Envoy:TLS双向认证
环境准备
| 主机 | 角色 | 数量 |
|---|---|---|
| front-envoy | front envoy | 1 |
| service envoy | 作为内部后端的envoy | 2 |
| end | 后端应用程序 | 2 |
访问 / front-envoy ==> end * 2
访问 /red/colorful ==> end red 不验证客户端证书 单项tls
访问 /gray/colorful ==> end gray 验证客户端证书 双项tls
docker-compose
version: '3'
services:
front-envoy:
image: envoyproxy/envoy-alpine:v1.15-latest
environment:
- ENVOY_UID=0
ports:
- 80:80
- 443:443
- 82:9901
volumes:
- ./envoy.yaml:/etc/envoy/envoy.yaml
- ./certs/front-envoy/:/etc/envoy/certs/
- ./certs/CA/:/etc/envoy/ca/
networks:
envoymesh:
aliases:
- front-envoy
depends_on:
- webserver1
- webserver2
gray-envoy:
image: envoyproxy/envoy-alpine:v1.15-latest
environment:
- ENVOY_UID=0
volumes:
- ./service_gray.yaml:/etc/envoy/envoy.yaml
- ./certs/service_gray/:/etc/envoy/certs/
- ./certs/CA1/:/etc/envoy/ca/
network_mode: "service:webserver1"
depends_on:
- webserver1
red-envoy:
image: envoyproxy/envoy-alpine:v1.15-latest
environment:
- ENVOY_UID=0
volumes:
- ./service_red.yaml:/etc/envoy/envoy.yaml
- ./certs/service_red/:/etc/envoy/certs/
- ./certs/CA1/:/etc/envoy/ca/
network_mode: "service:webserver2"
depends_on:
- webserver2
webserver1:
image: sealloong/envoy-end:latest
networks:
envoymesh:
aliases:
- service_gray
- front_envoy
environment:
- VERSION=v1
- COLORFUL=gray
expose:
- 90
webserver2:
image: sealloong/envoy-end:latest
networks:
envoymesh:
aliases:
- service_red
- front_envoy
environment:
- VERSION=v1
- COLORFUL=red
expose:
- 90
networks:
envoymesh: {}
front-envoy
admin:
access_log_path: "/dev/null"
address:
socket_address:
address: 0.0.0.0
port_value: 9901
static_resources:
secrets:
- name: servers
tls_certificate:
certificate_chain:
filename: "/etc/envoy/certs/server.crt"
private_key:
filename: "/etc/envoy/certs/server.key"
- name: clients
tls_certificate:
certificate_chain:
filename: "/etc/envoy/certs/client.crt"
private_key:
filename: "/etc/envoy/certs/client.key"
- name: validation
validation_context:
trusted_ca:
filename: "/etc/envoy/ca/ca.crt"
listeners:
- name: listener_http
address:
socket_address: { address: 0.0.0.0, port_value: 80 }
filter_chains:
- filters:
- name: envoy.http_connection_manager
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager
codec_type: auto
stat_prefix: ingress_http
route_config:
name: local_route
virtual_hosts:
- name: service
domains: [ "*" ]
routes:
- match: { prefix: "/" }
redirect:
https_redirect: true
port_redirect: 443
http_filters:
- name: envoy.router
- name: listener_https
address:
socket_address: { address: 0.0.0.0, port_value: 443 }
filter_chains:
- filters:
- name: envoy.http_connection_manager
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager
stat_prefix: ingress_https
codec_type: AUTO
route_config:
name: https_route
virtual_hosts:
- name: https_route
domains: ["*"]
routes:
- match: { prefix: "/gray/colorful" }
route:
prefix_rewrite: "/colorful"
cluster: gray
- match: { prefix: "/red/colorful" }
route:
prefix_rewrite: "/colorful"
cluster: red
- match: { prefix: "/" }
route:
cluster: front_envoy
http_filters:
- name: envoy.router
access_log:
- name: envoy.listener.accesslog
typed_config:
"@type": type.googleapis.com/envoy.extensions.access_loggers.file.v3.FileAccessLog
path: /dev/stdout
log_format:
