Kubernetes实战总结 - Prometheus部署
什么是普罗米修斯?
Prometheus是最初在SoundCloud上构建的开源系统监视和警报工具包 。
自2012年成立以来,许多公司和组织都采用了Prometheus,该项目拥有非常活跃的开发人员和用户社区。
组件说明
- Prometheus:负责实现对K8s集群监控数据的获取,存储以及查询。
- PrometheusOperator:为Prometheus实例的部署和管理提供了简单的监视定义。
- KubeStateMetrics:是K8s集群资源使用情况的聚合器,收集数据给K8s集群内使用(如HPA)。
- AlertManager:负责将告警信息重复数据删除,分组和路由到正确的接收者集成。
- NodeExporter:用于采集集群中各个节点的资源使用情况。
- Grafana:一个跨平台的开源的度量分析和可视化工具。
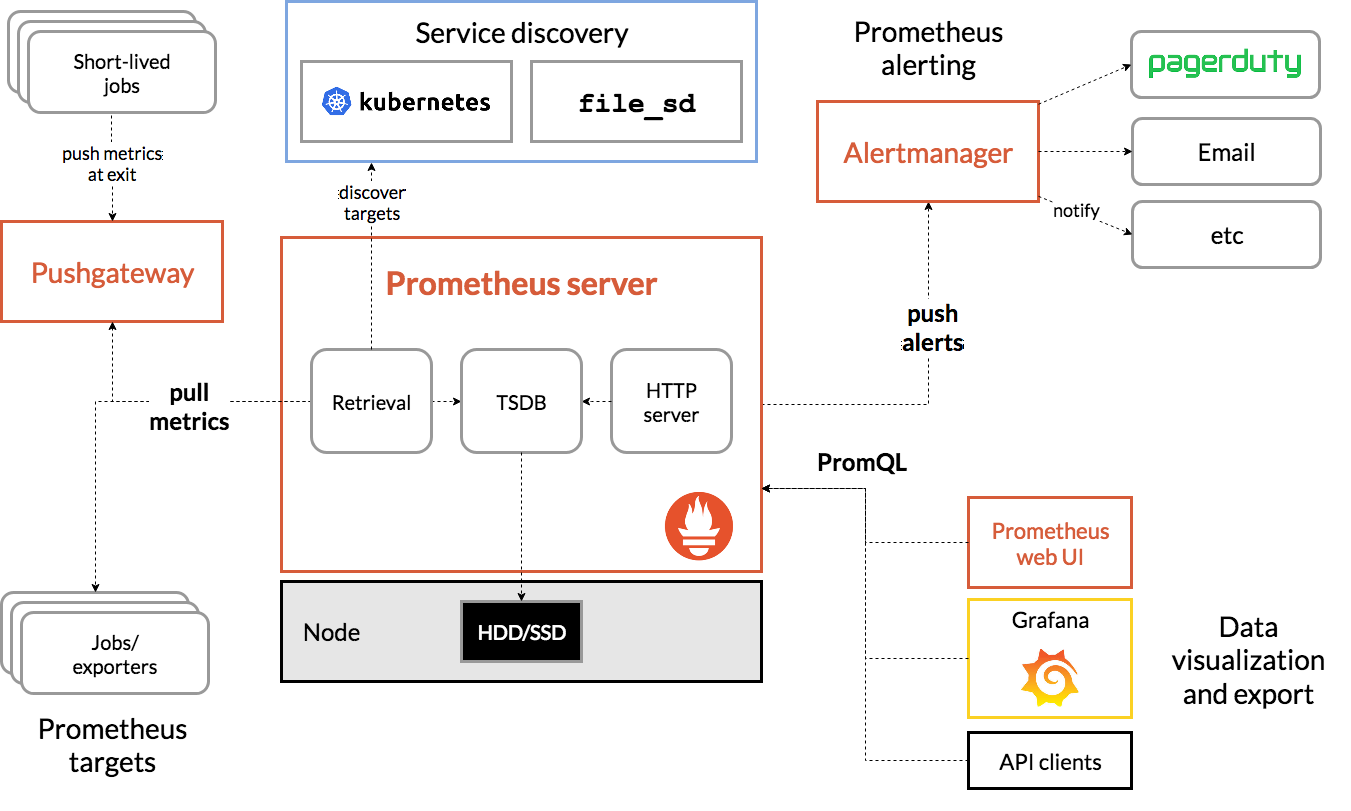
系统架构
什么时候合适?
