[转帖]IOC Security: Indicators of Attack vs. Indicators of Compromise
IOC Security: Indicators of Attack vs. Indicators of Compromise
https://www.crowdstrike.com/blog/indicators-attack-vs-indicators-compromise/
- December 9, 2014
- Jessica DeCianno
- Endpoint Protection
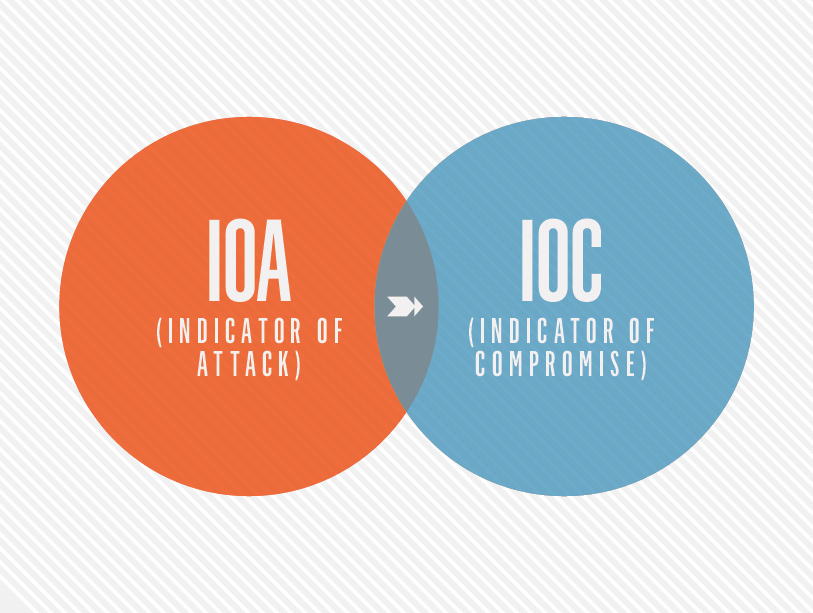
What is an Indicator of Compromise (IOC)?
First we should provide a definition of an indicator of compromise (IOC). An IOC is often described in the forensics world as evidence on a computer that indicates that the security of the network has been breached. Investigators usually gather this data after being informed of a suspicious incident, on a scheduled basis, or after the discovery of unusual call-outs from the network. Ideally, this information is gathered to create “smarter” tools that can detect and quarantine suspicious files in the future.
In the Cyber world, an IOC is an MD5 hash, a C2 domain or hardcoded IP address, a registry key, filename, etc. These IOCs are constantly changing making a proactive approach to securing the enterprise impossible. Because IOCs provide a reactive method of tracking the bad guys, when you find an IOC, there is a high probability that you have already been compromised.
What is an Indicator of Attack (IOA)?
Unlike Indicators of Compromise (IOCs) used by legacy endpoint detection solutions, indicators of attack (IOA) focus on detecting the intent of what an attacker is trying to accomplish, regardless of the malware or exploit used in an attack. Just like AV signatures, an IOC-based detection approach cannot detect the increasing threats from malware-free intrusions and zero-day exploits. As a result, next-generation security solutions are moving to an IOA-based approach pioneered by CrowdStrike.
Indicator of Attack – Physical World
One way to focus our discussion around Indicators of Attack (IOA’s) is to provide an example of how a criminal would plan and undertake to rob a bank in the physical world.
A smart thief would begin by “casing” the bank, performing reconnaissance and understanding any defensive vulnerabilities. Once he determines the best time and tactics to strike, he proceeds to enter the bank. The robber disables the security system, moves toward the vault, and attempts to crack the combination. If he succeeds, he pinches the loot, makes an uneventful getaway and completes the mission. IOA’s are a series of behaviors a bank robber must exhibit to succeed at achieving his objective. He has to drive around the bank (identifying the target), park, and enter the building before he can enter the vault. If he doesn’t disable the security system, it will alarm when he enters the vault and takes the money.
Of course, activities like driving around the bank, parking and entering the bank do not, on their own, indicate an attack is imminent. Moreover, opening a bank vault and withdrawing cash is not necessarily an IOA… if the individual is authorized to access the vault. Specific combinations of activity trigger IOA’s.
Indicator of Attack – Cyber World
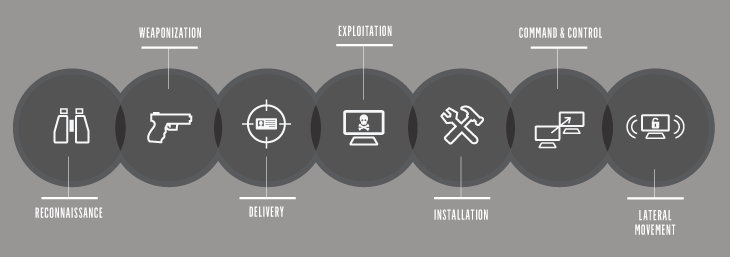
Let’s examine an example from the cyber world. An IOA represents a series of actions that an adversary must conduct to succeed. If we break down the most common and still the most successful tactic of determined adversaries – the spear phish – we can illustrate this point.
