codeforces 701 B. Cells Not Under Attack
2 seconds
256 megabytes
standard input
standard output
Vasya has the square chessboard of size n × n and m rooks. Initially the chessboard is empty. Vasya will consequently put the rooks on the board one after another.
The cell of the field is under rook's attack, if there is at least one rook located in the same row or in the same column with this cell. If there is a rook located in the cell, this cell is also under attack.
You are given the positions of the board where Vasya will put rooks. For each rook you have to determine the number of cells which are not under attack after Vasya puts it on the board.
The first line of the input contains two integers n and m (1 ≤ n ≤ 100 000, 1 ≤ m ≤ min(100 000, n2)) — the size of the board and the number of rooks.
Each of the next m lines contains integers xi and yi (1 ≤ xi, yi ≤ n) — the number of the row and the number of the column where Vasya will put the i-th rook. Vasya puts rooks on the board in the order they appear in the input. It is guaranteed that any cell will contain no more than one rook.
Print m integer, the i-th of them should be equal to the number of cells that are not under attack after first i rooks are put.
3 3
1 1
3 1
2 2
4 2 0
5 2
1 5
5 1
16 9
100000 1
300 400
9999800001
分析:这道题刚开始没做出来,看了题解。这道题说让你放棋子,当把这个棋子放下后当前行和当前列都会受到这个棋子的攻击,问你,当放下一个棋子后没有受到攻击的格子还有多少。其实只要统计那些行那些列被棋子占据了即可。用两个set分别保存当前状态下那些行那些列被占据,然后用总棋子数(n*n) 减去被占的行数即:r.size() * n,和被占的列数即: (n - 已受到影的行) ( n - r.size()) * l.size(); 就完成了。
/*************************************************************************
> File Name: cfC.cpp
> Author:
> Mail:
> Created Time: 2016年08月08日 星期一 13时42分35秒
************************************************************************/ #include<iostream>
#include<bits/stdc++.h>
using namespace std;
typedef long long ll;
set<ll> r,l; int main()
{
ios::sync_with_stdio(false);
cin.tie();
ll n,m;
cin >> n >> m;
ll x,y;
ll ans;
ll flag = ;
while(m--)
{
cin >> x >> y;
r.insert(x);
l.insert(y);
ans = n * n - r.size() * n - (n - r.size()) * l.size();
if(flag)
cout << ' ';
cout << ans;
flag++;
}
cout << endl;
return ;
}
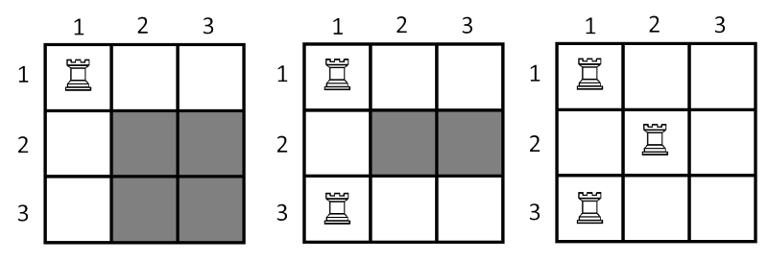
On the picture below show the state of the board after put each of the three rooks. The cells which painted with grey color is not under the attack.
codeforces 701 B. Cells Not Under Attack的更多相关文章
- codeforces 701B B. Cells Not Under Attack(水题)
题目链接: B. Cells Not Under Attack 题意: n*n的棋盘,现在放m个棋子,放一个棋子这一行和这一列就不会under attack了,每次放棋子回答有多少点还可能under ...
- Codeforces Round #364 (Div. 2) B. Cells Not Under Attack
B. Cells Not Under Attack time limit per test 2 seconds memory limit per test 256 megabytes input st ...
- Codeforces Round #364 (Div. 2) Cells Not Under Attack
Cells Not Under Attack 题意: 给出n*n的地图,有给你m个坐标,是棋子,一个棋子可以把一行一列都攻击到,在根据下面的图,就可以看出让你求阴影(即没有被攻击)的方块个数 题解: ...
