emSecure Use Digital Signatures to protect your products
emSecure Use Digital Signatures to protect your products
emSecure is an RSA based software solution to authenticate digital assets. It can be used to secure products at no per unit cost against hacking and cloning.
Features
- RSA - Dual keys, private and public make it 100% safe
- Hardware-independent, any CPU, no additional hardware needed
- High performance, small memory footprint
- Simple API, easy to integrate
- Applicable for new and existing products
- Complete package, key generator and tools included
- Drag-and-drop Sign And Verify application included
- Full source code
What is emSecure?
emSecure is a SEGGER software package that allows creation and verification of digital signatures.
One important feature is that emSecure can make it impossible to create a clone of an embedded device by simply copying hardware and firmware.
And it can do much more, such as securing firmware updates distributed to embedded devices and authenticating licenses, serial numbers, and sensitive data.
emSecure offers 100% protection against hacking. It is not just nice to have, but in fact a must-have, not only for critical devices such as election machines, financial applications, or sensors.
Compromised devices are dangerous in several ways, not just from a commercial point of view. They hamper manufacturers' reputation and might entail severe legal disputes. Not addressing the issue of hacking and cloning is irresponsible.
Based on asymmetric encryption algorithms with two keys, emSecure signatures cannot be forged by reverse engineering of the firmware. A secure, private key is used to generate the digital signature, whereas a second, public key is used to authenticate data by its signature. There is neither a way to get the private key from the public key, nor is it possible to generate a valid signature without the private key.
The emSecure source code has been created from scratch for embedded systems, to achieve highest portability with a small memory footprint and high performance. However, usage is not restricted to embedded systems.
With its easy usage, it takes less than one day to add and integrate emSecure into an existing product.
emSecure is a very complete package, including ready-to-run tools and functionality for generation of keys and signatures.
Why should I use emSecure?
Security consideration
If you want to check the integrity of your data, for instance the firmware running on your product, you would normally include a checksum or hash value into it, generated by a CRC or SHA function. Hashes are excellent at ensuring a critical data transmission, such as a firmware download, has worked flawlessly and to verify that an image, stored in memory, has not changed. However they do not add much security, as an attacker can easily compute the hash value of modified data or images.
Digital signatures can do more. In addition to the integrity check, which is provided by hash functions, a digital signature assures the authenticity of the provider of the signed data, as only he can create a valid signature.
emSecure creates digital signatures using the RSA cryptosystem that has proven robust against decades of attacks on the algorithms. For the default of 2048-bit key sizes, it is considered well beyond the capability of governments, with all their computing power and using the very latest number-theoretic methods, to recover a properly generated RSA private key before 2030, and most probably well beyond that.
emSecure can be used for two security approaches:
1. Anti-hacking: Prevent tampering or exchange of data, for example the firmware running on a product, with non-authorized data.
2. Anti-cloning: Prevent a firmware to be run on a cloned hardware device.
Anti-Hacking — Authentication of firmware
To make sure only authorized firmware images are run on a product the firmware image will be signed with emSecure.
To do this an emSecure key pair is generated one time.
The private key will be included in the production process of the firmware. Once a firmware is created and ready to be shipped or included into a product it will be signed with this private key. The signature will be transferred and stored in the product alongside the firmware.
Firmware signing in production:
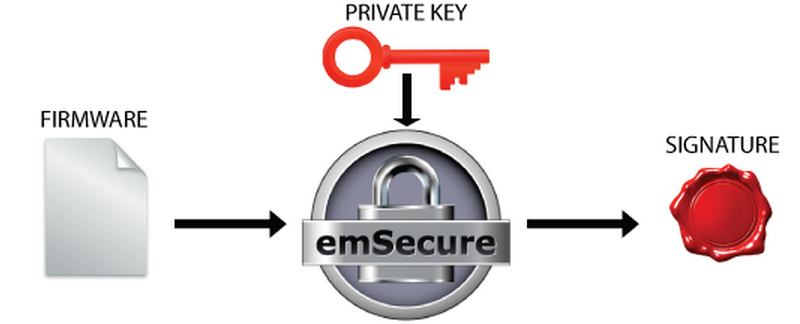
The public key will be included in the bootloader of the product, which manages firmware updates and starts the firmware.
