poj1523 求割点 tarjan
| Time Limit: 1000MS | Memory Limit: 10000K | |
| Total Submissions: 7678 | Accepted: 3489 |
Description
Node 3 is therefore a Single Point of Failure (SPF) for this network. Strictly, an SPF will be defined as any node that, if unavailable, would prevent at least one pair of available nodes from being able to communicate on what was previously a fully connected network. Note that the network on the right has no such node; there is no SPF in the network. At least two machines must fail before there are any pairs of available nodes which cannot communicate. 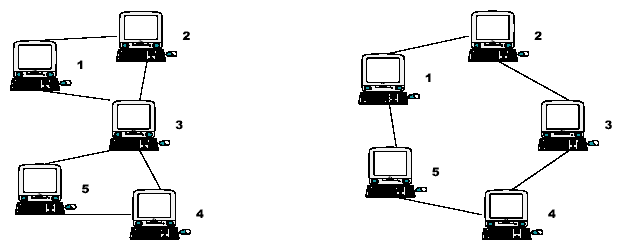
Input
Output
The first network in the file should be identified as "Network #1", the second as "Network #2", etc. For each SPF node, output a line, formatted as shown in the examples below, that identifies the node and the number of fully connected subnets that remain when that node fails. If the network has no SPF nodes, simply output the text "No SPF nodes" instead of a list of SPF nodes.
Sample Input
1 2
5 4
3 1
3 2
3 4
3 5
0 1 2
2 3
3 4
4 5
5 1
0 1 2
2 3
3 4
4 6
6 3
2 5
5 1
0 0
Sample Output
Network #1
SPF node 3 leaves 2 subnets Network #2
No SPF nodes Network #3
SPF node 2 leaves 2 subnets
SPF node 3 leaves 2 subnets
题意: 求割点 同时求出删除当前点后,分成几个连通分量。
思路:
tarjan算法求割点。 tarjan处理强连通 其实都是基于dfs的。同时维护2个数组。 dfn[] 和 low[] 分别表示第i点时的深度,和通过能够到达的祖先的深度。
求强连通的时候,如果low[i] == dfn[i] 说明栈内当前点以上的点 都是强连通块里面的。也就是说i的子树中不能到达i的祖先。
在求割点的时候,如果low[v] > dfn[u](v是u的子节点)说明v不能到达u的祖先 说明删除u后 v的子树从原图中分离。
#include<set>
#include<map>
#include<queue>
#include<stack>
#include<cmath>
#include<string>
#include<vector>
#include<cstdio>
#include<cstring>
#include<iostream>
#include<algorithm>
#define INF 1000000001
#define MOD 1000000007
#define ll long long
#define lson l,m,rt<<1
#define rson m+1,r,rt<<1|1
#define pi acos(-1.0)
using namespace std;
const int MAXN = ;
struct node
{
int to;
int next;
}edge[MAXN*];
int ind,pre[MAXN],dfn[MAXN],low[MAXN],num[MAXN],n,vis[MAXN];
void add(int x,int y)
{
edge[ind].to = y;
edge[ind].next = pre[x];
pre[x] = ind ++;
}
void dfs(int rt,int d)
{
vis[rt] = ;
dfn[rt] = low[rt] = d;
for(int i = pre[rt]; i != -; i = edge[i].next){
int t = edge[i].to;
if(!vis[t]){
dfs(t,d + );
low[rt] = min(low[rt],low[t]);
if(low[t] >= dfn[rt]){
num[rt] ++;
}
}
else {
low[rt] = min(low[rt],dfn[t]);
}
}
}
int main()
{
int x,y,ff = ;
while(){
n = ;
scanf("%d",&x);
if(!x)break;
scanf("%d",&y);
ind = , memset(pre,-,sizeof(pre));
add(x,y), add(y,x);
n = max(x,y);
while(){
scanf("%d",&x);
if(!x)break;
scanf("%d",&y);
n = max(n,x);
n = max(n,y);
add(x,y), add(y,x);
}
memset(vis,,sizeof(vis));
memset(dfn,,sizeof(dfn));
memset(low,,sizeof(low));
memset(num,,sizeof(num));
dfs(,);
int flag = ;
if(ff >= )printf("\n");
printf("Network #%d\n",++ff);
num[] = num[] ? num[] - : ;
for(int i = ; i <= n; i++){
if(num[i]){
flag = ;
printf(" SPF node %d leaves %d subnets\n",i,num[i] + );
}
}
if(!flag){
printf(" No SPF nodes\n");
}
}
return ;
}
poj1523 求割点 tarjan的更多相关文章
- poj1523求割点以及割后连通分量数tarjan算法应用
无向图,双向通道即可,tarjan算法简单应用.点u是割点,条件1:u是dfs树根,则u至少有2个孩子结点.||条件2:u不是根,dfn[u]=<low[v],v是u的孩子结点,而且每个这样的v ...
