Hash Tables and Hash Functions
Reference: Compuer science
Introduction:
This computer science video describes the fundamental principles of the hash table data structure which allows for very fast insertion and retrieval of data. It covers commonly used hash algorithms for numeric and alphanumeric keys and summarises the objectives of a good hash function. Collision resolution is described, including open addressing techniques such as linear and quadratic probing, and closed addressing techniques such as chaining with a linked list.

Consider a list:

Find Ada
You can use linearly search, which costs the time of O(n)
Or you happend to know the index of ada(8), you can look up the value very quickly.
this costs you the time of O(1)
Can help wondering that what if we encode the name into index would the look-up process become O(1).?
Absolutely!
we can turn the key(i.e. the name) into a number(index) with a hash function.
Let's say take each letter of the word get its ascii code,add them up,divided by the length of the array,get the remainder.

Namely , the hash function here is :
we can serve the properties of a person as the value,the name as key.
So that we can look up the profile of a person by the key(i.e.name)

Notes:

So far you aquire the ability to transform a key into index, you can look up very information by hash table.
Needless to say, that is unrealistic.

Have you ever consider the case that two different key are truned into a same index number?
That is collisions.
Let's look a example.
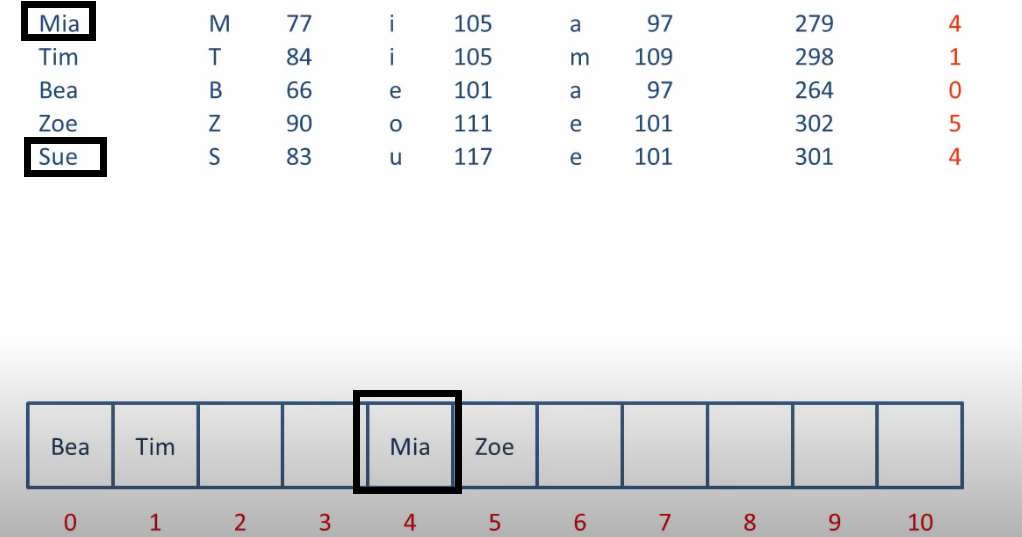
How to solve collisions?
we can put sue into the next place index5 which is empty.
Basically we can put the one that causes collision into the next empty place.
this is linear probing.
put the element somewhere other than the caculated adress is call open adressing.
because every location is open to every elements.
we can use a varity of techniques to decide where to palce.
If we get to the end of the array still can't find a empty place,
it may cycle around to the start of the array.
As you can image , the indexing process is also involved linear probing.(linear search)
In the worse case scenario, it takes O(n) to store and search a key.
Need to mention:

Another way to deal with collisions is called chaining. (close addressing)
we add a linked list in the collision index.
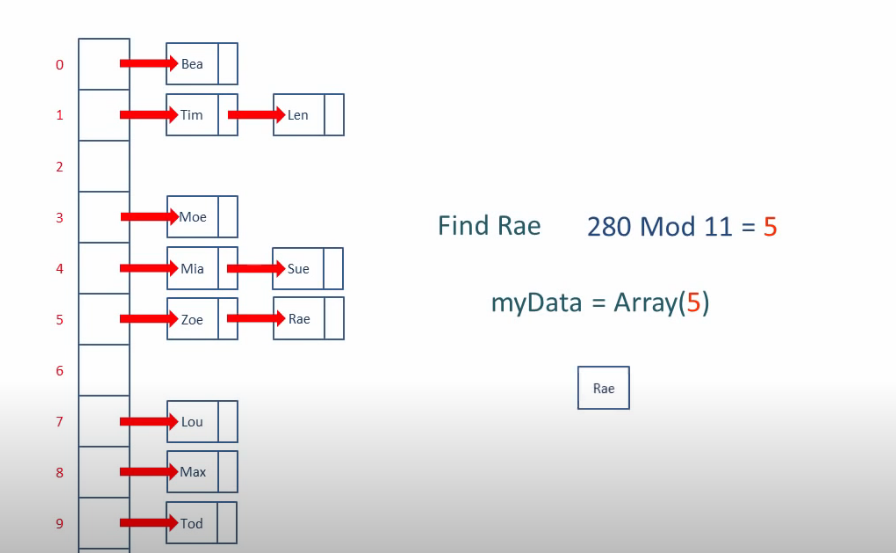
traverse the linked list also takes time.
Summary:



