Chapter 5: Design and implement security
Configure authentication
Authenticating users
IIS authentication
- Anonymous
- ASP.net impersonation
- Basic
transmit username/password between client/server in Base64 encoded but not encrypted. - Digest
username/password are encrypted - Forms
1: without using built-in windows security system
2: use FormsAuthentication.SetAuthCookie to make authentication token available for the rest of the session. - Windows
supported only in microsoft browser
use NTLM/Kerberos
straightforward and easy to implement, especially on intranet. - ASP.net impersonation authentication
independent of authentication mode configured in Web.config file
System.Security.Principal.IPrincipal / System.Security.Principal.IIdentity
- WindowsIdentity/WindowsPrincipal
- FormsIdentity/GenericPrincipal
- GenericIdentity/GenericPrinciapl
use AuthorizeAttribute to enforce authentication
- Form authentication + SimpleMembership + WebSecurity
Windows authentication- use Active directory to manage users
- all users are members of your domain
- require users to use IE or Microsoft browser
Form authentication - use standard ASP.net membership provider db schema or your own
Custom authentication - create a custom provider by implementing IIdentity or IPrincipal to interact with underlying authentication mechanism
Manage user session by cookies
FormsAuthenticationTicket authTicket = new FormsAuthenticationTicket(
1,
userName,
DateTime.Now,
DateTime.Now.AddDays(90),
createPersistentCookie, // a Boolean indicating whether a cookie
// should be created on the user's machine
String.Join(";",rolesArr) //user's roles
);
// add cookie to response stream
string encTicket = FormsAuthentication.Encrypt(authTicket);
System.Web.HttpCookie authCookie = new System.Web.HttpCookie(FormsAuthentication.
FormsCookieName, encTicket);
System.Web.HttpContext.Current.Response.Cookies.Add(authCookie);
Configuring membership providers
- use SimpleMembershipProvider/WebSecurity helper classes
Creating custom membership providers
- ActiveDirectoryProvider for app use windows authentication
- SqlMembershipProvider for form authentication
Configure and apply authorization
- create roles
- configure roles
configure a SQL membership role provider in Web.config file
use InitializeDatabaseConnection(...) for SimpleMembershipProvider with SimpleRole. - Authorizing roles programmatically
- applying Authorize attribute
- check in code via followings
*RoleProvider.GetRolesForUser, RoleProvider.IsUserInRole, HttpContext.User.IsInRole
*WebSecurity.RequireRoles(...)
- creating custom role providers
- Implementing WCF service authorization
Design and implement claims-based authentication across federated identity stores
- Implementing federated authentication by using Windows Azure Access Control Service (ACS)
ACS features includes:- integrates with Windows Identity Foundation (WIF)
- support well-known identity providers such as Facebook, Microsoft account, Yahoo and Google
- support Active Directory Federation Services (ADFS) 2.0
- support OAuth 2.0, WS-Trust and WS-Federation protocols
- support various token formats, include JSON Web Token (JWT), Security Assertion Markup Language (SAML) and Simple Web Token (SWT)
- provides a web-based management portal
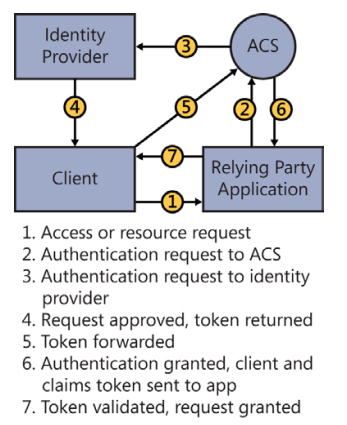
- Creating a custom security token by using WIF
- Handling token formats for SAML and SWT tokens
Manage data integrity
encryption terminology
- Encryption: DES, AES
- Hashing: MD5, SHA
- Salting
Applying encryption to application data
- Symmetric: AES, DES, RC2, Rijindael, TripleDES
- Asymmetric: DSA, ECDiffieHellman, ECDsa, RSA
using (RijndaelManaged rijndaelManaged = new RijndaelManaged())
{
// assumes that the key and initialization vectors are already configured
CryptoStream crypoStream = new CryptoStream(myManagedStream, rijndaelManaged.
CreateEncryptor(),CryptoStreamMode.Write);
};
using (RijndaelManaged rijndaelManaged = new RijndaelManaged())
{
// assumes that the key and initialization vectors are already configured
CryptoStream crypoStream = new CryptoStream(myManagedStream, rijndaelManaged.
CreateDecryptor(),CryptoStreamMode.Read);
};
Applying encryption to the configuraion sections of an application
- DPAPIProtectedConfigurationProvider
- RsaProtectedConfigurationProvider: allow export/import of the keys used for encryption/decryption
- use aspnet_regiis to encrypt/decrypt sections of the Web.confg file.
