hdu 4119 Isabella's Message
Isabella's Message
Time Limit: 2000/1000 MS (Java/Others) Memory Limit: 32768/32768 K (Java/Others)
Total Submission(s): 1365 Accepted Submission(s): 400
The encrypted message is an N * N matrix, and each grid contains a character.
Steve uses a special mask to work as a key. The mask is N * N(where N is an even number) matrix with N*N/4 holes of size 1 * 1 on it.
The decrypt process consist of the following steps:
1. Put the mask on the encrypted message matrix
2. Write down the characters you can see through the holes, from top to down, then from left to right.
3. Rotate the mask by 90 degrees clockwise.
4. Go to step 2, unless you have wrote down all the N*N characters in the message matrix.
5. Erase all the redundant white spaces in the message.
For example, you got a message shown in figure 1, and you have a mask looks like figure 2. The decryption process is shown in figure 3, and finally you may get a message "good morning".
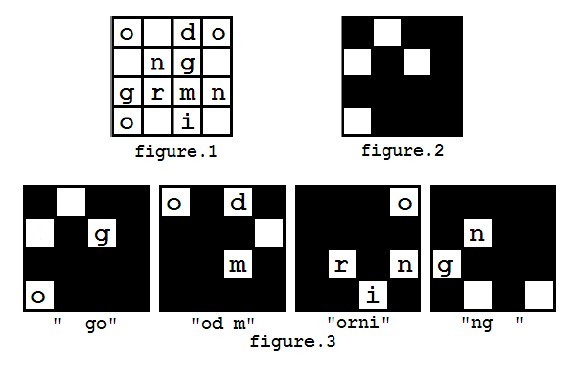
You can assume that the mask is always carefully chosen that each character in the encrypted message will appear exactly once during decryption.
However, in the first step of decryption, there are several ways to put the mask on the message matrix, because the mask can be rotated (but not flipped). So you may get different results such as "od morning go" (as showed in figure 4), and you may also get other messages like "orning good m", "ng good morni".
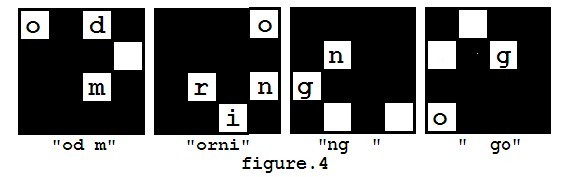
Steve didn't know which direction of the mask should be chosen at the beginning, but after he tried all possibilities, he found that the message "good morning" is the only one he wanted because he couldn't recognize some words in the other messages. So he will always consider the message he can understand the correct one. Whether he can understand a message depends whether he knows all the words in the message. If there are more than one ways to decrypt the message into an understandable one, he will choose the lexicographically smallest one. The way to compare two messages is to compare the words of two messages one by one, and the first pair of different words in the two messages will determine the lexicographic order of them.
Isabella sends letters to Steve almost every day. As decrypting Isabella's message takes a lot of time, and Steve can wait no longer to know the content of the message, he asked you for help. Now you are given the message he received, the mask, and the list of words he already knew, can you write a program to help him decrypt it?
Each test case contains several lines.
The first line contains an even integer N(2 <= N <= 50), indicating the size of the matrix.
The following N lines each contains exactly N characters, reresenting the message matrix. The message only contains lowercase letters and periods('.'), where periods represent the white spaces.
You can assume the matrix contains at least one letter.
The followingN lines each containsN characters, representing the mask matrix. The asterisk('*') represents a hole, and period('.') otherwise. The next line contains an integer M(1 <= M <= 100), the number of words he knew.
Then the following M lines each contains a string represents a word. The words only contain lowercase letters, and its length will not exceed 20.
If Steve cannot understand the message, just print the Y as "FAIL TO DECRYPT".
4
o.do
.ng.
grmn
o.i.
.*..
*.*.
....
*...
2
good
morning
4
..lf
eoyv
oeou
vrer
..*.
.*..
....
*.*.
