Lab 3-3
Execute the malware found in the file Lab03-03.exe while monitoring it using basic dynamic analysis tools in a safe environment.
Questions and Short Answers
What do you notice when monitoring this malware with Process Explorer?
A: The malware performs process replacement on svchost.exe.
Can you identify any live memory modifications?
A: Comparing the disk image of svchost.exe with its memory image shows that they are not the same. The memory image has strings such as practicalmalwareanalysis.log and [ENTER], but the disk image has neither.
What are the malware’s host-based indicators?
A: The malware creates the log file practicalmalwareanalysis.log.
What is the purpose of this program?
A: The program performs process replacement on svchost.exe to launch
a keylogger.
Detailed Analysis
For this lab, we begin by launching Process Explorer and procmon. When procmon starts, the events stream by quickly, so we use File -> Capture Events to toggle event capture on and off. (It’s best to keep event capture off until all dynamic analysis programs are started and you’re ready to execute the program.) We use Filter -> Filter to open the Filter dialog, and then ensure that only the default filters are enabled by clicking the Reset button.
Lab03-03.exe can be run from the command prompt or by double-clicking its icon. Once run, Lab03-03.exe should be visible inside Process Explorer. Notice how it creates the subprocess svchost.exe, and then exits, but leaves the svchost.exe process running as an orphaned process, as shown in