Kali Linux configuration "Ettercap"
Xx_Instroduction
- Ettercap is a man-in-the-middle attack(MITM) tool,kali take this tool,so,use front we are need configuration that configuration file.

Ax_Open
- vi /etc/ettercap/etter.conf

1 ############################################################################
2 ## 3 # ettercap -- etter.conf -- configuration file #
4 # #
5 # Copyright (C) ALoR & NaGA #
6 # #
7 # This program is free software; you can redistribute it and/or modify #
8 # it under the terms of the GNU General Public License as published by #
9 # the Free Software Foundation; either version 2 of the License, or #
10 # (at your option) any later version. #
11 # #
12 # #
13 ############################################################################
14
15 [privs]
16 ec_uid = 0 #nobody is the default
17 #haha userid and groupid gaiwei 0
18 ec_gid = 0 # nobody is the default
19
20 [mitm]
21 arp_storm_delay = 10 # milliseconds
22 arp_poison_smart = 0 # boolean
23 arp_poison_warm_up = 1 # seconds
24 arp_poison_delay = 10 # seconds
25 arp_poison_icmp = 1 # boolean
26 arp_poison_reply = 1 # boolean
27 arp_poison_request = 0 # boolean
28 arp_poison_equal_mac = 1 # boolean
29 dhcp_lease_time = 1800 # seconds
30 port_steal_delay = 10 # seconds
31 port_steal_send_delay = 2000 # microseconds
32 ndp_poison_warm_up = 1 # seconds
33 ndp_poison_delay = 5 # seconds
34 ndp_poison_send_delay = 1500 # microseconds
35 ndp_poison_icmp = 1 # boolean
36 ndp_poison_equal_mac = 1 # boolean
37 icmp6_probe_delay = 3 # seconds
38
39 [connections]
40 connection_timeout = 300 # seconds
41 connection_idle = 5 # seconds
42 connection_buffer = 10000 # bytes
43 connect_timeout = 5 # seconds
44
45 [stats]
46 sampling_rate = 50 # number of packets
47
48 [misc]
49 close_on_eof = 1 # boolean value
50 store_profiles = 1 # 0 = disabled; 1 = all; 2 = local; 3 = remote
51 aggressive_dissectors = 1 # boolean value
52 skip_forwarded_pcks = 1 # boolean value
53 checksum_check = 0 # boolean value
54 submit_fingerprint = 0 # boolean valid (set if you want ettercap to submit unknown finger prints)
55 checksum_warning = 0 # boolean value (valid only if checksum_check is 1)
56 sniffing_at_startup = 1 # boolean value
57
58 ############################################################################
59 #
60 # You can specify what DISSECTORS are to be enabled or not...
61 #
62 # e.g.: ftp = 21 enabled on port 21 (tcp is implicit)
63 # ftp = 2345 enabled on non standard port
64 # ftp = 21,453 enabled on port 21 and 453
65 # ftp = 0 disabled
66 #
67 # NOTE: some dissectors have multiple default ports, if you specify a new
68 # one, all the default ports will be overwritten
69 #
70 #
71
72 #dissector default port
73
74 [dissectors]
75 ftp = 21 # tcp 21
76 ssh = 22 # tcp 22
77 telnet = 23 # tcp 23
78 smtp = 25 # tcp 25
79 dns = 53 # udp 53
80 dhcp = 67 # udp 68
81 http = 80 # tcp 80
82 ospf = 89 # ip 89 (IPPROTO 0x59)
83 pop3 = 110 # tcp 110
84 #portmap = 111 # tcp / udp
85 vrrp = 112 # ip 112 (IPPROTO 0x70)
86 nntp = 119 # tcp 119
87 smb = 139,445 # tcp 139 445
88 imap = 143,220 # tcp 143 220
89 snmp = 161 # udp 161
90 bgp = 179 # tcp 179
91 ldap = 389 # tcp 389
92 https = 443 # tcp 443
93 ssmtp = 465 # tcp 465
94 rlogin = 512,513 # tcp 512 513
95 rip = 520 # udp 520
96 nntps = 563 # tcp 563
97 ldaps = 636 # tcp 636
98 telnets = 992 # tcp 992
99 imaps = 993 # tcp 993
100 ircs = 994 # tcp 993
101 pop3s = 995 # tcp 995
102 socks = 1080 # tcp 1080
103 radius = 1645,1646 # udp 1645 1646
104 msn = 1863 # tcp 1863
105 cvs = 2401 # tcp 2401
106 mysql = 3306 # tcp 3306
107 icq = 5190 # tcp 5190
108 ymsg = 5050 # tcp 5050
109 mdns = 5353 # udp 5353
110 vnc = 5900,5901,5902,5903 # tcp 5900 5901 5902 5903
111 x11 = 6000,6001,6002,6003 # tcp 6000 6001 6002 6003
112 irc = 6666,6667,6668,6669 # tcp 6666 6667 6668 6669
113 gg = 8074 # tcp 8074
114 proxy = 8080 # tcp 8080
115 rcon = 27015,27960 # udp 27015 27960
116 ppp = 34827 # special case ;) this is the Net Layer code
117 TN3270 = 23,992 # tcp 23 992
118
119 #
120 # you can change the colors of the curses GUI.