Prometheus非常适合记录任何纯数字时间序列。
它既适合以机器为中心的监视,也适合于高度动态的面向服务的体系结构的监视。在微服务世界中,它对多维数据收集和查询的支持是一种特别的优势。
Prometheus的设计旨在提高可靠性,使其成为中断期间要使用的系统,以使您能够快速诊断问题。
每个Prometheus服务器都是独立的,而不依赖于网络存储或其他远程服务。当基础结构的其他部分损坏时,您可以依靠它,并且无需设置广泛的基础结构即可使用它。
什么时候不合适?
普罗米修斯重视可靠性。即使在故障情况下,您始终可以查看有关系统的可用统计信息。
如果您需要100%的准确性(例如按请求计费),则Prometheus并不是一个不错的选择,因为所收集的数据可能不会足够详细和完整。
在这种情况下,最好使用其他系统来收集和分析数据以进行计费,并使用Prometheus进行其余的监视。
部署安装
Github : https://github.com/coreos/kube-prometheus
1、下载官方源码文件(默认镜像源来自quay.io)
wget -o kube-prometheus.tgz https://github.com/coreos/kube-prometheus/archive/v0.3.0.tar.gz
- 当然,如果你的国外网不太友好,也可以下载本人百度云文件(已修改镜像源到aliyuncs)kube-prometheus-0.3.0.zip(ccer )
2、解压并部署安装
tar -zxvf kube-prometheus.tgz && cd kube-prometheus-0.3.0/manifests
kubectl create -f setup
until kubectl get servicemonitors --all-namespaces ; do date; sleep 1; echo ""; done
kubectl create -f .
[root@k8s-32 manifests]# ls -R
.:
alertmanager-alertmanager.yaml kube-state-metrics-service.yaml prometheus-clusterRole.yaml
alertmanager-secret.yaml node-exporter-clusterRoleBinding.yaml prometheus-operator-serviceMonitor.yaml
alertmanager-serviceAccount.yaml node-exporter-clusterRole.yaml prometheus-prometheus.yaml
alertmanager-serviceMonitor.yaml node-exporter-daemonset.yaml prometheus-roleBindingConfig.yaml
alertmanager-service.yaml node-exporter-serviceAccount.yaml prometheus-roleBindingSpecificNamespaces.yaml
grafana-dashboardDatasources.yaml node-exporter-serviceMonitor.yaml prometheus-roleConfig.yaml
grafana-dashboardDefinitions.yaml node-exporter-service.yaml prometheus-roleSpecificNamespaces.yaml
grafana-dashboardSources.yaml prometheus-adapter-apiService.yaml prometheus-rules.yaml
grafana-deployment.yaml prometheus-adapter-clusterRoleAggregatedMetricsReader.yaml prometheus-serviceAccount.yaml
grafana-serviceAccount.yaml prometheus-adapter-clusterRoleBindingDelegator.yaml prometheus-serviceMonitorApiserver.yaml
grafana-serviceMonitor.yaml prometheus-adapter-clusterRoleBinding.yaml prometheus-serviceMonitorCoreDNS.yaml
grafana-service.yaml prometheus-adapter-clusterRoleServerResources.yaml prometheus-serviceMonitorKubeControllerManager.yaml
kube-state-metrics-clusterRoleBinding.yaml prometheus-adapter-clusterRole.yaml prometheus-serviceMonitorKubelet.yaml
kube-state-metrics-clusterRole.yaml prometheus-adapter-configMap.yaml prometheus-serviceMonitorKubeScheduler.yaml
kube-state-metrics-deployment.yaml prometheus-adapter-deployment.yaml prometheus-serviceMonitor.yaml
kube-state-metrics-roleBinding.yaml prometheus-adapter-roleBindingAuthReader.yaml prometheus-service.yaml
kube-state-metrics-role.yaml prometheus-adapter-serviceAccount.yaml setup
kube-state-metrics-serviceAccount.yaml prometheus-adapter-service.yaml
kube-state-metrics-serviceMonitor.yaml prometheus-clusterRoleBinding.yaml ./setup:
0namespace-namespace.yaml prometheus-operator-0prometheusruleCustomResourceDefinition.yaml prometheus-operator-deployment.yaml
prometheus-operator-0alertmanagerCustomResourceDefinition.yaml prometheus-operator-0servicemonitorCustomResourceDefinition.yaml prometheus-operator-serviceAccount.yaml
prometheus-operator-0podmonitorCustomResourceDefinition.yaml prometheus-operator-clusterRoleBinding.yaml prometheus-operator-service.yaml
prometheus-operator-0prometheusCustomResourceDefinition.yaml prometheus-operator-clusterRole.yamlls -R
[root@k8s-32 manifests]# kubectl create -f setup/.
