DASCTF X CBCTF 2023|无畏者先行 CRYPTO—WP
EzRSA
1、题目信息
from Crypto.Util.number import *
import random
from gmpy2 import *
from libnum import *
from flag import flag
def padding(f):
random_chars = bytes([random.randint(0, 255) for _ in range(32)])
f = f + random_chars
return f
def guess_p(p):
e = 65537
P = p
n1 = getPrime(512)*getPrime(512)
with open('enc.txt', 'w+') as f:
while jacobi(2,n1) == 1:
n1 = getPrime(512)*getPrime(512)
while P:
pad = random.randint(0, 2**2023)**2
message = pad << 1 + P % 2
cipher = pow(message, e, n1)
f.write(str(cipher)+'n')
P //= 2
print("n1 = "+ str(n1) )
def guess_q(q):
def encrypt(q, n):
e = random.randint(1000,2000)
noise = random.randint(0, n - 1)
c = pow(q+noise,e,n)
return e, noise,c
n2 = getPrime(512)*getPrime(512)
e1, noise1, c1 = encrypt(q, n2)
e2, noise2, c2 = encrypt(q, n2)
print("n2 = "+ str(n2) )
print('(e1, noise1, c1) =', (e1,noise1,c1))
print('(e2, noise2, c2) =', (e2,noise2,c2))
p = getPrime(512)
q = getPrime(512)
n = p*q
guess_p(p)
guess_q(q)
e = 0x10001
flag = padding(flag)
m = bytes_to_long(flag)
c = pow(m,e,n)
print("c = " + str(c))
'''
n1 = 65634094430927080732256164808833233563732628654160389042977689628512527168256899310662239009610512772020503283842588142453533499954947692968978190310627721338357432052800695091789711809256924541784954080619073213358228083200846540676931341013554634493581962527475555869292091755676130810562421465063412235309
n2 = 103670293685965841863872863719573676572683187403862749665555450164387906552249974071743238931253290278574192713467491802940810851806104430306195931179902098180199167945649526235613636163362672777298968943319216325949503045377100235181706964846408396946496139224344270391027205106691880999410424150216806861393
(e1, noise1, c1) = (1743, 44560588075773853612820227436439937514195680734214431948441190347878274184937952381785302837541202705212687700521129385632776241537669208088777729355349833215443048466316517110778502508209433792603420158786772339233397583637570006255153020675167597396958251208681121668808253767520416175569161674463861719776, 65643009354198075182587766550521107063140340983433852821580802983736094225036497335607400197479623208915379722646955329855681601551282788854644359967909570360251550766970054185510197999091645907461580987639650262519866292285164258262387411847857812391136042309550813795587776534035784065962779853621152905983)
(e2, noise2, c2) = (1325, 35282006599813744140721262875292395887558561517759721467291789696459426702600397172655624765281531167221787036009507833425145071265739486735993631460189629709591456017092661028839951392247601628468621576100035700437892164435424035004463142959219067199451575338270613300215815894328788753564798153516122567683, 50327632090778183759544755226710110702046850880299488259739672542025916422119065179822210884622225945376465802069464782311211031263046593145733701591371950349735709553105217501410716570601397725812709771348772095131473415552527749452347866778401205442409443726952960806789526845194216490544108773715759733714)
c = 124349762993424531697403299350944207725577290992189948388824124986066269514204313888980321088629462472088631052329128042837153718129149149661961926557818023704330462282009415874674794190206220980118413541269327644472633791532767765585035518183177197863522573410860341245613331398610013697803459403446614221369
'''题目分析:
看到jacobi(2,n1)知道是二次剩余的知识
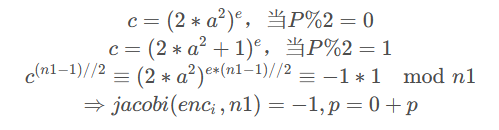
相关消息攻击直接解
exp
import binascii
import libnum
from gmpy2 import *
from Crypto.Util.number import *
n1 = 65634094430927080732256164808833233563732628654160389042977689628512527168256899310662239009610512772020503283842588142453533499954947692968978190310627721338357432052800695091789711809256924541784954080619073213358228083200846540676931341013554634493581962527475555869292091755676130810562421465063412235309
