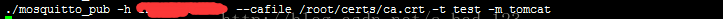Mosquitto 单向SSL配置
Mosquitto 单向SSL配置
摘自:https://blog.csdn.net/a_bcd_123/article/details/70167833
1.生成证书
要单向配置SSL 需要 做三项前置工作
1. 生成CA证书
2.生成server 端证书,server 端key
github 的一个开源项目已经做到这点 ,详情可见 https://github.com/iandl/mqttitude/blob/master/tools/TLS/generate-CA.sh
为方便阅读,整个shell 代码先贴出来
#!/bin/sh
#(@)generate-CA.sh - Create CA key-pair and server key-pair signed by CA
# Copyright (c) 2013 Jan-Piet Mens <jpmens()gmail.com>
# All rights reserved.
#
# Redistribution and use in source and binary forms, with or without
# modification, are permitted provided that the following conditions are met:
#
# 1. Redistributions of source code must retain the above copyright notice,
# this list of conditions and the following disclaimer.
# 2. Redistributions in binary form must reproduce the above copyright
# notice, this list of conditions and the following disclaimer in the
# documentation and/or other materials provided with the distribution.
# 3. Neither the name of mosquitto nor the names of its
# contributors may be used to endorse or promote products derived from
# this software without specific prior written permission.
#
# THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS"
# AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
# IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
# ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE
# LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
# CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
# SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
# INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN
# CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
# ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
# POSSIBILITY OF SUCH DAMAGE.
set -e
DIR=${TARGET:='.'}
# A space-separated list of alternate hostnames (subjAltName)
# may be empty ""
ALTHOSTNAMES="broker.example.com foo.example.de"
CA_ORG='/O=MQTTitude.org/emailAddress=nobody@example.net'
CA_DN="/CN=An MQTT broker${CA_ORG}"
CACERT=${DIR}/ca
SERVER=${DIR}/server
SERVER_DN="/CN=$(hostname -f)$CA_ORG"
keybits=2048
openssl=$(which openssl)
function maxdays() {
nowyear=$(date +%Y)
years=$(expr 2032 - $nowyear)
days=$(expr $years '*' 365)
echo $days
}
function getipaddresses() {
/sbin/ifconfig |
sed -En '/inet6? /p' |
sed -Ee 's/inet6? (addr:)?//' |
awk '{print $1;}' |
sed -e 's/[%/].*//' |
egrep -v '(::1|127\.0\.0\.1)' # omit loopback to add it later
}
function addresslist() {
ALIST=""
for a in $(getipaddresses); do
ALIST="${ALIST}IP:$a,"
done
ALIST="${ALIST}IP:127.0.0.1,IP:::1,"
for h in $(echo ${ALTHOSTNAMES}); do
ALIST="${ALIST}DNS:$h,"
done
ALIST="${ALIST}DNS:localhost"
echo $ALIST
}
days=$(maxdays)
if [ -n "$CAKILLFILES" ]; then
rm -f $CACERT.??? $SERVER.??? $CACERT.srl
fi
if [ ! -f $CACERT.crt ]; then
# Create un-encrypted (!) key
$openssl req -newkey rsa:${keybits} -x509 -nodes -days $days -extensions v3_ca -keyout $CACERT.key -out $CACERT.crt -subj "${CA_DN}"
echo "Created CA certificate in $CACERT.crt"
$openssl x509 -in $CACERT.crt -nameopt multiline -subject -noout
chmod 400 $CACERT.key
chmod 444 $CACERT.crt
fi
if [ ! -f $SERVER.key ]; then
echo "--- Creating server key and signing request"
$openssl genrsa -out $SERVER.key $keybits
$openssl req -new \
-out $SERVER.csr \
-key $SERVER.key \
-subj "${SERVER_DN}"
chmod 400 $SERVER.key
fi
if [ -f $SERVER.csr -a ! -f $SERVER.crt ]; then
# There's no way to pass subjAltName on the CLI so
# create a cnf file and use that.
CNF=`mktemp /tmp/cacnf.XXXXXXXX` || { echo "$0: can't create temp file" >&2; exit 1; }
sed -e 's/^.*%%% //' > $CNF <<\!ENDconfig
%%% [ JPMextensions ]
%%% basicConstraints = critical,CA:false
%%% nsCertType = server
%%% keyUsage = nonRepudiation, digitalSignature, keyEncipherment
%%% nsComment = "Broker Certificate"
%%% subjectKeyIdentifier = hash
%%% authorityKeyIdentifier = keyid,issuer:always
%%% subjectAltName = $ENV::SUBJALTNAME
%%% # issuerAltName = issuer:copy
%%% nsCaRevocationUrl = http://mqttitude.org/carev/
%%% nsRevocationUrl = http://mqttitude.org/carev/
!ENDconfig
SUBJALTNAME="$(addresslist)"
export SUBJALTNAME # Use environment. Because I can. ;-)
echo "--- Creating and signing server certificate"
$openssl x509 -req \
-in $SERVER.csr \
-CA $CACERT.crt \
-CAkey $CACERT.key \
-CAcreateserial \
-CAserial "${DIR}/ca.srl" \
-out $SERVER.crt \
-days $days \
-extfile ${CNF} \
-extensions JPMextensions
rm -f $CNF
chmod 444 $SERVER.crt
fi
实际过程中大家可根据自己的需要修改这段脚本的内容,为了快速搭建我们的单向SSL, 我们这里不做任何修改,直接执行这段shell
执行完成后可生成 server.crt server.csr server.ke ca.crt ca.key ca.srl
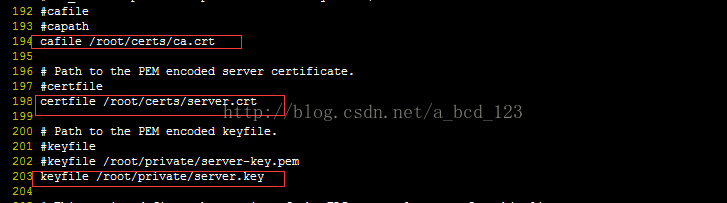
2.配置mosquitto 配置文件
ca.crt, sever.crt, server.key 是第一步中生成的文件
启动 broker
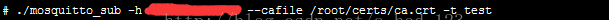
启动 subscribe 端, 这里需要注意,如果sbuscreibe 端和broker 不在同一台机器,请将第一步生成的ca.crt 拷贝到 该机器
启动 publish 端, 如果publish 端和broker 不在同一台机器,请将第一步生成的ca.crt 拷贝到 该机器
配置完成,可以发送,接收消息了
Mosquitto 单向SSL配置的更多相关文章
- mosquitto --- 单向认证
1.生成证书要单向配置SSL 需要 做三项前置工作 1. 生成CA证书 2.生成server 端证书,server 端key github 的一个开源项目已经做到这点 ,详情可见 https://gi ...
