Sending Secret Messages LightOJ - 1404
Sending Secret Messages LightOJ - 1404
Alice wants to send Bob some confidential messages. But their internet connection is not secured enough. As their names have been used in many networking schemes, they are very rich now. So, they don't want to send encoded messages, they want to use secured dedicated connection for them. So, they talked to some ISPS (Internet Service Providers) about their problem. Only they get is that there are N routers in the network, some of them share bidirectional links. Each link has a capacity, and for each KB of data passing through this link, they have to pay some money. Assume that Alice is connected with the 1st router and Bob is connected to the Nth router.
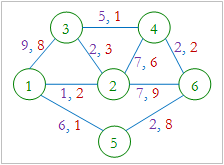
For example, in the picture, Alice wants to send 4 KB data from router 1 to router 6. Each link is identified by two integers in the form (a, b) where 'a' denotes the capacity of the link and 'b'denotes per KB cost of the link. So, Alice can send 1KB of data through 1 - 2 - 3 - 4 - 6 (cost 8), 2KB data through 1 - 5 - 6 (cost 2 * 9=18) and 1KB data through 1 - 3 - 4 - 6 (cost 11). So, the total cost is 37 units.
Now Alice wants to send P KB of data to Bob. You have to find the minimum amount of money they have to pay to achieve their goal.
Input
Input starts with an integer T (≤ 50), denoting the number of test cases.
Each case starts with a blank line. Next line contains three integers N (2 ≤ N ≤ 50), M (0 ≤ M ≤ N*(N-1)/2) and P (1 ≤ P ≤ 1000), where M denotes the number of bidirectional links. Each of the next M lines contains four integers u v w c (1 ≤ u, v ≤ N, u ≠ v, 1 ≤ w, c ≤ 100), meaning that there is a link between router u and v, and at most c KB data can be sent through this link, and each KB of data through this link will cost w. You can assume that there will be at most one connection between a pair of routers.
Output
For each case, print the case number and the minimum amount of money required or "impossible" if it's not possible to send P KB of data.
Sample Input
3
6 9 4
3 1 9 8
1 2 1 2
1 5 6 1
5 6 2 8
6 4 2 2
4 2 7 6
2 6 7 9
3 4 5 1
3 2 2 3
6 9 9
3 1 9 8
1 2 1 2
1 5 6 1
5 6 2 8
6 4 2 2
4 2 7 6
2 6 7 9
3 4 5 1
3 2 2 3
4 4 20
1 3 1 3
3 4 1 4
1 2 1 2
2 4 1 5
Sample Output
Case 1: 37
Case 2: 139
Case 3: impossible
题意:给定一个图,有n个顶点m条无向边,每条边都有容量和费用,求从1到n穿输p的数据量时的费用。
题解:费用流模板,EK算法介绍 https://blog.csdn.net/y990041769/article/details/21026445
#include <iostream>
#include <cstdio>
#include <cstring>
#include <algorithm>
#include <vector>
#include <queue>
using namespace std;
typedef long long ll;
const int MAXX=;
const int INF=0x3f3f3f3f; struct node
{
int st;
int to;
int next;
int cap;
int cost;
}edge[MAXX]; int head[MAXX],tol;
int pre[MAXX],dis[MAXX];
bool vis[MAXX];
int n,m,p; void init()
{
tol=;
memset(head,-,sizeof(head));
} void addedge(int u,int v,int cap,int cost)
{
edge[tol].st=u;
edge[tol].to=v;
edge[tol].cap=cap;
edge[tol].cost=cost;
edge[tol].next=head[u];
head[u]=tol++; edge[tol].st=v;
edge[tol].to=u;
edge[tol].cap=;
edge[tol].cost=-cost;
edge[tol].next=head[v];
head[v]=tol++;
} int minCostMaxFlow(int s,int t,int p)
{
int cost=;
while(p>)
{
queue<int> q;
memset(dis,INF,sizeof(dis));
memset(vis,,sizeof(vis));
memset(pre,-,sizeof(pre));
dis[s]=;
vis[s]=;
q.push(s);
while(!q.empty())
{
int u=q.front(); q.pop();
vis[u]=;
for(int i=head[u];i!=-;i=edge[i].next)
{
int to=edge[i].to;
if(edge[i].cap>&&dis[to]>dis[u]+edge[i].cost)
{
dis[to]=dis[u]+edge[i].cost;
pre[to]=i;
if(!vis[to])
{
vis[to]=;
q.push(to);
}
}
}
}
if(dis[t]==INF)return -;
int minn=p; for(int i=pre[t];i!=-;i=pre[edge[i].st])
minn=min(minn,edge[i].cap); for(int i=pre[t];i!=-;i=pre[edge[i].st])
{
edge[i].cap-=minn;
edge[i^].cap+=minn;
}
cost+=minn*dis[t];
p-=minn;
}
return cost;
} int main()
{
int T,x,y,z,w,cas=;
scanf("%d",&T);
while(T--)
{
scanf("%d%d%d",&n,&m,&p);
init();
for(int i=;i<=m;i++)
{
scanf("%d%d%d%d",&x,&y,&z,&w);
addedge(x,y,z,w);
addedge(y,x,z,w);
}
int ans=minCostMaxFlow(,n,p);
printf("Case %d: ",cas++);
if(ans!=-) printf("%d\n",ans);
else printf("impossible\n");
}
return ;
}
Sending Secret Messages LightOJ - 1404的更多相关文章
- How the Bitcoin protocol actually works
sklearn实战-乳腺癌细胞数据挖掘(博客主亲自录制视频教程) https://study.163.com/course/introduction.htm?courseId=1005269003&a ...
