AIM Tech Round (Div. 2) C. Graph and String
2 seconds
256 megabytes
standard input
standard output
One day student Vasya was sitting on a lecture and mentioned a string s1s2... sn, consisting of letters "a", "b" and "c" that was written on his desk. As the lecture was boring, Vasya decided to complete the picture by composing a graph G with the following properties:
- G has exactly n vertices, numbered from 1 to n.
- For all pairs of vertices i and j, where i ≠ j, there is an edge connecting them if and only if characters si and sj are either equal or neighbouring in the alphabet. That is, letters in pairs "a"-"b" and "b"-"c" are neighbouring, while letters "a"-"c" are not.
Vasya painted the resulting graph near the string and then erased the string. Next day Vasya's friend Petya came to a lecture and found some graph at his desk. He had heard of Vasya's adventure and now he wants to find out whether it could be the original graph G, painted by Vasya. In order to verify this, Petya needs to know whether there exists a string s, such that if Vasya used this s he would produce the given graph G.
The first line of the input contains two integers n and m 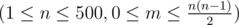 — the number of vertices and edges in the graph found by Petya, respectively.
— the number of vertices and edges in the graph found by Petya, respectively.
Each of the next m lines contains two integers ui and vi (1 ≤ ui, vi ≤ n, ui ≠ vi) — the edges of the graph G. It is guaranteed, that there are no multiple edges, that is any pair of vertexes appear in this list no more than once.
In the first line print "Yes" (without the quotes), if the string s Petya is interested in really exists and "No" (without the quotes) otherwise.
If the string s exists, then print it on the second line of the output. The length of s must be exactly n, it must consist of only letters "a", "b" and "c" only, and the graph built using this string must coincide with G. If there are multiple possible answers, you may print any of them.
2 1
1 2
Yes
aa
4 3
1 2
1 3
1 4
No
In the first sample you are given a graph made of two vertices with an edge between them. So, these vertices can correspond to both the same and adjacent letters. Any of the following strings "aa", "ab", "ba", "bb", "bc", "cb", "cc" meets the graph's conditions.
In the second sample the first vertex is connected to all three other vertices, but these three vertices are not connected with each other. That means that they must correspond to distinct letters that are not adjacent, but that is impossible as there are only two such letters: a and c.
看了半天才看明白题意,可以理解为给n个点涂色(可涂的颜色有a,b,c),相连接的点可以涂aa bb cc ab ba bc cb。
问是否存在可行的涂色方案,有的话 输出。
样例2的话他解释的很清晰了

这么连的话 3 4也得连接。与样例描述不符。
思路:类似于贪心,如果某个点连接了其他n-1个点,那么这个点就被标记为b。然后再找一个没有被标记的点,标记成a.同时与a相连接的点也标记成a。剩下那些没有被标记的点标记成c.然后n^2 检查一遍是否成立。
/* ***********************************************
Author :guanjun
Created Time :2016/2/5 19:01:28
File Name :cfAIMc.cpp
************************************************ */
#include <iostream>
#include <cstring>
#include <cstdlib>
#include <stdio.h>
#include <algorithm>
#include <vector>
#include <queue>
#include <set>
#include <map>
#include <string>
#include <math.h>
#include <stdlib.h>
#include <iomanip>
#include <list>
#include <deque>
#include <stack>
#define ull unsigned long long
#define ll long long
#define mod 90001
#define INF 0x3f3f3f3f
#define maxn 10000+10
#define cle(a) memset(a,0,sizeof(a))
const ull inf = 1LL << ;
const double eps=1e-;
using namespace std; bool cmp(int a,int b){
return a>b;
}
int mark[];
int vis[][];
int cnt[];
int main()
{
#ifndef ONLINE_JUDGE
freopen("in.txt","r",stdin);
#endif
//freopen("out.txt","w",stdout);
int n,m,x,y;
while(cin>>n>>m){
cle(vis);
cle(cnt);
for(int i=;i<=m;i++){
scanf("%d%d",&x,&y);
vis[x][y]=vis[y][x]=;
cnt[x]++;
cnt[y]++;
}
cle(mark);
for(int i=;i<=n;i++){
if(cnt[i]==n-){
mark[i]=;//b
}
}
for(int i=;i<=n;i++){
if(!mark[i]){
mark[i]=;//a
for(int j=;j<=n;j++){
if(mark[j]!=&&vis[i][j])mark[j]=;
}
break;
}
}
for(int i=;i<=n;i++){
if(!mark[i])mark[i]=;//c
}
int flag=;
for(int i=;i<=n;i++){
for(int j=i+;j<=n;j++){
if(vis[i][j]){
//if(!mark[i]||!mark[j])flag=1;
if((mark[i]+mark[j]==)&&(mark[i]!=mark[j]))flag=;
//if(flag)break;
}
else{
if(!mark[i]&&!mark[j])continue;
if(!((mark[i]+mark[j]==)&&(mark[i]!=mark[j])))flag=; }
if(flag)break;
}
if(flag)break;
}
if(flag)puts("No");
else{
puts("Yes");
for(int i=;i<=n;i++){
printf("%c",mark[i]-+'a');
}
}
}
return ;