On a firmware update and when starting the product, the bootloader will verify the firmware by its signature. If they match, the firmware is started, otherwise the application will stay in the bootloader or even erase the firmware.
Anti-Hacking Bootloader Verification:
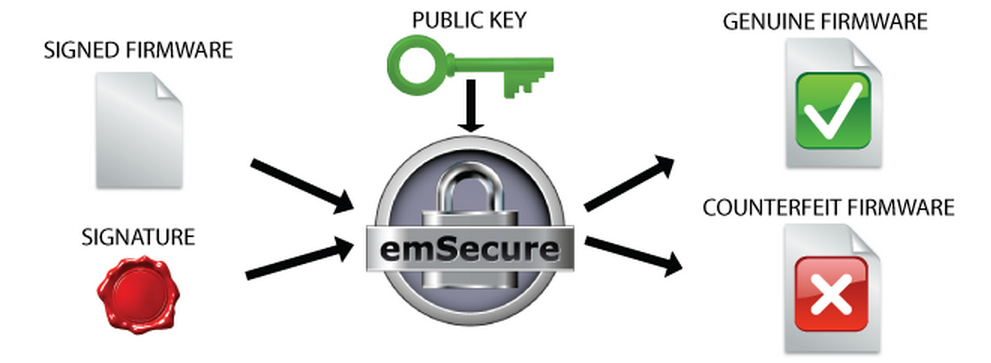
Anti-Cloning — Authentication of hardware
To make sure a product cannot be re-produced by non-authorized manufacturers, by simply copying the hardware, emSecure will be used to sign each genuine product unit.
First an emSecure key pair is generated one time. This is likely done at the production site.
Hardware signing in production:
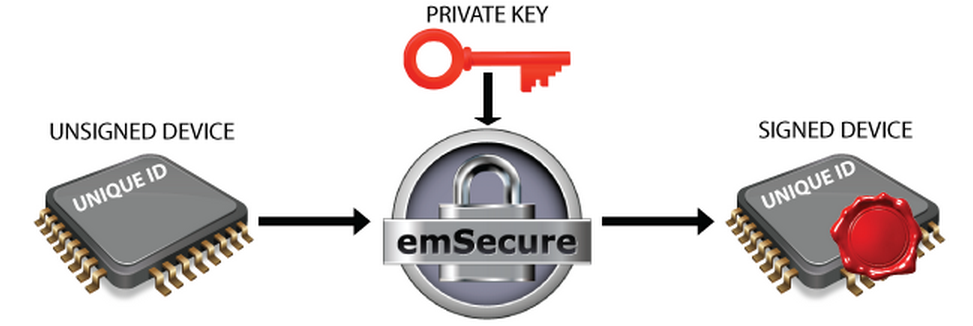
The private key will be included in the production process of the product. At the end of the production process, after the unit is assembled and tested, some hardware-specific, fixed, and unique data, like the unique id of the microcontroller is read from the unit. This data is signed by emSecure with the private key and the signature is written back to the unit into an OTP area or a specified location on memory.
The public key will be included in the firmware which will run on the product. When the firmware is running it will read the unique data from the unit and verify it with the signature. When the signature does not match, for example, when it was simply copied to a counterfeit unit with other unique data, the firmware will refuse to run.
