Spring boot security权限管理集成cas单点登录
挣扎了两周,Spring security的cas终于搞出来了,废话不多说,开篇!
- Spring boot集成Spring security
本篇是使用spring security集成cas,因此,先得集成spring security
新建一个Spring boot项目,加入maven依赖,我这里是用的架构是Spring boot2.0.4+Spring mvc+Spring data jpa+Spring security5
pom.xml:<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion> <groupId>com.cas.client1</groupId>
<artifactId>cas-client1</artifactId>
<version>0.0.1-SNAPSHOT</version>
<packaging>jar</packaging> <name>cas-client1</name>
<description>Demo project for Spring Boot</description> <parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.0.4.RELEASE</version>
<relativePath/> <!-- lookup parent from repository -->
</parent> <properties>
<project.build.sourceEncoding>UTF-8</project.build.sourceEncoding>
<project.reporting.outputEncoding>UTF-8</project.reporting.outputEncoding>
<java.version>1.8</java.version>
</properties> <dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-thymeleaf</artifactId>
</dependency> <dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-tomcat</artifactId>
<scope>provided</scope>
</dependency>
<dependency>
<groupId>junit</groupId>
<artifactId>junit</artifactId>
<version>4.12</version>
<scope>test</scope>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-test</artifactId>
<scope>test</scope>
</dependency>
<!-- security taglibs -->
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-taglibs</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.security.oauth</groupId>
<artifactId>spring-security-oauth2</artifactId>
<version>RELEASE</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-data-jpa</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-jdbc</artifactId>
</dependency>
<dependency>
<groupId>mysql</groupId>
<artifactId>mysql-connector-java</artifactId>
<version>5.1.46</version>
</dependency>
<!-- https://mvnrepository.com/artifact/com.alibaba/druid-spring-boot-starter -->
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>druid-spring-boot-starter</artifactId>
<version>1.1.10</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot</artifactId>
<version>2.0.2.RELEASE</version>
<scope>compile</scope>
</dependency>
</dependencies> <build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build> </project>application.properties:
server.port=8083
#静态文件访问存放地址
spring.resources.static-locations=classpath:/html/
# thymeleaf 模板存放地址
spring.thymeleaf.prefix=classpath:/html/
spring.thymeleaf.suffix=.html
spring.thymeleaf.mode=LEGACYHTML5
spring.thymeleaf.encoding=UTF-8 # JDBC 配置(驱动类自动从url的mysql识别,数据源类型自动识别)
# 或spring.datasource.url=
spring.datasource.druid.url=jdbc:mysql://localhost:3306/vhr?useUnicode=true&characterEncoding=UTF8
# 或spring.datasource.username=
spring.datasource.druid.username=root
# 或spring.datasource.password=
spring.datasource.druid.password=1234
#或 spring.datasource.driver-class-name=
#spring.datasource.druid.driver-class-name=com.mysql.jdbc.Driver #连接池配置(通常来说,只需要修改initialSize、minIdle、maxActive
# 如果用Oracle,则把poolPreparedStatements配置为true,mysql可以配置为false。分库分表较多的数据库,建议配置为false。removeabandoned不建议在生产环境中打开如果用SQL Server,建议追加配置)
spring.datasource.druid.initial-size=1
spring.datasource.druid.max-active=20
spring.datasource.druid.min-idle=1
# 配置获取连接等待超时的时间
spring.datasource.druid.max-wait=60000
#打开PSCache,并且指定每个连接上PSCache的大小
spring.datasource.druid.pool-prepared-statements=true
spring.datasource.druid.max-pool-prepared-statement-per-connection-size=20
#spring.datasource.druid.max-open-prepared-statements=和上面的等价
spring.datasource.druid.validation-query=SELECT 'x'
#spring.datasource.druid.validation-query-timeout=
spring.datasource.druid.test-on-borrow=false
spring.datasource.druid.test-on-return=false
spring.datasource.druid.test-while-idle=true
#配置间隔多久才进行一次检测,检测需要关闭的空闲连接,单位是毫秒
spring.datasource.druid.time-between-eviction-runs-millis=60000
#配置一个连接在池中最小生存的时间,单位是毫秒
spring.datasource.druid.min-evictable-idle-time-millis=300000
#spring.datasource.druid.max-evictable-idle-time-millis=
#配置多个英文逗号分隔
#spring.datasource.druid.filters= stat # WebStatFilter配置,说明请参考Druid Wiki,配置_配置WebStatFilter
#是否启用StatFilter默认值true
spring.datasource.druid.web-stat-filter.enabled=true
spring.datasource.druid.web-stat-filter.url-pattern=/*
spring.datasource.druid.web-stat-filter.exclusions=*.js,*.gif,*.jpg,*.png,*.css,*.ico,/druid/*
spring.datasource.druid.web-stat-filter.session-stat-enable=false
spring.datasource.druid.web-stat-filter.session-stat-max-count=1000
spring.datasource.druid.web-stat-filter.principal-session-name=admin
spring.datasource.druid.web-stat-filter.principal-cookie-name=admin
spring.datasource.druid.web-stat-filter.profile-enable=true # StatViewServlet配置
#展示Druid的统计信息,StatViewServlet的用途包括:1.提供监控信息展示的html页面2.提供监控信息的JSON API
#是否启用StatViewServlet默认值true
spring.datasource.druid.stat-view-servlet.enabled=true
spring.datasource.druid.stat-view-servlet.url-pattern=/druid/* # JPA config
spring.jpa.database=mysql
spring.jpa.hibernate.ddl-auto=update
spring.jpa.show-sql=true
spring.jpa.generate-ddl=true
spring.jpa.properties.hibernate.dialect=org.hibernate.dialect.MySQL5Dialect
