the western stars until I die.
如, for --> eud tdk oek 那么得到的又可以按照5个(适当个数)为一组进行重新分组,得到最后密文。
例题
接下来我们来看一题。 【攻防世界】题目链接 【Decrypt-the-Message】
审题解题
首先我们得到一首诗歌
The life that I have
Is all that I have
And the life that I have
Is yours.The love that I have
Of the life that I have
Is yours and yours and yours.A sleep I shall have
A rest I shall have
Yet death will be but a pause.For the peace of my years
In the long green grass
Will be yours and yours and yours.
以及 decrypted message (解密消息)
emzcf sebt yuwi ytrr ortl rbon aluo konf ihye cyog rowh prhj feom ihos perp twnb tpak heoc yaui usoa irtd tnlu ntke onds goym hmpq
解题脚本
已知原理,我们可以运用网上大佬的 解密工具 ,解密脚本如下:
import sys
import itertools
from os import listdir
from os.path import isfile, join
abc='abcdefghijklmnopqrstuvwxyz'
def loadlist(infile):
tlist = []
for line in open(infile,'r'):
for w in line.split(): tlist.append(w.lower())
return tlist
def encrypt(code, poem, msg):
# Load all words of the poem into a temporary list
twords = loadlist(poem)
# Select only those words specified in the code in a new list
pwords = ''
for c in code: pwords += twords[c].lower()
plen = len(pwords)
# We can only support encoding all alphabetical letters, a key length greater len(abc) is not reasonable here
if plen > len(abc): sys.exit(3)
# Assign an index for each letter in the key based on the alphabet
pcode = [None] * plen
count = 0
while(count<plen):
for al in abc:
for pc, pl in enumerate(pwords):
if al!=pl: continue
pcode[pc]=count
count+=1
# Load all words of the message into a string
mwords = ''
for line in open(msg, 'r'):
for w in line.split(): mwords+=w.lower()
mlen = len(mwords)
# Split message into chunks of size plen, append random (here alphabet) characters to fill the last chunk, if necessary
cpairs = []
curlen = plen
while(curlen<mlen):
cpairs.append(mwords[curlen-plen:curlen])
curlen+=plen
rword = mwords[curlen-plen:curlen]
rlen = len(rword)
if rlen < plen: rword += abc[:plen-rlen]
cpairs.append(rword)