namespace/monitoring created
customresourcedefinition.apiextensions.k8s.io/alertmanagers.monitoring.coreos.com created
customresourcedefinition.apiextensions.k8s.io/podmonitors.monitoring.coreos.com created
customresourcedefinition.apiextensions.k8s.io/prometheuses.monitoring.coreos.com created
customresourcedefinition.apiextensions.k8s.io/prometheusrules.monitoring.coreos.com created
customresourcedefinition.apiextensions.k8s.io/servicemonitors.monitoring.coreos.com created
clusterrole.rbac.authorization.k8s.io/prometheus-operator created
clusterrolebinding.rbac.authorization.k8s.io/prometheus-operator created
deployment.apps/prometheus-operator created
service/prometheus-operator created
serviceaccount/prometheus-operator created
[root@k8s-32 manifests]# kubectl create -f .
alertmanager.monitoring.coreos.com/main created
secret/alertmanager-main created
service/alertmanager-main created
serviceaccount/alertmanager-main created
servicemonitor.monitoring.coreos.com/alertmanager created
secret/grafana-datasources created
configmap/grafana-dashboard-apiserver created
configmap/grafana-dashboard-cluster-total created
configmap/grafana-dashboard-controller-manager created
configmap/grafana-dashboard-k8s-resources-cluster created
configmap/grafana-dashboard-k8s-resources-namespace created
configmap/grafana-dashboard-k8s-resources-node created
configmap/grafana-dashboard-k8s-resources-pod created
configmap/grafana-dashboard-k8s-resources-workload created
configmap/grafana-dashboard-k8s-resources-workloads-namespace created
configmap/grafana-dashboard-kubelet created
configmap/grafana-dashboard-namespace-by-pod created
configmap/grafana-dashboard-namespace-by-workload created
configmap/grafana-dashboard-node-cluster-rsrc-use created
configmap/grafana-dashboard-node-rsrc-use created
configmap/grafana-dashboard-nodes created
configmap/grafana-dashboard-persistentvolumesusage created
configmap/grafana-dashboard-pod-total created
configmap/grafana-dashboard-pods created
configmap/grafana-dashboard-prometheus-remote-write created
configmap/grafana-dashboard-prometheus created
configmap/grafana-dashboard-proxy created
configmap/grafana-dashboard-scheduler created
