dfs 序
dfs序可以\(O(1)\)判断书上两个点的从属关系
Tree Queries
题面翻译
给你一个以\(1\)为根的有根树.
每回询问\(k\)个节点\({v_1, v_2 \cdots v_k}\)
求出是否有一条以根节点为一端的链使得询问的每个节点到此链的距离均\(\leq 1\).
只需输出可行性, 无需输出方案.
题目描述
You are given a rooted tree consisting of\(n\)vertices numbered from\(1\)to\(n\). The root of the tree is a vertex number\(1\).
A tree is a connected undirected graph with\(n-1\)edges.
You are given\(m\)queries. The\(i\)-th query consists of the set of\(k_i\)distinct vertices\(v_i[1], v_i[2], \dots, v_i[k_i]\). Your task is to say if there is a path from the root to some vertex\(u\)such that each of the given\(k\)vertices is either belongs to this path or has the distance\(1\)to some vertex of this path.
输入格式
The first line of the input contains two integers\(n\)and\(m\)(\(2 \le n \le 2 \cdot 10^5\),\(1 \le m \le 2 \cdot 10^5\)) — the number of vertices in the tree and the number of queries.
Each of the next\(n-1\)lines describes an edge of the tree. Edge\(i\)is denoted by two integers\(u_i\)and\(v_i\), the labels of vertices it connects\((1 \le u_i, v_i \le n, u_i \ne v_i\)).
It is guaranteed that the given edges form a tree.
The next\(m\)lines describe queries. The\(i\)-th line describes the\(i\)-th query and starts with the integer\(k_i\)(\(1 \le k_i \le n\)) — the number of vertices in the current query. Then\(k_i\)integers follow:\(v_i[1], v_i[2], \dots, v_i[k_i]\)(\(1 \le v_i[j] \le n\)), where\(v_i[j]\)is the\(j\)-th vertex of the\(i\)-th query.
It is guaranteed that all vertices in a single query are distinct.
It is guaranteed that the sum of\(k_i\)does not exceed\(2 \cdot 10^5\)(\(\sum\limits_{i=1}^{m} k_i \le 2 \cdot 10^5\)).
输出格式
For each query, print the answer — "YES", if there is a path from the root to some vertex\(u\)such that each of the given\(k\)vertices is either belongs to this path or has the distance\(1\)to some vertex of this path and "NO" otherwise.
样例 #1
样例输入 #1
10 6
1 2
1 3
1 4
2 5
2 6
3 7
7 8
7 9
9 10
4 3 8 9 10
3 2 4 6
3 2 1 5
3 4 8 2
2 6 10
3 5 4 7
样例输出 #1
YES
YES
YES
YES
NO
NO
提示
The picture corresponding to the example:
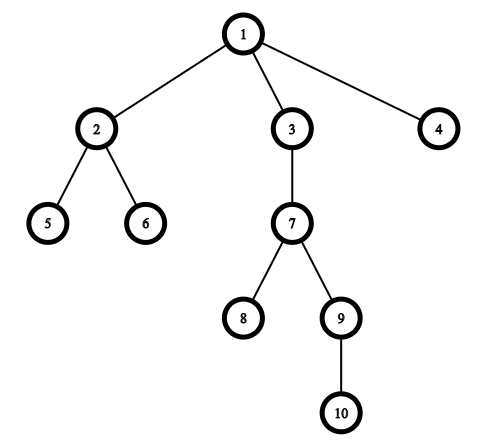
Consider the queries.
The first query is\([3, 8, 9, 10]\). The answer is "YES" as you can choose the path from the root\(1\)to the vertex\(u=10\). Then vertices\([3, 9, 10]\)belong to the path from\(1\)to\(10\)and the vertex\(8\)has distance\(1\)to the vertex\(7\)which also belongs to this path.