121 # here is a list of values:
122 # 0 Black 4 Blue
123 # 1 Red 5 Magenta
124 # 2 Green 6 Cyan
125 # 3 Yellow 7 White
126 #
127 [curses]
128 color_bg = 0
129 color_fg = 7
130 color_join1 = 2
131 color_join2 = 4
132 color_border = 7
133 color_title = 3
134 color_focus = 6
135 color_menu_bg = 4
136 color_menu_fg = 6
137 color_window_bg = 4
138 color_window_fg = 7
139 color_selection_bg = 6
140 color_selection_fg = 6
141 color_error_bg = 1
142 color_error_fg = 3
143 color_error_border = 3
144
145 #
146 # This section includes all the configurations that needs a string as a
147 # parmeter such as the redirect command for SSL mitm attack.
148 #
149 [strings]
150
151 # the default encoding to be used for the UTF-8 visualization
152 utf8_encoding = "ISO-8859-1"
153
154 # the command used by the remote_browser plugin
155 remote_browser = "xdg-open http://%host%url"
156
157
158 #####################################
159 # redir_command_on/off
160 #####################################
161 # you must provide a valid script for your operating system in order to have
162 # the SSL dissection available
163 # note that the cleanup script is executed without enough privileges (because
164 # they are dropped on startup). so you have to either: provide a setuid program
165 # or set the ec_uid to 0, in order to be sure the cleanup script will be
166 # executed properly
167 # NOTE: the script must fit into one line with a maximum of 255 characters
168
169 #---------------
170 # Linux
171 #---------------
172
173 # if you use ipchains:
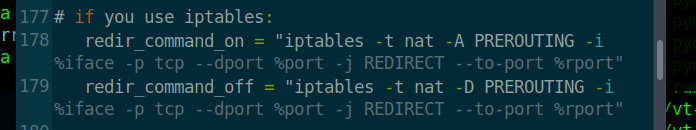
174 #redir_command_on = "ipchains -A input -i %iface -p tcp -s 0/0 -d 0/0 %port -j REDIRECT %rport"
175 #redir_command_off = "ipchains -D input -i %iface -p tcp -s 0/0 -d 0/0 %port -j REDIRECT %rport"
176
177 # if you use iptables:
178 redir_command_on = "iptables -t nat -A PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport"
179 redir_command_off = "iptables -t nat -D PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport"
180
181 #---------------
182 # Mac Os X
183 #---------------
184
185 # quick and dirty way:
186 #redir_command_on = "ipfw -q add set %set fwd 127.0.0.1,%rport tcp from any to any %port in via %iface"
187 #redir_command_off = "ipfw -q delete set %set"
188
189 # a better solution is to use a script that keeps track of the rules interted
190 # and then deletes them on exit:
191
192 # redir_command_on:
193 # ----- cut here -------
194 # #!/bin/sh
195 # if [ -a "/tmp/osx_ipfw_rules" ]; then
196 # ipfw -q add head -n 1 osx_ipfw_rules fwd 127.0.0.1,1 tcp from any to any2 in via 3 197 # else 198 # ipfw add fwd 127.0.0.1,1 tcp from any to any 2 in via3 | cut -d " " -f 1 >> /tmp/osx_ipfw_rules
199 # fi
200 # ----- cut here -------
201
202 # redir_command_off:
203 # ----- cut here -------
204 # #!/bin/sh
205 # if [ -a "/tmp/osx_ipfw_rules" ]; then
206 # ipfw -q delete head -n 1 /tmp/osx_ipfw_rules
207 # rm -f /tmp/osx_ipfw_rules
208 # fi
209 # ----- cut here -------
210
211 #---------------
212 # FreeBSD
213 #---------------
214
215 # Before OF can be used, make sure the kernel module has been loaded by
216 # kldstat | grep pf.ko. If the rusult is empty, you can load it by
217 # kldload pf.ko or add 'pf_enable="YES"' to the /etc/rc.conf and reboot.