configmap/grafana-dashboard-statefulset created
configmap/grafana-dashboard-workload-total created
configmap/grafana-dashboards created
deployment.apps/grafana created
service/grafana created
serviceaccount/grafana created
servicemonitor.monitoring.coreos.com/grafana created
clusterrole.rbac.authorization.k8s.io/kube-state-metrics created
clusterrolebinding.rbac.authorization.k8s.io/kube-state-metrics created
deployment.apps/kube-state-metrics created
role.rbac.authorization.k8s.io/kube-state-metrics created
rolebinding.rbac.authorization.k8s.io/kube-state-metrics created
service/kube-state-metrics created
serviceaccount/kube-state-metrics created
servicemonitor.monitoring.coreos.com/kube-state-metrics created
clusterrole.rbac.authorization.k8s.io/node-exporter created
clusterrolebinding.rbac.authorization.k8s.io/node-exporter created
daemonset.apps/node-exporter created
service/node-exporter created
serviceaccount/node-exporter created
servicemonitor.monitoring.coreos.com/node-exporter created
apiservice.apiregistration.k8s.io/v1beta1.metrics.k8s.io created
clusterrole.rbac.authorization.k8s.io/prometheus-adapter created
clusterrole.rbac.authorization.k8s.io/system:aggregated-metrics-reader created
clusterrolebinding.rbac.authorization.k8s.io/prometheus-adapter created
clusterrolebinding.rbac.authorization.k8s.io/resource-metrics:system:auth-delegator created
clusterrole.rbac.authorization.k8s.io/resource-metrics-server-resources created
configmap/adapter-config created
deployment.apps/prometheus-adapter created
rolebinding.rbac.authorization.k8s.io/resource-metrics-auth-reader created
service/prometheus-adapter created
serviceaccount/prometheus-adapter created
clusterrole.rbac.authorization.k8s.io/prometheus-k8s created
clusterrolebinding.rbac.authorization.k8s.io/prometheus-k8s created
servicemonitor.monitoring.coreos.com/prometheus-operator created
prometheus.monitoring.coreos.com/k8s created
rolebinding.rbac.authorization.k8s.io/prometheus-k8s-config created
rolebinding.rbac.authorization.k8s.io/prometheus-k8s created
rolebinding.rbac.authorization.k8s.io/prometheus-k8s created
rolebinding.rbac.authorization.k8s.io/prometheus-k8s created
role.rbac.authorization.k8s.io/prometheus-k8s-config created
