HTTPS and the TLS handshake protocol阅读笔记
目的
为能够透彻理解HTTPS报文交互过程,做此笔记。
本文大部分内容来自 : http://albertx.mx/blog/https-handshake/
http://www.cnblogs.com/svan/p/5090201.html
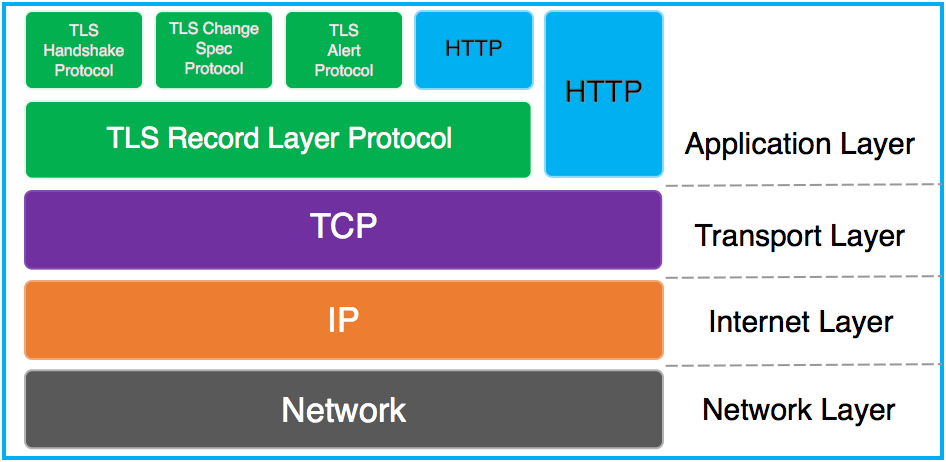
TLS Handshake Protocol
The TLS Handshake its like a sub-protocol of the TLS protocol. Its purpose is to define the algorithms and keys to authenticate the parties, verify and encrypt the data.
一次完整的http交互如下:
client hello -- 客户端向服务器打招呼 (带着 支持的 ciper suites)
server hello -- 服务器响应客户端 (告诉客户端, 我选择了哪一个 ciper suite)
Certificate Server hello done -- 服务器向客户端送证书(表明自己的身份)
Client Key Exchange, change ciper spec, encrypted handshake message -- 客户端发送密钥, 告诉服务器开始传送密文数据了, 传送一个加密的握手数据
New Session Ticket, change ciper spec, encrypted handshake message -- 服务器建立会话凭据, 告诉客户端开始传送密文数据了,传送一个加密的握手数据。

流程如下:
http://security.stackexchange.com/questions/20803/how-does-ssl-tls-work/20847#20847
Client Server ClientHello -------->
ServerHello
Certificate*
ServerKeyExchange*
CertificateRequest*
<-------- ServerHelloDone
Certificate*
ClientKeyExchange
CertificateVerify*
[ChangeCipherSpec]
Finished -------->
[ChangeCipherSpec]
<-------- Finished
Application Data <-------> Application Data
Client Hello
- The version of SSL that the client is trying to use for negotiating with the server
- Some random bytes generated by the client that will be used next to generate a master key for encryption.
- A list of encryption algorithms called cipher_suites. The client tells the server which cipher suites it understands.
主要传送 客户端支持的 加密算法列表:

Cipher Suites
包括四个部分:
TLS_DHE_RSA_WITH_AES_256_CBC_SHA
DHE -- 密码交换加密算法
RSA -- 认证算法
AES_256_CBC -- 数据交换加密算法
SHA -- 数据完整性算法
Now, let me talk about the cipher suites listed above. If you review the image posted in the client hello section you will see a list. This list indicates the algorithms that will be used during the handshake and data transmission. The protocol needs 4 algorithms to work:
- Authentication algorithm
- Key Exchange algorithm
- Bulk cipher algorithm
- Message Authentication algorithm
These 4 algorithms are specified in the cipher suite.
Analyzing the first suite in the list we have the text: TLS_DHE_RSA_WITH_AES_256_CBC_SHA.