spring.jpa.open-in-view=true
# 解决jpa no session的问题
spring.jpa.properties.hibernate.enable_lazy_load_no_trans=true这里使用数据库存储角色权限信息,分三种实体:用户;角色;资源;用户对角色多对多;角色对资源多对多
创建几个实体类:
用户:这里直接使用用户持久化对象实现Spring security要求的UserDetails接口,并实现对应方法package com.cas.client1.entity; import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.util.CollectionUtils; import javax.persistence.*;
import java.util.ArrayList;
import java.util.Collection;
import java.util.List; @Entity
@Table(name = "s_user")
public class User implements UserDetails {
@Id
private String id;
@Column(name = "username")
private String username;
@Column(name = "password")
private String password; @ManyToMany(fetch = FetchType.LAZY)
@JoinTable(
name = "s_user_role",
joinColumns = @JoinColumn(name = "user_id"),
inverseJoinColumns = @JoinColumn(name = "role_id")
)
private List<Role> roles; public User() {
} public User(String id, String username, String password) {
this.id = id;
this.username = username;
this.password = password;
} public String getId() {
return id;
} public void setId(String id) {
this.id = id;
} public List<Role> getRoles() {
return roles;
} public void setRoles(List<Role> roles) {
this.roles = roles;
} @Override
public String getUsername() {
return username;
} @Override
public boolean isAccountNonExpired() {
return true;
} @Override
public boolean isAccountNonLocked() {
return true;
} @Override
public boolean isCredentialsNonExpired() {
return true;
} @Override
public boolean isEnabled() {
return true;
} public void setUsername(String username) {
this.username = username;
} @Transient
List<GrantedAuthority> grantedAuthorities=new ArrayList<>();
@Override
public Collection<? extends GrantedAuthority> getAuthorities() {
if (grantedAuthorities.size()==0){
if (!CollectionUtils.isEmpty(roles)){
for (Role role:roles){
List<Resource> resources = role.getResources();
if (!CollectionUtils.isEmpty(resources)){
for (Resource resource:resources){
grantedAuthorities.add(new SimpleGrantedAuthority(resource.getResCode()));
}
}
}
}
grantedAuthorities.add(new SimpleGrantedAuthority("AUTH_0"));
}
return grantedAuthorities;
}
@Override
public String getPassword() {
return password;
} public void setPassword(String password) {
this.password = password;
}
}注意看这里:
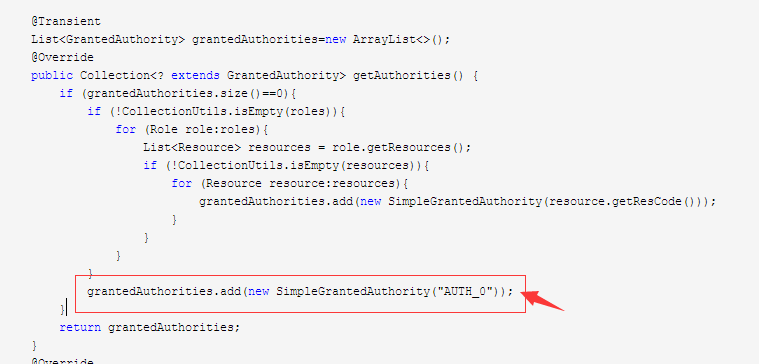
我给每一位登录的用户都授予了AUTH_0的权限,AUTH_0在下面的SecurityMetaDataSource里被关联的url为:/**,也就是说除开那些机密程度更高的,这个登录用户能访问所有资源
角色:
package com.cas.client1.entity; import javax.persistence.*;
import java.util.List; /**
* @author Administrator
*/
@Entity
@Table(name = "s_role")
public class Role {
@Id
@Column(name = "id")
private String id;
@Column(name = "role_name")
private String roleName; @ManyToMany(fetch = FetchType.LAZY)
@JoinTable(
name = "s_role_res",
joinColumns = @JoinColumn(name = "role_id"),
inverseJoinColumns = @JoinColumn(name = "res_id")
)
private List<Resource> resources;
@ManyToMany(fetch = FetchType.LAZY)
@JoinTable(
name = "s_user_role",
joinColumns = @JoinColumn(name = "role_id"),
inverseJoinColumns = @JoinColumn(name = "user_id")
)
private List<User> users; public String getId() {
return id;
} public void setId(String id) {
this.id = id;
} public String getRoleName() {
return roleName;
} public void setRoleName(String roleName) {
this.roleName = roleName;
} public List<Resource> getResources() {
return resources;
} public void setResources(List<Resource> resources) {
this.resources = resources;
} public List<User> getUsers() {
return users;
} public void setUsers(List<User> users) {
this.users = users;
}
}权限:
package com.cas.client1.entity; import javax.persistence.Column;
import javax.persistence.Entity;
import javax.persistence.Id;
import javax.persistence.Table; @Entity
@Table(name = "s_resource")
public class Resource {
@Id
@Column(name = "id")
private String id;
@Column(name = "res_name")
private String resName;
@Column(name = "res_code")
private String resCode;
@Column(name = "url")
private String url;
@Column(name = "priority")
private String priority; public String getId() {
return id;
} public void setId(String id) {
this.id = id;
} public String getResName() {
return resName;
} public void setResName(String resName) {
this.resName = resName;
} public String getResCode() {
return resCode;
} public void setResCode(String resCode) {
this.resCode = resCode;
} public String getUrl() {
return url;
} public void setUrl(String url) {
this.url = url;
} public String getPriority() {
return priority;
} public void setPriority(String priority) {
this.priority = priority;
}
}建立几个DAO
UserDao:package com.cas.client1.dao; import com.cas.client1.entity.User;
import org.springframework.data.jpa.repository.JpaRepository;
import org.springframework.data.jpa.repository.Query;
import org.springframework.data.repository.query.Param;
import org.springframework.stereotype.Repository; import java.util.List; @Repository
public interface UserDao extends JpaRepository<User,String> {
@Override
List<User> findAll(); List<User> findByUsername(String username); /**
* 根据用户名like查询
* @param username
* @return
*/
