Internet Secure
key
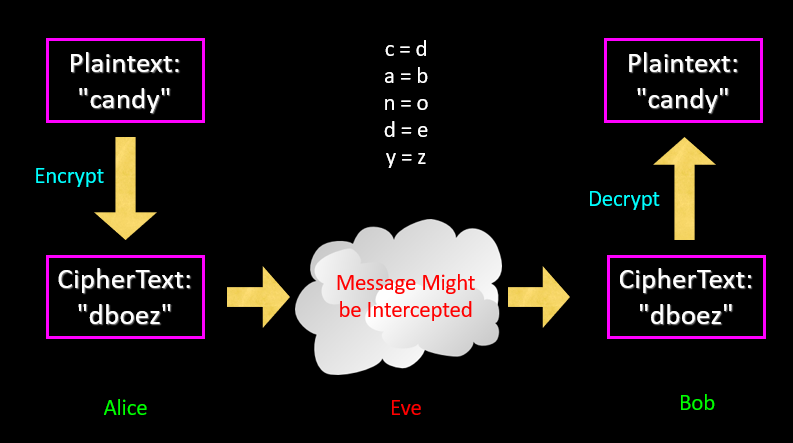
- Secret key(密钥):ues the same key to Encryption and decryption(symmetric-key)对称加密,需要绝对安全的空间来传递key
- Pulic kay(公钥):ues different key to Encryption and decryption (asymmetric-key)非对称加密
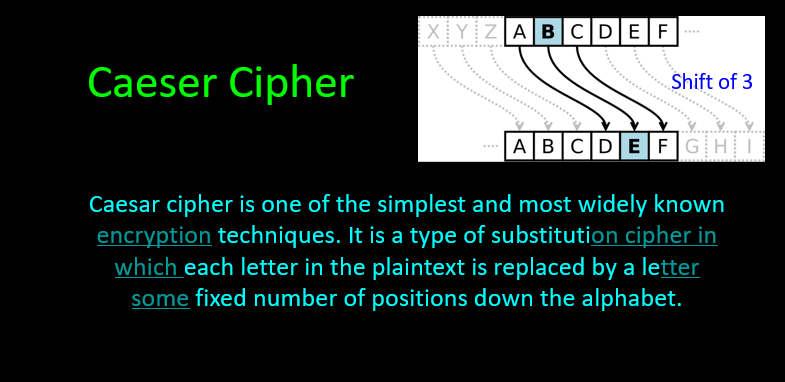
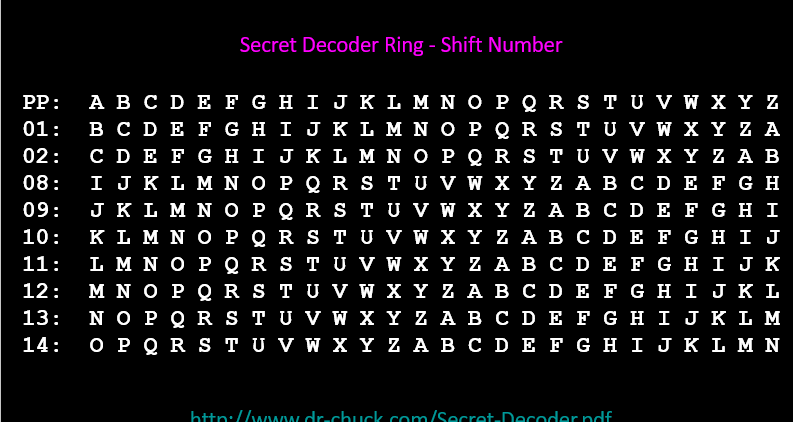
Caeser Cipher(凯撒密码)
- core:replace(替换思想)
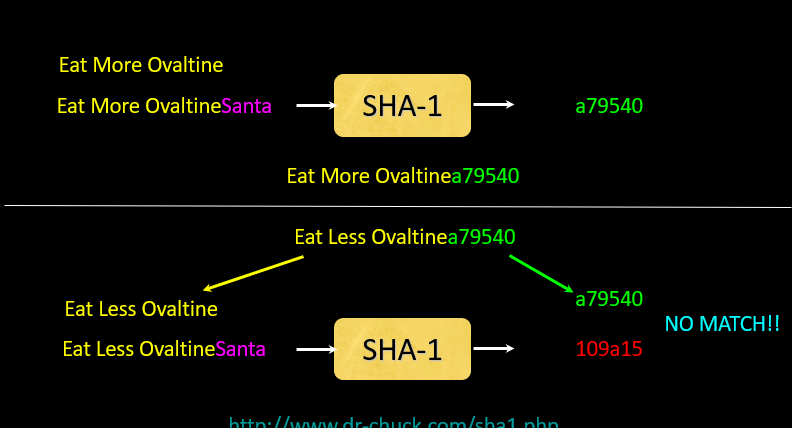
Cryptographic Hash(又是可爱的哈希)
- Converting any length of input into a fixed length string or digest of information(任意长度输入转化为固定长度二进制串)
- 哈希碰撞:Different inputs give the same result
- a good hash function:any tiny change --> a big change with digest

Hash for Password(使用哈希的密码系统)
- Do not store the password you entered directly(非直接存密码)
