Web缓存欺骗
class, css, jar, js, jpg, jpeg, gif, ico, png, bmp, pict, csv, doc, docx, xls, xlsx, ps, pdf,
pls, ppt, pptx, tif, tiff, ttf, otf, webp, woff, woff2, svg, svgz, eot, eps, ejs, swf, torrent,
midi, mid
存在漏洞的地址:http://www.xx.com/cc.css位于cdn缓存上,但是访问该css同http://www.xx.com/home.php一样,所以造成了该漏洞
漏洞利用:将http://www.xx.com/cc.css地址发给笑脸用户,用户在上面的操作会留在cdn缓存上,造成了泄漏,这个时候,恶意攻击者访问该用户就造成了,缓存欺骗。
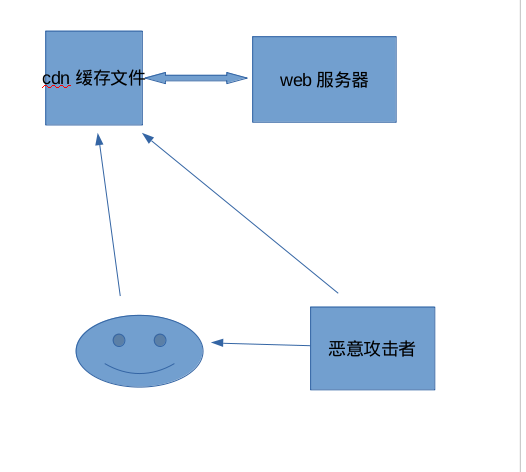
以下为hackone案例,仅供参考,顺便提下,案例二的poc可以进行证明漏洞
Jun 2nd (8 months ago)
I have found a Vulnerability in vanilla forums which called Web cache deception attack.
Web Cache Deception Attack
Websites often tend to use web cache functionality to store files that are often retrieved, to reduce latency from the web server.
Websites often tend to use web cache functionality (for example over a CDN, a load balancer, or simply a reverse proxy). The purpose is simple: store files that are often retrieved, to reduce latency from the web server.
When accessing a URL like http://www.example.com/home.php/non-existent.css
A GET request to that URL will be produced by the browser. The server returns the content of http://www.example.com/home.php. And yes, the URL remains http://www.example.com/home.php/non-existent.css. The HTTP headers will be the same as for accessing http://www.example.com/home.php directly: same caching headers and same content type (text/html, in this case).
The web cache servre saves the returned page in the server's cache. Then the attacker can go to the url: http://www.example.com/home.php/non-existent.css and the page of the victim will be presented with the victim's sensitive information (The page content).
The dangerous part in this attack, unlike phishing attacks, is that the url isn't looks suspicious at all. It looks like a normal url from the original website, so the victim thinks that it is ok to click on the link.
Steps:
- The attacker sends the following link to the victim: https://open.vanillaforums.com/messages/all/non-existent.css
- The victim opens the link and the inbox page will be loaded normally. (The web cache server then saves this page)
- The attacker open the same link (https://open.vanillaforums.com/messages/all/non-existent.css), and the inbox page of the victim with all his private contant is loaded.
If you need a video to understand it better, ask me and I will send you one.
Impact
The attacker can achieve all the private content of a specific victim, without the victim knowing about it.
二:
Hello,
Your Web-Server is vulnerable to web cache poisoning attacks.
This means, that the attacker are able to get another user informations.
If you are logged in and visit this website (For example):
https://postmates.com/SomeRandomText.css
Then the server will store the information in the cache, BUT with the logged in user information :)
A non-logged-in user can then visit this website and see the information contained therein.
In that case, this url: https://postmates.com/SomeRandomText.css
I have written a small javascript / html code, which executes this attack fully automated, you just need to visit the website and wait like 3 seconds.
Here is the small PoC code
<html>
<head>
</head>
<body>
<script>
var cachedUrl = 'https://postmates.com/' + generateId() + '.css';
const popup = window.open(cachedUrl);
function generateId() {
var content = '';
const alphaWithNumber = 'QWERTZUIOPASDFGHJUKLYXCVBNM1234567890';
for (var i = 0; i < 10; i++) {
content += alphaWithNumber.charAt(Math.floor(Math.random() * alphaWithNumber.length))
}
return content;
}
var checker = setInterval(function() {
if (popup.closed) {
clearInterval(checker);
}
}, 200);
var closer = setInterval(function() {
popup.close();
document.body.innerHTML = 'Victims content is now cached <a href="' + cachedUrl + '">here and the url can be saved on the hackers server</a><br><b>Full Url: ' + cachedUrl + '</b>';
clearInterval(closer);
}, 3000);
</script>
</body>
</html>
Theoretically, the attacker could then store this information on his server, but in this example, the URL is simply shown.
I would suggest keeping an eye on caching for more security and hope you enjoyed my report.
Some informations about the attack:
https://www.blackhat.com/docs/us-17/wednesday/us-17-Gil-Web-Cache-Deception-Attack.pdf
The screenshots with the steps are in the attachments
Not important for this report, but i want to look deeper in your website: Can you create an account for me? Im from Germany and dont have american phone number :)
Impact
Web cache poisoning attack can be used to steal user informations like lastname and member id which is important for the login security feature. (For example)
Web缓存欺骗的更多相关文章
- 【转】一种新型的Web缓存欺骗攻击技术
为了减少WEB响应时延并减小WEB服务器负担,现在WEB缓存技术已经用的非常普遍了,除了专门的CDN,负载均衡以及反向代理现在也会缓存一部分的网页内容.这里我要介绍一种WEB缓存欺骗攻击技术,这种攻击 ...