text_format: "[%START_TIME%] \"%REQ(:METHOD)% %REQ(X-ENVOY-ORIGINAL-PATH?:PATH)% %PROTOCOL%\" %RESPONSE_CODE% %RESPONSE_FLAGS% %BYTES_RECEIVED% %BYTES_SENT% %DURATION% %RESP(X-ENVOY-UPSTREAM-SERVICE-TIME)% \"%REQ(X-FORWARDED-FOR)%\" \"%REQ(USER-AGENT)%\" \"%REQ(X-REQUEST-ID)%\" \"%REQ(:AUTHORITY)%\" \"%UPSTREAM_HOST%\"\n"
transport_socket:
name: envoy.transport_sockets.tls
typed_config:
"@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.DownstreamTlsContext
common_tls_context:
tls_certificate_sds_secret_configs:
- name: servers
clusters:
- name: front_envoy
connect_timeout: 0.25s
type: strict_dns
lb_policy: round_robin
load_assignment:
cluster_name: front_envoy
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address: { address: front_envoy, port_value: 90 }
- name: gray
connect_timeout: 0.25s
type: strict_dns
lb_policy: round_robin
load_assignment:
cluster_name: gray
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address: { address: service_gray, port_value: 443 }
transport_socket:
name: envoy.transport_sockets.tls
typed_config:
"@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.UpstreamTlsContext
common_tls_context:
tls_certificate_sds_secret_configs:
- name: clients
validation_context_sds_secret_config:
name: validation
- name: red
connect_timeout: 0.25s
type: strict_dns
lb_policy: round_robin
load_assignment:
cluster_name: red
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address: { address: service_red, port_value: 443 }
transport_socket:
name: envoy.transport_sockets.tls
typed_config:
"@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.UpstreamTlsContext
common_tls_context:
tls_certificate_sds_secret_configs:
- name: clients
service gray
admin:
access_log_path: "/dev/null"
address:
socket_address:
address: 0.0.0.0
port_value: 9901
static_resources:
listeners:
- name: listener_https
address:
socket_address: { address: 0.0.0.0, port_value: 443 }
filter_chains:
- filters:
- name: envoy.http_connection_manager
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager
stat_prefix: ingress_https
codec_type: AUTO
route_config:
name: https_route
virtual_hosts:
- name: https_route
domains: ["*"]
routes:
- match: { prefix: "/" }
route:
cluster: service_gray
http_filters:
- name: envoy.router
access_log:
- name: envoy.listener.accesslog
typed_config:
"@type": type.googleapis.com/envoy.extensions.access_loggers.file.v3.FileAccessLog
path: /dev/stdout
log_format:
text_format: "[%START_TIME%] \"%REQ(:METHOD)% %REQ(X-ENVOY-ORIGINAL-PATH?:PATH)% %PROTOCOL%\" %RESPONSE_CODE% %RESPONSE_FLAGS% %BYTES_RECEIVED% %BYTES_SENT% %DURATION% %RESP(X-ENVOY-UPSTREAM-SERVICE-TIME)% \"%REQ(X-FORWARDED-FOR)%\" \"%REQ(USER-AGENT)%\" \"%REQ(X-REQUEST-ID)%\" \"%REQ(:AUTHORITY)%\" \"%UPSTREAM_HOST%\"\n"
transport_socket:
name: envoy.transport_sockets.tls
typed_config:
"@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.DownstreamTlsContext
common_tls_context:
tls_certificates:
certificate_chain:
filename: "/etc/envoy/certs/server.crt"
private_key:
filename: "/etc/envoy/certs/server.key"
validation_context:
trusted_ca:
filename: "/etc/envoy/ca/ca.crt"
require_client_certificate: true
clusters:
- name: service_gray
connect_timeout: 0.25s
type: strict_dns
lb_policy: round_robin
load_assignment:
cluster_name: service_gray
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address: { address: 127.0.0.1, port_value: 90 }