- TLS: This is Transport Layer Security, the protocol we are using in the negotiation
- DHE: Denotes Ephemeral Diffie-Hellman. Diffie-Hellman is an
algorithm for key exchanging cryptographic keys. Diffie-Hellman in
ephemeral mode enhances its security- RSA: This is the algorithm used for authentication. The most used algorithm in public-key cryptography (Rivest, Shamir and Adleman)
- WITH_AES_256_CBC: Advanced Encryption Standard is one of
the best algorithms used in symmetric cryptography. Its key size can be
of 128 bits, 192 bits or 256 bits. In this case the key size is 256
bits. CBC stands for Cipher-block Chaining one mode of
operation in encryption. It means that the algorithm will encrypt the
bytes of data by blocks and then it will link the encrypted blocks like a
chain.- SHA: Secure Hash Algorithm will be used for message authentication creating a hash of each block of the message to verify the integrity of such message.
Server Hello
- Some random bytes now generated by the server that will be used to generate a master key.
- The cipher suite selected by the server (from the previous list sent by the client) that will be used for authentication, encryption and verification of the messages
告诉客户端,我选择的算法。

Certificate
The Certificate command is usually sent again from server to client. In this command the information transmitted is the list of certificates that the client needs to have in order to authenticate the server and to encrypt some information. This can be one, two or more certificates.
证书用于认证服务器端的身份,防止被钓鱼等攻击。 其中也包括 服务器端的 公钥, 用于加密数据。
证书 可以是多个, 呈现链式法则。

Server Hello Done
Immediately after the Certificate message the server sends the Server Hello Done message. At this point the client has all the information it needs to generate the key material that both parties will need to encrypt the data. This key material is sent in the next handshake message…
服务器端,告诉客户端, 你已经具备产生密钥的条件, 快生成吧。
Client Key Exchange
The client generates some bytes of data, encrypt them with the public key of the certificate it received and then sends the encrypted data to the server (this is called PreMaster secret and will be used to generate the Master secret). The algorithm by which the client protects the data is defined during the Client Hello and Server Hello messages. It can be RSA or Diffie-Hellman.
客户端生成 一串随机的byte(PreMaster secret), 使用公钥加密后,传给服务器。 加密的算法hello过程已经确定。
关于master secret 生成, 见如下文章介绍(在第五点告诉你 master secret产生):
http://www.cnblogs.com/svan/p/5090201.html
使用RSA算法的SSL握手过程是这样的
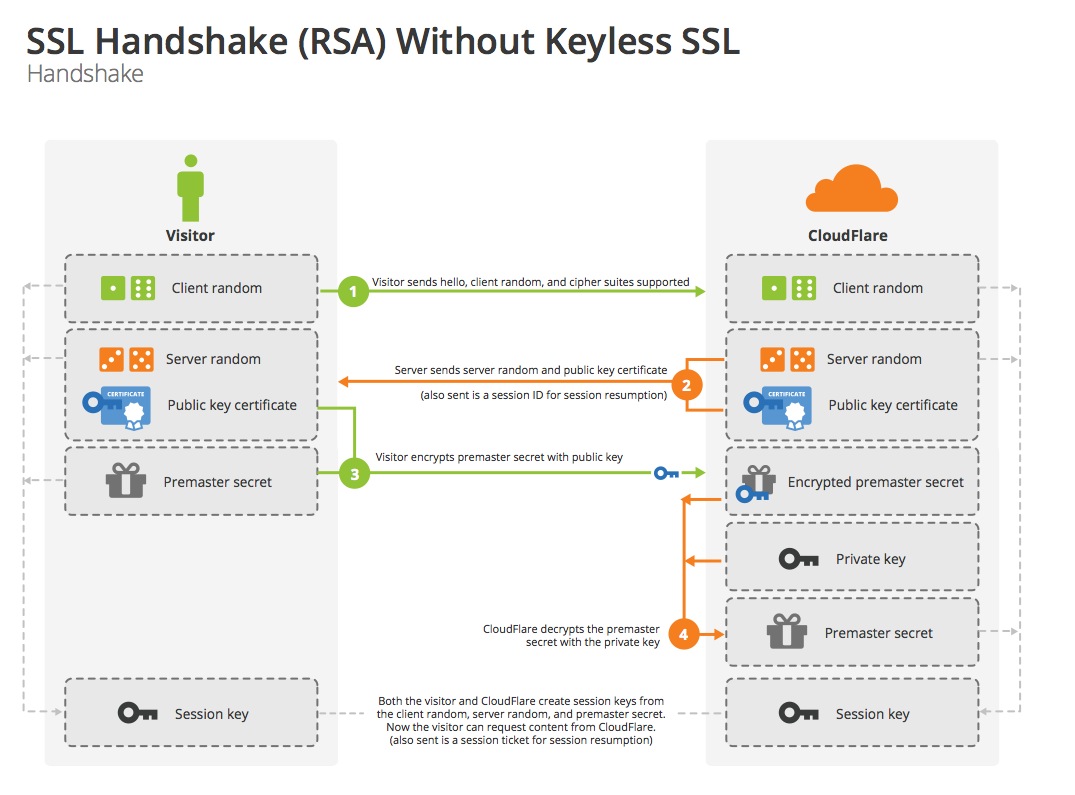
- [明文] 客户端发送随机数