Anti-Cloning Firmware Verification:
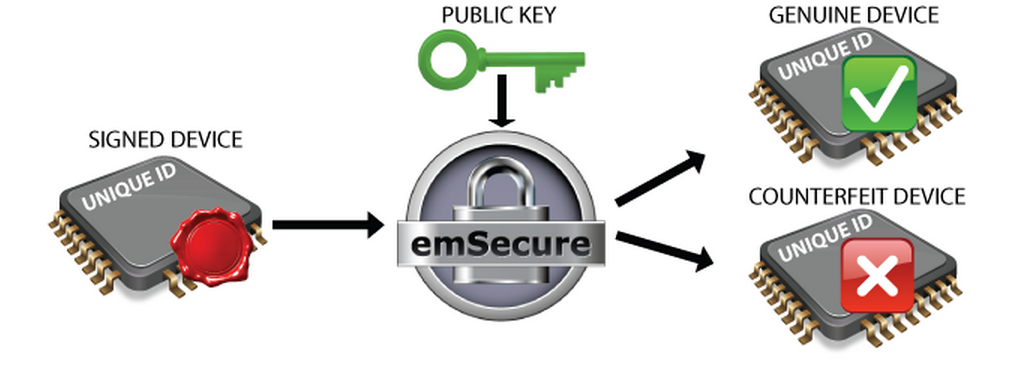
Technical Background
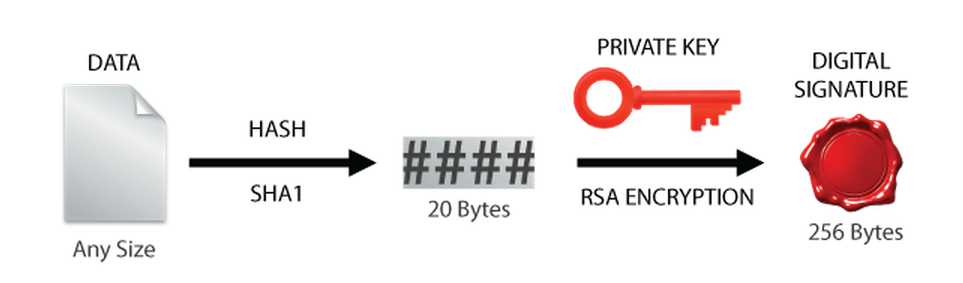
The emSecure signing operation starts by using a secure hash algorithm (SHA1) to generate a hash from the original data. Using the 2kBit RSA private key along with the hash, a digital signature is generated using RSA encryption.
emSecure Signing Technical Details:
The emSecure verification process starts with the data one wishes to verify and the digital signature which was created from the original file. A hash file is generated for the unverified data. The public key and RSA decryption is used to generate the original hash and then compared to verify whether the data file is genuine.
emSecure Verification Technical Details:

FAQs
| Q: | I want to inhibit copying a whole firmware from one product hardware to another cloned one. How can I prevent it to be run from the cloned version with emSecure? |
| A: | Nearly every modern MCU includes a unique ID, which is different on every device. When the signature covers this UID it is only valid on one single device and cannot be run on a cloned or copied product. The firmware can verify the signature at boot-time. |
| Q: |
I added a digital signature to my product. Where should I verify it? |
| A: | Signature verification can be done in-product or off-product. With in-product verification the firmware for example verifies the digital signature at boot-time and refuses to run when the signature cannot be verified. With off-product verification an external application, e.g. a PC application communicating with the device, reads the signature and data from the product and verifies it. |
| Q: | I want my product to only run genuine firmware images. How can I achieve this with emSecure? |
| A: | To make sure a firmware image is genuine, the complete image can be signed with a digital signature. Like when using a CRC for integrity checks, the signature is sent with the firmware data upon a firmware update. The application or bootloader programming the firmware onto the device validates the firmware data with its signature. The signature can only be generated with the private key and should be provided by the developer with the firmware data. |
| Q: | I am providing additional licenses for my product which shall be locked to a specific user or computer. Can I generate license keys with emSecure? |
| A: | Yes. emSecure can generate unique license keys for any data, like a computer ID, a user name, e-mail address or any other data. |
| Q: | My product is sending data to a computer application. Can I make sure the computer application is getting data only from my product with emSecure? |
| A: | Yes. In this case the product is used to sign the data and the computer applications verifies it. To prevent the private key from being read from the product it might be stored encrypted on the product or in the application and decrypted prior to signing the data. |
| Q: | Does emSecure support DSA or ECDSA? |
| A: | No, but both DSA and ECDSA signing and verification code is available from SEGGER. Please get in touch with us if you feel DSA or ECDSA signature verification is what you need. |
emSecure Use Digital Signatures to protect your products的更多相关文章
- Android Application Digital Signatures - Android 数字签名
Android 数字签名 同一个开发人员的多个程序尽可能使用同一个数字证书,这能够带来下面优点. (1)有利于程序升级,当新版程序和旧版程序的数字证书同样时,Android系统才会觉得这两个程序是同一 ...