Figure 3-8L. (An orphaned process has no parent process listed in the process tree structure.) The fact that svchost.exe is orphaned is highly unusual and highly suspicious.
Process Explorer 在 Lab03-03.exe 运行前中后的状态如下图:

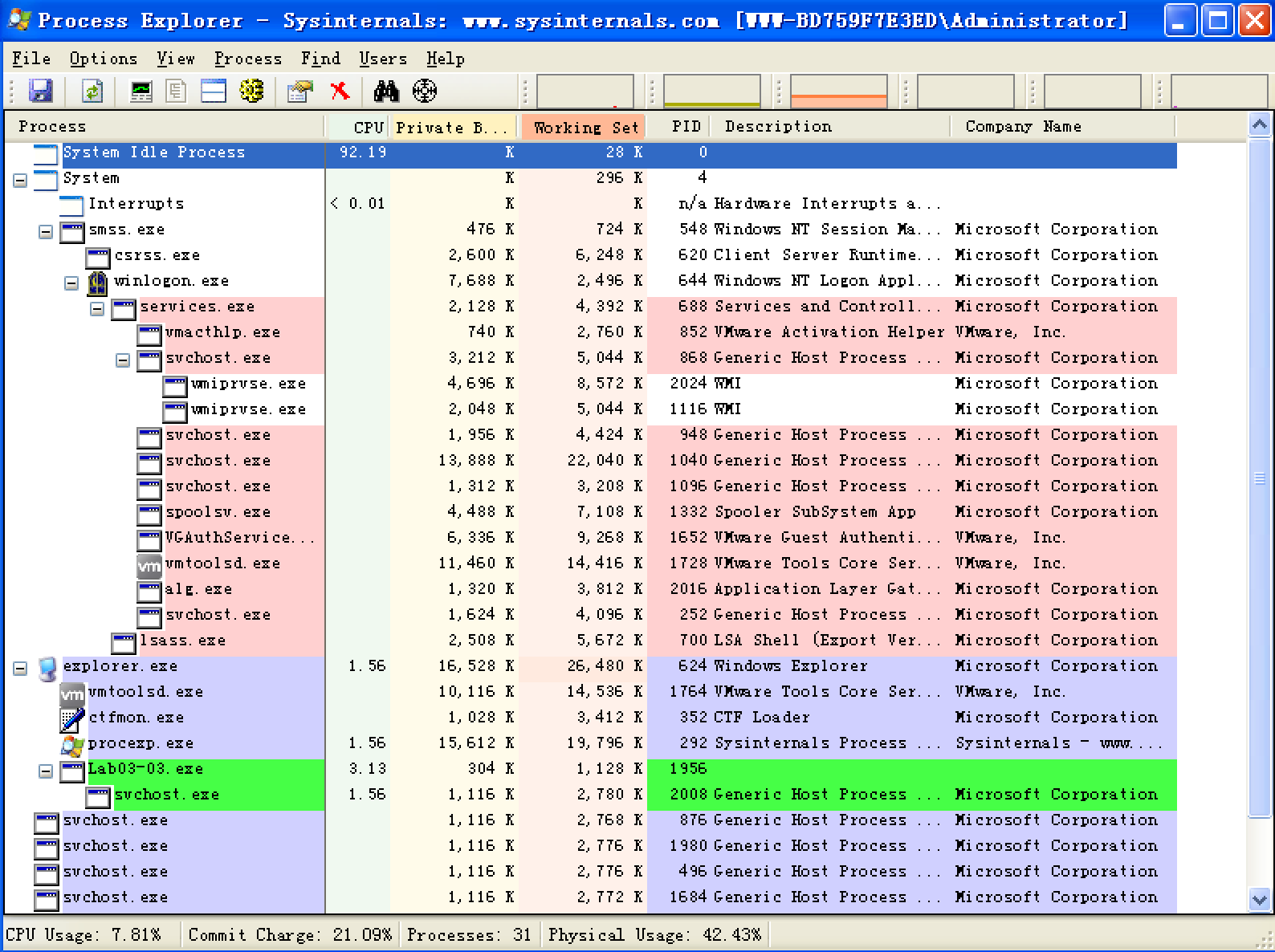
注:此图是我运行了很多遍,拼手速截的,故进程 PID 会有出入。
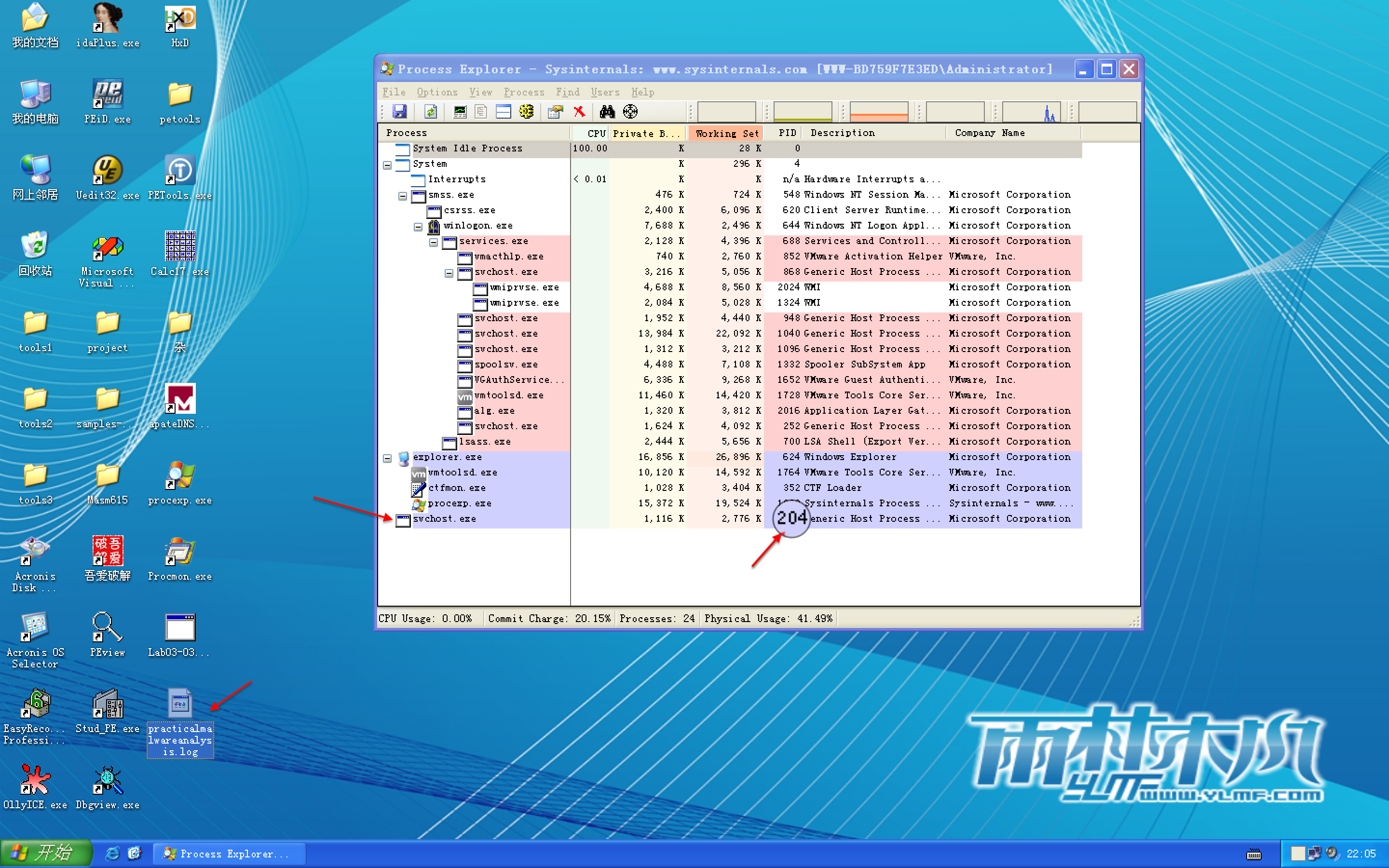
Figure 3-8L: Process Explorer view of orphaned svchost.exe

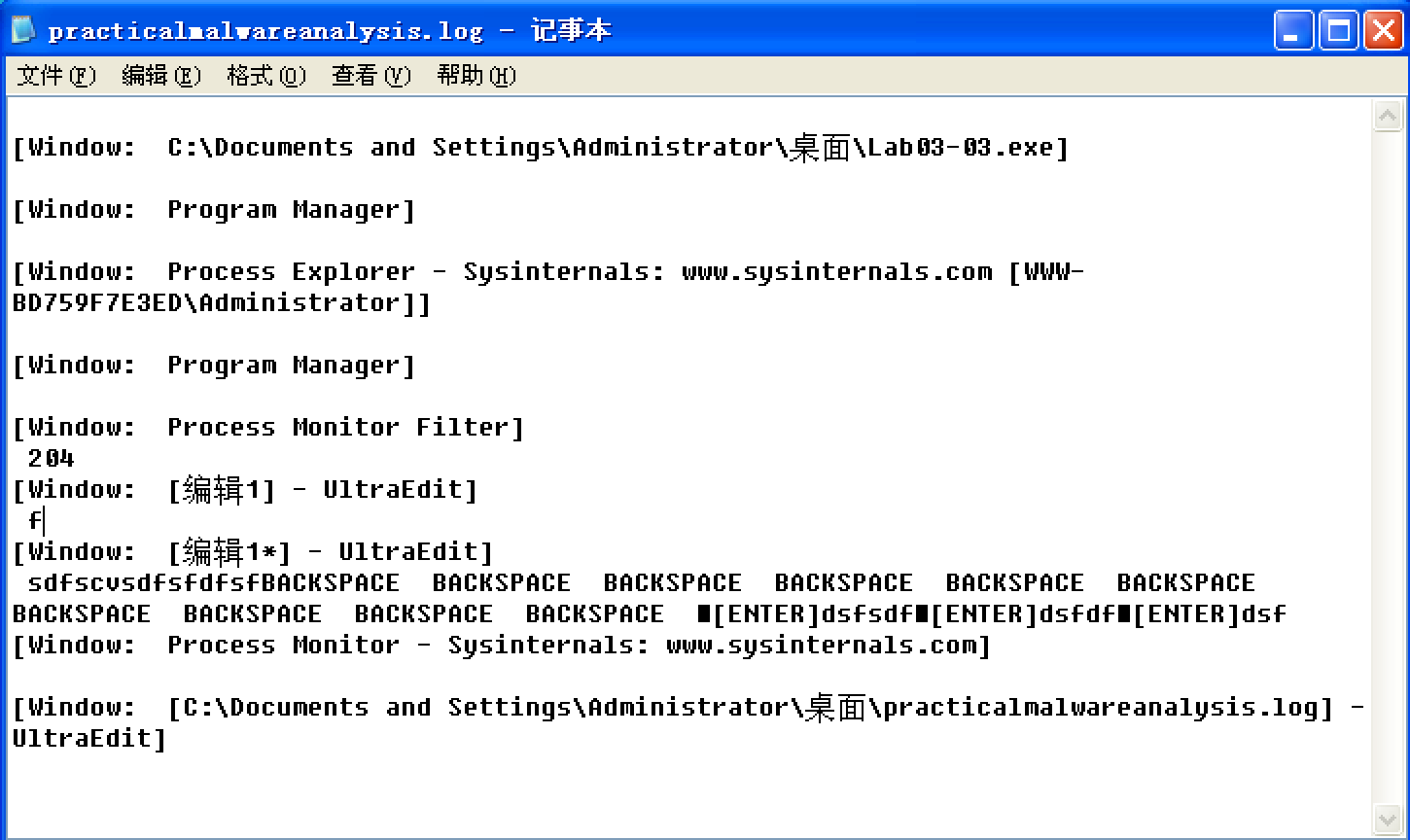
We investigate further by right-clicking and selecting Properties for the orphaned svchost.exe process. As shown in Figure 3-8L, the process appears to be a valid svchost.exe process with PID 204, but this svchost.exe is suspicious because svchost.exe is typically a child of services.exe.