The second query is\([2, 4, 6]\). The answer is "YES" as you can choose the path to the vertex\(u=2\). Then the vertex\(4\)has distance\(1\)to the vertex\(1\)which belongs to this path and the vertex\(6\)has distance\(1\)to the vertex\(2\)which belongs to this path.
The third query is\([2, 1, 5]\). The answer is "YES" as you can choose the path to the vertex\(u=5\)and all vertices of the query belong to this path.
The fourth query is\([4, 8, 2]\). The answer is "YES" as you can choose the path to the vertex\(u=9\)so vertices\(2\)and\(4\)both have distance\(1\)to the vertex\(1\)which belongs to this path and the vertex\(8\)has distance\(1\)to the vertex\(7\)which belongs to this path.
The fifth and the sixth queries both have answer "NO" because you cannot choose suitable vertex\(u\).
std
#include<bits/stdc++.h>
using namespace std;
const int N = 2e5+9;
int n,m;
int h[N],ver[N<<1],ne[N<<1],idx;
int dep[N],fa[N],dfn[N],sz[N],tim;
int k[N];
void add(int u,int v)
{
idx++,ver[idx] = v,ne[idx] = h[u];h[u] = idx;
}
void dfs(int u,int pre)
{
fa[u] = pre,dfn[u] = ++tim,dep[u] = dep[pre]+1,sz[u] = 1;
for(int i = h[u];i;i= ne[i])
{
int v = ver[i];
if(v == pre)continue;
dfs(v,u);
sz[u] += sz[v];
}
}
bool cmp(int x,int y){return dep[x] > dep[y];}
int main()
{
scanf("%d%d",&n,&m);
for(int i = 1;i < n;i++)
{
int u,v;
scanf("%d%d",&u,&v);
add(u,v),add(v,u);
}
dfs(1,1);
while(m--)
{
int t;
scanf("%d",&t);
for(int i = 1;i <= t;i++)scanf("%d",&k[i]),k[i] = fa[k[i]];
sort(k+1,k+1+t,cmp);
bool flag = 1;
for(int i = 1;i < t;i++)
{
if(dfn[k[i]] > dfn[k[i+1]]+sz[k[i+1]]-1 || dfn[k[i]] < dfn[k[i+1]])
{
flag = 0;
break;
}
}
if(flag)printf("YES\n");
else printf("NO\n");
}
return 0;
}
dfs 序的更多相关文章
- BZOJ 3083: 遥远的国度 [树链剖分 DFS序 LCA]
3083: 遥远的国度 Time Limit: 10 Sec Memory Limit: 1280 MBSubmit: 3127 Solved: 795[Submit][Status][Discu ...
- BZOJ 4196: [Noi2015]软件包管理器 [树链剖分 DFS序]
4196: [Noi2015]软件包管理器 Time Limit: 10 Sec Memory Limit: 512 MBSubmit: 1352 Solved: 780[Submit][Stat ...
- BZOJ 2434: [Noi2011]阿狸的打字机 [AC自动机 Fail树 树状数组 DFS序]
2434: [Noi2011]阿狸的打字机 Time Limit: 10 Sec Memory Limit: 256 MBSubmit: 2545 Solved: 1419[Submit][Sta ...
- 【BZOJ-3779】重组病毒 LinkCutTree + 线段树 + DFS序
3779: 重组病毒 Time Limit: 20 Sec Memory Limit: 512 MBSubmit: 224 Solved: 95[Submit][Status][Discuss] ...
- 【BZOJ-1146】网络管理Network DFS序 + 带修主席树
1146: [CTSC2008]网络管理Network Time Limit: 50 Sec Memory Limit: 162 MBSubmit: 3495 Solved: 1032[Submi ...
- 【Codeforces163E】e-Government AC自动机fail树 + DFS序 + 树状数组
E. e-Government time limit per test:1 second memory limit per test:256 megabytes input:standard inpu ...
- 【BZOJ-3881】Divljak AC自动机fail树 + 树链剖分+ 树状数组 + DFS序
3881: [Coci2015]Divljak Time Limit: 20 Sec Memory Limit: 768 MBSubmit: 508 Solved: 158[Submit][Sta ...