- What is a Digital Signature? 理解数字签名与数字证书
What is a Digital Signature?An introduction to Digital Signatures, by David Youd Bob (Bob's public k ...
- Vacuum Pump Manufacturer - Vacuum Pump: Prevents Reactive Compound Decomposition Products
Vacuum packaging has been popular in the industry for a long time. Many large companies have joined ...
- Core Java Volume I — 1.2. The Java "White Paper" Buzzwords
1.2. The Java "White Paper" BuzzwordsThe authors of Java have written an influential White ...
- Cryptographic method and system
The present invention relates to the field of security of electronic data and/or communications. In ...
- Method and system for public-key-based secure authentication to distributed legacy applications
A method, a system, an apparatus, and a computer program product are presented for an authentication ...
- BlackArch-Tools
BlackArch-Tools 简介 安装在ArchLinux之上添加存储库从blackarch存储库安装工具替代安装方法BlackArch Linux Complete Tools List 简介 ...
- 著名ERP厂商的SSO单点登录解决方案介绍一
SSO英文全称Single Sign On,单点登录.SSO是在多个应用系统中,用户只需要登录一次就可以访问所有相互信任的应用系统.它包括可以将这次主要的登录映射到其他应用中用于同一个用户 ...
- 比特币_Bitcoin 简介
2008-11 Satoshi Nakamoto Bitcoin: A Peer-to-Peer Electronic Cash System http://p2pbucks.com/?p=99 ...
随机推荐
- Node.js Error: listen EADDRNOTAVAIL
1 前言 nodejs部署在云服务器,外网用域名加端口访问不进来,但在服务器本地用127.0.0.1加端口可以访问,并且端口已经放开,然后只能排查配置.此文章仅作为记录使用. 如果端口和另一个的端口一 ...
- js获取iframe中的元素
var obj=document.getElementById("iframe的name").contentWindow; var ifmObj=obj.document.getE ...
- PHP替换指定字符串
在PHP中,有两个函数可以实现字符串替换,strtr()和str_repalce()函数. 首先我们简单了解下strtr()函数的定义及语法. strtr:转换指定字符. 两个语法: 第一种语法: s ...
- python 全栈开发,Day34(基于UDP协议的socket)
昨日内容回顾 网络的基础概念arp协议 :通过ip地址找到mac地址五层模型 : 应用层 传输层 网络层 数据链路层 物理层tcp协议 : 可靠的 面向连接 全双工 三次握手 四次挥手udp协议 : ...
- DB操作-用批处理执行Sql语句
用批处理在命令行状态下调用查询分析器来执行这个sql文件里的语句.下面就是sqlserver帮助里对于查询分析器(isqlw)命令行参数的解释:isqlw 实用工具(SQL 查询分析器)使您得以输入 ...
- Codeforces 707E Garlands
Garlands 我怎么感觉好水啊. 因为询问只有2000组, 离线询问, 枚举联通块再枚举询问, 二维树状数组更新答案. #include<bits/stdc++.h> #define ...
- Codeforces 585D Lizard Era: Beginning
Lizard Era: Beginning 折半之后搜就完事了, 直接存string字符串卡空间, 随便卡卡空间吧. #include<bits/stdc++.h> #define LL ...
- Python yaml处理
安装方式: pip install pyyaml 一.module.yaml为 name: Tom Smith age: 37 spouse: name: Jane Smith age: 25 chi ...
- 080 HBase的属性
一:基本属性 1.查看属性 2.解释属性 NAME:列簇名 BLOOMFILTER:布隆过滤器,用于对storefile的过滤 共有三种类型: ROW:行健过滤 ROWCOL:行列过滤 NONE:无 ...
- 060 关于Hive的调优(本身,sql,mapreduce)
1.关于hive的优化 ->大表拆分小表 ->过滤字段 ->按字段分类存放 ->外部表与分区表 ->外部表:删除时只删除元数据信息,不删除数据文件 多人使用多个外部表操作 ...