Signing application data to prevent tampering
// create the hash code of the text to sign
SHA1 sha = SHA1.Create();
byte[] hashcode = sha.ComputeHash(TextToConvert);
// use the CreateSignature method to sign the data
DSA dsa = DSA.Create();
byte[] signature = dsa.CreateSignature(hashcode);
// create the hash code of the text to verify
SHA1 sha = SHA1.Create();
byte[] hashcode = sha.ComputeHash(TextToVerify);
// use the VerifySignature method to verify the DSA signature
DSA dsa = DSA.Create();
bool isSignatureValid = dsa.VerifySignature(hashcode, signature);
Implement a secure site with ASP.NET
Securing communication by applying SSL/TLS certificates
setup site with certificate and httpsSalt and hash passwords for storage
Using HTML encoding to prevent cross-site scripting attacks (AntiXSS Library)
- use @Html.Encode()
- encode the data before saving to db
- use AntiXSS library from NuGet
Implementing deferred validation and handle unvalidated requests
Preventing SQL injection attacks by parameterizing queries
Preventing cross-site request forgeries (XSRFs)
[RequireSession]
[AcceptVerbs(HttpVerbs.Post)]
[HttpPost]
[ValidateAntiForgeryToken]
public ActionResult Login(string username, string password, string remember, string deviceToken, string apid)
{
}
@using (Html.BeginForm("Login", "Authorize"))
{
@Html.AntiForgeryToken();
}
internally cookie is used for XSRF validation.
Chapter 5: Design and implement security的更多相关文章
- Chapter 2: Design the user experience
Apply the user interface design for a web application 介绍了Css的常用属性和html5的新element,以及Htmlhelper的简单方法,如 ...
- Chapter 1: Design the application architecture
1.1 Plan the application layers 提到了repository pattern,SoC(Separation of Concern), 进而提及MVC,Action/Act ...
- Chapter 7. Design and Performance
本章将对MPEG4及H.264的实现细节进行讲解和比对. Motion Estimation 衡量运动估计的好坏有三种函数(第228页):MSE,MAE和SAE,其中由于SAE运算速度最快所以采用的最 ...
- MapReduce Design Patterns(chapter 1)(一)
Chapter 1.Design Patterns and MapReduce MapReduce 是一种运行于成百上千台机器上的处理数据的框架,目前被google,Hadoop等多家公司或社区广泛使 ...
- (转)MapReduce Design Patterns(chapter 1)(一)
翻译的是这本书: Chapter 1.Design Patterns and MapReduce MapReduce 是一种运行于成百上千台机器上的处理数据的框架,目前被google,Hadoop等多 ...
- Page Security
参见开发文档 Overview This document describes how to build applications that grant selected access to indi ...
- Chapter 6 — Improving ASP.NET Performance
https://msdn.microsoft.com/en-us/library/ff647787.aspx Retired Content This content is outdated and ...
- Quality in the Test Automation Review Process and Design Review Template
About this document Prerequisite knowledge/experience: Software Testing, Test Automation Applicable ...
- Security Software Engineer
Security Software Engineer Are you excited to be part of the VR revolution and work on cutting edge ...
随机推荐
- Python开发入门与实战17-新浪云部署
17. 新浪云部署 上一章节我们介绍了如何在本地windows服务器部署python django的网站,本章我们简要说明一下如何把python django工程部署到云服务上. 本章章节我们描述如何 ...
- rem ,em ,px的区别
参考网址:http://www.cnblogs.com/leejersey/p/3662612.html
- 禁用 baloo_file_extractor 加速 ubuntu 14.04 (KDE)
在复制了一堆零散文件后,系统同然变得奇卡,看看cpu和ram都占用不高,但看到这个进程 baloo_file_extractor 时不时地冒一下泡,怀疑是它在频繁访问硬盘.禁止它自动启动的方式: $ ...
- 怎么在excel中快速查找重复记录
假设数字在A列,数字从A1开始:方法一:辅助列中输入公式,数据重复时会出现“重复”提示.=IF(COUNTIF(A:A,A1)>1,"重复","") ,下 ...
- BZOJ 1537 二维偏序
#include <iostream> #include <cstring> #include <cstdio> #include <algorithm> ...
- linux命令:du
1.命令介绍: du用来查看文件和目录的使用空间. 2.命令格式: du [选项] 文件 3.命令参数: -a或-all 显示目录中个别文件的大小. -b或-bytes 显示目录或文件大小时,以b ...
- 推荐一个自动抽取pdf高亮笔记的web应用
很多人可能像我一样,喜欢用电脑或平板阅读pdf格式的论文或电子书,阅读过程中难免会使用highlight(高亮)工具标记出重要的文字和段落.有没有办法将所有高亮的部分抽取出来,形成一篇单独的笔记呢?下 ...
- A Simple Problem with Integers_树状数组
Problem Description Let A1, A2, ... , AN be N elements. You need to deal with two kinds of operation ...
- Android开源益智游戏“斗地主”单机版源代码
Android开源益智游戏"斗地主"单机版源代码 这是一个网上流传的Android开源斗地主单机版项目,运行结果如图: 项目源代码导入到Eclipse后可直接运行,我把ecl ...
- 探究toString()和valueOf()
1.用法如下:toString()方法:返回对象的字符串表示. 对象 操作 Array 将 Array 的元素转换为字符串.结果字符串由逗号分隔,且连接起来. Boolean 如果 Boolean 值 ...