From this same properties page, we select Strings to show the strings in both the executable image on disk and in memory. Toggling between the Image and Memory radio buttons shows significant discrepancies between the images. As shown in Figure 3-9L, the strings in memory on the right contain practicalmalwareanalysis.log and [ENTER], seen at \({\color{red}1}\) and \({\color{red}2}\), neither of which is found in a typical Windows svchost.exe file on disk, as seen on the left.

Figure 3-9L: Process Explorer shows strings that are not normally contained in svchost.exe.
The presence of the string practicalmalwareanalysis.log, coupled with strings like [ENTER] and [CAPS LOCK], suggests that this program is a keylogger. To test our assumption, we open Notepad and type a short message to see if the malware will perform keylogging. To do so, we use the PID (found in Process Explorer) for the orphaned svchost.exe to create a filter in procmon to show only events from that PID (204). As you can see in Figure 3-10L, the CreateFile and WriteFile events for svchost.exe are writing to the file named practicalmalwareanalysis.log. (This same string is visible in the memory view of the orphaned svchost.exe process.)
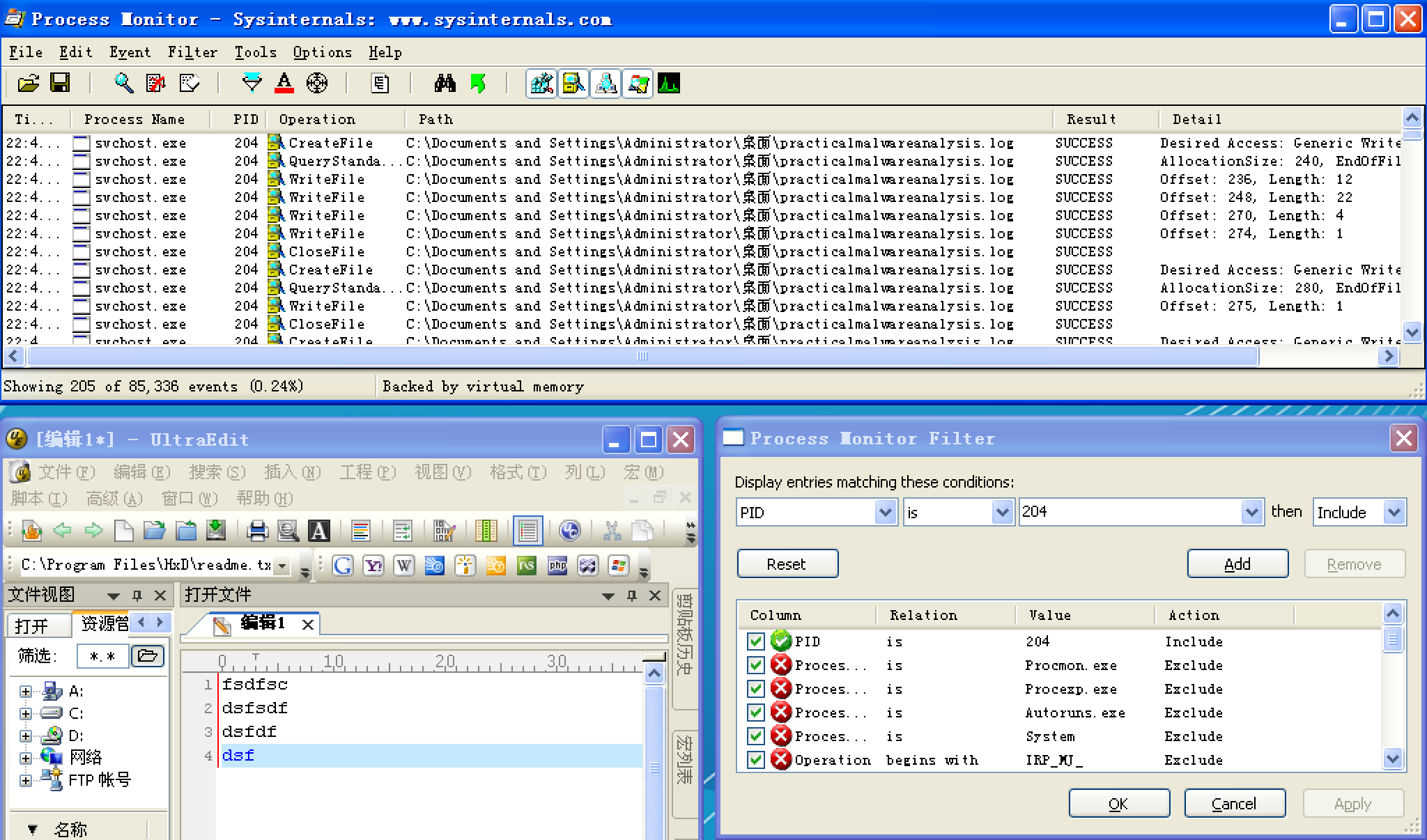
Figure 3-10L: Procmon output of svchost.exe with PID 204
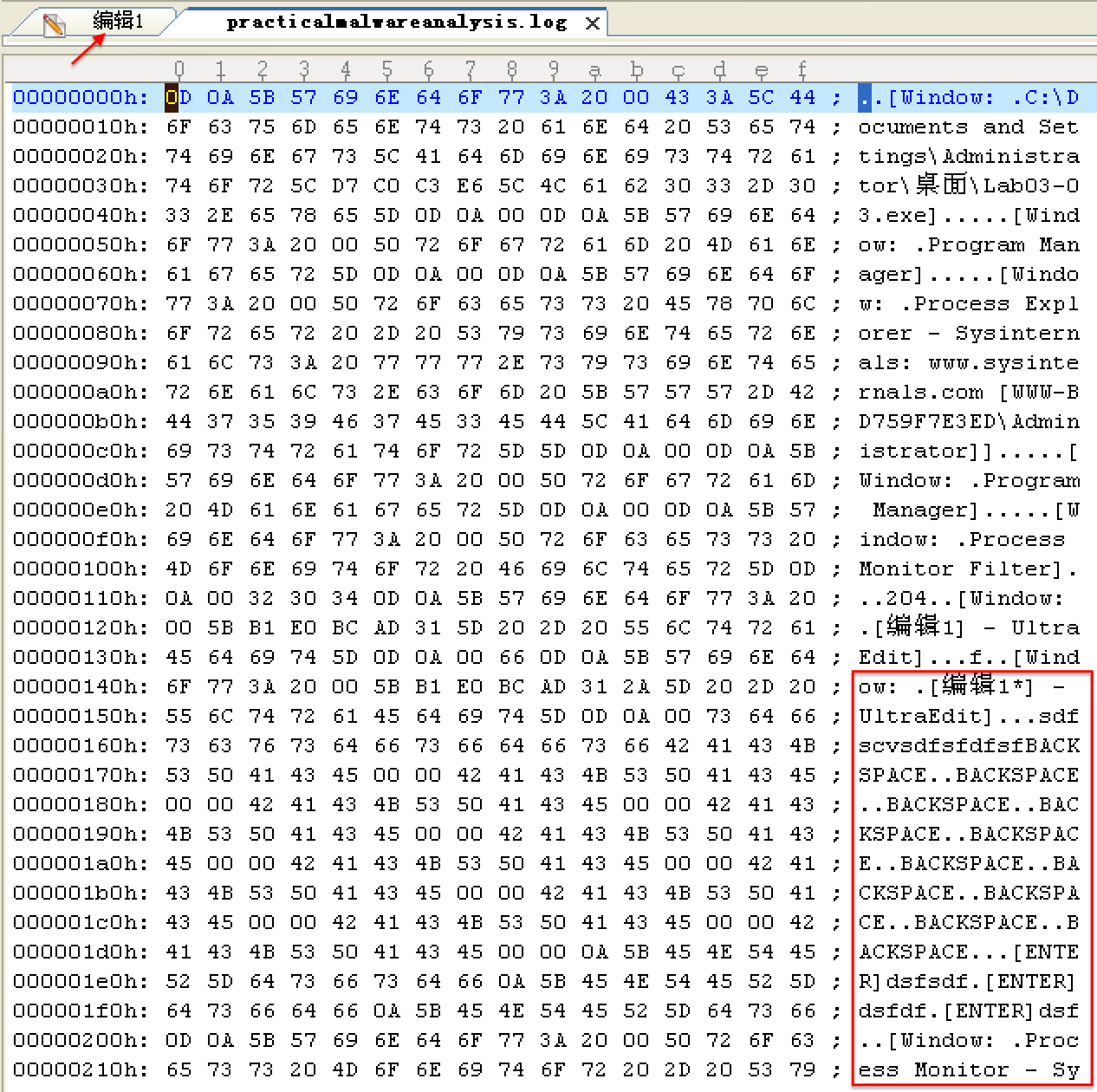
Opening practicalmalwareanalysis.log with a simple text editor reveals the keystrokes you entered in Notepad. We conclude that this malware is a keylogger that uses process replacement on svchost.exe.
Preference
Lab 3-3的更多相关文章