# Encrypt the message according to the key
cip = ''
for i in code: cip+=abc[i]
cip+=' '
for i in pcode:
for pair in cpairs:
cip += pair[i]
cip+=' '
return cip
def decrypt(poem, cip):
# Load all words of the poem into a temporary list
twords = loadlist(poem)
# Load all cipher chunks of the ciphertext into a list
cwords = loadlist(cip)
# Get the code rom the first chunk and remove it from the ciphertext list
code = []
for i in cwords.pop(0):
code.append(abc.index(i))
# Select only those words specified in the code in a new multi-arrayed list
xwords = [[] for x in range(len(code))]
for xcount, c in enumerate(code):
tlen = c
while(c<len(twords)):
xwords[xcount].append(twords[c].lower())
c+=26
# Get all possible combinations
for comb in itertools.product(*xwords):
pwords = ''
for c in comb: pwords+=c
plen = len(pwords)
# Rearrange the chunks according to the key
pcode = [None] * plen
count = 0
while(count<plen):
for al in abc:
for pc, pl in enumerate(pwords):
if al!=pl: continue
pcode[count]=cwords[pc]
count+=1
# Decrypt the ciphertext
msg = ''
wlen = len(pcode[0])
for c in range(0, wlen):
for word in pcode:
msg+=word[c]
print msg
# first argument = poem
# second argument = ciphertxt or msg
if len(sys.argv) != 3: sys.exit(2)
#print encrypt([0, 5, 13, 16, 19], sys.argv[1], sys.argv[2])
decrypt(sys.argv[1], sys.argv[2])
【注意】 该脚本是python2哦!把诗歌命名为 poem 信息命名为 msg
python poemcode.py poem msg
或者直接下载整份github源文件:执行如下命令:
python poemcode.py examples/2/ctfpoem examples/2/ctfcip
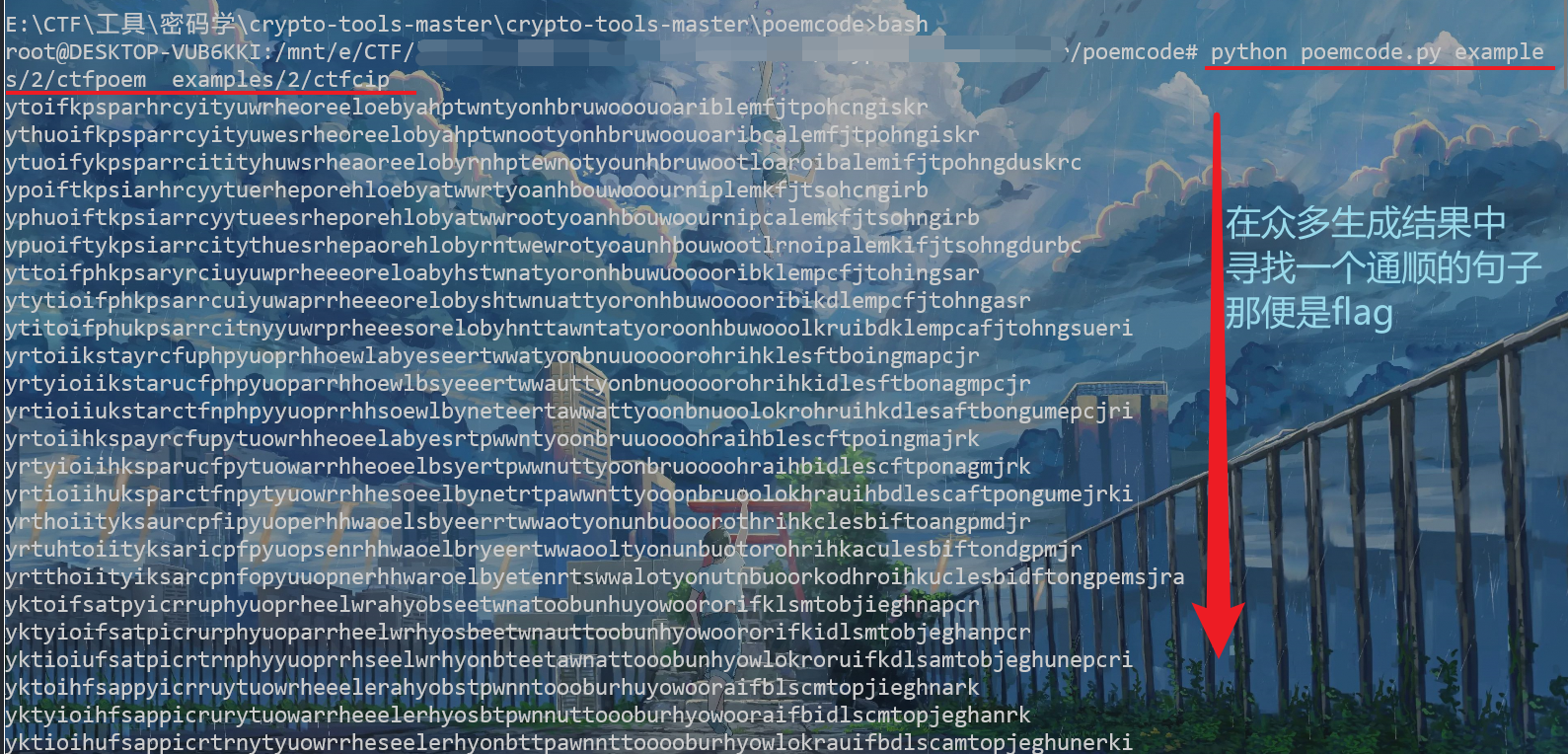
最终找到flag
ifyouthinkcryptographyistheanswertoyourproblemthenyoudonotknowwhatyourproblemisabcdefghijklmnopqrstu
【侵权删】【参考链接】:https://blog.csdn.net/dchua123/article/details/105470394/
【转载请放链接】:https://www.cnblogs.com/Jlay/p/Poem_Codes.html
Poem Codes - 攻防世界(Decrypt-the-Message)的更多相关文章
- 攻防世界-crypto-Decrypt-the-Message(Poem Codes-诗歌密码)
题目来源:su-ctf-quals-2014题目描述:解密这段信息! 下载附件,内容如下 The life that I have Is all that I have And the life th ...
