Cells Not Under Attack
Vasya has the square chessboard of size n × n and m rooks. Initially the chessboard is empty. Vasya will consequently put the rooks on the board one after another.
The cell of the field is under rook's attack, if there is at least one rook located in the same row or in the same column with this cell. If there is a rook located in the cell, this cell is also under attack.
You are given the positions of the board where Vasya will put rooks. For each rook you have to determine the number of cells which arenot under attack after Vasya puts it on the board.
The first line of the input contains two integers n and m (1 ≤ n ≤ 100 000, 1 ≤ m ≤ min(100 000, n2)) — the size of the board and the number of rooks.
Each of the next m lines contains integers xi and yi (1 ≤ xi, yi ≤ n) — the number of the row and the number of the column where Vasya will put the i-th rook. Vasya puts rooks on the board in the order they appear in the input. It is guaranteed that any cell will contain no more than one rook.
Print m integer, the i-th of them should be equal to the number of cells that are not under attack after first i rooks are put.
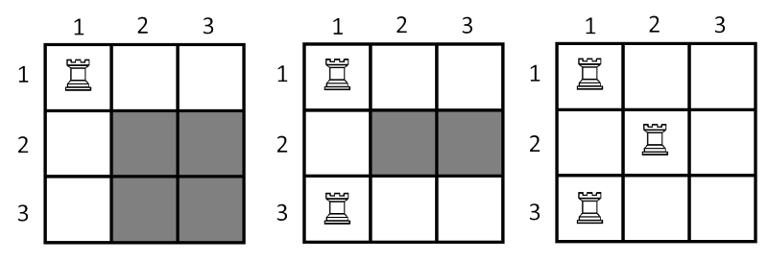
3 3
1 1
3 1
2 2
4 2 0
5 2
1 5
5 1
16 9
100000 1
300 400
9999800001
On the picture below show the state of the board after put each of the three rooks. The cells which painted with grey color is not under the attack.
分析:模拟即可;
代码:
#include <iostream>
#include <cstdio>
#include <cstdlib>
#include <cmath>
#include <algorithm>
#include <climits>
#include <cstring>
#include <string>
#include <set>
#include <map>
#include <queue>
#include <stack>
#include <vector>
#include <list>
#include <ext/rope>
#define rep(i,m,n) for(i=m;i<=n;i++)
#define rsp(it,s) for(set<int>::iterator it=s.begin();it!=s.end();it++)
#define vi vector<int>
#define pii pair<int,int>
#define mod 1000000007
#define inf 0x3f3f3f3f
#define pb push_back
#define mp make_pair
#define fi first
#define se second
#define ll long long
#define pi acos(-1.0)
const int maxn=1e5+;
const int dis[][]={{,},{-,},{,-},{,}};
using namespace std;
using namespace __gnu_cxx;
ll gcd(ll p,ll q){return q==?p:gcd(q,p%q);}
ll qpow(ll p,ll q){ll f=;while(q){if(q&)f=f*p;p=p*p;q>>=;}return f;}
int n,m,x,y,cnt1,cnt2;
bool a[maxn],b[maxn];
int main()
{
int i,j,k,t;
scanf("%d%d",&n,&m);
ll now=1ll*n*n;
while(m--)
{
scanf("%d%d",&x,&y);
if(!a[x])
{
now-=n;
now+=cnt2;
}
if(!b[y])
{
now-=n;
now+=cnt1;
}
if(!a[x])cnt1++;
if(!b[y])cnt2++;
if(!a[x]&&!b[y])now++;
a[x]=b[y]=true;
printf("%lld ",now);
}
//system ("pause");
return ;
}
Cells Not Under Attack的更多相关文章
- CF 701B Cells Not Under Attack(想法题)
题目链接: 传送门 Cells Not Under Attack time limit per test:2 second memory limit per test:256 megabyte ...
- Codeforces Round #364 (Div. 2) B. Cells Not Under Attack
B. Cells Not Under Attack time limit per test 2 seconds memory limit per test 256 megabytes input st ...
- Codeforces Round #364 (Div. 2) Cells Not Under Attack
Cells Not Under Attack 题意: 给出n*n的地图,有给你m个坐标,是棋子,一个棋子可以把一行一列都攻击到,在根据下面的图,就可以看出让你求阴影(即没有被攻击)的方块个数 题解: ...
- codeforces #364b Cells Not Under Attack
比赛的时候 long long sum=n*n,计算不出1e10长度到数,没有搞掉. 哎,以后要注意这个地方.这个题其实不难: 统计能被攻击到的个数,然后用总的个数减掉就可以了.注意有些地方重复计算, ...
- codeforces 701B B. Cells Not Under Attack(水题)
题目链接: B. Cells Not Under Attack 题意: n*n的棋盘,现在放m个棋子,放一个棋子这一行和这一列就不会under attack了,每次放棋子回答有多少点还可能under ...
- codeforces 701 B. Cells Not Under Attack
B. Cells Not Under Attack time limit per test 2 seconds memory limit per test 256 megabytes input st ...
- cf701B Cells Not Under Attack
Vasya has the square chessboard of size n × n and m rooks. Initially the chessboard is empty. Vasya ...
- CodeForces 701B Cells Not Under Attack
题目链接:http://codeforces.com/problemset/problem/701/B 题目大意: 输入一个数n,m, 生成n*n的矩阵,用户输入m个点的位置,该点会影响该行和该列,每 ...
- Codeforces #364 DIV2
~A题 A. Cards time limit per test 1 second memory limit per test 256 megabytes input standard input ...
随机推荐
- 用sqlyog远程连接LINUX系统的MYSQL出现错解决方法
无法给远程连接的用户权限问题.结果这样子操作mysql库,即可解决.在本机登入mysql后,更改 “mysql” 数据库里的 “user” 表里的 “host” 项,从”localhost”改称'%' ...
- html 任意表格
<!DOCTYPE html><html> <head> <meta charset="utf-8" /> ...
- hdu_4714_Tree2cycle(树形DP)
题目连接:http://acm.hdu.edu.cn/showproblem.php?pid=4714 题意:给你N个点N-1条边,形成一个树,让你拆树,并连接成一个环,每拆一次,连接一次,消耗1,问 ...
- gridview列绑定HyperLink
<asp:HyperLink ID="HyperLink1" Target="_blank" runat="server" Navig ...
- Petit FatFs
FatFs is a generic FAT/exFAT file system module for small embedded systems. The FatFs module is writ ...
- MySQL SQL优化——分片搜索
DELIMITER $$ DROP PROCEDURE IF EXISTS `test_release`.`Sp_JP_A_NotifyBegin`$$ CREATE DEFINER=`encysys ...
- Sql Server异常捕获 try catch
declare @num int begin try end try begin catch select ERROR_LINE() as 错误行数, ERROR_MESSAGE() as 错误消息 ...
- Dominating Patterns
Dominating Patterns Time Limit:3000MS Memory Limit:Unknown 64bit IO Format:%lld & %llu Descr ...
- Linux 安全模块
LSM是Linux Secrity Module的简称,即linux安全模块.其是一种轻量级通用访问控制框架,适合于多种访问控制模型在它上面以内核可加载模块的形实现.用户可以根据自己的需求选择合适的安 ...
- 删除 win8.1中的网络1,网络2,宽带连接1,宽带连接2等网络记录
新建txt文本,保存如下内容为reg文档: Windows Registry Editor Version 5.00 [-HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\W ...