- store digest(存储哈希值)
- 几乎是不可逆

- share secret(共享密码)
在信息后面加上特定字符串,再哈希
Public Key Encryption Confidentiality
- base on two prime(从两个素数开始)
- Public key:Open to the outside world for encryption(公钥)
- Private key: Used for decryption, private ownership(私钥)
- not perfect but it is hard to break
- Public keys can be distributed arbitrarily without protection(公钥分发简单)
- private keys are protected in computers or servers.
SSL(Secure Sockets Layer)安全套接字层
- Security for TCP
- Located between Application Layer and Transport Layer
- Because of the hierarchical structure, the underlying structure only needs to be responsible for the transmission of ciphertext (it is not known whether the transmission is ciphertext or plaintext).

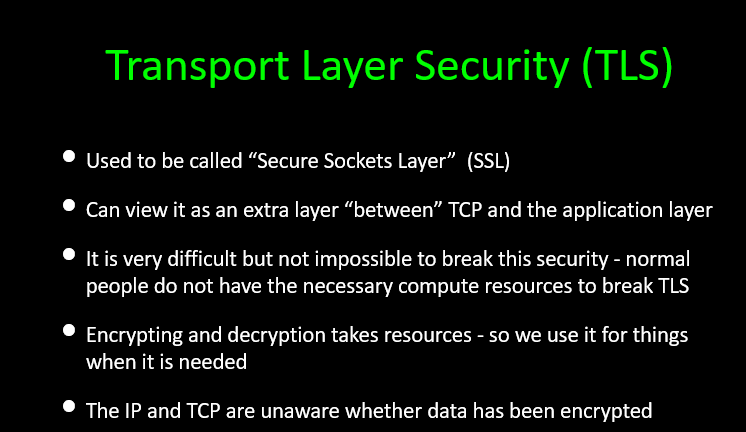
TLS(Transpot Layer Security)
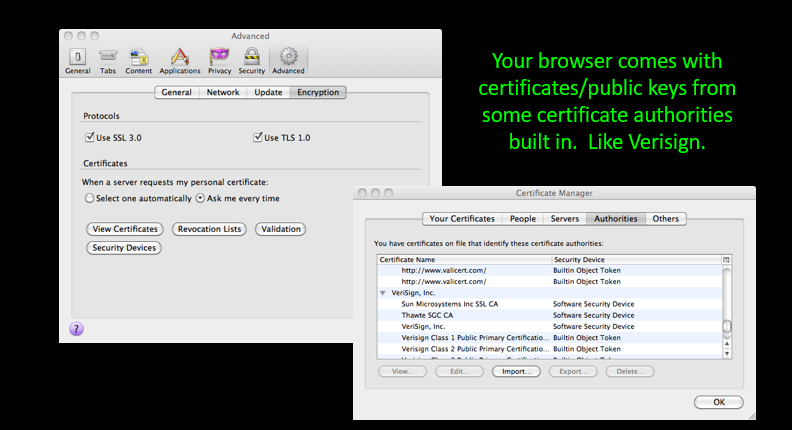
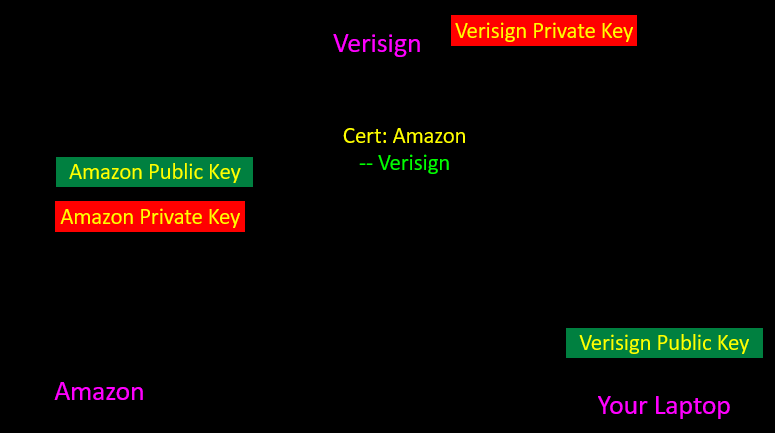
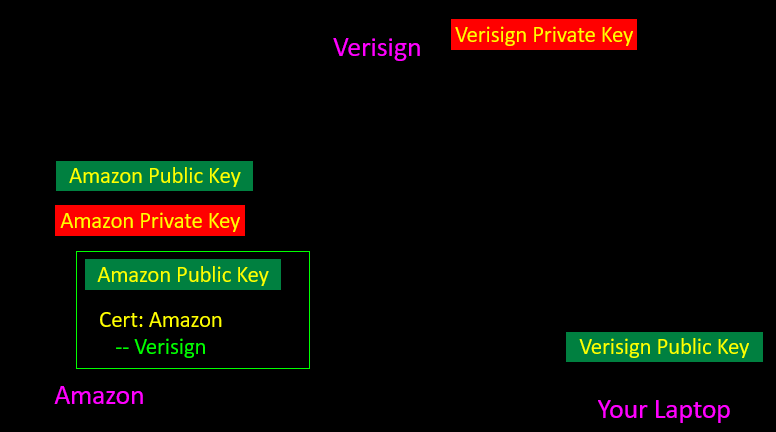
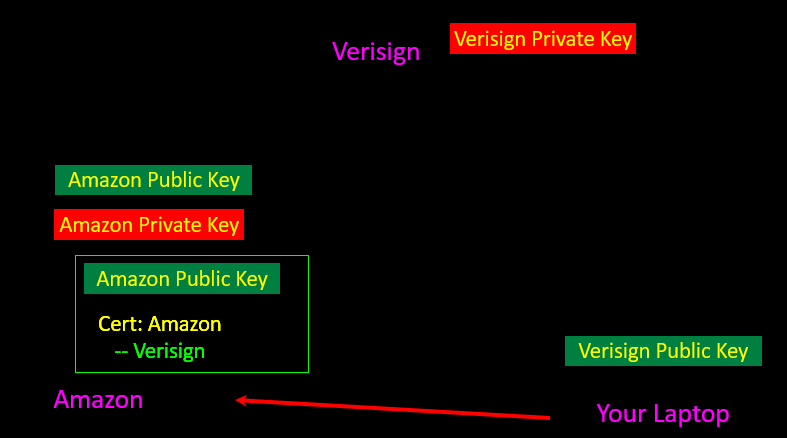
Digital Certificates(数字证书)
- Make sure the person you are talking to(确保谈话对象)
- Amazon发公钥给VerSign,VerSign计算验证后,确实是Amazon,就返回一个带签名的公钥

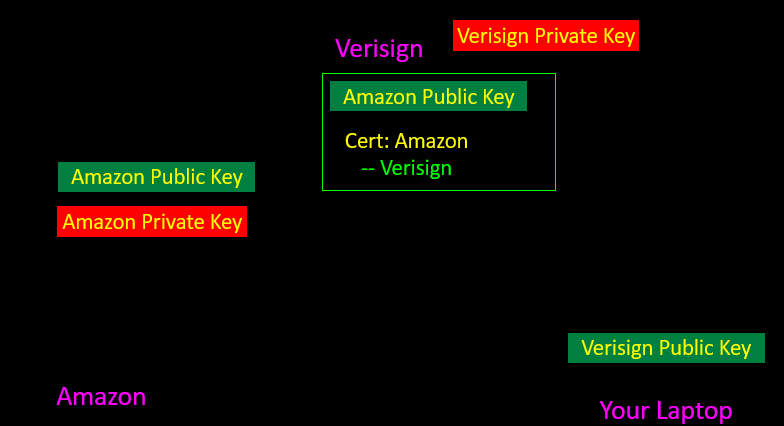
Summary

Internet Secure的更多相关文章
- Internet History,Tecchnology and Security
Internet History Internet Technologe Internet Secure
- Internet protocol security (ipsec) packet processing for multiple clients sharing a single network address
Embodiments of the present invention address deficiencies of the art in respect to secure communicat ...
