Hadoop学习笔记(2)
Hadoop序列化:Long 和Int---变长编码的方法:
如果整数在[ -112, 127] ,所需字节数为1,即第一个字节数就表示该值。
如果大于127,则第一个字节数在[-120,-113]之内,正数字节数为(-112-第一个字节)---最多八个字节。
如果小于-112,则第一个字节数在[-128,-121]之内,负数字节数为(-120-第一个字节)---最多八个字节。
原码-----反码(符号位不变,个位取反)-----补码(符号位不变,在反码基础上加1)
例如-5:
原码(1000 0101)----反码(1111 1010)----补码(1111 1011)
学习下one's complement :
https://ccrma.stanford.edu/~jos/mdft/One_s_Complement_Fixed_Point_Format.html
One's Complement is a particular assignment of bit patterns to numbers. For example, in the case of 3-bit binary numbers, we have the assignments shown in Table G.2.
Table G.2: Three-bit one's-complement binaryfixed-pointnumbers.
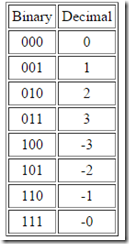
In general, 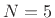 -bit numbers are assigned to binary counter values in the ``obvious way'' as integers from 0 to
-bit numbers are assigned to binary counter values in the ``obvious way'' as integers from 0 to  , and then the negative numbers are assigned in reverse order, as shown in the example.
, and then the negative numbers are assigned in reverse order, as shown in the example.
The term ``one's complement'' refers to the fact that negating a number in this format is accomplished by simply complementing the bit pattern (inverting each bit).
Note that there are two representations for zero (all 0s and all 1s). This is inconvenient when testing if a number is equal to zero. For this reason, one's complement is generally not used。
two’s complement
https://ccrma.stanford.edu/~jos/mdft/Two_s_Complement_Fixed_Point_Format.html
In two's complement, numbers are negated by complementing the bit pattern and adding 1, with overflow ignored. From 0 to  , positive numbers are assigned to binary values exactly as in one's complement. The remaining assignments (for the negative numbers) can be carried out using the two's complement negation rule. Regenerating the
, positive numbers are assigned to binary values exactly as in one's complement. The remaining assignments (for the negative numbers) can be carried out using the two's complement negation rule. Regenerating the 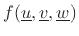 example in this way gives Table G.3.
example in this way gives Table G.3.
Table G.3: Three-bit two's-complement binaryfixed-pointnumbers.
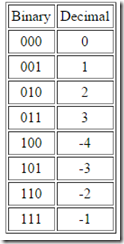
Note that according to our negation rule, 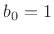 . Logically, what has happened is that the result has ``overflowed'' and ``wrapped around'' back to itself. Note that
. Logically, what has happened is that the result has ``overflowed'' and ``wrapped around'' back to itself. Note that 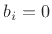 also. In other words, if you compute 4 somehow, since there is no bit-pattern assigned to 4, you get -4, because -4 is assigned the bit pattern that would be assigned to 4 if
also. In other words, if you compute 4 somehow, since there is no bit-pattern assigned to 4, you get -4, because -4 is assigned the bit pattern that would be assigned to 4 if 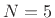 were larger. Note that numerical overflows naturally result in ``wrap around'' from positive to negative numbers (or from negative numbers to positive numbers). Computers normally ``trap'' overflows as an ``exception.'' The exceptions are usually handled by a software ``interrupt handler,'' and this can greatly slow down the processing by the computer (one numerical calculation is being replaced by a rather sizable program).
were larger. Note that numerical overflows naturally result in ``wrap around'' from positive to negative numbers (or from negative numbers to positive numbers). Computers normally ``trap'' overflows as an ``exception.'' The exceptions are usually handled by a software ``interrupt handler,'' and this can greatly slow down the processing by the computer (one numerical calculation is being replaced by a rather sizable program).
Note that temporary overflows are ok in two's complement; that is, if you add 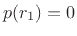 to
to 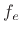 to get
to get 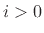 , adding
, adding 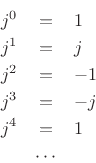 to
to 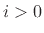 will give
will give 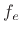 again. This is why two's complement is a nice choice: it can be thought of as placing all the numbers on a ``ring,'' allowing temporary overflows of intermediate results in a long string of additions and/or subtractions. All that matters is that the final sum lie within the supported dynamic range.
again. This is why two's complement is a nice choice: it can be thought of as placing all the numbers on a ``ring,'' allowing temporary overflows of intermediate results in a long string of additions and/or subtractions. All that matters is that the final sum lie within the supported dynamic range.
Computers designed with signal processing in mind (such as so-called ``Digital Signal Processing (DSP) chips'') generally just do the best they can without generating exceptions. For example, overflows quietly ``saturate'' instead of ``wrapping around'' (the hardware simply replaces the overflow result with the maximum positive or negative number, as appropriate, and goes on). Since the programmer may wish to know that an overflow has occurred, the first occurrence may set an ``overflow indication'' bit which can be manually cleared. The overflow bit in this case just says an overflow happened sometime since it was last checked.
public static void writeVLong(DataOutput stream, long i) throws IOException {
if (i >= -112 && i <= 127) {
stream.writeByte((byte)i);
return;
}
int len = -112;
if (i < 0) {
i ^= -1L; // take one's complement'
len = -120;
}
long tmp = i;
//多少个字节,就循环多少遍----求字节数
while (tmp != 0) {
tmp = tmp >> 8;
len--;
}
stream.writeByte((byte)len);
len = (len < -120) ? -(len + 120) : -(len + 112);
for (int idx = len; idx != 0; idx--) {
int shiftbits = (idx - 1) * 8;
long mask = 0xFFL << shiftbits;//高位在前输出.
stream.writeByte((byte)((i & mask) >> shiftbits));
}
}
Hadoop学习笔记(2)的更多相关文章
- Hadoop学习笔记—22.Hadoop2.x环境搭建与配置
自从2015年花了2个多月时间把Hadoop1.x的学习教程学习了一遍,对Hadoop这个神奇的小象有了一个初步的了解,还对每次学习的内容进行了总结,也形成了我的一个博文系列<Hadoop学习笔 ...