client_random和支持的加密方式列表 - [明文] 服务器返回随机数
server_random,选择的加密方式和服务器证书链 - [RSA] 客户端验证服务器证书,使用证书中的公钥加密
premaster secret发送给服务端 - 服务端使用私钥解密
premaster secret - 两端分别通过
client_random,server_random和premaster secret生成master secret,用于对称加密后续通信内容
master secret是如何计算的
master_secret = PRF(pre_master_secret, "master secret",
ClientHello.random + ServerHello.random)
[0..47];
Change Cipher Spec
This is also sent from client to server indicating that the server MUST be prepared to receive the data in encrypted format and not in readable format because all the previous messages exchanged between client and server had been readable. This is the last message sent from client to server as readable. After this all the data sent to the server will be encrypted and we will not be able to read the contents with wireshark or any other sniffer tool. Proof of this is that in the below image the message after the Change Cipher Spec is an Encrypted Handshake Message.
客户端告诉服务器, 下一个报文开始传送 密文 了噢。

Finished
This is the first message protected by the algorithms and keys negotiated between the entities (this is the Encrypted Handshake Messsage we saw in the image). Both client and server send the Finished message but the first to do it is the client. If the server receives the message and could decrypt and understand it, it means the the server is reading the encrypted information in the right way. Now the only missing part is that client could decrypt the information sent by the server. To do that the server must send a Change Cipher Spec message too followed by the Finished message in the encrypted way. Exactly the same as client did. Again if the client could decrypt the Finished message it means that both parties are in frequency and they can talk to each other protecting all the data in transit.
客户端先想服务器端, 发送一个加密的报文, 如果服务器能够解密,并理解无误(客户端加密的内容, 是之前明文报文的一个摘要, 服务器端解密后, 计算其受到报文的摘要,并跟解密的摘要比较, 如果相等,则服务器接受客户端数据通道无误。)
然后服务器端,也一致, 需要按照客户端的做法, 先发送一个 change ciper spec消息, 告诉客户端要发送 密文了准备接受哦,
然后发送一个验证性通道畅通的加密报文, 客户端解密OK, 并可以理解(同上), 则两端握手成功。
开始传送应用数据。
HTTPS and the TLS handshake protocol阅读笔记的更多相关文章
- Formal Analysis of the TLS Handshake Protocol -----论文整理
1.关键词 TLS.SSL.Formal Analsysis Conridentiality Secerecy 2.Table THE SSL/TLS handshake Protocol 3 ...
- normalization 阅读笔记
https://zhuanlan.zhihu.com/p/33173246 阅读笔记 1. normalization whiting - PCA 2. Internal Covariate Shif ...
- 解决docker pull出现 error pulling image configuration: Get https://dseasb33srnrn.cloudfront.net······: net/http: TLS handshake timeout的问题
[root@MyCentos7 var]# docker pull javaUsing default tag: latestTrying to pull repository docker.io/l ...