5
i
you
the
love
forever
4
.sle
s.c.
e.fs
..uu
*...
.*..
...*
..*.
1
successful
Case #2: love you forever
Case #3: FAIL TO DECRYPT
#include <iostream>
#include <stdio.h>
#include <string.h>
using namespace std;
#define MAXN 55
struct node {
char map[MAXN][MAXN];
};
int n,kk;char str[4][10000],lib[10000][25],anss[10000],stemp[10000];int strnum[4];
bool strflag[4];
node change(node a)
{
int i,j,ii,k;node b;
for(i=0,ii=0;i<n;i++,ii++)
{
for(j=n-1,k=0;j>=0;j--,k++)
{
b.map[ii][k]=a.map[j][i];
}
}
return b;
}
bool find(char str[])
{
int i;
for(i=0;i<kk;i++)
{
if(strcmp(str,lib[i])==0)
return true;
}
return false;
}
int main()
{
int tcase,i,j,i2,space,tt=1;
node a,b;
scanf("%d",&tcase);
while(tcase--)
{
memset(strnum,0,sizeof(strnum));
memset(strflag,true,sizeof(strflag));
for(i=0;i<4;i++)
{
memset(str[i],0,sizeof(str[i]));
}
scanf("%d",&n);
gets(stemp);
for(i=0;i<n;i++)
{
for(j=0;j<n;j++)
{
char c=getchar();
a.map[i][j]=c;
}
gets(stemp);
}
for(i=0;i<n;i++)
{
for(j=0;j<n;j++)
{
char c=getchar();
b.map[i][j]=c;
}
gets(stemp);
}
scanf("%d",&kk);
gets(stemp);
for(i=0;i<kk;i++)
{
scanf("%s",lib[i]);
}
memset(stemp,0,sizeof(stemp));
int space=0;node primeb=b;
for(i=0;i<4;i++)
{
bool flag=true;space=0;b=primeb;
for(j=0;j<4&&flag;j++)
{
for(int ii=0;ii<n&&flag;ii++)
for(int jj=0;jj<n&&flag;jj++)
{
if(b.map[ii][jj]=='*')
{
if(a.map[ii][jj]=='.'&&space>0)
{
stemp[space++]='\0';
if(!find(stemp))
{
flag=false;
strflag[i]=false;
}
else
{
str[i][strnum[i]++]=' ';
for(i2=0;i2<=space-2;i2++)
{
str[i][strnum[i]++]=stemp[i2];
}
}
space=0;
}
if(a.map[ii][jj]!='.')
{
stemp[space++]=a.map[ii][jj];
}
}
} b=change(b);
}
if(space>0&&flag)
{
stemp[space++]='\0';
if(!find(stemp))
{
flag=false;
strflag[i]=false;
}
else
{
str[i][strnum[i]++]=' ';
for(i2=0;i2<=space-2;i2++)
{
str[i][strnum[i]++]=stemp[i2];
}
}
space=0;
}
primeb=change(primeb);
}
bool flag=true;
for(i=0;i<4;i++)
{
if(strflag[i])
{
str[i][strnum[i]++]='\0';
if(flag)
{
strcpy(anss,str[i]);
flag=false;
}
if(strcmp(anss,str[i])>0)
strcpy(anss,str[i]);
}
}
if(!flag)
printf("Case #%d:%s\n",tt++,anss);
else
printf("Case #%d: FAIL TO DECRYPT\n",tt++);
}
return 0;
}
hdu 4119 Isabella's Message的更多相关文章
- hdu 4119 Isabella's Message 模拟题
Isabella's Message Time Limit: 20 Sec Memory Limit: 256 MB 题目连接 http://acm.hdu.edu.cn/showproblem.p ...
- hdu 3410 Passing the Message(单调队列)
题目链接:hdu 3410 Passing the Message 题意: 说那么多,其实就是对于每个a[i],让你找他的从左边(右边)开始找a[j]<a[i]并且a[j]=max(a[j])( ...
