Network Security Threats
Network Security
- Combination of low-cost powerful computing and high-performance networks is a two-edged sword:
- Many powerful new services and applications are enabled
- But computer systems and networks become highly susceptible(敏感) to a wide variety of security threats
- Openness vs Security
- Network security involves countermeasures(对策) to protect computer systems from intruders(入侵者)
- Firewalls, security protocols, security practices, etc.
Eavesdropping
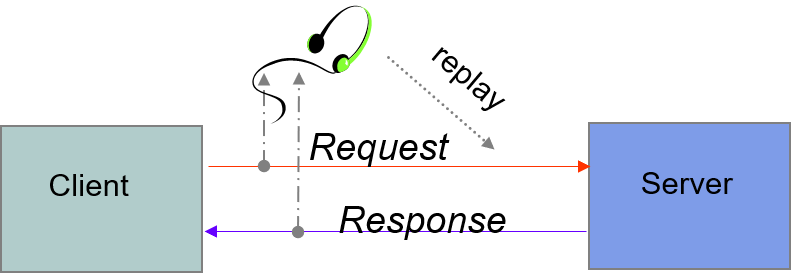
- Information transmitted over network can be observed and recorded by eavesdroppers (using a packet sniffer)
- Information can be replayed(重播) in attempts to access server
- Requirements: privacy, authentication(认证), non-repudiation(否认)
Client Imposter
client imposter(冒名顶替者)
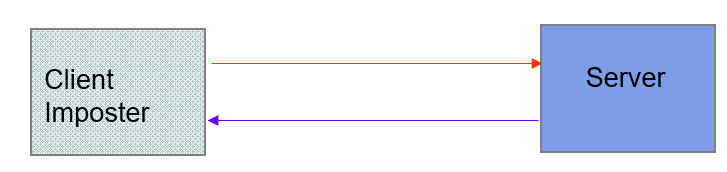
- Imposters attempt to gain unauthorized(未经授权的) access to server
- Ex. bank account or database of personal records
- For example, in IP spoofing(戏弄) imposter sends packets with false source IP address
Requirements: privacy, authentication
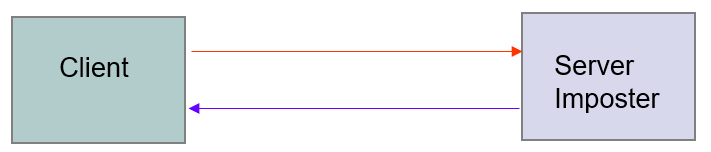
Server Imposter

- An imposter impersonates(模拟) a legitimate(合法的) server to gain sensitive information from a client
- E.g. bank account number and associated user password
- Requirements: privacy, authentication, non-repudiation
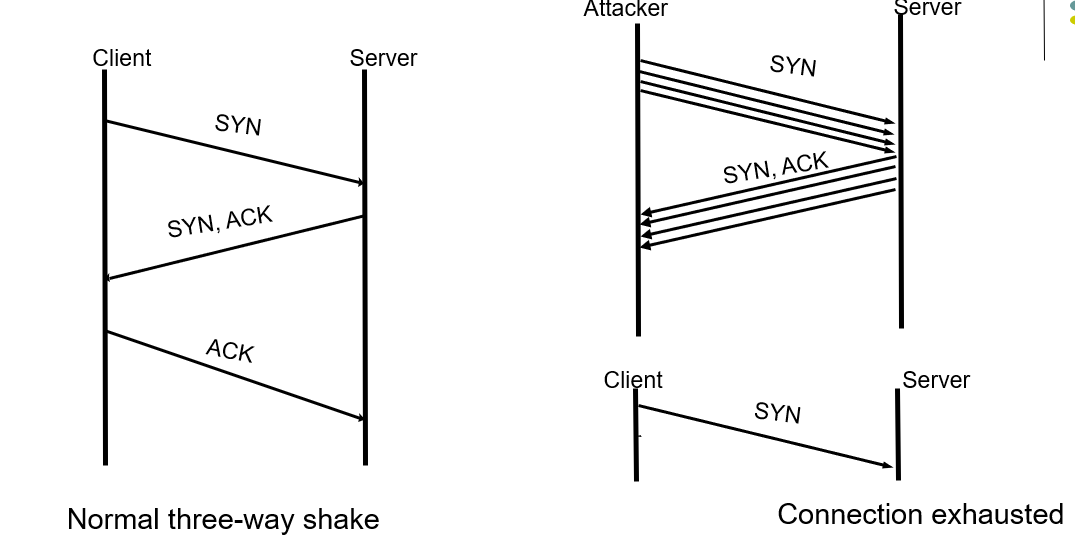
Denial of Service (DoS) Attack
- Attacker can flood a server with requests, overloading the server resources (er. TCP Three-way handshake)
- Results in denial of service to legitimate clients
- Distributed denial of service attack on a server involves coordinated attack from multiple (usually hijacked) computers
- Requirement: availability
TCP SYN Flood
- The attacker sends a repeated same packet, to every port on the target server over using a fake IP address.
- The server will send back ack continunously, prevents other client sending syn.