List<User> getUserByUsernameContains(String username); @Query("from User where id=:id")
User getUserById(@Param("id") String id); }ResourceDao:
package com.cas.client1.dao; import com.cas.client1.entity.Resource;
import org.springframework.data.jpa.repository.JpaRepository;
import org.springframework.data.jpa.repository.Query;
import org.springframework.stereotype.Repository; import java.util.List; /**
* @author Administrator
*/
@Repository
public interface ResourceDao extends JpaRepository<Resource,String> { @Query("from Resource order by priority")
List<Resource> getAllResource();
}Service
UserService:package com.cas.client1.service; import com.cas.client1.dao.UserDao;
import com.cas.client1.entity.User;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.stereotype.Service; import java.util.List; @Service
public class UserService {
@Autowired
private UserDao userDao; public User findByUsername(String username){
List<User> list = userDao.findByUsername(username);
return list!=null&&list.size()>0?list.get(0):null;
}
}ResourceService:
package com.cas.client1.service; import com.cas.client1.dao.ResourceDao;
import com.cas.client1.entity.Resource;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.stereotype.Service; import java.util.List; @Service
public class ResourceService {
@Autowired
private ResourceDao resourceDao; public List<Resource> getAll(){
return resourceDao.getAllResource();
}
}创建UserDetailsServiceImpl,实现UserDetailsService接口,这个类是用以提供给Spring security从数据库加载用户信息的
package com.cas.client1.security; import com.cas.client1.entity.User;
import com.cas.client1.service.UserService;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.cas.authentication.CasAssertionAuthenticationToken;
import org.springframework.security.core.userdetails.AuthenticationUserDetailsService;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.core.userdetails.UsernameNotFoundException;
import org.springframework.stereotype.Component; /**
* @author Administrator
*/
@SuppressWarnings("ALL")
@Component
public class UserDetailsServiceImpl implements UserDetailsService{
@Autowired
private UserService userService;
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
User user = userService.findByUsername(username);
return user;
} }记得加@Component注解,以把实例交由Spring管理,或@Service,你们喜欢就好 创建SecurityMetaDataSource类
该类实现Spring security的FilterInvocationSecurityMetadataSource接口,作用是提供权限的元数据定义,并根据请求url匹配该url所需要的权限,获取权限后交由AccessDecisionManager的实现者裁定能否访问这个url,不能则会返回403的http错误码
SecurityMetaDataSource:package com.cas.client1.security; import com.cas.client1.entity.Resource;
import com.cas.client1.service.ResourceService;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.access.AccessDecisionManager;
import org.springframework.security.access.ConfigAttribute;
import org.springframework.security.access.SecurityConfig;
import org.springframework.security.access.intercept.AbstractSecurityInterceptor;
import org.springframework.security.web.FilterInvocation;
import org.springframework.security.web.access.intercept.FilterInvocationSecurityMetadataSource;
import org.springframework.security.web.util.matcher.AndRequestMatcher;
import org.springframework.security.web.util.matcher.AntPathRequestMatcher;
import org.springframework.security.web.util.matcher.RequestMatcher;
import org.springframework.stereotype.Component; import javax.annotation.PostConstruct;
import java.util.*; @Component
public class SecurityMetaDataSource implements FilterInvocationSecurityMetadataSource { @Autowired
private ResourceService resourceService; private LinkedHashMap<String,Collection<ConfigAttribute>> metaData;
@PostConstruct
private void loadSecurityMetaData(){
List<Resource> list = resourceService.getAll();
metaData=new LinkedHashMap<>();
for (Resource resource:list){
List<ConfigAttribute> attributes=new ArrayList<>();
attributes.add(new SecurityConfig(resource.getResCode()));
metaData.put(resource.getUrl(),attributes);
}
List<ConfigAttribute> base=new ArrayList<>();
base.add(new SecurityConfig("AUTH_0"));
metaData.put("/**",base);
} @Override
public Collection<ConfigAttribute> getAttributes(Object object) throws IllegalArgumentException {
FilterInvocation invocation= (FilterInvocation) object;
if (metaData==null){
return new ArrayList<>(0);
}
String requestUrl = invocation.getRequestUrl();
System.out.println("请求Url:"+requestUrl);
Iterator<Map.Entry<String, Collection<ConfigAttribute>>> iterator = metaData.entrySet().iterator();
Collection<ConfigAttribute> rs=new ArrayList<>();
while (iterator.hasNext()){
Map.Entry<String, Collection<ConfigAttribute>> next = iterator.next();
String url = next.getKey();
Collection<ConfigAttribute> value = next.getValue();
RequestMatcher requestMatcher=new AntPathRequestMatcher(url);
if (requestMatcher.matches(invocation.getRequest())){
rs = value;
break;
}
}
System.out.println("拦截认证权限为:"+rs);
return rs;
} @Override
public Collection<ConfigAttribute> getAllConfigAttributes() {
System.out.println("invoke getAllConfigAttributes ");
//loadSecurityMetaData();
//System.out.println("初始化元数据");
Collection<Collection<ConfigAttribute>> values = metaData.values();
