[转] An Introduction to Mutual SSL Authentication
1. Introduction
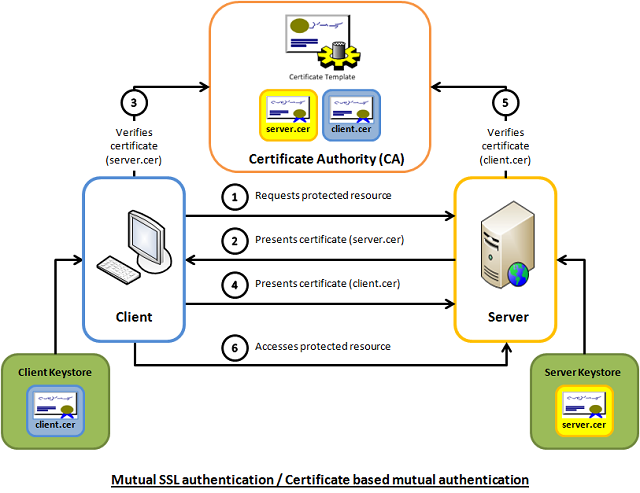
Mutual SSL authentication or certificate based mutual authentication refers to two parties authenticating each other through verifying the provided digital certificate so that both parties are assured of the others' identity. In technology terms, it refers to a client (web browser or client application) authenticating themselves to a server (website or server application) and that server also authenticating itself to the client through verifying the public key certificate/digital certificate issued by the trusted Certificate Authorities (CAs). Because authentication relies on digital certificates, certification authorities such as Verisign or Microsoft Certificate Server are an important part of the mutual authentication process. From a high-level point of view, the process of authenticating and establishing an encrypted channel using certificate-based mutual authentication involves the following steps:
- A client requests access to a protected resource.
- The server presents its certificate to the client.
- The client verifies the server’s certificate.
- If successful, the client sends its certificate to the server.
- The server verifies the client’s credentials.
- If successful, the server grants access to the protected resource requested by the client.
2. Background
Mutual SSL authentication works similar to SSL (Secure Socket Layer) authentication, with the addition of client authentication using digital signatures. Thus, SSL authentication and Mutual SSL authentication also informally known as 1-way SSL authentication and 2-way SSL authentication, respectively. As a developer, if you're interested in developing or be able to debug the mutual SSL authentication effectively, it can be very useful to understand the intricacies of the handshake messages happening under the hood.
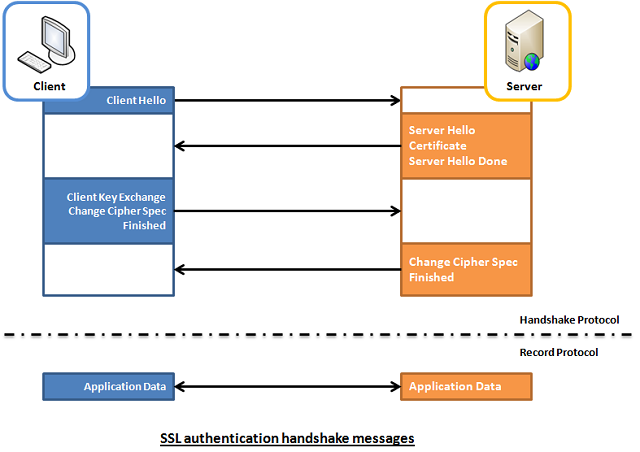
2.1 SSL authentication (server --> client)
In SSL authentication, the client is presented with a server’s certificate, the client computer might try to match the server’s CA against the client’s list of trusted CAs. If the issuing CA is trusted, the client will verify that the certificate is authentic and has not been tampered with. In this aspect, both client and server use 9 handshake messages to establish the encrypted channel prior to message exchanging.
- Client sends
ClientHellomessage proposing SSL options. - Server responds with
ServerHellomessage selecting the SSL options. - Server sends
Certificatemessage, which contains the server's certificate. - Server concludes its part of the negotiation with
ServerHelloDonemessage. - Client sends session key information (encrypted with server's public key) in
ClientKeyExchangemessage. - Client sends
ChangeCipherSpecmessage to activate the negotiated options for all future messages it will send. - Client sends
Finishedmessage to let the server check the newly activated options. - Server sends
ChangeCipherSpecmessage to activate the negotiated options for all future messages it will send. - Server sends
Finishedmessage to let the client check the newly activated options.