218
219 # Check if the PF status is enabled by
220 # pfctl -si | grep Status | awk '{print $2;}'. If "Disabled", enable it with
221 # pfctl -e.
222
223 #redir_command_on = "(pfctl -sn 2> /dev/null; echo 'rdr pass on %iface inet proto tcp from any to any port %port -> localhost port %rport') | pfctl -f - 2> /dev/null"
224 #redir_command_off = "pfctl -Psn 2> /dev/null | grep -v %port | pfctl -f - 2> /dev/null"
225
226
227 #---------------
228 # Open BSD
229 #---------------
230
231 # unfortunately the pfctl command does not accepts direct rules adding
232 # you have to use a script which executed the following command:
233
234 # ----- cut here -------
235 # #!/bin/sh
236 # rdr pass on 1 inet proto tcp from any to any port2 -> localhost port $3 | pfctl -a sslsniff -f -
237 # ----- cut here -------
238
239 # it's important to remember that you need "rdr-anchor sslsniff" in your
240 # pf.conf in the TRANSLATION section.
241
242 #redir_command_on = "the_script_described_above %iface %port %rport"
243 #redir_command_off = "pfctl -a sslsniff -Fn"
244
245 # also, if you create a group called "pfusers" and have EC_GID be that group,
246 # you can do something like:
247 # chgrp pfusers /dev/pf
248 # chmod g+rw /dev/pf
249 # such that all users in "pfusers" can run pfctl commands; thus allowing non-root
250 # execution of redir commands.
251
252
253 ##########
254 # EOF #
255 ##########</pre>
Bx_Modificati
- Line 16 and line 18 will userid and groupid value instead 0

- Line 178 and line 179 do away with "#" ,in this way can pass iptables firewall function transmit part flow.
save,close,and ok
Kali Linux configuration "Ettercap"的更多相关文章
- kali linux之窥看女神上网隐私(ettercap+wireshark+zenmap +dsniff)
作者:小波 http://www.cnblogs.com/xiaobo-Linux/ 无聊就玩了玩,不要干一些坏事哟~~网上也有一些文章关于kali linux的,就实战了一番.kali是用的debi ...
- Kali Linux ettercap的使用
ettercap是执行ARP欺骗嗅探的工具,通常用它来施行中间人攻击. 我还介绍过另一个arp欺骗工具-arpspoof 我使用的是Kali Linux 2.0:在开始使用ettercap之前,先配置 ...
- kali Linux 渗透测试 | ettercap图形界面(ARP 欺骗 + DNS欺骗)
上次我们使用 arpspoof 工具在命令行中完成了 arp 欺骗实验,今天我们用另一种工具 ettercap 工具来实现.ettercap支持图形化操作,对新手非常友好,并且操作非常简单, ette ...
- Kali Linux——迈向网络攻防
自从进入大三的课程后,在已学的高数.线代.数论.概率论.信息论.通信等知识的技术上,开始了网络信息安全.网 络攻防的学习.俗话说得好,磨刀不误砍柴工,开始网络攻防之旅也势必要一个好的工具.然 ...