- MIT 6.828 JOS学习笔记18. Lab 3.2 Part B: Page Faults, Breakpoints Exceptions, and System Calls
现在你的操作系统内核已经具备一定的异常处理能力了,在这部分实验中,我们将会进一步完善它,使它能够处理不同类型的中断/异常. Handling Page Fault 缺页中断是一个非常重要的中断,因为我 ...
- MIT 6.828 JOS学习笔记17. Lab 3.1 Part A User Environments
Introduction 在这个实验中,我们将实现操作系统的一些基本功能,来实现用户环境下的进程的正常运行.你将会加强JOS内核的功能,为它增添一些重要的数据结构,用来记录用户进程环境的一些信息:创建 ...
- MIT 6.828 JOS学习笔记16. Lab 2.2
Part 3 Kernel Address Space JOS把32位线性地址虚拟空间划分成两个部分.其中用户环境(进程运行环境)通常占据低地址的那部分,叫用户地址空间.而操作系统内核总是占据高地址的 ...
- MIT 6.828 JOS学习笔记15. Lab 2.1
Lab 2: Memory Management lab2中多出来的几个文件: inc/memlayout.h kern/pmap.c kern/pmap.h kern/kclock.h kern/k ...
- MIT 6.828 JOS学习笔记10. Lab 1 Part 3: The kernel
Lab 1 Part 3: The kernel 现在我们将开始具体讨论一下JOS内核了.就像boot loader一样,内核开始的时候也是一些汇编语句,用于设置一些东西,来保证C语言的程序能够正确的 ...