Collection<ConfigAttribute> all=new ArrayList<>();
for (Collection<ConfigAttribute> each:values){
each.forEach(configAttribute -> {
all.add(configAttribute);
});
}
return all;
} @Override
public boolean supports(Class<?> clazz) {
return true;
}
}同理:记得加上@Component注解 重头戏来了!Spring security的配置
创建SpringSecurityConfig类
该类继承于WebSecurityConfigurerAdapter,核心的配置类,在这里定义Spring security的使用方式SpringSecurityConfig
package com.cas.client1.security; import com.cas.client1.config.CasProperties;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.access.AccessDecisionManager;
import org.springframework.security.access.AccessDecisionVoter;
import org.springframework.security.access.vote.AffirmativeBased;
import org.springframework.security.access.vote.RoleVoter;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.builders.WebSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.web.access.intercept.FilterSecurityInterceptor; import java.util.ArrayList;
import java.util.List; /**
* Spring security配置
* @author youyp
* @date 2018-8-10
*/
@SuppressWarnings("ALL")
@Configuration
@EnableWebSecurity
public class SpringSecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
private UserDetailsServiceImpl userDetailsService; @Autowired
private SecurityMetaDataSource securityMetaDataSource; @Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
super.configure(auth);
} @Override
public void configure(WebSecurity web) throws Exception {
web.ignoring().antMatchers("/js/**","/css/**","/img/**","/*.ico","/login.html",
"/error","/login.do");
} @Override
protected void configure(HttpSecurity http) throws Exception {
System.out.println("配置Spring security");
http.formLogin()
//指定登录页是”/login”
.loginPage("/login.html").permitAll()
.loginProcessingUrl("/login.do").permitAll()
.defaultSuccessUrl("/home",true)
.permitAll()
//登录成功后可使用loginSuccessHandler()存储用户信息,可选。
//.successHandler(loginSuccessHandler()).permitAll()
.and()
.logout().permitAll()
.invalidateHttpSession(true)
.and()
//登录后记住用户,下次自动登录,数据库中必须存在名为persistent_logins的表
.rememberMe()
.tokenValiditySeconds(1209600)
.and()
.csrf().disable()
//其他所有资源都需要认证,登陆后访问
.authorizeRequests().anyRequest().fullyAuthenticated(); http.addFilterBefore(filterSecurityInterceptor(),FilterSecurityInterceptor.class);
} /**
* 注意:这里不能加@Bean注解
* @return
* @throws Exception
*/
//@Bean
public FilterSecurityInterceptor filterSecurityInterceptor() throws Exception {
FilterSecurityInterceptor filterSecurityInterceptor=new FilterSecurityInterceptor();
filterSecurityInterceptor.setSecurityMetadataSource(securityMetaDataSource);
filterSecurityInterceptor.setAuthenticationManager(authenticationManager());
filterSecurityInterceptor.setAccessDecisionManager(affirmativeBased());
return filterSecurityInterceptor;
} /**
* 重写AuthenticationManager获取的方法并且定义为Bean
* @return
* @throws Exception
*/
@Override
@Bean
public AuthenticationManager authenticationManagerBean() throws Exception {
return super.authenticationManagerBean();
} @Autowired
public void configureGlobal(AuthenticationManagerBuilder auth) throws Exception {
//指定密码加密所使用的加密器为passwordEncoder()
//需要将密码加密后写入数据库
auth.userDetailsService(userDetailsService).passwordEncoder(passwordEncoder());
auth.eraseCredentials(false);
} @Bean
public BCryptPasswordEncoder passwordEncoder() { return new BCryptPasswordEncoder(4);
} /**
* 定义决策管理器,这里可直接使用内置的AffirmativeBased选举器,
* 如果需要,可自定义,继承AbstractAccessDecisionManager,实现decide方法即可
* @return
*/
@Bean
public AccessDecisionManager affirmativeBased(){
List<AccessDecisionVoter<? extends Object>> voters=new ArrayList<>();
voters.add(roleVoter());
System.out.println("正在创建决策管理器");
return new AffirmativeBased(voters);
} /**
* 定义选举器
* @return
*/
@Bean
public RoleVoter roleVoter(){
//这里使用角色选举器
RoleVoter voter=new RoleVoter();
System.out.println("正在创建选举器");
voter.setRolePrefix("AUTH_");
System.out.println("已将角色选举器的前缀修改为AUTH_");
return voter;
} }说一个注意点:
FilterSecurityInterceptor这个过滤器最为重要,它负责数据库权限信息加载,权限鉴定等关键动作,这个过滤器位于SpringSecurityFilterChain,即Spring security的过滤器链中,如果将这个类在配置类中加了@Bean注解,那么它将直接加入web容器的过滤器链中,这个链是首层过滤器链,
进入这个过滤器链之后才会进入SpringSecurityFilterChain这个负责安全的链条,如果这个跑到外层去了,就会导致这个独有的过滤器一直在生效,请求无限被拦截重定向,因为这个过滤器前面没有别的过滤器阻止它生效,如果它位于SpringSecurityFilterChain中,在进入FilterSecurityInterceptor这个
过滤器之前会有很多的Spring security过滤器在生效,如果不满足前面的过滤器的条件,不会进入到这个过滤器。也就是说,要进入到这个过滤器,必须要从SpringSecurityFilterChain进入,从其他地方进入都会导致请求被无限重定向 另外
FilterSecurityInterceptor这个类继承于AbstractSecurityInterceptor并实现Filter接口,由此我们可以重写该类,自定义我们的特殊业务,但是,个人觉得FilterSecurityInterceptor这个实现类已经很完整地实现了这个过滤器应做的工作,没有必要重写
类似的,还有AccessDecisionManager这个“决策者”,Spring security为这个功能提供了几个默认的实现者,如AffirmativeBased这个类,是一个基于投票的决策器,投票器(Voter)要求实现AccessDecisionVoter接口,Spring security已为我们提供了几个很有用的投票器如RoleVoter,WebExpressionVoter
这些我们都没有必要去自定义,而且自定义出来的也没有默认实现拓展性和稳定性更好再定义一个登陆的Controller
LoginControllerpackage com.cas.client2.casclient2.controller; import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.cas.authentication.CasAuthenticationToken;
import org.springframework.security.cas.web.CasAuthenticationFilter;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.RequestMapping; import javax.servlet.http.HttpSession; @SuppressWarnings("ALL")