- 解决 docker.io 上拉取 images Get https://registry-1.docker.io/v2/: net/http: TLS handshake timeout
处理方式 使用如下命令获取 registry-1.docker.io 可用的 ip dig @114.114.114.114 registry-1.docker.io 看到如下输出结果 ; <& ...
- Hadoop阅读笔记(七)——代理模式
关于Hadoop已经小记了六篇,<Hadoop实战>也已经翻完7章.仔细想想,这么好的一个框架,不能只是流于应用层面,跑跑数据排序.单表链接等,想得其精髓,还需深入内部. 按照<Ha ...
- CI框架源码阅读笔记3 全局函数Common.php
从本篇开始,将深入CI框架的内部,一步步去探索这个框架的实现.结构和设计. Common.php文件定义了一系列的全局函数(一般来说,全局函数具有最高的加载优先权,因此大多数的框架中BootStrap ...
- Mongodb Manual阅读笔记:CH4 管理
4 管理 Mongodb Manual阅读笔记:CH2 Mongodb CRUD 操作Mongodb Manual阅读笔记:CH3 数据模型(Data Models)Mongodb Manual阅读笔 ...
- “CoreCLR is now Open Source”阅读笔记
英文原文:CoreCLR is now Open Source 阅读笔记如下: CoreCLR是.NET Core的执行引擎,功能包括GC(Garbage Collection), JIT(将CIL代 ...
- QCon 2015 阅读笔记 - 移动开发最佳实践
所有ppt下载地址:http://pan.baidu.com/s/1mg9o4TM 下面是移动开发实践部分的阅读笔记. 移动开发网络性能优化实践 - 陈浩然 (携程) 携程是非常标准的移动App架构, ...
随机推荐
- Mac OS 快捷键
系统 (Option+) Command+Space 切换输入法 Command+Tab 切换不同应用 Command+Tab 切换一个应用内的不同窗口 Command+Shift+3 截取整个屏幕 ...
- twitter storm源码走读之2 -- tuple消息发送场景分析
欢迎转载,转载请注明出处源自徽沪一郎.本文尝试分析tuple发送时的具体细节,本博的另一篇文章<bolt消息传递路径之源码解读>主要从消息接收方面来阐述问题,两篇文章互为补充. worke ...
- jedis操作
Jedis jedis = RedisUtil.getJedis(); try { // 向key-->name中放入了value-->minxr jedis.set("name ...
- 【翻译】CEDEC2014 CAPCOM 照相机正确的照片真实的制作工作流
这次带来的翻译是Capcom在CEDEC2014上发表的技术美术相关的资料.资料的目的,就是在已经拥有了一套基于物理的渲染引擎的前提下,如何进行图片真实的材料的拍摄并制作为引擎里的材质,以及如何正确 ...
- P1010 幂次方
这么难得题,居然普及-?做了好久 #include <bits/stdc++.h> using namespace std; int fact[21]; void solve(int n) ...
- fortran中如何提供计算程序运行时间?
如下: Real time_begin , time_end1 , time_end2 Integer i , j call CPU_TIME(time_begin) write(*,*) time_ ...
- java 重写 重载
首先我们来讲讲:重载(Overloading) (1) 方法重载是让类以统一的方式处理不同类型数据的一种手段.多个同名函数同时存在,具有不同的参数个数/类型. 重载Overloading是一个类中多态 ...
- 七 mybatis的延迟加载
1 延迟加载 1.1 什么是延迟加载 resultMap可以实现高级映射(使用association.collection实现一对一及一对多映射),association.coll ...
- Linq中常用的方法
这几天闲着也是闲着,就仔细的研究了一下Linq的语法,还有他的一些扩展方法的使用. 下面是一些常用的扩展方法. Aggregate 自定义的聚合计算 All 检测序列中所有元素是否都满足指定的条件 A ...
- linux环境下的伪分布式环境搭建
本文的配置环境是VMware10+centos2.5. 在学习大数据过程中,首先是要搭建环境,通过实验,在这里简短粘贴书写关于自己搭建大数据伪分布式环境的经验. 如果感觉有问题,欢迎咨询评论. 一:伪 ...