- MIT 6.828 JOS学习笔记7. Lab 1 Part 2.2: The Boot Loader
Lab 1 Part 2 The Boot Loader Loading the Kernel 我们现在可以进一步的讨论一下boot loader中的C语言的部分,即boot/main.c.但是在我们 ...
- python opencv 利用Lab空间把春天的场景改为秋天
前一段时间实现了Reinhard颜色迁移算法,感觉挺有意思的,然后在代码上随意做了一些更改,有了一些发现,把Lab通道的a通道值改为127左右,可以将绿色改为黄色,而对其他颜色的改动非常小,因此可以将 ...
- Acadia Lab 228 + Lab 222
又是一对串烧实验,布好线后非常方便就可以一起完成. 连线方案一模一样: Lab 228 数码管骰子 核心代码如下: def loop() : global cnt global btn_read,se ...
- Acadia Lab 203 + Lab 231
在做完 Lab 6 之后,惊觉选做实验缺口很大,于是遍历了一遍夏任务,找到了一条最省力的路线. 做完 Lab 6 的连线不用拆,可以接下来做以下两个实验: Lab 203 网络时钟 核心代码如下: v ...
- GJM : 【技术干货】给The Lab Renderer for Unity中地形添加阴影
感谢您的阅读.喜欢的.有用的就请大哥大嫂们高抬贵手"推荐一下"吧!你的精神支持是博主强大的写作动力以及转载收藏动力.欢迎转载! 版权声明:本文原创发表于 [请点击连接前往] ,未经 ...
随机推荐
- centos7之安装wordpress
wordpress安装教程如下: mysql安装可以参考我的博客园Centos构建Java环境:https://www.cnblogs.com/youcong/p/9118753.html 1.安装a ...
- Oracle使用——Oracle表空间处理
创建表空间 查看表空间信息(名称.大小) select t1.name tablespace_name ,t2.name file_local ,t2.bytes / (1024 * 1024) f ...
- shell脚本中如何实现scp传输?
示例脚本如下: #! /bin/sh expect -c " spawn scp -r /home/jello/jello.txt jello@110.110.110.110:/home/j ...
- 【做题】CF1045(ABH)
原文链接https://www.cnblogs.com/cly-none/p/9697662.html 题目当然不会做完了,这里只讲有做&会做的. A. Last chance 题意:有\(n ...
- AtCoder Beginner Contest 117 解题报告
果然abc都是手速场. 倒序开的qwq. D题因为忘记1e12二进制几位上界爆了一发. A - Entrance Examination 就是除一下就行了... 看样例猜题意系列. #include& ...
- P4450 双亲数
思路 同zap-queries 莫比乌斯反演的板子 数据范围小到不用整除分块... 代码 #include <cstdio> #include <algorithm> #inc ...
- p3396 哈希冲突(暴力)
想了好久,没想到优秀的解法,结果是个暴力大吃一静.jpg 分类讨论,预处理\(p\le \sqrt{n}\) 的情况,其他直接暴力,复杂度\(O(n \sqrt{n} )\) #include < ...
- UVA 10870 Recurrences(矩阵乘法)
题意 求解递推式 \(f(n)=a_1*f(n-1)+a_2*f(n-2)+....+a_d*f(n-d)\) 的第 \(n\) 项模以 \(m\). \(1 \leq n \leq 2^{31}-1 ...
- ISE14.7兼容性问题集锦https://www.cnblogs.com/ninghechuan/p/7241371.html
ISE14.7兼容性问题集锦 对于电子工程师来说,很多电路设计仿真软件都是特别大的,安装下来一般都是上G,甚至几十G,而且win7的兼容性也是最好的,不愿意升级win10是因为麻烦,而且没有必要,对于 ...
- SNMOJ 31
考虑将给入的$A$数组差分,得到差分数组$C$ 每一次操作相当于把差分数组的每一位${+1}$,其中一个位置上${-n+1}$. 我们可以直接算出要进行多少次操作:${T=\frac{\sum A[i ...