@Controller
public class LoginController {
@Autowired
private AuthenticationManager authenticationManager; /**
* 自定义登录地址
* @param username
* @param password
* @param session
* @return
*/
@RequestMapping("login.do")
public String login(String username,String passwod, HttpSession session){
try {
System.out.println("进入登录请求..........");
UsernamePasswordAuthenticationToken token=new UsernamePasswordAuthenticationToken(username,passwod); Authentication authentication=authenticationManager.authenticate(token);
SecurityContextHolder.getContext().setAuthentication(authentication);
session.setAttribute("SPRING_SECURITY_CONTEXT", SecurityContextHolder.getContext());
System.out.println("登录成功");
return "redirect:home.html";
}catch (Exception e){
e.printStackTrace();
return "login.html";
} }
}创建几个页面:在resources下创建文件夹html,用于存放html静态文件,
home.html<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>HOME</title>
</head>
<body>
<h1>welcome to Home</h1>
<button onclick="javascript:location.href='/logout'">退出</button>
</body>
</html>login.html
<!DOCTYPE html>
<html lang="en" xmlns="http://www.w3.org/1999/xhtml" xmlns:th="http://www.thymeleaf.org"
xmlns:sec="http://www.thymeleaf.org/thymeleaf-extras-springsecurity3">
<head>
<meta charset="UTF-8">
<title>登录</title>
</head> <body>
<span style="color: red" id="msg"></span>
<form action="/login.do" method="post">
<div><label> User Name : <input type="text" name="username"/> </label></div>
<div><label> Password: <input type="password" name="password"/> </label></div>
<div><input type="submit" value="Sign In"/></div>
<input type="checkbox" name="remember-me" value="true" th:checked="checked"/><p>Remember me</p>
</form> </body>
<script type="text/javascript">
var url=location.href
var param=url.split("?")[1];
console.log(param);
if (param){
var p=param.split("&");
var msg=p[0].split("=")[1];
document.getElementById("msg").innerHTML=msg;
}
</script>
</html>admin.html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>admin</title>
</head>
<body>
你好,欢迎登陆,这是管理员界面,拥有/admin.html的访问权限才能访问
</body>
</html>再定义几个错误页面
在html文件夹下创建一个error文件夹,在error文件夹中创建403.html,404.html,500.html;在程序遇到这些错误码时,会自动跳转到对应的页面先启动一下项目,让spring-data-jpa反向生成一下表结构
再往数据库插入几条数据:
用户表的密码需要放密文,我们把我们的明文密码使用我们的密码encoder转一下:BCryptPasswordEncoder.encode("123");得到密文后存到数据库的password字段中
用户表: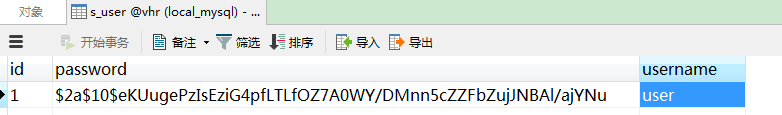
资源表:即权限信息表
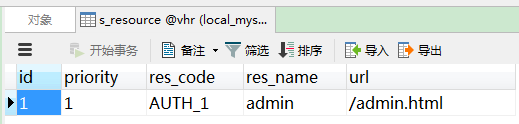
角色表:
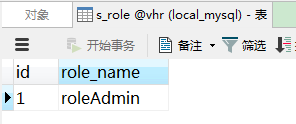
角色权限中间表:
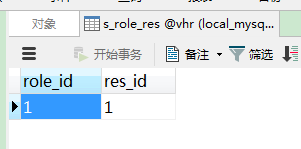
我们先不给用户配置角色,现在是空角色
启动Spring boot启动类,访问localhost:8083,检测到没登录会自动跳到登录页面,登录后自动跳转到home.html
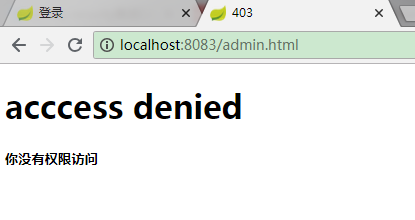
访问admin.html,返回403页面,当前用户无权限访问
再将刚刚的角色分配给用户,再次访问
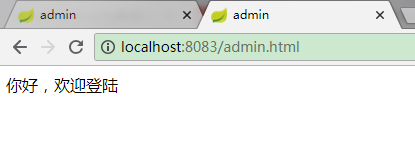
此时便可访问,大功告成!
- 部署CAS server
cas全称 Central Authentication Service,翻译为:中央认证服务;从名字我们便可得知,这是一个独立的服务,主要负责用户登录凭证的验证;事实也是如此,cas有认证中心和client端,认证中心就是我们的cas server,负责用户凭证的验证,需要独立部署,cas client就是我们的各个相互信任的应用
我们从cas官网下载源码,从moudle中找到一个.war后缀的文件,将这个文件拷出来,
改一下文件名为:cas,放到一个Tomcat中,启动tomcat,(端口先改一下,如8081),在浏览器中访问localhost:8081/cas即可看到cas的登录界面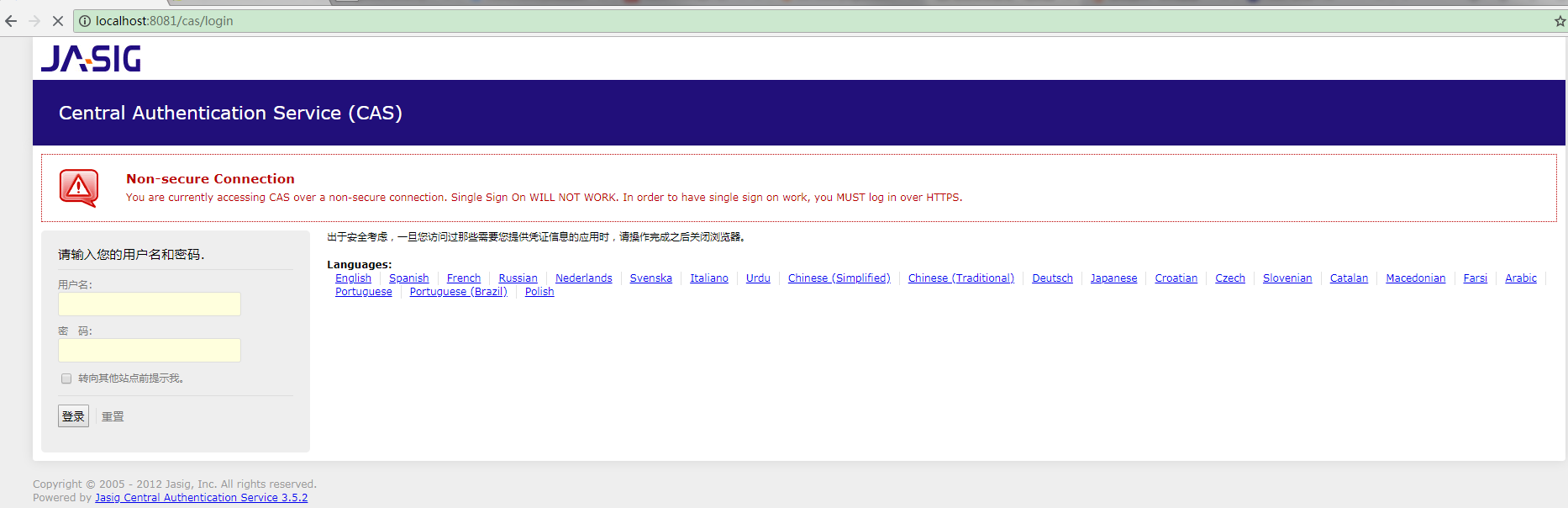
报了个警告,说我们没有配置ssl,也就是需要配置https,不过可以不用配置,
我们可以配置使用http:设置cas server使用http非安全协议
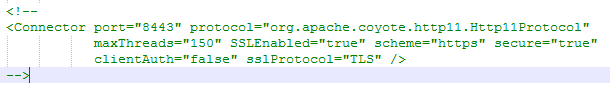
主要有以下步骤:
1.WEB-INF/deployerConfigContext.xml中在< bean class = "org.jasig.cas.authentication.handler.support.HttpBasedServiceCredentialsAuthenticationHandler" p:httpClient-ref = "httpClient" />增加参数 p:requireSecure="false" ,是否需要安全验证,即 HTTPS,false 为不采用 如下:< bean class = "org.jasig.cas.authentication.handler.support.HttpBasedServiceCredentialsAuthenticationHandler" p:httpClient-ref = "httpClient" p:requireSecure= "false" />
1. WEB-INF/spring-configuration/ticketGrantingTicketCookieGenerator.xml中将p:cookieSecure="true"修改为 p:cookieSecure="false"
2. WEB-INF/spring-configuration/warnCookieGenerator.xml中将p:cookieSecure="true"改为p:cookieSecure="false"
3. 在tomcat的server.xml中关闭8443端口,如下图
- 配置CAS client
在之前Spring security的基础上,我们加入cas认证
在pom.xml中加入依赖包:<!-- security 对CAS支持 -->
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-cas</artifactId>
</dependency>修改一下我们的UserDetailsServiceImpl类,让它实现AuthenticationUserDetailsService<CasAssertionAuthenticationToken>接口
UserDetailsServiceImpl:package com.cas.client1.security; import com.cas.client1.entity.User;
import com.cas.client1.service.UserService;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.cas.authentication.CasAssertionAuthenticationToken;
import org.springframework.security.core.userdetails.AuthenticationUserDetailsService;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.core.userdetails.UsernameNotFoundException;
import org.springframework.stereotype.Component; /**
* @author Administrator
*/
@SuppressWarnings("ALL")
@Component
public class UserDetailsServiceImpl implements UserDetailsService,
AuthenticationUserDetailsService<CasAssertionAuthenticationToken> {
@Autowired
private UserService userService;
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
User user = userService.findByUsername(username);