- 2016 ACM/ICPC Asia Regional Dalian Online 1010 Weak Pair dfs序+分块
Time Limit: 4000/2000 MS (Java/Others) Memory Limit: 262144/262144 K (Java/Others)Total Submissio ...
- DFS序+线段树 hihoCoder 1381 Little Y's Tree(树的连通块的直径和)
题目链接 #1381 : Little Y's Tree 时间限制:24000ms 单点时限:4000ms 内存限制:512MB 描述 小Y有一棵n个节点的树,每条边都有正的边权. 小J有q个询问,每 ...
- 树形DP+DFS序+树状数组 HDOJ 5293 Tree chain problem(树链问题)
题目链接 题意: 有n个点的一棵树.其中树上有m条已知的链,每条链有一个权值.从中选出任意个不相交的链使得链的权值和最大. 思路: 树形DP.设dp[i]表示i的子树下的最优权值和,sum[i]表示不 ...
随机推荐
- Docker安装MySQL并使用Navicat连接
MySQL简单介绍: MySQL 是一个开放源码的关系数据库管理系统,开发者为瑞典 MySQL AB 公司.目前 MySQL 被广泛地应用在 Internet 上的大中小型网站中.由于其体积小.速度快 ...
- python的三层架构
项目目录规范 Foo/ |-- core/ # 存放业务逻辑相关代码 | |-- core.py | |-- api/ # 存放接口文件,接口主要用于为业务逻辑提供数据操作. | |-- api.py ...
- v-contextmenujs 右键菜单点击
忙碌了一晚上的"枫师傅"用上了新插件v-contextmenujs,这个插件就按照他的文档来就行 我的使用: <!-- 这里是demo.vue,之所以选择html是为了代码高 ...
- Logstash:运用 fingerprint 过滤器处理重复的文档
文章转载自:https://blog.csdn.net/UbuntuTouch/article/details/106639848 背景:Elasticsearch 索引 在介绍重复数据删除解决方案之 ...
- Elasticsearch:Index生命周期管理入门
如果您要处理时间序列数据,则不想将所有内容连续转储到单个索引中. 取而代之的是,您可以定期将数据滚动到新索引,以防止数据过大而又缓慢又昂贵. 随着索引的老化和查询频率的降低,您可能会将其转移到价格较低 ...
- Redis高并发分布式锁详解
为什么需要分布式锁 1.为了解决Java共享内存模型带来的线程安全问题,我们可以通过加锁来保证资源访问的单一,如JVM内置锁synchronized,类级别的锁ReentrantLock. 2.但是随 ...
- C#-12 转换
一 什么是转换 转换是接受一个类型的值并使用它作为另一个类型的等价值的过程. 下列代码演示了将1个short类型的值强制转换成byte类型的值. short var1 = 5; byte var2 = ...
- VScode开发STM32/GD32单片机-MakeFile工程JlinkRTT配置
本次使用开发板为STM32F401CCU6,使用CubeMX配置一个Makefile工程 配置时候为内部时钟 工程选择makefile工程类型 只生成需要的文件 用VSCode打开后显示很多波浪线 选 ...
- 代码随想录第二天| 977.有序数组的平方 ,209.长度最小的子数组 ,59.螺旋矩阵II
2022/09/22 第二天 第一题 这题我就直接平方后排序了,很无脑但很快乐啊(官方题解是双指针 第二题 滑动窗口的问题,本来我也是直接暴力求解发现在leetCode上超时,看了官方题解,也是第一次 ...
- EFCore (二)之 跟踪实体
核心 SaveChanges() "已分离"和"未改变"的实体,SaveChanges()忽略: "已添加"的实体,SaveChanges( ...