role.rbac.authorization.k8s.io/prometheus-k8s created
role.rbac.authorization.k8s.io/prometheus-k8s created
role.rbac.authorization.k8s.io/prometheus-k8s created
prometheusrule.monitoring.coreos.com/prometheus-k8s-rules created
service/prometheus-k8s created
serviceaccount/prometheus-k8s created
servicemonitor.monitoring.coreos.com/prometheus created
servicemonitor.monitoring.coreos.com/kube-apiserver created
servicemonitor.monitoring.coreos.com/coredns created
servicemonitor.monitoring.coreos.com/kube-controller-manager created
servicemonitor.monitoring.coreos.com/kube-scheduler created
servicemonitor.monitoring.coreos.com/kubelet createdkubectl create -f .
3、等待部署完成
kubectl get pod -n monitoring
NAME READY STATUS RESTARTS AGE
alertmanager-main-0 2/2 Running 0 65m
alertmanager-main-1 2/2 Running 0 65m
alertmanager-main-2 2/2 Running 0 65m
grafana-7c54b4677d-btwfb 1/1 Running 0 65m
kube-state-metrics-58b656b699-p8m29 3/3 Running 0 65m
node-exporter-rc5mx 2/2 Running 0 65m
node-exporter-vdzkb 2/2 Running 0 65m
node-exporter-xzdw2 2/2 Running 0 65m
prometheus-adapter-7d6f96974c-76m4z 1/1 Running 0 65m
prometheus-k8s-0 3/3 Running 1 65m
prometheus-k8s-1 3/3 Running 1 65m
prometheus-operator-5bd99d6457-89n7h 1/1 Running 0 66m
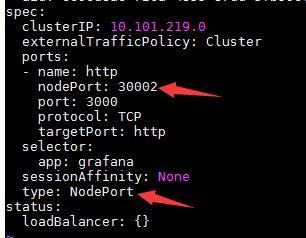
4、更改访问模式(ClusterIP => NodePort)
1)Prometheus
kubectl edit svc/prometheus-k8s -n monitoring
2)Alert Manager
kubectl edit svc/alertmanager-main -n monitoring
3)Grafana
kubectl edit svc/grafana -n monitoring
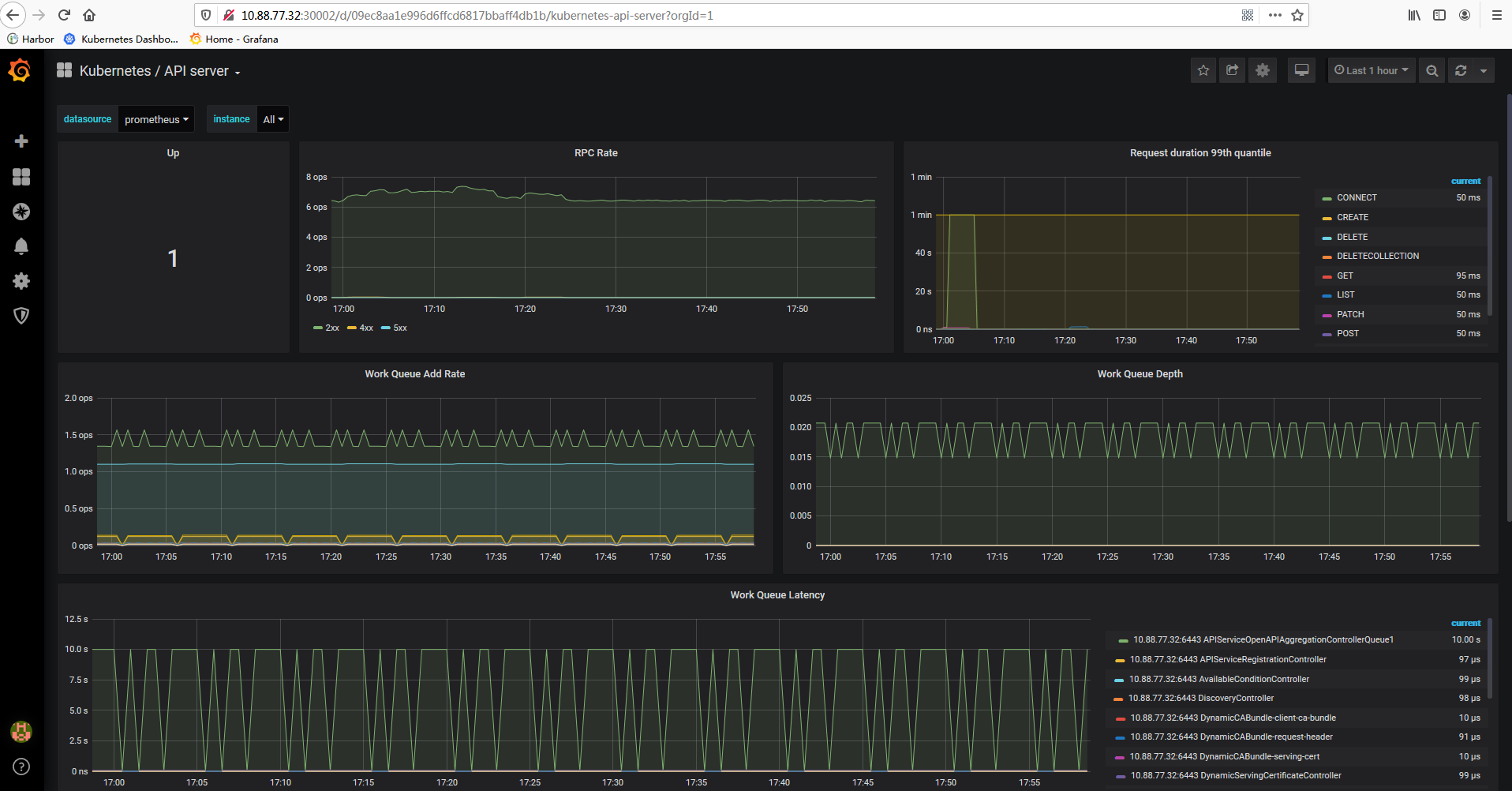
5、访问MasterIP:Port,其中Grafana默认用户名和密码都是admin
>>> 普罗米修斯功能强大,目前我也还没有完全掌握,具体应用还需要大家自己深度学习。
作者:Leozhanggg
出处:https://www.cnblogs.com/leozhanggg/p/12661566.html
本文版权归作者和博客园共有,欢迎转载,但未经作者同意必须保留此段声明,且在文章页面明显位置给出原文连接,否则保留追究法律责任的权利。
Kubernetes实战总结 - Prometheus部署的更多相关文章
- kubernetes实战篇之部署一个.net core微服务项目
目录 继上一篇kubernetes理论知识完结.本篇主要讲解基于nexus搭建一个docker镜像仓库(当然大家实践过程是不必完全跟着做,也可以搭建harbor仓库或者直接把镜像推送到docker h ...
- Kubernetes实战总结 - 自定义Prometheus
一.概述 首先Prometheus整体监控结构略微复杂,一个个部署并不简单.另外监控Kubernetes就需要访问内部数据,必定需要进行认证.鉴权.准入控制, 那么这一整套下来将变得难上加难,而且还需 ...
- kubernetes二进制高可用部署实战
环境: 192.168.30.20 VIP(虚拟) 192.168.30.21 master1 192.168.30.22 master2 192.168.30.23 node1 192.168.30 ...