(e1, noise1, c1) = (1743, 44560588075773853612820227436439937514195680734214431948441190347878274184937952381785302837541202705212687700521129385632776241537669208088777729355349833215443048466316517110778502508209433792603420158786772339233397583637570006255153020675167597396958251208681121668808253767520416175569161674463861719776, 65643009354198075182587766550521107063140340983433852821580802983736094225036497335607400197479623208915379722646955329855681601551282788854644359967909570360251550766970054185510197999091645907461580987639650262519866292285164258262387411847857812391136042309550813795587776534035784065962779853621152905983)
(e2, noise2, c2) = (1325, 35282006599813744140721262875292395887558561517759721467291789696459426702600397172655624765281531167221787036009507833425145071265739486735993631460189629709591456017092661028839951392247601628468621576100035700437892164435424035004463142959219067199451575338270613300215815894328788753564798153516122567683, 50327632090778183759544755226710110702046850880299488259739672542025916422119065179822210884622225945376465802069464782311211031263046593145733701591371950349735709553105217501410716570601397725812709771348772095131473415552527749452347866778401205442409443726952960806789526845194216490544108773715759733714)
c = 124349762993424531697403299350944207725577290992189948388824124986066269514204313888980321088629462472088631052329128042837153718129149149661961926557818023704330462282009415874674794190206220980118413541269327644472633791532767765585035518183177197863522573410860341245613331398610013697803459403446614221369
n2 = 103670293685965841863872863719573676572683187403862749665555450164387906552249974071743238931253290278574192713467491802940810851806104430306195931179902098180199167945649526235613636163362672777298968943319216325949503045377100235181706964846408396946496139224344270391027205106691880999410424150216806861393
ciphers = []
with open('enc.txt') as f:
for line in f.read().split('n'):
if line.strip():
ciphers.append(int(line.strip()))
p = ''
for i in ciphers:
if jacobi(i,n1) == -1:
p = '0' + p
else:
p = '1' + p
p = int(p,2)
def franklinReiter(n,e1,e2,c1,c2,noise1,noise2):
PR.<x> = PolynomialRing(Zmod(n))
g1 = (x + noise1)^e1 - c1
g2 = (x + noise2)^e2 - c2
def gcd(g1, g2):
while g2:
g1, g2 = g2, g1 % g2
return g1.monic() #
return -gcd(g1, g2)[0]
q=franklinReiter(n2,e1,e2,c1,c2,noise1,noise2)
q = 13189337905641321257372188436353844418280745284875462357019668708167547026960641869513283218672677712590326347601424108528959315675307896082223561007980457
p = 9473204278465588641589315677772678997836862033858760337441231265335880892205102590571357305720744128962068300763212493598006400853597404586755248901932203
e = 0x10001
phi = (p - 1) * (q - 1)
d = inverse(e,phi)
print(long_to_bytes(int(pow(c,d,p * q))))
# DASCTF{W05-y03r_m2st1r-j2c0b1_2nd_p01yn0mi2l!}剩下的题目难度大,直接看官方WP吧
https://test-cuycc6s9lprw.feishu.cn/docx/T7budbiSWoTNd4xQGVicHL1Vnpf
DASCTF X CBCTF 2023|无畏者先行 CRYPTO—WP的更多相关文章
- bugku crypto wp上半部分汇总
1.滴答~滴 摩斯码,在线解开. 2. 栅栏密码,在线解就出flag了. 3. Ook解密,由.?!Ook组成密文,在线网站解密 4.这不是摩斯密码 有点像jsfuck,发现又不是,因为不会出现大于号 ...
- BUUCTF Crypto
BUUCTF 几道crypto WP [AFCTF2018]Morse 简单的莫尔斯密码,最直观的莫尔斯密码是直接采用空格分割的点和划线,这题稍微绕了一下使用的是斜杠来划分 所以首先将斜杠全部替换为空 ...
- 2021羊城杯比赛复现(Crypto)
bigrsa 题目: from Crypto.Util.number import * from flag import * n1 = 10383529640908175186077053551474 ...
- 周练7(ssti)
{7*7} ->49 -> smarty {{7*'7'}} -> 49 -> twig {{7*'7'}} -> 7777777 -> jinjia2 1. [B ...
- BUUCTF Crypto_WP(2)
BUUCTF Crypto WP 几道密码学wp [GXYCTF2019]CheckIn 知识点:Base64,rot47 下载文件后,发现一个txt文件,打开发现一串base64,界面之后出现一串乱 ...