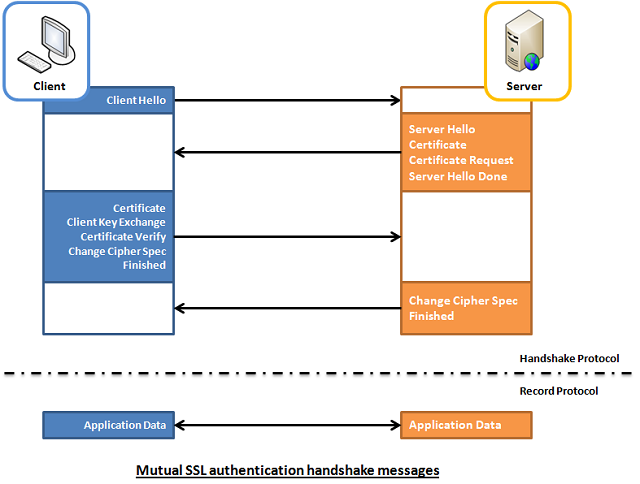
2.2 Mutual SSL Authentication (server <--> client)
Whereas in mutual SSL authentication, both client and server authenticate each other through the digital certificate so that both parties are assured of the others' identity. In this aspect, both client and server use 12 handshake messages to establish the encrypted channel prior to message exchanging.
- Client sends
ClientHellomessage proposing SSL options. - Server responds with
ServerHellomessage selecting the SSL options. - Server sends
Certificatemessage, which contains the server's certificate. - Server requests client's certificate in
CertificateRequestmessage, so that the connection can be mutually authenticated. - Server concludes its part of the negotiation with
ServerHelloDonemessage. - Client responds with
Certificatemessage, which contains the client's certificate. - Client sends session key information (encrypted with server's public key) in
ClientKeyExchangemessage. - Client sends a
CertificateVerifymessage to let the server know it owns the sent certificate. - Client sends
ChangeCipherSpecmessage to activate the negotiated options for all future messages it will send. - Client sends
Finishedmessage to let the server check the newly activated options. - Server sends
ChangeCipherSpecmessage to activate the negotiated options for all future messages it will send. - Server sends
Finishedmessage to let the client check the newly activated options.
3. Capture and Analyze
To help readers better visualize what's happening under the hood, I've enhanced a code example taken from the Microsoft website so that both client and server are capable of authenticating each other using the mutual SSL authentication. The code sample is very simple, and I won't illustrate much here. Basically, what it does is the client application sends a "Hello from the client." message to the server and the server application replies with a "Hello from the server." message, right after the mutual SSL authentication is completed successfully.
To capture the handshake messages transacted between the client and server, I use one of the popular and open-source packet analyzer tools called WireShark. It is a powerful and easy to use packet capture and analyzer tool, which can captures messages over a hundred of protocols. To learn more about how you can make use of this tool, please visit its website.
However, due to the lack of supported Loopback Interface in Windows operating system, I've to setup the client and server application running on two different machines in order to use Wireshark to capture their handshake messages. The handshake messages captured while running the applications are shown in the screenshot below, and the IP address "10.5.3.28" and "10.5.3.18" in the Source or Destination columns represents "The Client" and "The Server", respectively.
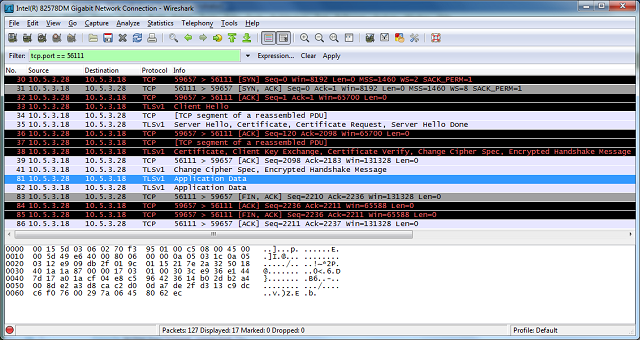
For analysis and verifying purposes, the handshake messages that we're concerned about are summarized and listed below:
No.30, 31 and 32 are the TCP (Transmission Control Protocol) handshake messages.