- SSL 通信原理及Tomcat SSL 配置
SSL 通信原理及Tomcat SSL 双向配置 目录1 参考资料 .................................................................. ...
- Apollo单向SSL认证(1)
参考链接:https://www.cnblogs.com/benwu/articles/4891758.html keytool -genkey -alias mybroker -keyalg RSA ...
- 百度CDN 网站SSL 配置
百度CDN SSL配置步骤 一般从SSL提供商购买到的证书是CRT二进制格式的. 1. 将 CRT 导入到IIS中, 然后从IIS中导出为PFX格式 2. 下载openssl,执行下面命令 提取用户证 ...
- Nginx SSL配置过程
1. 在godaddy购买了UCC SSL(最多5个域名)的SSL证书 2. 设置证书 -- 管理 -- 3. 需要制作证书申请CSR文件(在线工具制作或者openssl命令制作),保存CSR和key ...
- ssl配置
Apache SSL配置 作者: JeremyWei | 可以转载, 但必须以超链接形式标明文章原始出处和作者信息及版权声明网址: http://weizhifeng.net/apache-ssl.h ...
- nginx反向代理cas server之1:多个cas server负载均衡配置以及ssl配置
系统环境采用centOS7 由于cas server不支持session持久化方式的共享,所以请用其他方式代替,例如:组播复制. 为什么不支持session持久化:http://blog.csdn.n ...
- centos7邮件服务器SSL配置
在上篇文章centos7搭建postfix邮件服务器的搭建中我们没有配置SSL,接下来我们在这篇文章中讲讲centos7邮件服务器SSL配置. 1. 创建SSL证书 [root@www ~]# cd ...
- Sahi (2) —— https/SSL配置(102 Tutorial)
Sahi (2) -- https/SSL配置(102 Tutorial) jvm版本: 1.8.0_65 sahi版本: Sahi Pro 6.1.0 参考来源: Sahi官网 Sahi Quick ...
随机推荐
- Ten Qualities of an Effective Team Player
If you were choosing team members for a business team in your organization, who would the best team ...
- java代码-----实现打印三角形
总结:今天我有个体会,喜欢不代表了解,了解不代表精通.我好失败 对于正三角形,就是注意空格.打星号.的实现. package com.a.b; public class Gl { public sta ...
- [转]java中byte转换int时为何与0xff进行与运算
在剖析该问题前请看如下代码public static String bytes2HexString(byte[] b) { String ret = ""; for (int ...
- 淘宝开源Web服务器Tengine基本安装步骤
Tengine 是由淘宝核心系统部基于Nginx开发的Web服务器,它在Nginx的基础上,针对大访问量 网站的需求,添加了很多功能和特性.Tengine的性能和稳定性已经在大型的网站如淘宝网,淘宝商 ...
- php 数组去重 (一维数组与二维数组)
数组中重复项的去除 一维数组的重复项: 使用array_unique函数即可,使用实例如下: <?php $aa=array("apple" ...
- node 通过指令创建一个package.json文件
描述包的文件是package.json文件. 一个这样的文件,里面的信息还是挺大的.我们可以放弃手动建立.为了练手我们有命令行来建一个这样的包; 完成name,varsion....license ...
- 5月16日上课笔记-js中DOM操作
一.DOM操作 DOM节点的操作 增加 删除 修改 节点的信息: nodeName 获取节点的标签名 parentNode 获取父节点 childNodes IE忽略回车换行,chrome回车换行是文 ...
- java之IO整理(中)
一:打印流/*System.out.println()重定向输出*/ /*public static void main(String[] args) { System.out.println(&qu ...
- oracle autotrace使用
通过以下方法可以把Autotrace的权限授予Everyone, 如果你需要限制Autotrace权限,可以把对public的授权改为对特定user的授权. D:\oracle\ora92>sq ...
- 【Oracle】安装Oracle 10gR2 For CentOS
Oracle10gR2安装安装环境项目 版本信息 备注操作系统 CentOS5.364bit Oracle数据库 Oracle10.2.0.4 64bit 硬件信 ...