- 异或加密 - cr2-many-time-secrets(攻防世界) - 异性相吸(buuctf)
Crib dragging attack 在开始了解 Crib dragging attack 之前,先来理一理 异或. 异或加密 [详情请戳这里] XOR 加密简介 异或加密特性: ① 两个值相同时 ...
- RSA(攻防世界)Rsa256 -- cr4-poor-rsa
RSA256 [攻防世界] 题目链接 [RSA256] 下载附件得到两个文件. 猜测第一个 txt 文件 可能为RSA加密密文 ,第二个估计就是密钥.依次打开看看: 果然如此. 目标: 寻找 n.e. ...
- CTF--web 攻防世界web题 robots backup
攻防世界web题 robots https://adworld.xctf.org.cn/task/answer?type=web&number=3&grade=0&id=506 ...
- CTF--web 攻防世界web题 get_post
攻防世界web题 get_post https://adworld.xctf.org.cn/task/answer?type=web&number=3&grade=0&id=5 ...
- 攻防世界 web进阶练习 NewsCenter
攻防世界 web进阶练习 NewsCenter 题目是NewsCenter,没有提示信息.打开题目,有一处搜索框,搜索新闻.考虑xss或sql注入,随便输入一个abc,没有任何搜索结果,页面也没有 ...
- 【攻防世界】高手进阶 pwn200 WP
题目链接 PWN200 题目和JarvisOJ level4很像 检查保护 利用checksec --file pwn200可以看到开启了NX防护 静态反编译结构 Main函数反编译结果如下 int ...
- XCTF攻防世界Web之WriteUp
XCTF攻防世界Web之WriteUp 0x00 准备 [内容] 在xctf官网注册账号,即可食用. [目录] 目录 0x01 view-source2 0x02 get post3 0x03 rob ...
- 攻防世界 | CAT
来自攻防世界官方WP | darkless师傅版本 题目描述 抓住那只猫 思路 打开页面,有个输入框输入域名,输入baidu.com进行测试 发现无任何回显,输入127.0.0.1进行测试. 发现已经 ...
随机推荐
- Python核心编程之生成器
生成器 1. 什么是生成器 大家知道通过列表生成式(不知道的可自行百度一下),我们可以直接创建一个列表,但是,受内存限制,列表内容肯定是有限的.比如我们要创建一个包含100万个元素的列表,这100万个 ...
- 使用PyPdf2合并PDF文件(没有空白、报错)
使用PyPdf2合并PDF文件(没有空白.报错) 对于合并之后pdf空白,或者出现 'latin-1' codec can't encode characters in position 8-11: ...
- Django折腾日记(django2.0)
新建项目 django-admin startproject mysite 运行 python manage.py runserver 创建一个应用 python manage.py startapp ...
- mybatis-plus自动填充
1,给字段添加注解 @TableField(value = "create_time", fill = FieldFill.INSERT) 2,添加填充处理器,需要实现接口Meta ...
- 关于GIT配置公私钥
问题:pull代码时显示 原因:公钥与私钥对不上,或者没有配置导致 解决: 1.生成私钥:TortoiseGIT → PuttyGen → Generate(点击后鼠标晃动会加速)→Save Priv ...
- 对于类似经销商的实体中Place(CBM_PALCE_ID = NULL)的情况,如何获取省市信息(限foton)
在库里像上述描述的数据很多,这种情况需要拿fence里的经纬度,反查省市 String[] strArr = data.getFence().getValue().split(";" ...
- Kubernetes 搭建 ES 集群(存储使用 local pv)
一.集群规划 由于当前环境中没有分布式存储,所以只能使用本地 PV 的方式来实现数据持久化. ES 集群的 master 节点至少需要三个,防止脑裂. 由于 master 在配置过程中需要保证主机名固 ...
- STM32入门系列-GPIO概念介绍
GPIO(general purpose intput output)是通用输入输出端口的简称,可以通过软件来控制其输入和输出.STM32 芯片的 GPIO 引脚与外部设备连接起来,从而实现与外部通讯 ...
- nginx反向代理三台web服务器,实现负载均衡
修改nginx.conf #在http和server之间加入这个模块 upstream guaji{ server 127.0.0.1:8080; server 127.0.0.2:8080; ser ...
- ERROR: No matching distribution found for cv2
ImportError: No module named cv2和No matching distribution found for cv2的问题 原因 这个是由于没有导入opencv库导致的 解决 ...