return user;
} /**
* 实现AuthenticationUserDetailsService的方法,
* 用于获取cas server返回的用户信息,再根据用户关键信息加载出用户在当前系统的权限
* @param token
* @return
* @throws UsernameNotFoundException
*/
@Override
public UserDetails loadUserDetails(CasAssertionAuthenticationToken token) throws UsernameNotFoundException {
String name = token.getName();
System.out.println("获得的用户名:"+name);
User user = userService.findByUsername(name);
if (user==null){
throw new UsernameNotFoundException(name+"不存在");
}
return user;
}
}在application.properties文件中加上以下内容:
# cas服务器地址
cas.server.host.url=http://localhost:8081/cas
# cas服务器登录地址
cas.server.host.login_url=${cas.server.host.url}/login
# cas服务器登出地址
cas.server.host.logout_url=${cas.server.host.url}/logout?service=${app.server.host.url}
# 应用访问地址
app.server.host.url=http://localhost:8083
# 应用登录地址
app.login.url=/login.do
# 应用登出地址
app.logout.url=/logout新增一个配置实体类
CasProperties
package com.cas.client1.config; import org.springframework.beans.factory.annotation.Value;
import org.springframework.stereotype.Component; @Component
public class CasProperties {
@Value("${cas.server.host.url}")
private String casServerUrl; @Value("${cas.server.host.login_url}")
private String casServerLoginUrl; @Value("${cas.server.host.logout_url}")
private String casServerLogoutUrl; @Value("${app.server.host.url}")
private String appServerUrl; @Value("${app.login.url}")
private String appLoginUrl; @Value("${app.logout.url}")
private String appLogoutUrl; /**get set方法略
*/
}再修改一下我们的Spring security配置类
package com.cas.client1.security; import com.cas.client1.config.CasProperties;
import org.jasig.cas.client.session.SingleSignOutFilter;
import org.jasig.cas.client.validation.Cas20ServiceTicketValidator;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.http.HttpMethod;
import org.springframework.security.access.AccessDecisionManager;
import org.springframework.security.access.AccessDecisionVoter;
import org.springframework.security.access.vote.AffirmativeBased;
import org.springframework.security.access.vote.RoleVoter;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.cas.ServiceProperties;
import org.springframework.security.cas.authentication.CasAuthenticationProvider;
import org.springframework.security.cas.web.CasAuthenticationEntryPoint;
import org.springframework.security.cas.web.CasAuthenticationFilter;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.builders.WebSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.web.access.intercept.FilterSecurityInterceptor;
import org.springframework.security.web.authentication.logout.LogoutFilter;
import org.springframework.security.web.authentication.logout.SecurityContextLogoutHandler; import java.util.ArrayList;
import java.util.List; /**
* Spring security配置
* @author youyp
* @date 2018-8-10
*/
@SuppressWarnings("ALL")
@Configuration
@EnableWebSecurity
public class SpringSecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
private CasProperties casProperties; @Autowired
private UserDetailsServiceImpl userDetailsService; @Autowired
private SecurityMetaDataSource securityMetaDataSource; @Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
super.configure(auth);
auth.authenticationProvider(casAuthenticationProvider());
} @Override
public void configure(WebSecurity web) throws Exception {
web.ignoring().antMatchers("/js/**","/css/**","/img/**","/*.ico","/login.html",
"/error","/login.do");
//web.ignoring().antMatchers("/js/**","/css/**","/img/**","/*.ico",,"/home");
//web.ignoring().antMatchers("/**");
// super.configure(web); } @Override
protected void configure(HttpSecurity http) throws Exception {
System.out.println("配置Spring security");
http.formLogin()
//指定登录页是”/login”
//.loginPage("/login.html").permitAll()
//.loginProcessingUrl("/login.do").permitAll()
//.defaultSuccessUrl("/home",true)
//.permitAll()
//登录成功后可使用loginSuccessHandler()存储用户信息,可选。
//.successHandler(loginSuccessHandler()).permitAll()
.and()
.logout().permitAll()
//退出登录后的默认网址是”/home”
//.logoutSuccessUrl("/home.html")
//.permitAll()
.invalidateHttpSession(true)
.and()
//登录后记住用户,下次自动登录,数据库中必须存在名为persistent_logins的表
.rememberMe()
.tokenValiditySeconds(1209600)
.and()
.csrf().disable()
//其他所有资源都需要认证,登陆后访问
.authorizeRequests().anyRequest().fullyAuthenticated();
http.exceptionHandling().authenticationEntryPoint(casAuthenticationEntryPoint())
.and()
.addFilterAt(casAuthenticationFilter(),CasAuthenticationFilter.class)
.addFilterBefore(casLogoutFilter(),LogoutFilter.class)
.addFilterBefore(singleSignOutFilter(),CasAuthenticationFilter.class);
/**
* FilterSecurityInterceptor本身属于过滤器,不能在外面定义为@Bean,
* 如果定义在外面,则这个过滤器会被独立加载到webContext中,导致请求会一直被这个过滤器拦截
* 加入到Springsecurity的过滤器链中,才会使它完整的生效
*/
http.addFilterBefore(filterSecurityInterceptor(),FilterSecurityInterceptor.class);
} /**
* 注意:这里不能加@Bean注解
* @return
* @throws Exception
*/
// @Bean
public FilterSecurityInterceptor filterSecurityInterceptor() throws Exception {
FilterSecurityInterceptor filterSecurityInterceptor=new FilterSecurityInterceptor();
filterSecurityInterceptor.setSecurityMetadataSource(securityMetaDataSource);