A successful phishing email must persuade the target to click on a link or open a document that will infect the machine. Once compromised, the attacker will silently execute another process, hide in memory or on disk and maintain persistence across reboots of the system. The next step is to make contact with a command and control site, informing his handlers that he awaits further instructions.
IOAs are concerned with the execution of these steps, the intent of the adversary and the outcomes he is trying to achieve. IOA’s are not focused on the specific tools he uses to accomplish his objectives.
By monitoring these execution points, gathering the indicators and consuming them via a Stateful Execution Inspection Engine, we can determine how an actor successfully gains access to the network and we can infer intent. No advance knowledge of the tools or malware (aka: Indicators of Compromise) is required.
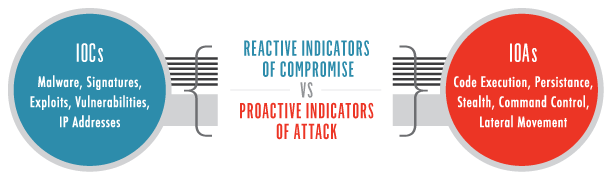
Comparing an IOA to an IOC
In revisiting the bank robber analogy, imagine if we were only looking for IOC’s. In evidence from a previous robbery CCTV allowed us to identify that the bank robber drives a purple van, wears a Baltimore Ravens cap and uses a drill and liquid nitrogen to break into the vault. Though we try to track and observe these unique characteristics, his modus operandi (MO), what happens when the same individual instead drives a red car and wears a cowboy hat and uses a crowbar to access the vault? The result? The robber is successful again because we, the surveillance team, relied on indicators that reflected an outdated profile (IOCs).
Remember from above, an IOA reflects a series of actions an actor / robber must perform to be successful: enter the bank, disable the alarm systems, enter the vault, etc.
IOA’s are the Real-time Recorder
A by-product of the IOA approach is the ability to collect and analyze exactly what is happening on the network in real-time. The very nature of observing the behaviors as they execute is equivalent to observing a video camera and accessing a flight data recorder within your environment.
Returning to the physical world, when a detective arrives on a crime scene and has a gun, a body, and some blood they usually ask to see if anyone has any video of what transpired. The blood, body, and gun are IOCs that need to be manually reconstructed and are point-in-time artifacts. Very simply put, IOAs provide content for the video logs.
In the Cyber realm, showing you how an adversary slipped into your environment, accessed files, dumped passwords, moved laterally and eventually exfiltrated your data is the power of an IOA.

Real-world Adversary Activity – Chinese Actor
CrowdStrike’s Intelligence Team documented the following example activity attributed to a Chinese actor. The following example does highlight how one particular adversary’s activity eluded even endpoint protections.
This adversary uses the following tradecraft:
- In memory malware – never writes to disk
- A known and acceptable IT tool – Windows PowerShell with command line code
- Cleans up logs after themselves leaving no trace
Let’s explore the challenges that other endpoint solutions have with this tradecraft:
Anti-Virus – since the malware is never written to disk, most AV solutions set for an on-demand scan will not be alerted. On-demand scanning is only triggered on a file write or access. In addition, most proactive organizations perform a full scan only once a week because of the performance impact on the end user. If defenders were performing this full scan, and if the AV vendor was able to scan memory with an updated signature, they may provide an alert of this activity.
AV 2.0 Solutions – these are solutions that use machine learning and other techniques to determine if a file is good or bad. PowerShell is a legitimate windows system administration tool that isn’t (and shouldn’t be) identified as malicious. Thus, these solutions will not alert clients to this behavior.
Whitelisting – Powershell.exe is a known IT tool and would be allowed to execute in most environments, evading whitelisting solutions that may be in place.
IOC Scanning Solutions – since this adversary never writes to disk and cleans up after completing their work, what would we search for? IOC’s are known artifacts and in this case, there are no longer artifacts to discover. Moreover, most forensic-driven solutions require periodic “sweeps” of the targeted systems, and if an adversary can conduct his business between sweeps, he will remain undetected.
Final Words
In conclusion, at CrowdStrike, we know that our clients have adversary problems, not malware problems. By focusing on the tactics, techniques and procedures of targeted attackers, we can determine who the adversary is, what they are trying to access, and why. By the time you detect Indicators of Compromise, your organization has probably already been breached and may require an expensive incident response effort to remediate the damage.
By recording and gathering the indicators of attack and consuming them via a Stateful Execution Inspection Engine, you enable your team to view activity in real time and react in the present. Accessing your own network flight recorder avoids many of the time-consuming tasks associated with “putting the pieces together” after the fact. Providing first responders with the tools necessary to reconstruct the crime scene provides a cost-effective and proactive approach to confronting advanced persistent threats.