No.33 - Corresponding to Section 2.2 - Item 1.
No.35 - It contains 4 messages, which are:
- Server Hello - corresponding to Section 2.2 - Item 2.
- Certificate - corresponding to Section 2.2 - Item 3.
- Certificate Request - corresponding to Section 2.2 - Item 4.
- Server Hello Done - corresponding to Section 2.2 - Item 5.
No.38 - It contains 5 messages, which are
- Certificate - corresponding to Section 2.2 - Item 6.
- Client Key Exchange - corresponding to Section 2.2 - Item 7.
- Certificate Verify - corresponding to Section 2.2 - Item 8.
- Change Cipher Spec - corresponding to Section 2.2 - Item 9.
- Encrypted Handshake Message - corresponding to the Finish message listed in Section 2.2 - Item 10.
No.41 - It contains 2 messages, which are
- Change Cipher Spec - corresponding to Section 2.2 - Item 11.
- Encrypted Handshake Message - corresponding to the Finish message listed in Section 2.2 - Item 12.
Messages from No.81 onwards are application data messages exchange between the client and server.
4. Using the Code
The demo project included in this article, which is available for download at the top of this article, is intended to be run locally as opposed to the captured one shown above. This is because the certificates included in the demo project are generated for "localhost" use only. If you would like to try it out, please follow the steps outlined below to get it up and running on your workstation.
4.1 Install the Client and Server Certificate
Follow the steps outlined below to install the client and server certificates into the Windows certificate store:
- Unzip the downloaded demo project anywhere on the file system.
- Open a Snap-in window
- Start -> Run -> Type mmc
- Add/Remove Snap-in... (Ctrl-M)
- Add a Certificates snap-in for ‘My user account’
- Expand the (Trusted Root Certification Authorities)/Certificates node
- Right click the Certificates folder and choose All Tasks – Import
- Browse to the "Certificates" folder included in the demo project.
- Import the "MyServer.cer" and click through the remaining windows and finish.
- Repeat the step 4 and 5.
- Import the "MyClient.cer" certificate and click through the remaining windows and finish.
- Now, you should see the 2 imported certificates, which has the same details as the screenshot below (other irrelevant certificates are not shown here)
4.2 Build and Run the Solution
- Open the "MutualSslDemo.sln" solution in Visual Studio.
- Hit F5 to run the solution.
- Now, you shall see similar results as the one shown below:
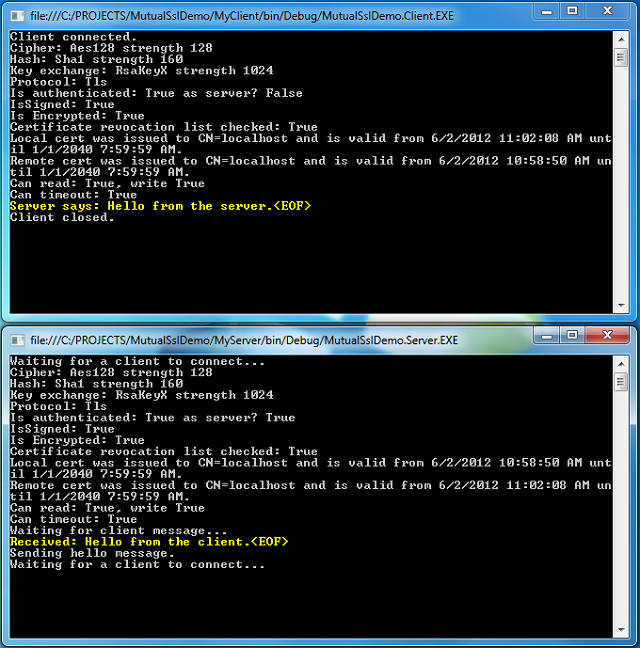
Of course, you can switch between the Mutual SSL authentication and SSL authentication behavior in the demo project (MyServer) by setting the argument "clientCertificateRequired" of the SslStream.AuthenticateAsServer function to true and false, respectively.