- 作为前端应当了解的Web缓存知识
缓存优点 通常所说的Web缓存指的是可以自动保存常见http请求副本的http设备.对于前端开发者来说,浏览器充当了重要角色.除此外常见的还有各种各样的代理服务器也可以做缓存.当Web请求到达缓存时, ...
- Web缓存杂谈
一.概述 缓存通俗点,就是将已经得到的‘东东’存放在一个相对于自己而言,尽可能近的地方,以便下次需要时,不会再二笔地跑到起始点(很远的地方)去获取,而是就近解决,从而缩短时间和节约金钱(坐车要钱嘛). ...
- 前端应当了解的Web缓存知识
缓存优点 通常所说的Web缓存指的是可以自动保存常见http请求副本的http设备.对于前端开发者来说,浏览器充当了重要角色.除此外常见的还有各种各样的代理服务器也可以做缓存.当Web请求到达缓存时, ...
- 浅谈Web缓存
在前端开发中性能一直都是被大家所重视的一点,然后判断一个网站的性能最直观的就是看网页打开的速度. 其中提高网页反应的速度的一个方式就是使用缓存.一个优秀的缓存策略可以缩短网页请求资源的距离,减少延迟, ...
- web缓存
web缓存HTTP协议的一个核心特性,它能最小化网络流量,并且提升用户所感知的整个系统响应速度. 什么能被缓存? *Logo和商标图像 *普通的不变化的图像(例如,导航图标) *CSS样式表 *普通的 ...
- Web 技术人员需知的 Web 缓存知识(转)
最近的译文距今已有4年之久,原文有一定的更新.今天踩着前辈们的肩膀,再次把这篇文章翻译整理下.一来让自己对web缓存的理解更深刻些,二来让大家注意力稍稍转移下,不要整天HTML5, 面试题啊叨啊叨的~ ...
- c# web 缓存管理
using System; using System.Collections; using System.Text.RegularExpressions; using System.Web; usin ...
- HTML5时代的Web缓存机制
HTML5 之离线应用Manifest 我们知道,使用传统的技术,就算是对站点的资源都实施了比较好的缓存策略,但是在断网的情况下,是无法访问的,因为入口的HTML页面我们一般运维的考虑,不会对其进行缓 ...
随机推荐
- 王颖奇 20171010129《面向对象程序设计(java)》第十四周学习总结
实验十四 Swing图形界面组件 理论知识知识点: 1.Swing和MVC设计模式2.布局管理器3.文本输入4.选择组件5.菜单6.对话框 实验时间 2018-11-29 1.实验目的与要求 (1) ...
- 用VirtualBox代替VMWare安装Ubuntu系统图文教程总结
文章目录 为什么使用VirtualBox,而不是VMWare? 图文教程 安装VirtualBox 下载Ubuntu镜像 新建虚拟机 安装Ubuntu系统 总结 为什么使用VirtualBox,而不是 ...
- 栈溢出(Stack Overflow)
调用栈(Call Stack)描述的时函数之间的调用关系.它由多个栈帧(Stack Frame)组成,每个栈帧对应着一个未运行完的函数.栈帧中保存了该函数的返回地址和局部变量,因而不能再执行完毕后找到 ...
- 导出jar包和api文档
导出jar包过程 右击项目名称->export 选择java->JAR file next->选择路径 导出成功 生成api文档 选择doc->右键export java-&g ...
- [hihoCoder1231 2015BeijingOnline]求圆与多边形公共部分的周长
题意:如题 思路:离散.将所有交点求出来,相当于将多变形的边切成了很多条元边,对每条元边,有两种情况 在圆内,答案加上此边长 在圆外,答案加上此边相对于圆心的"有向转弧" #inc ...
- Python单元测试框架:pytest
(一)介绍 pytest是一个非常成熟的全功能的Python测试框架,主要特点有以下几点: 1.简单灵活,容易上手: 2.支持参数化: 3.能够支持简单的单元测试和复杂的功能测试,还可以用来做sele ...
- java 版本比较
public class version { public static int compareVersion(String version1, String version2) throws Exc ...
- Nginx 、MySQL、Django 在 Docker-compose 中的部署
概述 本文主要记录了在 Linux 3.10.0-1062.el7.x86_64 下使用 docker-compose 搭建服务的过程,由于公司服务器在内网中,搭建镜像及下载依赖时需要外部代理,如果本 ...
- scrapy五大核心组件
scrapy五大核心组件 引擎(Scrapy)用来处理整个系统的数据流处理, 触发事务(框架核心) 调度器(Scheduler)用来接受引擎发过来的请求, 压入队列中, 并在引擎再次请求的时候返回. ...
- 4.4 Go goto continue break
4.4 Go goto continue break Go语言的goto语句可以无条件的跳转到指定的代码行执行. goto语句一般与条件语句结合,实现条件转义,跳出循环体等. Go程序不推荐使用got ...