Interested in learning more about the IOA approach? Read our article on how CrowdStrike leverages Event Stream Processing (ESP) to detect malicious behavior.
[转帖]IOC Security: Indicators of Attack vs. Indicators of Compromise的更多相关文章
- [转帖]/etc/security/limits.conf的含义
https://www.cnblogs.com/pzk7788/p/7250723.html /etc/security/limits.conf 是 Linux 资源使用配置文件,用来限制用户对系统资 ...
- 《Network Security A Decision and Game Theoretic Approach》阅读笔记
网络安全问题的背景 网络安全研究的内容包括很多方面,作者形象比喻为盲人摸象,不同领域的网络安全专家对网络安全的认识是不同的. For researchers in the field of crypt ...
- Security Software Engineer
Security Software Engineer Are you excited to be part of the VR revolution and work on cutting edge ...
- [安全转帖]浅析安全威胁情报共享框架OpenIOC
浅析安全威胁情报共享框架OpenIOC https://www.freebuf.com/sectool/86580.html Indicator of compromise Outline: 1. I ...
- document.domain与js跨域的问题
以前如果要使iframe里面的脚本能访问parent的内容,但iframe和parent的二级域名相同,那一般都会在两者都写上document.domain="xxx.com" 以 ...
- Coablt strike官方教程中文译版本
安装和设置 系统要求 Cobalt Strike的最低系统要求 2 GHz +以上的cpu 2 GB RAM 500MB +可用空间 在Amazon的EC2上,至少使用较高核数的CPU(c1.medi ...
- Parity 钱包启动配置
Parity. Ethereum Client. By Wood/Paronyan/Kotewicz/Drwięga/Volf et al. Copyright 2015, 2016, 2017, 2 ...
- VC/MFC 编程技巧大总结
1 toolbar默认位图左上角那个点的颜色是透明色,不喜欢的话可以自己改. 2 VC++中 WM_QUERYENDSESSION WM_ENDSESSION 为系统关机消息. 3 Java学习书推荐 ...
- 【云计算】使用Libcloud屏蔽OpenStack、AWS、AliYun等虚拟化层差异
libcloud 是一个访问云计算服务的统一接口,该项目已经成为 Apache 组织的顶级项目,采用 Python 开发. Apache基金会于5月25日宣布,Libcloud已完成孵化.成为顶级项目 ...
随机推荐
- if语句的嵌套:从键盘输入3个实数,利用条件表达式求其最大者。
#include<stdio.h>void main(){ float a,b,c,max; scanf("%f%f%f",&a,&b,&c); ...
- vant - Navbar slot 插槽使用
//子组件 <template> <van-nav-bar> <slot slot="left" name="left">& ...
- 2019.12.07 java计算
class Demo05{ public static void main(String[] args) { int a=1; a++; int b=1 + a++ + a + a++; System ...
- 洛谷 P3371 【模板】单源最短路径(弱化版) 题解
P3371 [模板]单源最短路径(弱化版) 题目背景 本题测试数据为随机数据,在考试中可能会出现构造数据让SPFA不通过,如有需要请移步 P4779. 题目描述 如题,给出一个有向图,请输出从某一点出 ...
- C语言博客06-结构体
1.本章学习总结 1.1 学习内容总结 结构体如何定义.成员如何赋值 1.结构体的一般形式为: struct 结构体名 { 数据类型 成员名1: 数据类型 成员名2: : 数据类型 成员名n: }: ...
- 深入理解数据库索引采用B树和B+树的原因
前面几篇关于数据库底层磁盘文件读取,数据库索引实现细节进行了深入的研究,但是没有串联起来的讲解为什么数据库索引会采用B树和B+树而不是其他的数据结构,例如平衡二叉树.链表等,因此,本文打算从数据库文件 ...
- flask + Python3 实现的的API自动化测试平台---- IAPTest接口测试平台,更名:FXTest 接受定制开发(java版开发完毕)
**背景: 1.平时测试接口,总是现写代码,对测试用例的管理,以及测试报告的管理持久化做的不够, 2.工作中移动端开发和后端开发总是不能并行进行,需要一个mock的依赖来让他 ...
- CSS各类布局
http://www.liquidapsive.com/ 1 静态布局(Static Layout)网页上的所有元素的尺寸一律使用px作为单位.特点:不管浏览器尺寸具体是多少,网页布局始终按照最初写代 ...
- 两个对象值相同 (x.equals(y) == true) ,但却可有不同的 hash code ,这 句话对不对
答:不对,有相同的 hash code这是java语言的定义:1) 对象相等则hashCode一定相等:2) hashCode相等对象未必相等 1.如果是基本变量,没有hashcode和equals方 ...
- egg.js搭建 api设置跨域
1.egg简述 Egg.js,为企业级框架和应用而生,是阿里开源的企业级 Node.js 框架. 2.特点 Egg 奉行『约定优于配置』,按照一套统一的约定进行应用开发,团队内部采用这种方式可以减少开 ...