}
AIM Tech Round (Div. 2) C. Graph and String的更多相关文章
- AIM Tech Round (Div. 2) C. Graph and String 二分图染色
C. Graph and String 题目连接: http://codeforces.com/contest/624/problem/C Description One day student Va ...
- AIM Tech Round (Div. 2) B. Making a String 贪心
B. Making a String 题目连接: http://codeforces.com/contest/624/problem/B Description You are given an al ...
- Codeforces AIM Tech Round (Div. 2)
这是我第一次完整地参加codeforces的比赛! 成绩 news standings中第50. 我觉这个成绩不太好.我前半小时就过了前三题,但后面的两题不难,却乱搞了1.5h都没有什么结果,然后在等 ...
- AIM Tech Round (Div. 1) D. Birthday 数学 暴力
D. Birthday 题目连接: http://www.codeforces.com/contest/623/problem/D Description A MIPT student named M ...
- AIM Tech Round (Div. 2) D. Array GCD dp
D. Array GCD 题目连接: http://codeforces.com/contest/624/problem/D Description You are given array ai of ...
- AIM Tech Round (Div. 2) A. Save Luke 水题
A. Save Luke 题目连接: http://codeforces.com/contest/624/problem/A Description Luke Skywalker got locked ...
- AIM Tech Round (Div. 2) B
B. Making a String time limit per test 1 second memory limit per test 256 megabytes input standard i ...
- AIM Tech Round (Div. 2) A
A. Save Luke time limit per test 1 second memory limit per test 256 megabytes input standard input o ...
- AIM Tech Round (Div. 1) C. Electric Charges 二分
C. Electric Charges 题目连接: http://www.codeforces.com/contest/623/problem/C Description Programmer Sas ...
随机推荐
- 【线段树查询区间最值】poj 3264 Balanced Lineup
#include<cstdio> #include<algorithm> using namespace std; ; struct Seg { int l,r,mi,ma; ...
- 【2018.9.26】K-D Tree详解
网上对K-D-Tree的讲解不尽清晰,我学了很久都不会写,这里新开一文做一些讲解. 1.K-D-Tree是什么? K-DTree 即 K-Dimensional-Tree,常用来作空间划分及近邻搜索, ...
- UVa10234 Race
递推,设有i个人排在第一名,剩下的人排在后面,方案有f[i]种,则f[i]=sum(c[n][i]*f[n-i]) 1<=i<=n /*by SilverN*/ #include<a ...
- msp430入门学习40
msp430的其他八 msp430入门学习
- Java Socket应用
Java Socket(套接字)通常也称作"套接字",用于描述IP地址和端口,是一个通信链的句柄.应用程序通常通过"套接字"向网络发出请求或者应答网络请求.
- 虽然今天angular5发布了,但我还是吧这篇angularjs(1)+webpack的文章发出来吧哈哈哈
本文为原创,转载请注明出处: cnzt 文章:cnzt-p http://www.cnblogs.com/zt-blog/p/7779384.html 写在前面: 因为最近总结自己之前做过 ...
- 【Todo】UDP P2P打洞原理
参考以下两篇文章: https://my.oschina.net/ososchina/blog/369206 http://m.blog.csdn.net/article/details?id=666 ...
- RecyclerView的万能切割线
效果图: 用法: 加入默认切割线:高度为2px.颜色为灰色 mRecyclerView.addItemDecoration(new RecycleViewDivider(mContext, Linea ...
- linux的主分区与逻辑分区的关系
主分区和扩展分区的差别在于主分区位于硬盘的最開始.MBR 扇区的位置.这个位置的数据在计算机启动时.会自己主动被 BIOS 读取而且运行,也就是说这个位置的分区表会自己主动被 BIOS 读取到内 ...
- react 使用 moment 进行 日期格式化
在react中使用得先导入: import moment from 'moment'; 调用: npm install moment var moment = require('moment'); m ...