- hdu 4300 Clairewd’s message KMP应用
Clairewd’s message 题意:先一个转换表S,表示第i个拉丁字母转换为s[i],即a -> s[1];(a为明文,s[i]为密文).之后给你一串长度为n<= 100000的前 ...
- hdu 4300 Clairewd’s message(具体解释,扩展KMP)
题目链接:http://acm.hdu.edu.cn/showproblem.php?pid=4300 Problem Description Clairewd is a member of FBI. ...
- hdu 4300 Clairewd’s message(扩展kmp)
Problem Description Clairewd is a member of FBI. After several years concealing in BUPT, she interce ...
- HDU 4300 Clairewd’s message(KMP+思维)
题目链接:http://acm.hdu.edu.cn/showproblem.php?pid=4300 题目大意:题目大意就是给以一段字符xxxxzzz前面x部分是密文z部分是明文,但是我们不知道是从 ...
- 【HDU 4300 Clairewd’s message】
Clairewd is a member of FBI. After several years concealing in BUPT, she intercepted some important ...
- HDU - 3410 Passing the Message 单调递减栈
Passing the Message What a sunny day! Let’s go picnic and have barbecue! Today, all kids in “Sun Flo ...
- hdu 4300 Clairewd’s message 字符串哈希
Clairewd’s message Time Limit: 2000/1000 MS (Java/Others) Memory Limit: 32768/32768 K (Java/Other ...
随机推荐
- 在centos6.5下yum仓库的创建
第一步:打开虚拟机,装入光盘镜像,选择为已连接 第二步: df -h mount umount /dev/sr0 mkdir /centos mount /dev/sr0 /centos mkdir ...
- R与数据分析旧笔记(五)数学分析基本
R语言的各种分布函数 rnorm(n,mean=0,sd=1)#高斯(正态) rexp(n,rate=1)#指数 rgamma(n,shape,scale=1)#γ分布 rpois(n,lambda) ...
- codeforces 589F. Gourmet and Banquet 二分+网络流
题目链接 给你n种菜, 每一种可以开始吃的时间不一样, 结束的时间也不一样. 求每种菜吃的时间都相同的最大的时间.时间的范围是0-10000. 看到这个题明显可以想到网络流, 但是时间的范围明显不允许 ...
- 四轴飞行器1.7 NRF24L01P无线通讯和改进型环形缓冲
原创文章,欢迎转载,转载请注明出处 这次花了10多天了才再次写blog,一是中秋优点小活动,二是这次完成了不少东西.. 终于接近完成了,这次完成了NRF的通讯,并且用了改进的环形缓冲和简单的通讯协议规 ...
- 解析Tensorflow官方PTB模型的demo
RNN 模型作为一个可以学习时间序列的模型被认为是深度学习中比较重要的一类模型.在Tensorflow的官方教程中,有两个与之相关的模型被实现出来.第一个模型是围绕着Zaremba的论文Recurre ...
- 注册表与盘符(转victor888文章 )
转自: http://blog.csdn.net/loulou_ff/article/details/3769479 写点东西,把这阶段的研究内容记录下来,同时也给研究相关内容的同志提供参考, ...
- 一步一步学习SignalR进行实时通信_2_Persistent Connections
原文:一步一步学习SignalR进行实时通信_2_Persistent Connections 一步一步学习SignalR进行实时通信\_2_Persistent Connections Signal ...
- ecshop删除商品函数
/** * 从回收站删除多个商品 * @param mix $goods_id 商品id列表:可以逗号格开,也可以是数组 * @return void */ function delete_goods ...
- 非线性规划问题的matlab求解
函数:[x, fval] = fmincon(FUN, X0, A, B, Aeq, Beq, LB, UB, NONLCON) 返回的x:是一个向量——在取得目标函数最小时各个xi的取值: 返回的f ...
- HDU2159:FATE(二维完全背包)
Problem Description 最近xhd正在玩一款叫做FATE的游戏,为了得到极品装备,xhd在不停的杀怪做任务.久而久之xhd开始对杀怪产生的厌恶感,但又不得不通过杀怪来升完这最后一级.现 ...