 Collapse | Copy Code
Collapse | Copy Code
// Mutual SSL authentication (requires client certificate)
sslStream.AuthenticateAsServer(certificate, true, SslProtocols.Default, true);
// SSL authentication only (do not require client certificate)
sslStream.AuthenticateAsServer(certificate, false, SslProtocols.Default, true);
[转] An Introduction to Mutual SSL Authentication的更多相关文章
- SSL (Secure Sockets Layer)
本文转载自SSL (Secure Sockets Layer) TLS简介 The Transport Layer Security (TLS) protocol aims primarily to ...
- 推荐一个比FiddlerCore好用的HTTP(S)代理服务器
为什么不用FiddlerCore? 说到FiddlerCore大家可能会比较陌生,那么它哥Fiddler就比较熟悉了:抓包.模拟低带宽.修改请求我平时比较常用.Fiddler的本质就是一个HTTP代理 ...
- 你想要了解但是却羞于发问的有关SSL的一切
Everything You Ever Wanted to Know About SSL (but Were Afraid to Ask) Or perhaps more accurately, &q ...
- Using JAAS Authentication in Java Clients---weblogic document
The following topics are covered in this section: JAAS and WebLogic Server JAAS Authentication Devel ...
- Cryptographic method and system
The present invention relates to the field of security of electronic data and/or communications. In ...
- 网络服务器之HTTPS服务
import ssl, socket, time if __name__ == "__main__": context = ssl.SSLContext(ssl.PROTOCOL_ ...
- Network Load Balancing Technical Overview--reference
http://technet.microsoft.com/en-us/library/bb742455.aspx Abstract Network Load Balancing, a clusteri ...
- mailsend - Send mail via SMTP protocol from command line
Introduction mailsend is a simple command line program to send mail via SMTP protocol. I used to sen ...
- How To Setup a CA
How To Setup a CA Original Version by Ian AldermanUpdated by Zach Miller Introduction You can set up ...
随机推荐
- checkpoint NGFW VM安装
step1:在VMworkstation中创建虚拟机向导,选择Linux 2.6内核 64位如下图: 虚拟机的配置建议如下: RAM:至少8GB Disk:120G CPU:四核 step2:使用IO ...
- command not found解决方案
如果新装的系统,运行一些很正常的诸如:shutdown,fdisk的命令时,悍然提示:bash:command not found.那么 首先就要考虑root 的$PATH里是否已经包含了这些环境变量 ...
- sql基本的增删查改语句
1.增---用于向表中插入新的行/数据 语法:insert into 表名(值1,值2,值3...) values(值1,值2,值3,...) 或者 语法:insert [into] <表名&g ...
- SpringBoot集成RabbitMQ 从零到一,学会MQ异步和解耦--
RabbitMQ 概念 RabbitMQ 即一个消息队列,_主要是用来实现应用程序的异步和解耦,同时也能起到消息缓冲,消息分发的作用._RabbitMQ使用的是AMQP协议,它是一种二进制协议.默认启 ...
- Busybox构建根文件系统和制作Ramdisk
定制根文件系统的方法很多,最常用的是使用BusyBox来构建定制根文件系统.它集成压缩了Linux的许多工具和命令,可以使用户迅速方便地建立一套相对完整.功能丰富的文件系统,其中包括大量常用的应用 ...
- Vue element 分页
Vue单页面,有一个带分页的表格,表格内数据关联页码,套路如下: 代码如下: <div class="c-table-list auth-list m-bottom-20"& ...
- LR 11录制IE起不来
注:LR 11一般使用的是IE8或IE9 1.在录制脚本时Start Recoding中,默认如下,这样有可能IE打不开,需要更改路径,到对应的IE路径再尝试. 2.降低IE版本到IE8或者9 3.I ...
- leetcode 刷题进展
最近没发什么博客了 凑个数 我的leetcode刷题进展 https://gitee.com/def/leetcode_practice 个人以为 刷题在透不在多 前200的吃透了 足以应付非算法岗 ...
- char对比varchar
char对比varchar 相同点:char与varchar都是存储字符串的数据类型 不同点:char是固定长度的字符类型,而varchar是可变长度的字符类型,这个一定要注意.另外进行select时 ...
- Numpy and Matplotlib
Numpy介绍 编辑 一个用python实现的科学计算,包括:1.一个强大的N维数组对象Array:2.比较成熟的(广播)函数库:3.用于整合C/C++和Fortran代码的工具包:4.实用的线性代数 ...