- zoj 1119 / poj 1523 SPF (典型例题 求割点 Tarjan 算法)
poj : http://poj.org/problem?id=1523 如果无向图中一个点 u 为割点 则u 或者是具有两个及以上子女的深度优先生成树的根,或者虽然不是一个根,但是它有一个子女 w, ...
- uva 315 Network(无向图求割点)
https://uva.onlinejudge.org/index.php?option=com_onlinejudge&Itemid=8&page=show_problem& ...
- poj 1523 SPF(tarjan求割点)
本文出自 http://blog.csdn.net/shuangde800 ------------------------------------------------------------ ...
- Tarjan求割点和桥
by szTom 前置知识 邻接表存储及遍历图 tarjan求强连通分量 割点 割点的定义 在一个无向图中,如果有一个顶点集合,删除这个顶点集合以及这个集合中所有顶点相关联的边以后,图的连通分量增多, ...
- Tarjan应用:求割点/桥/缩点/强连通分量/双连通分量/LCA(最近公共祖先)【转】【修改】
一.基本概念: 1.割点:若删掉某点后,原连通图分裂为多个子图,则称该点为割点. 2.割点集合:在一个无向连通图中,如果有一个顶点集合,删除这个顶点集合,以及这个集合中所有顶点相关联的边以后,原图变成 ...
- [学习笔记]tarjan求割点
都口胡了求割边,就顺便口胡求割点好了QAQ 的定义同求有向图强连通分量. 枚举当前点的所有邻接点: 1.如果某个邻接点未被访问过,则访问,并在回溯后更新 2.如果某个邻接点已被访问过,则更新 对于当前 ...
- tarjan算法求割点cojs 8
tarjan求割点:cojs 8. 备用交换机 ★★ 输入文件:gd.in 输出文件:gd.out 简单对比时间限制:1 s 内存限制:128 MB [问题描述] n个城市之间有通讯网 ...
- UESTC 900 方老师炸弹 --Tarjan求割点及删点后连通分量数
Tarjan算法. 1.若u为根,且度大于1,则为割点 2.若u不为根,如果low[v]>=dfn[u],则u为割点(出现重边时可能导致等号,要判重边) 3.若low[v]>dfn[u], ...
随机推荐
- POJ3255Roadblocks[次短路]
Roadblocks Time Limit: 2000MS Memory Limit: 65536K Total Submissions: 12697 Accepted: 4491 Descr ...
- java中有类似C#里ref或out的功能吗?
JAVA中都是值传递.JAVA中的“引用”和C++中的引用有本质的区别,倒是和C++中的指针非常类似.可以将JAVA的引用理解为“不支持指针运算的指针”.所以可以说JAVA中其实并不存在真正的引用,所 ...
- css布局多列等高
css .content{margin:0 auto;width: 600px;border: 3px solid #00c;overflow: hidden;} .left{float: left; ...
- java多线程系类:基础篇:06线程让步
本系类的知识点全部来源于http://www.cnblogs.com/skywang12345/p/3479243.html,我只是复制粘贴一下,特在此说明. 概要 本章,会对Thread中的线程让步 ...
- salt yum安装lamp
在批量安装软件前,先找台测试机yum装一遍,看是否报错等,是否依赖包全等 . 本次我们在dev环境下搞. 先看一下已搞成功的目录结构 定义dev环境的第二个好处 ...
- scala 学习笔记(01) 函数定义、分支、循环、异常处理、递归
package yjmyzz import scala.io.StdIn object ScalaApp { def main(args: Array[String]) { println(" ...
- es6+react环境搭建
工具说明 Node Koa React Webpack 项目结构 - build 客户端代码的构建文件目录 - config 项目的配置文件 - docs 项目相关的文档目录 - lib 服务端库文件 ...
- 2014-10-28——iframe多层嵌套时获取元素总结
同域: 父页面获取子页面元素: 注意:onload事件 jQuery获取:$("iframe").contents().find("holder")...... ...
- Java 并发工具包 java.util.concurrent 用户指南
1. java.util.concurrent - Java 并发工具包 Java 5 添加了一个新的包到 Java 平台,java.util.concurrent 包.这个包包含有一系列能够让 Ja ...
- Linux学习笔记-Ubuntu添加右键菜单打开终端
1.进入个人目录(如/home/batsing,下文缩写成 ~ ):设置显示隐藏文件,或使用命令行:2.进入 ~/.gnome2/nautilus-scripts 文件夹,新建一个文件,名为 term ...