- Understanding and Managing SMTP Virtual Servers
Simple Mail Transfer Protocol (SMTP) Service Overview The Simple Mail Transfer Protocol (SMTP) servi ...
- [UVa1057] Routing
问题描述 As more and more transactions between companies and people are being carried out electronically ...
- Coursera-Note: Internet History, Technology and Secure (1st week to 9th week)
目录 Coursera-Note: Internet History, Technology and Secure 第一周 第二周 数据交换: Packet switching技术: 第三周 创造ht ...
- Critical: Update Your Windows Secure Channel (cve-2014-6321,MS14-066)
前言:风雨欲来山满楼,下半年开始各种凶猛的漏洞层出不穷,天下已经不太平,互联网已经进入一个新的台阶 0x01 cve-2014-6321 11月的补丁月,微软请windows的用户吃了顿大餐,发布了1 ...
- Problem with "AnyConnect was not able to establish connection to the specified secure gateway."
Cisco的VPN客户端最近报"AnyConnect was not able to establish connection to the specified secure gateway ...
- HTTPS (HTTP Secure)
what is HTTPS HTTPS = HTTP + TSL Hypertext Transfer Protocol Secure (HTTPS) is acommunications proto ...
- What is XMLHTTP? How to use security zones in Internet Explorer
Types of Security Zones Internet Zone This zone contains Web sites that are not on your computer or ...
随机推荐
- Kafka 推荐网站
Kafka系列文章 [Kafka设计解析(一)- Kafka背景及架构介绍](http://www.jasongj.com/2015/03/10/KafkaColumn1/) [Kafka设计解析(二 ...
- 在tornado中使用异步mysql操作
在使用tornado框架进行开发的过程中,发现tornado的mysql数据库操作并不是一步的,造成了所有用户行为的堵塞.tornado本身是一个异步的框架,要求所有的操作都应该是异步的,但是数据库这 ...
- C# Server.MapPath的使用方法
(1)WebForm中: HttpContext.Current.Server.MapPath("~/Files/car/"); (2)Mvc中: Server.MapPath() ...
- 用 wait-notify 解决生产者-消费者问题
//生产者 package com.mzj.test; import java.util.Vector; import java.util.logging.Level; import java.uti ...
- 嵌入式C语言自我修养 01:Linux 内核中的GNU C语言语法扩展
1.1 Linux 内核驱动中的奇怪语法 大家在看一些 GNU 开源软件,或者阅读 Linux 内核.驱动源码时会发现,在 Linux 内核源码中,有大量的 C 程序看起来“怪怪的”.说它是C语言吧, ...
- 推荐软件7 taskbar numberer,结果get了WIN相关的快捷键
作为键盘控,Win+数字直达任务栏上的应用已经让我欣喜.接下来我的问题就是每次要数数字才能确定是哪个数字,期间我尝试过按常用顺序进行排序并尝试记住它们.直到我想也许应该有个软件可以在任务栏图标处贴上一 ...
- vs2013工程配置
1. 目标文件生成路径配置: 直接改在工程同级目录下 x64\debug目录下: 2. 调试工程路径配置: 命令-----参照物为工程 工作目录----参照物为运行程序 3. 拷贝工程: bat的写 ...
- Fibonacci递归以及数组实现
说起Fibonacci数列,首先想到的就是递归算法了,这也是帮助理解递归算法比较经典的题目实现如下: public static int Fibonacci(int n){ if (n == 0 ...
- 使用ChipScope Pro调试硬件
chipscope_icon提供与其他ChipScope内核的通信 chipscope_opb_iba促进传统片上外设总线(OPB)事务的监控 chipscope_plb_iba便于监控处理器本地总线 ...
- 20154327 Exp4 恶意代码分析
基础问题回答 (1)如果在工作中怀疑一台主机上有恶意代码,但只是猜想,所有想监控下系统一天天的到底在干些什么.请设计下你想监控的操作有哪些,用什么方法来监控. 监控网络连接 监控是否创建新的进程 监控 ...