- codeforces #364b Cells Not Under Attack
比赛的时候 long long sum=n*n,计算不出1e10长度到数,没有搞掉. 哎,以后要注意这个地方.这个题其实不难: 统计能被攻击到的个数,然后用总的个数减掉就可以了.注意有些地方重复计算, ...
- CF 701B Cells Not Under Attack(想法题)
题目链接: 传送门 Cells Not Under Attack time limit per test:2 second memory limit per test:256 megabyte ...
- Cells Not Under Attack
Cells Not Under Attack Vasya has the square chessboard of size n × n and m rooks. Initially the ches ...
- CodeForces 701B Cells Not Under Attack
题目链接:http://codeforces.com/problemset/problem/701/B 题目大意: 输入一个数n,m, 生成n*n的矩阵,用户输入m个点的位置,该点会影响该行和该列,每 ...
- Codeforces Round #115 A. Robot Bicorn Attack 暴力
A. Robot Bicorn Attack Time Limit: 20 Sec Memory Limit: 256 MB 题目连接 http://codeforces.com/contest/17 ...
- cf701B Cells Not Under Attack
Vasya has the square chessboard of size n × n and m rooks. Initially the chessboard is empty. Vasya ...
随机推荐
- 紫书 例题 11-5 UVa 10048 (Floyd求最大权值最小的路径)
这道题是Floyd的变形 改成d[i][j] = min(d[i][j], max(d[i][k], d[k][j]))就好了. #include<cstdio> #include< ...
- Spring学习总结(14)——Spring10种常见异常解决方法
在程序员生涯当中,提到最多的应该就是SSH三大框架了.作为第一大框架的Spring框架,我们经常使用. 然而在使用过程中,遇到过很多的常见异常,我在这里总结一下,大家共勉. 一.找不到配置文件的异常 ...
- R语言学习(一)前言
本系列文章由 @YhL_Leo 出品,转载请注明出处. 文章链接: http://blog.csdn.net/yhl_leo/article/details/49768161 R是一个有着统计分析功能 ...
- spring 、Mybatis配置sql server数据库
学习了:http://www.cnblogs.com/amwicfai/p/3181003.html beans.xml中的配置写法: <!-- 数据源 --> <bean id=& ...
- 1、初始JAVA
一. 语言的翻译分两种: 编译型语言:例如c语言.c++语言 优点:速度快 缺点:不能跨平台 编译器编译——>特定平台的目标文件obj——>特定平台 ...
- Zepto源代码分析之二~三个API
因为时间关系:本次仅仅对这三个API($.camelCase.$.contains.$.each)方法进行分析 第一个方法变量转驼峰:$.camelCase('hello-world-welcome' ...
- zzulioj--1807--小明在努力(递归)
1807: 小明在努力 Time Limit: 1 Sec Memory Limit: 128 MB Submit: 95 Solved: 35 SubmitStatusWeb Board Des ...
- springboot Ehcache缓存配置
例牌的导包 <!-- 包含支持UI模版(Velocity,FreeMarker,JasperReports), 邮件服务, 脚本服务(JRuby), 缓存Cache(EHCache), 任务计划 ...
- Java基础学习(六)-- 递归以及文件I/O流基础详解
递归 1.递归的概念: 在函数自身内部,调用函数本身的方式,称为递归. 2.递归的注意事项:包括递进去,归出来两步. 即:首先依次执行[函数调自身语句]上半部分的代码,知道最里层.(递进去),然后 ...
- Android 两步搞定Fragment的返回键
Fragment可以说是在Android开发必需要使用到技术,项目中的界面基本上都是使用Fragment来实现,而Activity只是作为Fragment的载体,但有些特殊情况下Fragment也不得 ...