- 2021江西省赛赛后总结(Crypto)
美国大选 程序: from Crypto.Util.number import * from secret import p,q def gcd(a, b): while b: a, b = b, a ...
- 躬身入局,干货分享,2023年春招后端技术岗(Python)面试实战教程,Offer今始为君发
早春二月,研发倍忙,杂花生树,群鸥竟飞.为什么?因为春季招聘,无论是应届生,还是职场老鸟,都在摩拳擦掌,秣马厉兵,准备在面试场上一较身手,既分高下,也决Offer,本次我们打响春招第一炮,躬身入局,让 ...
- 移动先行之谁主沉浮? 带着你的Net飞奔吧!
移动系源码:https://github.com/dunitian/Windows10 移动系文档:https://github.com/dunitian/LoTDotNet/tree/master/ ...
- 04.移动先行之谁主沉浮----XAML的探索
如果移动方向有任何问题请参考===> 异常处理汇总-移动系列(点) 移动先行之谁主沉浮? 带着你的Net飞奔吧! 链接======>(点) XMAL引入 XAML 类似于 HTML,是一种 ...
- Entity Framework 数据库先行、模型先行、代码先行
数据库先行(Database First):基于已存在的数据库,利用某些工具(如Vs提供的EF设计器)创建实体类,数据库对象与实体类的匹配关系等,你也可以手动修改这些自动生成的代码及匹配文件. 模型先 ...
随机推荐
- ElasticSearch之Close index API
关闭指定的索引. 索引关闭之后: 停止对读.写操作的响应. 停止检索操作的响应. 在索引关闭前,允许执行的操作,关闭之后均不允许执行. ElasticSearch取消对索引的相关维护操作,包含内存中的 ...
- 隐匿自己的c2服务器(一)
隐匿自己的c2服务器(一) 目录 隐匿自己的c2服务器(一) 服务器设置 安装java环境 启动设置 开启禁ping 微信机器人推送上线信息 ️端口特征修改 证书特征修改 流量特征修改 利用cdn加 ...
- C#开源的一款友好的.NET SDK管理器
前言 今天推荐一款由C#开源的.友好的.NET SDK管理器:Dots. 工具介绍 Dots 是一款 .NET SDK 管理器,可让您轻松安装.卸载和切换 .NET SDK.它是一款跨平台工具,可在 ...
- ubuntu中vim乱码以及执行shell脚本时出现乱码
vim打开文件中文出现乱码情况,可以参考如下办法: 在vim /usr/share/vim/vimrc文件末尾中加入 (这个vimrc文件是Vim 的系统级配置文件.文档.插件.语法高亮定义.颜色方案 ...
- const 方法可以改变(智能)指针成员指向的对象
<C++ Primer 5th> P406 const 方法,不能修改指针本身,但是可以修改指针指向的对象! class Foo { public: Foo() : c(new int() ...
- SignalR:React + ASP.NET Core Api
一. 后台WebApi配置: 注:Vision为业务名称,以此为例,可随意修改 1. 安装包:Microsoft.AspNetCore.SignalR 2. 注入 Startup.cs Configu ...
- GaussDB技术解读系列之应用无损透明(ALT)
本文作者 :华为云GaussDB研发高级工程师 藏琦 1.背景 GaussDB作为一款企业级分布式数据库,提供了"同城跨AZ双活.两地三中心.双集群强一致"等极致的高可用容灾能力. ...
- 聊聊LiteOS中生成的Bin、HEX、ELF三种文件格式
摘要:我们在使用编译器在编译工程后会要求生成可执行文件,将这些文件烧录到MCU进行运行,达到我们测试和使用程序的目的,再使用工具链进行编译的时候往往生成.bin..hex ..elf ..alf等文件 ...
- KubeEdge发布云原生边缘计算威胁模型及安全防护技术白皮书
摘要:本文将基于KubeEdge项目详细分析云原生边缘计算业务过程的威胁模型并给出对应的安全加固建议. 本文分享自华为云社区<KubeEdge发布云原生边缘计算威胁模型及安全防护技术白皮书> ...
- 从java到JavaScript(2):对比Java/Go/Swift/Rust看Dart
Dart与Java的一些直观区别 Dart和java以及C#都差不多,基本上不用学习可以直接使用,从这里可以你可以了解Dart有些特别之处.其实对于Java开发人员来说Dart,还是相对好理解的 基本 ...