filterSecurityInterceptor.setAuthenticationManager(authenticationManager());
filterSecurityInterceptor.setAccessDecisionManager(affirmativeBased());
return filterSecurityInterceptor;
} /**
* 认证入口
* <p>
* <b>Note:</b>浏览器访问不可直接填客户端的login请求,若如此则会返回Error页面,无法被此入口拦截
* </p>
* @return
*/
@Bean
public CasAuthenticationEntryPoint casAuthenticationEntryPoint(){
CasAuthenticationEntryPoint casAuthenticationEntryPoint=new CasAuthenticationEntryPoint();
casAuthenticationEntryPoint.setLoginUrl(casProperties.getCasServerLoginUrl());
casAuthenticationEntryPoint.setServiceProperties(serviceProperties());
return casAuthenticationEntryPoint;
} @Bean
public ServiceProperties serviceProperties() {
ServiceProperties serviceProperties=new ServiceProperties();
serviceProperties.setService(casProperties.getAppServerUrl()+casProperties.getAppLoginUrl());
serviceProperties.setAuthenticateAllArtifacts(true);
return serviceProperties;
} // @Bean
public CasAuthenticationFilter casAuthenticationFilter() throws Exception {
CasAuthenticationFilter casAuthenticationFilter=new CasAuthenticationFilter();
casAuthenticationFilter.setAuthenticationManager(authenticationManager());
casAuthenticationFilter.setFilterProcessesUrl(casProperties.getAppLoginUrl());
// casAuthenticationFilter.setAuthenticationSuccessHandler(
// new SimpleUrlAuthenticationSuccessHandler("/home.html"));
return casAuthenticationFilter;
} @Bean
public CasAuthenticationProvider casAuthenticationProvider(){
CasAuthenticationProvider casAuthenticationProvider=new CasAuthenticationProvider();
casAuthenticationProvider.setAuthenticationUserDetailsService(userDetailsService); casAuthenticationProvider.setServiceProperties(serviceProperties());
casAuthenticationProvider.setTicketValidator(cas20ServiceTicketValidator());
casAuthenticationProvider.setKey("casAuthenticationProviderKey");
return casAuthenticationProvider;
} @Bean
public Cas20ServiceTicketValidator cas20ServiceTicketValidator() {
return new Cas20ServiceTicketValidator(casProperties.getCasServerUrl());
} // @Bean
public SingleSignOutFilter singleSignOutFilter(){
SingleSignOutFilter singleSignOutFilter=new SingleSignOutFilter();
singleSignOutFilter.setCasServerUrlPrefix(casProperties.getCasServerUrl());
singleSignOutFilter.setIgnoreInitConfiguration(true);
return singleSignOutFilter;
} // @Bean
public LogoutFilter casLogoutFilter(){
LogoutFilter logoutFilter = new LogoutFilter(casProperties.getCasServerLogoutUrl(), new SecurityContextLogoutHandler());
logoutFilter.setFilterProcessesUrl(casProperties.getAppLogoutUrl());
return logoutFilter;
} /**
* 重写AuthenticationManager获取的方法并且定义为Bean
* @return
* @throws Exception
*/
@Override
@Bean
public AuthenticationManager authenticationManagerBean() throws Exception {
return super.authenticationManagerBean();
} @Autowired
public void configureGlobal(AuthenticationManagerBuilder auth) throws Exception {
//指定密码加密所使用的加密器为passwordEncoder()
//需要将密码加密后写入数据库
//auth.userDetailsService(userDetailsService).passwordEncoder(passwordEncoder());
//auth.eraseCredentials(false);
} @Bean
public BCryptPasswordEncoder passwordEncoder() { return new BCryptPasswordEncoder(4);
} /**
* 定义决策管理器,这里可直接使用内置的AffirmativeBased选举器,
* 如果需要,可自定义,继承AbstractAccessDecisionManager,实现decide方法即可
* @return
*/
@Bean
public AccessDecisionManager affirmativeBased(){
List<AccessDecisionVoter<? extends Object>> voters=new ArrayList<>();
voters.add(roleVoter());
System.out.println("正在创建决策管理器");
return new AffirmativeBased(voters);
} /**
* 定义选举器
* @return
*/
@Bean
public RoleVoter roleVoter(){
//这里使用角色选举器
RoleVoter voter=new RoleVoter();
System.out.println("正在创建选举器");
voter.setRolePrefix("AUTH_");
System.out.println("已将角色选举器的前缀修改为AUTH_");
return voter;
} @Bean
public LoginSuccessHandler loginSuccessHandler() {
return new LoginSuccessHandler();
} }这里我们新增了几个filter,请注意,这几个filter定义时都不能配置@Bean注解,原因以上相同,这几个filter都要加入到springSecurity的FilterChain中,而不是直接加入到web容器的FilterChain中
再修改一下LoginControllerpackage com.cas.client1.controller; import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.cas.web.CasAuthenticationFilter;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.security.web.authentication.UsernamePasswordAuthenticationFilter;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.RequestMapping; import javax.servlet.http.HttpSession; @SuppressWarnings("Duplicates")
@Controller
public class LoginController {
@Autowired
private AuthenticationManager authenticationManager; /**
* 自定义登录地址
* @param username
* @param password
* @param session
* @return
*/
@RequestMapping("login.do")
public String login(String ticket, HttpSession session){
try {
System.out.println("进入登录请求..........");
//cas单点登录的用户名就是:_cas_stateful_ ,用户凭证是server传回来的ticket
String username = CasAuthenticationFilter.CAS_STATEFUL_IDENTIFIER;
UsernamePasswordAuthenticationToken token=new UsernamePasswordAuthenticationToken(username,ticket);
Authentication authentication=authenticationManager.authenticate(token);
SecurityContextHolder.getContext().setAuthentication(authentication);