Man-in-the-Middle Attack

- An imposter manages to place itself as man in the middle
- convincing the server that it is legitimate client
- convincing legitimate client that it is legitimate server
- gathering sensitive information and possibly hijacking(劫持) session
- Requirements: integrity, authentication
Malicious Code
- A client becomes infected with malicious code
- Virus: code that when executed, inserts itself in other programs
- Worms: code that installs copies of itself in other machines attached to a network
- Requirements: privacy, integrity, availability
Security Requirements
Security threats motivate requirements:
- Privacy: information should be readable only by intended recipient(接受者)
- Integrity: recipient can confirm that a message has not been altered during transmission
- Authentication: it is possible to verify that sender or receiver is who he claims to be
- Non-repudiation*(不可抵赖性): sender cannot deny having sent a given message.
- Availability: of information and services
Countermeasures
- Secure communication channels
- Encryption
- Cryptographic checksums and hashes (加密校验和和散列)
- Authentication
- Digital Signatures
- Secure borders
- Firewalls
- Virus checking
- Intrusion detection(入侵检测)
- Authentication
- Access Control (访问控制)
Network Security Threats的更多相关文章
- android9.0适配HTTPS:not permitted by network security policy'
app功能接口正常,其他手机运行OK,但是在Android9.0的手机上报错 CLEARTEXT communication to 192.168.1.xx not permitted by netw ...
- Android版本28使用http请求报错not permitted by network security policy
Android版本28使用http请求报错not permitted by network security policy android模拟器调试登录的时候报错 CLEARTEXT communic ...
- 《Network Security A Decision and Game Theoretic Approach》阅读笔记
网络安全问题的背景 网络安全研究的内容包括很多方面,作者形象比喻为盲人摸象,不同领域的网络安全专家对网络安全的认识是不同的. For researchers in the field of crypt ...
- Azure PowerShell (13) 批量设置Azure ARM Network Security Group (NSG)
<Windows Azure Platform 系列文章目录> 刚刚在帮助一个合作伙伴研究需求,他们的虚拟机全面的网络安全组(Network Security Group, NSG)会经常 ...
- Network Security Services If you want to add support for SSL, S/MIME, or other Internet security standards to your application, you can use Network Security Services (NSS) to implement all your securi
Network Security Services | MDN https://developer.mozilla.org/zh-CN/docs/NSS 网络安全服务 (NSS) 是一组旨在支持支持安 ...
- Firewall & Network Security
Firewall & Network Security 防火墙 & 网络安全 NAT Gateway VPC Virtual Private Cloud refs https://en ...
- 网络安全服务(Network Security Services, NSS
网络安全服务(Network Security Services, NSS)是一套为网络安全服务而设计的库 支持支持安全的客户端和 服务器应用程序.使用NSS构建的应用程序可以支持SSL v2 和v3 ...
- Network Security final project---War Game
项目介绍: 为自己的网段设置防火墙并尝试攻击其他组 网络结构: 每组有3个机器,包含一个gateway和两个workstation,其中gateway是可以连接到其他组的gateway,但是无法连接到 ...
- Mozilla Network Security Services拒绝服务漏洞
解决办法: 运行 yum update nss yum update nss
随机推荐
- No.2一步步学习vuejs 实例demo篇
简单应用Vue.js 的核心是一个允许采用简洁的模板语法来声明式的将数据渲染进 DOM 的系统: <div id="app"> {{ message }} </d ...
- 前端定位Position属性四个值
1.static(静态定位):默认值.没有定位,元素出现在正常的流中. 2.relative(相对定位):生成相对定位的元素,通过top,bottom,left,right的设置相对于其正常(原先本身 ...
- spring的事务传播行为
1.PROPAGATION_REQUIRED:如果当前没有事务,就创建一个新事务,如果当前存在事务,就加入该事务,该设置是最常用的设置. 比如说,ServiceB.methodB的事务级别定义为PRO ...
- Cardinality Estimation算法学习(二)(Linear Counting算法、最大似然估计(MLE))
在上篇,我了解了基数的基本概念,现在进入Linear Counting算法的学习. 理解颇浅,还请大神指点! http://blog.codinglabs.org/articles/algorithm ...
- SPOJ QTREE7
题意 一棵树,每个点初始有个点权和颜色 \(0 \ u\) :询问所有\(u,v\) 路径上的最大点权,要满足\(u,v\) 路径上所有点的颜色都相同 $1 u \(:反转\)u$ 的颜色 \(2 ...
- Android 初识Retrofit
什么是 Retrofit ? Retrofit 是一套 RESTful 架构的 Android(Java) 客户端实现,基于注解,提供 JSON to POJO(Plain Ordinary Java ...
- VC++中出现错误“ error c2065 'printf' undeclared identifier”的处理方法
原文:http://blog.csdn.net/panpan639944806/article/details/20135311 有两种可能: 1.未加头文件 #include <stdio.h ...
- linux 设置git记住密码
linux下: 1.在~/下, touch创建文件 .git-credentials, 用vim编辑此文件,输入: https://{username}:{password}@github.com 注 ...
- Java API 常用 详解
Runtime类的使用:可以查看内存信息,系统变量,执行系统软件命令,备份数据库相关操作
- 【Leetcode】【Medium】Remove Duplicates from Sorted List II
Given a sorted linked list, delete all nodes that have duplicate numbers, leaving only distinct numb ...