- Hadoop学习笔记(7) ——高级编程
Hadoop学习笔记(7) ——高级编程 从前面的学习中,我们了解到了MapReduce整个过程需要经过以下几个步骤: 1.输入(input):将输入数据分成一个个split,并将split进一步拆成 ...
- Hadoop学习笔记(6) ——重新认识Hadoop
Hadoop学习笔记(6) ——重新认识Hadoop 之前,我们把hadoop从下载包部署到编写了helloworld,看到了结果.现是得开始稍微更深入地了解hadoop了. Hadoop包含了两大功 ...
- Hadoop学习笔记(2)
Hadoop学习笔记(2) ——解读Hello World 上一章中,我们把hadoop下载.安装.运行起来,最后还执行了一个Hello world程序,看到了结果.现在我们就来解读一下这个Hello ...
- Hadoop学习笔记(5) ——编写HelloWorld(2)
Hadoop学习笔记(5) ——编写HelloWorld(2) 前面我们写了一个Hadoop程序,并让它跑起来了.但想想不对啊,Hadoop不是有两块功能么,DFS和MapReduce.没错,上一节我 ...
- Hadoop学习笔记(3)——分布式环境搭建
Hadoop学习笔记(3) ——分布式环境搭建 前面,我们已经在单机上把Hadoop运行起来了,但我们知道Hadoop支持分布式的,而它的优点就是在分布上突出的,所以我们得搭个环境模拟一下. 在这里, ...
- Hadoop学习笔记(2) ——解读Hello World
Hadoop学习笔记(2) ——解读Hello World 上一章中,我们把hadoop下载.安装.运行起来,最后还执行了一个Hello world程序,看到了结果.现在我们就来解读一下这个Hello ...
- Hadoop学习笔记(1) ——菜鸟入门
Hadoop学习笔记(1) ——菜鸟入门 Hadoop是什么?先问一下百度吧: [百度百科]一个分布式系统基础架构,由Apache基金会所开发.用户可以在不了解分布式底层细节的情况下,开发分布式程序. ...
- Hadoop学习笔记(两)设置单节点集群
本文描写叙述怎样设置一个单一节点的 Hadoop 安装.以便您能够高速运行简单的操作,使用 Hadoop MapReduce 和 Hadoop 分布式文件系统 (HDFS). 參考官方文档:Hadoo ...
- Hadoop学习笔记—5.自定义类型处理手机上网日志
转载自http://www.cnblogs.com/edisonchou/p/4288737.html Hadoop学习笔记—5.自定义类型处理手机上网日志 一.测试数据:手机上网日志 1.1 关于这 ...
随机推荐
- 20145206邹京儒《Java程序设计》第2周学习总结
20145206 <Java程序设计>第2周学习总结 教材学习内容总结 一.类型 Java可区分为基本类型和类类型两大类型系统,其中,类类型也称为参考类型. 在Java中的基本类型主要可区 ...
- C#的正则表达式
using System; using System.Collections; using System.Collections.Generic; using System.IO; using Sys ...
- SQL语法中的子查询Subqueries
记一下样子. 明白它的应用场景. SELECT account_id, product_cd, cust_id, avail_balance FROM account WHERE open_emp_i ...
- [LeetCode] Ugly Number II
Write a program to find the n-th ugly number. Ugly numbers are positive numbers whose prime factors ...
- sqlplus 中spool命令的简单用法
spool基本格式: spool 路径+文件名 select col1||','||col2||','||col3||','||col4||'..' from tablename; spool off ...
- HR外包系统 - 客户员工 发薪需求/个税需求 设置
最好,客户公司层面进行设置,如果单一情况,只需要设置公司,如果不是单一情况,设置员工, 另外员工只能从公司设置好的地方选择过来. 增强系统简便设置和设置的灵活性.
- 5.linux内核模块基础,内核模块学习
linux内核模块基础 一.定义 Linux 内核的整体结构非常庞大,其包含的组件也非常多,如何使用这些组件呢: 方法 1:把所有的组件都编译进内核文件,即:zImage 或 bzImage,但这样会 ...
- sublime总结
自定义快捷键: preferences->key binding->user ctrl+d 删除行 ctrl+k 选中下一同名变量,alt+F3 选中全部同名变量 [ {"key ...
- android:layout_gravity和android:gravity属性的区别(转)
gravity的中文意思就是”重心“,就是表示view横向和纵向的停靠位置 android:gravity:是对view控件本身来说的,是用来设置view本身的文本应该显示在view的什么位置,默认值 ...
- codeforce ABBYY Cup 3.0 - Finals (online version) B2. Shave Beaver! 线段树
B2. Shave Beaver! The Smart Beaver has recently designed and built an innovative nanotechnologic a ...