service red
admin:
access_log_path: "/dev/null"
address:
socket_address:
address: 0.0.0.0
port_value: 9901
static_resources:
listeners:
- name: listener_https
address:
socket_address: { address: 0.0.0.0, port_value: 443 }
filter_chains:
- filters:
- name: envoy.http_connection_manager
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager
stat_prefix: ingress_https
codec_type: AUTO
route_config:
name: https_route
virtual_hosts:
- name: https_route
domains: ["*"]
routes:
- match: { prefix: "/" }
route:
cluster: service_red
http_filters:
- name: envoy.router
access_log:
- name: envoy.listener.accesslog
typed_config:
"@type": type.googleapis.com/envoy.extensions.access_loggers.file.v3.FileAccessLog
path: /dev/stdout
log_format:
text_format: "[%START_TIME%] \"%REQ(:METHOD)% %REQ(X-ENVOY-ORIGINAL-PATH?:PATH)% %PROTOCOL%\" %RESPONSE_CODE% %RESPONSE_FLAGS% %BYTES_RECEIVED% %BYTES_SENT% %DURATION% %RESP(X-ENVOY-UPSTREAM-SERVICE-TIME)% \"%REQ(X-FORWARDED-FOR)%\" \"%REQ(USER-AGENT)%\" \"%REQ(X-REQUEST-ID)%\" \"%REQ(:AUTHORITY)%\" \"%UPSTREAM_HOST%\"\n"
transport_socket:
name: envoy.transport_sockets.tls
typed_config:
"@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.DownstreamTlsContext
common_tls_context:
tls_certificates:
- certificate_chain:
filename: "/etc/envoy/certs/server.crt"
private_key:
filename: "/etc/envoy/certs/server.key"
clusters:
- name: service_red
connect_timeout: 0.25s
type: strict_dns
lb_policy: round_robin
load_assignment:
cluster_name: service_red
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address: { address: 127.0.0.1, port_value: 90 }
配置说明
docker-compose
network_mode: "service:webserver1" 指定网络类型,使envoy和后端程序运行在一个网络下
secrets:
- name: servers
tls_certificate:
certificate_chain:
filename: "/etc/envoy/certs/server.crt"
private_key:
filename: "/etc/envoy/certs/server.key"
- name: clients
tls_certificate:
certificate_chain:
filename: "/etc/envoy/certs/client.crt"
private_key:
filename: "/etc/envoy/certs/client.key"
- name: validation
validation_context:
trusted_ca:
filename: "/etc/envoy/ca/ca.crt"
server
transport_socket:
name: envoy.transport_sockets.tls
typed_config:
"@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.DownstreamTlsContext
common_tls_context:
tls_certificates:
certificate_chain:
filename: "/etc/envoy/certs/server.crt"
private_key:
filename: "/etc/envoy/certs/server.key"
validation_context: # 验证机制的相关配置
trusted_ca: # 信任的ca证书,未指定时不会验证对端证书
filename: "/etc/envoy/ca/ca.crt" # 这里指定的为根ca
require_client_certificate: true # boolval 设置为ture,Envoy将拒绝没有有效客户端证书的连接。
验证结果
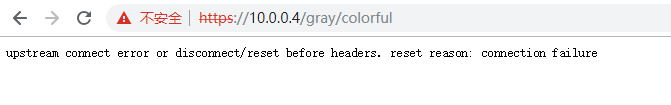
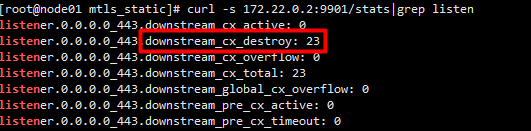
/gray/colorful后端服务开启了验证客户端ca,访问报错,后端程序并没收到请求,因证书无效,envoy销毁了请求
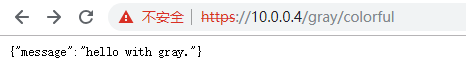
将根ca设置为可信任后
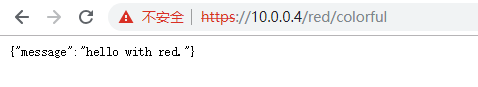
/red/colorful 没开启验证客户端证书
Envoy:TLS双向认证的更多相关文章
- linux运维、架构之路-Kubernetes集群部署TLS双向认证
一.kubernetes的认证授权 Kubernetes集群的所有操作基本上都是通过kube-apiserver这个组件进行的,它提供HTTP RESTful形式的API供集群内外客户端调 ...
- tls 双向认证 client端代码例子
example: python import httplib import json import ssl import urllib2 import requests CA_FILE = " ...
- 使用wireshark观察SSL/TLS握手过程--双向认证/单向认证
SSL/TLS握手过程可以分成两种类型: 1)SSL/TLS 双向认证,就是双方都会互相认证,也就是两者之间将会交换证书.2)SSL/TLS 单向认证,客户端会认证服务器端身份,而服务器端不会去对客户 ...