session.setAttribute("SPRING_SECURITY_CONTEXT", SecurityContextHolder.getContext());
System.out.println("登录成功");
return "redirect:home.html";
}catch (Exception e){
e.printStackTrace();
return "login.html";
} }
}这时,之前负责登录的loginController不再是验证用户名和密码正不正确了,因为用户名密码的验证已经交给cas server了,LoginController的工作就是接收cas server重定向时传回来的ticket,验证ticket的有效性,如果没有异常,则会进入到UserDetailsServiceImpl中的loadUserDetails方法,并根据用户名加载用户权限等信息,然后我们再将用户信息存入Session,完成本地登录,本地登录之后,用户每次请求时,就不需要再次验证ticket了,而是验证Session
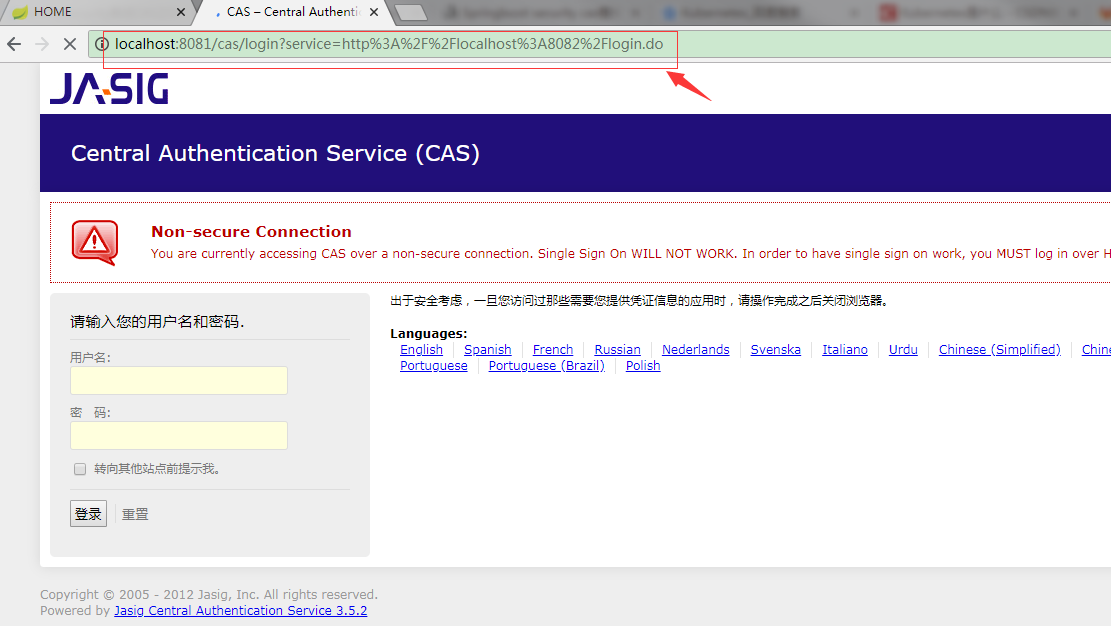
到这里,cas client已经配置完成,为了看清楚流程,我们以debug模式启动一下项目,在loginController的login方法开头打一个断点,打开浏览器调试模式(F12),切换到network看请求,在浏览器中输入:localhost:8083,浏览器会自动重定向到cas server 的登录页面,如下图:
我们输入一个数据库中有的用户名,再在密码栏中输入一次用户名,因为这里的cas server验证方式还没改,只要求用户名和密码相同就可通过验证,后面我会研究一下怎么修改cas server 的验证方式为数据库验证
如输入:用户名:user 密码:user
点击登录,验证成功后,我们看F12 network请求,发现浏览器发送了两个请求,一个是8081的,也就是cas server的,另外一个是8083的,也就是我们的client端的,如图: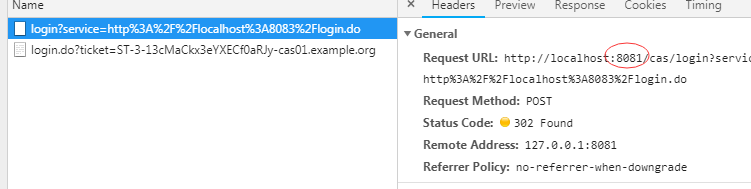
另一个
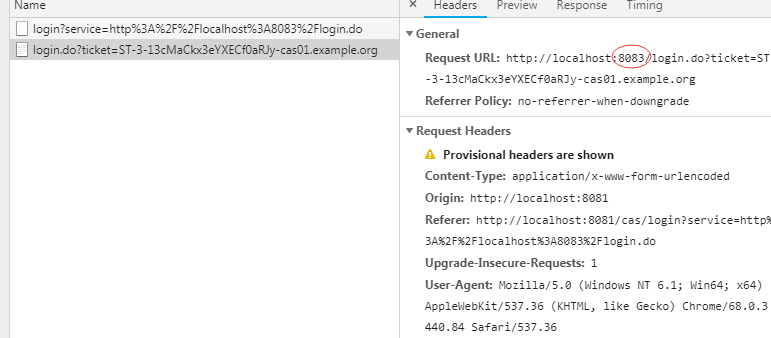
因为我们在后台开了debug模式,打了断点,所以后面这个请求一直在pending状态,我们先看第一个请求的详细情况:

很明显的,这个请求发送了我们的用户名和密码,由此可知,这个请求的作用就是负责在cas server后台验证用户名的密码,验证成功后,会自动重定向到第二个请求
我们再来看第二个请求: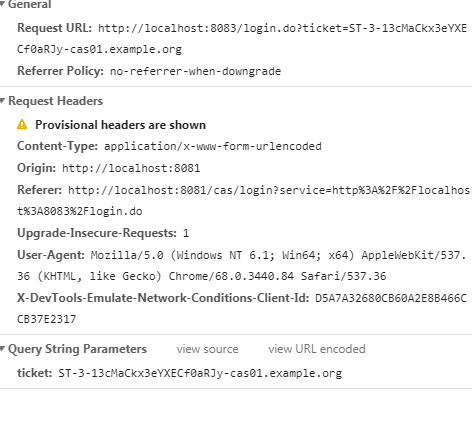
这个请求就是我们cas client所配置的登录地址,此时这个请求后面自动带上了一个名为ticket的参数,参数值是一串自动生成的随机字符串,由cas server生成的
我们再回到后台,没什么错误的话,我们可以看到LoginController接收到了这个参数,我们先在UserDetailsServiceImpl类的loadUserDetails方法的开头打一个断点,按F8让调试器跑走,此时,我们就可以看到调试器跳到了我们刚刚打的UserDetasServiceImpl的断点中,再看看参数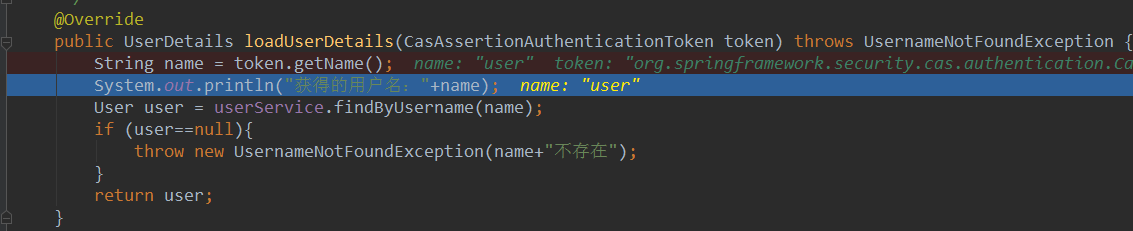
可以看出,我们接收到了cas server认证完ticket后传回来的用户名,我们根据用户名加载对应的权限,返回即可,此时我们再次按F8跳走
再回到界面,发现我们已经可以访问页面了: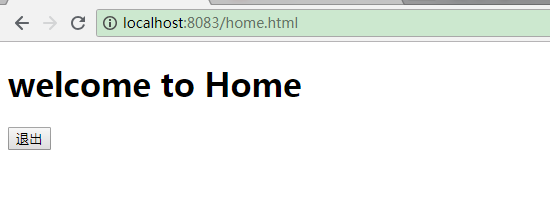
下一步,就是验证多个应用之间是否能只登陆一次就不用再登陆了;
我们将当前项目拷贝一份,改名称为cas-client2(maven的groupId和artifactId),再修改一下端口为8082,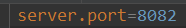 ,记得对应的cas配置也要改:
,记得对应的cas配置也要改: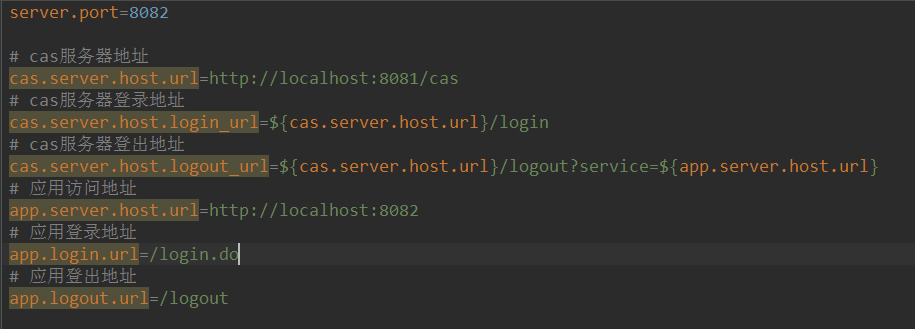
启动项目
先访问localhost:8082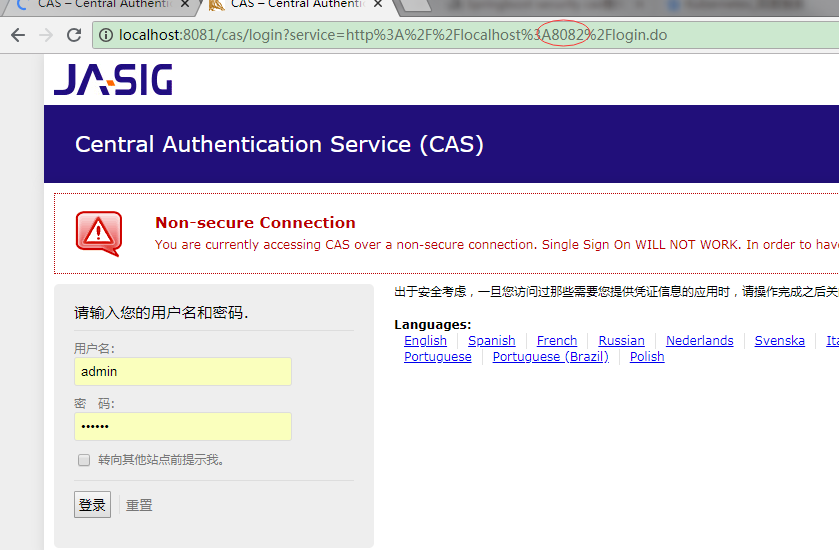
发现它自动跳转到了8081的cas server
再打开另外一个浏览器标签,访问localhost:8083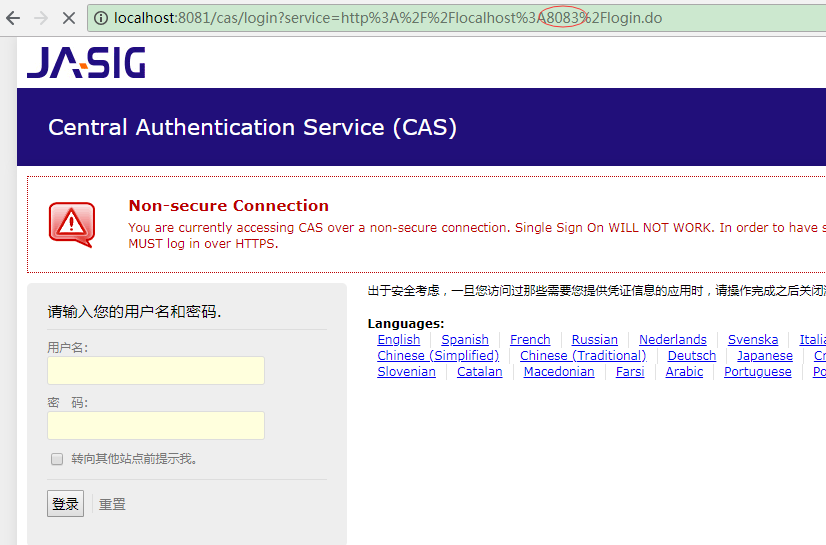
发现它也自动跳到了cas的登录页面,我们先在这里输入账号密码登录:
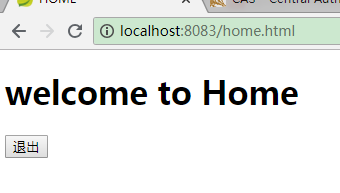
登录成功后,我们再切换回刚刚没登录的8082的网页标签,刷新一下,
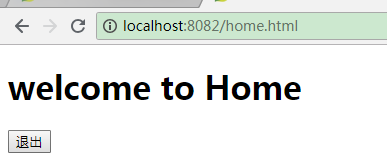
ok,8082也不用登陆了,大功告成!
源码地址:
https://github.com/yupingyou/casclient.git
另:Spring security原本默认有个/login和/logout的handler,(以前不是这个地址,不知道从哪个版本开始改了,以前好像是_spring_security_check,大概是这个,记不太清,我用了4以后就发现地址变了),但是我发现我访问/login的时候出现404,但/logout可以访问,没发现什么原因,后来我就自定义一个登陆了,也就是我配置的/login.do,代替了默认的/login
第一次动手写这么长的博客...............累
Spring boot security权限管理集成cas单点登录的更多相关文章
- (39.1) Spring Boot Shiro权限管理【从零开始学Spring Boot】
(本节提供源代码,在最下面可以下载)距上一个章节过了二个星期了,最近时间也是比较紧,一直没有时间可以写博客,今天难得有点时间,就说说Spring Boot如何集成Shiro吧.这个章节会比较复杂,牵涉 ...
- Spring Boot Shiro 权限管理
Spring Boot Shiro 权限管理 标签: springshiro 2016-01-14 23:44 94587人阅读 评论(60) 收藏 举报 .embody{ padding:10px ...
- (39.4) Spring Boot Shiro权限管理【从零开始学Spring Boot】
在读此文章之前您还可能需要先了解: (39.1) Spring Boot Shiro权限管理[从零开始学Spring Boot] http://412887952-qq-com.iteye.com/b ...
- (39.3) Spring Boot Shiro权限管理【从零开始学Spring Boot】
在学习此小节之前您可能还需要学习: (39.1) Spring Boot Shiro权限管理[从零开始学Spring Boot] http://412887952-qq-com.iteye.com/b ...
- (39.2). Spring Boot Shiro权限管理【从零开始学Spring Boot】
(本节提供源代码,在最下面可以下载) (4). 集成Shiro 进行用户授权 在看此小节前,您可能需要先看: http://412887952-qq-com.iteye.com/blog/229973 ...
- 十、 Spring Boot Shiro 权限管理
使用Shiro之前用在spring MVC中,是通过XML文件进行配置. 将Shiro应用到Spring Boot中,本地已经完成了SpringBoot使用Shiro的实例,将配置方法共享一下. 先简 ...
- Spring Boot Shiro 权限管理 【转】
http://blog.csdn.net/catoop/article/details/50520958 主要用于备忘 本来是打算接着写关于数据库方面,集成MyBatis的,刚好赶上朋友问到Shiro ...
- SpringBoot集成CAS单点登录,SSO单点登录,CAS单点登录(视频资料分享篇)
单点登录(Single Sign On),简称为 SSO,是目前比较流行的企业业务整合的解决方案之一.SSO的定义是在多个应用系统中,用户只需要登录一次就可以访问所有相互信任的应用系统. 很早期的公司 ...
- SpringBoot项目集成cas单点登录
添加依赖 添加cas client依赖 <dependency> <groupId>net.unicon.cas</groupId> <artifactId& ...
随机推荐
- 访问windows共享无法分配内存问题解决
设置:“HKLMSYSTEMCurrentControlSetControlSession ManagerMemory ManagementLargeSystemCache” 为 “1″ 设置:“HK ...
- codeforces 1284C. New Year and Permutation(组合数学)
链接:https://codeforces.com/problemset/problem/1284/C 题意:定义一个framed segment,在区间[l,r]中,max值-min值 = r - ...
- POJ3258 River Hopscotch(二分最大化最小值)
题目链接:http://poj.org/problem?id=3258 题意:给n个石头,起点和终点也是两个石头,去掉这石头中的m个,使得石头间距的最小值最大. 思路:二分石头间的最短距离,每次贪心地 ...
- H5 App设计者需要注意的问题
我们通常在做H5 APP设计的过程中,遇到很多看似很小,且很容易被忽略的问题,正是这些小问题,一次次的撩拨用户的耐心,让用户对你的APP心生怨念.现在WeX5君呕血为大家整理出H5 APP设计的21条 ...
- AcWing 789. 数的范围 二分+模板
https://www.acwing.com/problem/content/791/ #include<bits/stdc++.h> using namespace std; ; int ...
- 2.7 Axure rp (快速原型设计工具)
一. Axure rp 下载安装 直接百度栏输入Axure rp即可下载.安装无特别处,一直点击下一步即可. 安装的如果是英文版,可以下载汉化包,进行汉化. 汉化参照网址:http://www.a ...
- Stream中的map
#map可以让一个对象A的流转换为宁外一种对象B的流(其实也是A对象元素组成的流) 1.对象转换为List集合 //若Eticket是一个对象,其中orderId是String类型 //eticket ...
- 每天进步一点点------verilog语言实现的分频
一 .占空比50%的任意奇数分频 如果要实现占空比为50%的三分频时钟,可以通过待分频时钟下降沿触发计数,和上升沿同样的方法计数进行三分频,然后下降沿产生的三分频时钟和上升沿产生的时钟进行相或运算,即 ...
- (转载)Docker的boot2docker.iso镜像使用
原文路径:https://blog.csdn.net/jiangjingxuan/article/details/54908272#commentsedit 在Docker首次启动时需要下载的一个bo ...
- codeforces div2 603 E. Editor(线段树)
题目链接:https://codeforces.com/contest/1263/problem/E 题意:一个编译器,每次输入一些字符,R表示光标右移,L表示光标左移,然后有一些左括号( 和 右括 ...