- [USACO 08DEC]Secret Message
Description Bessie is leading the cows in an attempt to escape! To do this, the cows are sending sec ...
- Secret Message ---- (Trie树应用)
Secret Message 总时间限制: 2000ms 内存限制: 32768kB 描述 Bessie is leading the cows in an attempt to escap ...
- [USACO08DEC] 秘密消息Secret Message
题目描述 Bessie is leading the cows in an attempt to escape! To do this, the cows are sending secret bin ...
- 「USACO08DEC」「LuoguP2922」秘密消息Secret Message(AC自动机
题目描述 Bessie is leading the cows in an attempt to escape! To do this, the cows are sending secret bin ...
- 洛谷 P2922 [USACO08DEC]秘密消息Secret Message
题目描述 Bessie is leading the cows in an attempt to escape! To do this, the cows are sending secret bin ...
- Distributed Cache Coherence at Scalable Requestor Filter Pipes that Accumulate Invalidation Acknowledgements from other Requestor Filter Pipes Using Ordering Messages from Central Snoop Tag
A multi-processor, multi-cache system has filter pipes that store entries for request messages sent ...
- Fedora 24中的日志管理
Introduction Log files are files that contain messages about the system, including the kernel, servi ...
- window下安装jupyter
1.Install [Anaconda](https://docs.continuum.io/anaconda/install#anaconda-install) 实际上安装了anaconda就已经安 ...
随机推荐
- shell 例程 —— 解决redis读取稳定性
问题背景: php读取线上redis数据,常常不稳定,数据响应时有时无. 解决方法:多次读取.每次读取全部上一次没读出的数据,直到全部获取. 本文实现用shell进行多次redis数据读取, 每次取出 ...
- Xamarin nuget package update 错误
update xamarin.Forms包时出现错误: 'The specified path, file name, or both are too long. The fully qualifie ...
- SVN提交代码冲突解决方法总结
在近期svn提交代码时遇到多种情况的问题,现做一个解决办法的总结如下: 插播一条:idea下被svn版本控制各类文件的颜色区分,红棕色,未加入版本控制:绿色,已经加入控制暂未提交:蓝色,加入,已提交, ...
- 利用rman自己主动备份转储spfile
利用rman自己主动备份转储spfile [情景简单介绍] 生产环境丢失了server的參数文件,rman已开启自己主动备份设置. [操作过程简述] ----启动rman $rman target / ...
- hdoj-1214-圆桌会议【逆序数】
圆桌会议 Time Limit: 2000/1000 MS (Java/Others) Memory Limit: 65536/32768 K (Java/Others) Total Submissi ...
- 玩转CPU之直线
近期在看编程之美,看到第一个问题时,一下子就被吸引了,原来在windows 的任务管理器中还能够让CPU舞动起来,再一次的相信了编程中仅仅有想不到没有做不到,对于书中的做法和网上的实现大致都同样.只是 ...
- java分页之页面分页
import java.util.ArrayList; import java.util.List; /** * * @author cheney * * @date Aug 31, 2012 */ ...
- C++ 函数模板与类模板(使用 Qt 开发编译环境)
注意:本文中代码均使用 Qt 开发编译环境,如有疑问和建议欢迎随时留言. 模板是 C++ 支持参数化程序设计的工具,通过它可以实现参数多态性.所谓参数多态性,就是将程序所处理的对象的类型参数化,使得一 ...
- oc79--数组的内存管理
// // main.m // 集合(数组)对象的内存管理(MRC中) // #import <Foundation/Foundation.h> #import "Person. ...
- All Discs Considered(拓扑排序)
http://poj.org/problem?id=1778 题意:有两个DVD,第一个DVD上有编号为1~n1的安装包,第二个DVD上有编号为n1+1~n1+n2的安装包,给出m组关系(a,b) 表 ...