- SSL双向认证和SSL单向认证的流程和区别
refs: SSL双向认证和SSL单向认证的区别https://www.jianshu.com/p/fb5fe0165ef2 图解 https 单向认证和双向认证!https://cloud.tenc ...
- php实现https(tls/ssl)双向认证
php实现https(tls/ssl)双向认证 通常情况下,在部署https的时候,是基于ssl单向认证的,也就是说只要客户端认证服务器,而服务器不需要认证客户端. 但在一些安全性较高的场景,如银行, ...
- mosquitto ---SSL/TLS 单向认证+双向认证
生成证书 # * Redistributions in binary form must reproduce the above copyright # notice, this list of ...
- https 单向双向认证说明_数字证书, 数字签名, SSL(TLS) , SASL_转
转自:https 单向双向认证说明_数字证书, 数字签名, SSL(TLS) , SASL 因为项目中要用到TLS + SASL 来做安全认证层. 所以看了一些网上的资料, 这里做一个总结. 1. 首 ...
- 基于mosquitto的MQTT服务器---SSL/TLS 单向认证+双向认证
基于mosquitto的MQTT服务器---SSL/TLS 单向认证+双向认证 摘自:https://blog.csdn.net/ty1121466568/article/details/811184 ...
- tomcat配置SSL双向认证
一.SSL简单介绍 SSL(Secure Sockets Layer 安全套接层)就是一种协议(规范),用于保障客户端和服务器端通信的安全,以免通信时传输的信息被窃取或者修改. 怎样保障数据传输安全? ...
随机推荐
- Python3基础之构建setup.py
技术背景 在上一篇博客中,我们介绍了如何使用pyinstaller将python项目打包成一个可执行文件,并且放在系统目录下,让系统用户可以直接识别到我们构造的项目.而python项目中常见的setu ...
- QT项目-Chart Themes Example学习(一)
1.main.cpp #include "themewidget.h" #include <QtWidgets/QApplication> #include <Q ...
- Kafka又出问题了!
写在前面 估计运维年前没有祭拜服务器,Nginx的问题修复了,Kafka又不行了.今天,本来想再睡会,结果,电话又响了.还是运营,"喂,冰河,到公司了吗?赶紧看看服务器吧,又出问题了&quo ...
- PureStudy:学科知识分享——个人网站开发全解
PureStudy:学科知识分享--个人网站开发全解 项目描述 PureStudy,学科知识分享网站. 学生可以使用这个网站,来浏览相应学科的知识点.学习总结,获取相关的资料.此外,他们可以选择上传文 ...
- shell算数和逻辑运算
算术运算 Shell允许在某些情况下对算术表达式进行求值,比如:let和declare 内置命令,(( ))复合命令和算术扩 展.求值以固定宽度的整数进行,不检查溢出,尽管除以0 被困并标记为错误.运 ...
- 【秒懂音视频开发】14_AAC编码
AAC(Advanced Audio Coding,译为:高级音频编码),是由Fraunhofer IIS.杜比实验室.AT&T.Sony.Nokia等公司共同开发的有损音频编码和文件格式. ...
- Mybatis-plus 上
Mybatis-plus 上 简介 1.什么是Mybatis-plus MyBatis-Plus(简称 MP)是一个 MyBatis的增强工具,在 MyBatis 的基础上只做增强不做改变,为简化开发 ...
- kubernetes 降本增效标准指南| 资源利用率提升工具大全
背景 公有云的发展为业务的稳定性.可拓展性.便利性带来了极大帮助.这种用租代替买.并且提供完善的技术支持和保障的服务,理应为业务带来降本增效的效果.但实际上业务上云并不意味着成本一定较少,还需适配云上 ...
- SQL Server如何将查询的内容保存到新的sql 表中
我是采用语句将 查询后的数据保存到一个新表中 1)采用into table 语句,需要保存到的这个新表不需要提前创建 select *into NewTable from Table --插入新表的语 ...
- xman_2019_format(非栈上格式化字符串仅一次利用的爆破)
xman_2019_format(非栈上格式化字符串仅一次利用的爆破) 首先检查一下程序的保护机制 然后用IDA分析一下 存在后门 首先malloc了一片堆空间,读入数据 把刚刚读入的数据当作格式化字 ...