- 新书推荐《再也不踩坑的Kubernetes实战指南》
<再也不踩坑的Kubernetes实战指南>终于出版啦.目前可以在京东.天猫购买,京东自营和当当网预计一个星期左右上架. 本书贴合生产环境经验,解决在初次使用或者是构建集群中的痛点,帮 ...
- 2020 最新 Kubernetes实战指南
1.Kubernetes带来的变革 对于开发人员 由于公司业务多,开发环境.测试环境.预生产环境和生产环境都是隔离的,而且除了生产环境,为了节省成本,其他环境可能是没有日志收集的,在没有用k8s的 ...
- Kubernetes实战总结 - 阿里云ECS自建K8S集群
一.概述 详情参考阿里云说明:https://help.aliyun.com/document_detail/98886.html?spm=a2c4g.11186623.6.1078.323b1c9b ...
- OpenFaaS实战之一:部署
欢迎访问我的GitHub https://github.com/zq2599/blog_demos 内容:所有原创文章分类汇总及配套源码,涉及Java.Docker.Kubernetes.DevOPS ...
- Kubernetes(k8s)集群部署(k8s企业级Docker容器集群管理)系列目录
0.目录 整体架构目录:ASP.NET Core分布式项目实战-目录 k8s架构目录:Kubernetes(k8s)集群部署(k8s企业级Docker容器集群管理)系列目录 一.感谢 在此感谢.net ...
- kubernetes实战(二十五):kubeadm 安装 高可用 k8s v1.13.x
1.系统环境 使用kubeadm安装高可用k8s v.13.x较为简单,相比以往的版本省去了很多步骤. kubeadm安装高可用k8s v.11 和 v1.12 点我 主机信息 主机名 IP地址 说明 ...
随机推荐
- 【译文连载】 理解Istio服务网格(第六章 可观测性)
全书目录 第一章 概述 第二章 安装 第三章 流控 第四章 服务弹性 第五章 混沌测试 本文目录 第6章 可观测性 6.1 分布式调用链跟踪(tracing) 6.1.1 基本概念 6.1.2 Ja ...
- Node.Js的热更新服务——supervisor
因为目前项目每次修改文件要看效果,必须重启服务:node app.js再进入浏览器看效果,很是麻烦.所幸的是有很多第三方的管理工具(supervisor,hotnode,forever,pm2等),当 ...
- ES6拓展的对象功能
前言:因为之前看过很多的博客啊,书籍啊但是最后都雁过无痕,再问我基本没什么印象,所以就迫使自己看书的时候记点笔记,因为懒得写字[捂脸],现在是打字比写字要快好多,所以就写博客吧! ES6规范明确定义了 ...
- vue的子组件不能进行router的切换
在用vue开发过程中,偶然一次使用在子组件中进行router的切换,发现不起作用,后来才反应过来,子组件只是一个组件,vue的路由的切换只能是在父组件(也就是真正的页面)里面进行跳转!
- NoVNC安装部署
noVNC 是一个 HTML5 VNC 客户端,采用 HTML 5 WebSockets, Canvas 和 JavaScript 实现,noVNC 被普遍用在各大云计算.虚拟机控制面板中,比如 Op ...
- Spring Boot从入门到精通(九)整合Spring Data JPA应用框架
JPA是什么? JPA全称Java Persistence API,是Sun官方提出的Java持久化规范.是JDK 5.0注解或XML描述对象-关系表的映射关系,并将运行期的实体对象持久化到数据库中. ...
- Simulink仿真入门到精通(十四) Simulink自定义环境
14.1 Simulink环境自定义功能 sl_sustomization.m函数是Simulink提供给用户使用MATLAB语言自定义Simulink标准人机界面的函数机制.若sl_sustomiz ...
- Python xlsxwriter模块
1.简介: xlsxWriter支持多种excle功能:与excel完美兼容:写大文件,速度快且只占用很小的内存空间不支持读或者改现有的excel文件 2.安装: pip install xlsxwr ...
- 数据结构 - List 接口
简介 List接口继承自Collection接口,是Collection三大延伸接口之一.List中的元素都是有序的,并且都支持用索引访问.同时List中的元素允许重复. public interfa ...
- channel的基本使用
1.管道分类 读写管道 只读管道 只写管道 缓冲通道 :创建时指定大小(如果不指定默认为非缓冲通道) 2.正确使用管道 管道关闭后自能读,不能写 写入管道不能超过管道的容量cap,满容量还写则会阻塞 ...