Hash Tables and Hash Functions的更多相关文章
- 11 Hash tables
11 Hash tables Many applications require a dynamic set that supports only the dictionary operatio ...
- 查询计划Hash和查询Hash
查询计划hash和查询hash 在SQL Server 2008中引入的围绕执行计划和缓冲的新功能被称为查询计划hash和查询hash.这是使用针对查询或查询计划的算法来生成二进制hash值的二进制对 ...
- 14.4.3 Adaptive Hash Index 自适应hash index
14.4.3 Adaptive Hash Index 自适应hash index 自适应hash index(AHI) 让InnoDB 执行更像内存数据库在系统使用合适的负载组合和足够的内存用于Buf ...
- 14.2.5.6 Adaptive Hash Indexes 自适应Hash Indexes
14.2.5.6 Adaptive Hash Indexes 自适应Hash Indexes adaptive hash index(AHI) 让InnoDB 执行更加像在一个内存数据库里在, 在不牺 ...
- Hash::make与Hash::check
调用方法之前要先去引用: use Illuminate\Support\Facades\Hash; 可以调用 Hash 门面上的 make 方法对存储密码进行哈希: $pwd = Hash::make ...
- 转载:字符串hash总结(hash是一门优雅的暴力!)
转载自:远航休息栈 字符串Hash总结 Hash是什么意思呢?某度翻译告诉我们: hash 英[hæʃ] 美[hæʃ]n. 剁碎的食物; #号; 蔬菜肉丁;vt. 把…弄乱; 切碎; 反复推敲; 搞糟 ...
- cdoj1092-韩爷的梦 (字符串hash)【hash】
http://acm.uestc.edu.cn/#/problem/show/1092 韩爷的梦 Time Limit: 200/100MS (Java/Others) Memory Limi ...
- Hash表及hash算法的分析
Hash表中的一些原理/概念,及根据这些原理/概念: 一. Hash表概念 二. Hash构造函数的方法,及适用范围 三. Hash处理冲突方法,各自特征 四. ...
- Cuckoo Hash和多级Hash的粗浅认识
通过对Cuckoo Hash.多级Hash和BloomFilter的粗浅了解,感觉它们三者存在类似之处,算是近亲(暂且把普通的Hash称作远亲). Cuckoo Hash的思想非常简单,冲突时,重Ha ...
随机推荐
- JAVA死锁的检测流程
步骤一. 查询检测的进程 1.首先查看系统资源占用信息,TOP看一下 发现正在运行的JAVA项目CPU占用率很高,百分之360左右了,那么问题一定出在这个程序中 2 .也可以通过名称查询进程pid 步 ...
- uniapp保存图片到本地(APP和微信小程序端)
uniapp实现app端和微信小程序端图片保存到本地,其它平台未测过,原理类似. 微信小程序端主要是权限需要使用button的开放能力来反复调起,代码如下: 首先是条件编译两个平台的按钮组件: < ...
- Service Cloud 零基础(二)Knowledge浅谈
本篇参考:https://trailhead.salesforce.com/content/learn/projects/set-up-salesforce-knowledge https://tra ...
- ACL 的功能、匹配原则、端口号类别
功能 1)限制网络流量.提高网络性能.例如,ACL可以根据数据包的协议,指定这种类型的数据包具有更高的优先级,同等情况下可预先被网络设备处理. 2)提供对通信流量的控制手段. 3)提供网络访问的基本安 ...
- IO流(03)--序列化流、打印流
序列化流 Java提供了一种对象序列化的机制,用一个字节序列可以表示一个对象,该字节序列包含该对象的数据.对象的类型和对象中存储的属性等信息.字节序列写入到文件中后,就相当于在文件中保存了一个对象信息 ...
- js上 七、表达式
(1).什么是表达式 任何有值的内容都是表达式 一个表达式会产生一个值,它可以放在任何需要一个值的地方,比如a=3中的3就是一个表达式,a=3整体也可以作为一个表达式. 常见表达式有如下几种: ü 原 ...
- vue第八单元(组件通信 子父,父子组件通信 自定义事件 事件修饰符 v-model props验证 )
第八单元(组件通信 子父,父子组件通信 自定义事件 事件修饰符 v-model props验证 ) #课程目标 掌握使用props让父组件给子组件传参(重点) 掌握props属性的使用以及prop验证 ...
- [日常摸鱼]bzoj2724蒲公英-分块
区间众数经典题~ http://begin.lydsy.com/JudgeOnline/problem.php?id=4839这里可以提交~ 题意大概就是没有修改的询问区间众数,如果有一样的输出最小的 ...
- Eureka系列(九)Eureka自我保护机制
因为本篇简文并不是自己总结的,而是当了下搬运工,所以直接直接附上原作者博客链接. 参考链接: 1.SpringCloud Eureka自我保护机制 2.Spring Cloud Eurek ...
- 基于excel实现接口自动化测试
本文档介绍如何使用excel管理接口测试用例并一键执行的实现方式,其中包括 python 读写excel, request库的基本操作,接口用例的设计 接口用例设计 用例字段描述 被依赖表达式: 示例 ...