- [原创]kali linux下破解wifi密码以及局域网渗透
无线破解是进行无线渗透的第一步.破解无线目前只有两种方法:抓包.跑pin. 破解无线方法一:抓包.我是在kali linux下进行的. 将无线网卡的模式调为监听模式. airmon-ng start ...
- 教你如何在Kali Linux 环境下设置蜜罐?
导读 Pentbox是一个包含了许多可以使渗透测试工作变得简单流程化的工具的安全套件.它是用Ruby编写并且面向GNU/Linux,同时也支持Windows.MacOS和其它任何安装有Ruby的系统. ...
- Kali Linux渗透基础知识整理(三):漏洞利用
漏洞利用阶段利用已获得的信息和各种攻击手段实施渗透.网络应用程序漏洞诊断项目的加密通信漏洞诊断是必须执行的.顾名思义,利用漏洞,达到攻击的目的. Metasploit Framework rdeskt ...
- kali Linux系列教程之BeFF安装与集成Metasploit
kali Linux系列教程之BeFF安装与集成Metasploit 文/玄魂 kali Linux系列教程之BeFF安装与集成Metasploit 1.1 apt-get安装方式 1.2 启动 1. ...
- Kali Linux Web 渗透测试视频教程—第十四课-arp欺骗、嗅探、dns欺骗、session劫持
Kali Linux Web 渗透测试视频教程—第十四课-arp欺骗.嗅探.dns欺骗.session劫持 文/玄魂 目录 Kali Linux Web 渗透测试—第十四课-arp欺骗.嗅探.dns欺 ...
随机推荐
- Mysql基础01-语法
数据库 数据的存储:将数据放到表中,表再放到库中. 一个数据库中可以有多个表,每个表都有一个名字,用来标识自己.表名具有唯一性. 表由列组成,我们也称为字段.每个字段描述了它所含有的数据的意义表由列组 ...
- Elasticsearch logstash filter
参照官方文档: https://www.elastic.co/guide/en/logstash/current/advanced-pipeline.html demo-pipeline.conf i ...
- 导出excel时,跳转新空白页,不要跳转怎么改
导出excel的时候,偶尔会出现跳转到一个新页面再导出excel js中用window.open()做跳转 不想让它跳转到新页面,需要加一个隐藏的iframe <iframe name=&quo ...
- redis第一讲【redis的描述,linux和docker下的安装使用】
Redis(REmote DIctionary Server):是什么 redis(远程字典服务器),是完全开源免费的,高性能的k/v分布式内存数据,热门的Nosql数据库 Redis可以干什么: 内 ...
- 资源池模式和单例模式实现的自定义数据库连接池java实现版
在企业级开发中,我们往往不会直接使用原生的JDBC操作来实现与数据库得连接.因为数据库的连接是一个很宝贵的资源且耗时,我们往往会在内存中引入一个资源池来统一管理数据库的连接.这个模式也被总结为一种设计 ...
- 【CuteJavaScript】ES2019 新特性汇总
最近 ECMAScript2019,最新提案完成:tc39 Finished Proposals,我这里也是按照官方介绍的顺序进行整理,如有疑问,可以查看官方介绍啦~ 另外之前也整理了 <ES6 ...
- v-if和v-show 的区别
区别 1.手段:v-if是通过控制dom节点的存在与否来控制元素的显隐:v-show是通过设置DOM元素的display样式,block为显示,none为隐藏: 2.编译过程:v-if切换有一个局部编 ...
- Python3、setuptools、Pip3安装详解
Python3.setuptools.Pip3安装详解 2017年08月19日 18:58:47 安静的技术控 阅读数:26002 版权声明:本文为博主原创文章,未经博主允许不得转载. http ...
- 【Spring MVC】Properties文件的加载
[Spring MVC]Properties文件的加载 转载:https://www.cnblogs.com/yangchongxing/p/10726885.html 参考:https://java ...
- 【朝花夕拾】Android多线程之(三)runOnUiThread篇——程序猿们的贴心小棉袄
runOnUiThread()的使用以及原理实在是太简单了,简单到笔者开始都懒得单独开一篇文章来写它.当然这里说的简单,是针对对Handler比较熟悉的童鞋而言的.不过麻雀虽小,五脏俱全,runOnU ...
