Cert Manager 申请SSL证书流程及相关概念-二
中英文对照表
| 英文 | 英文 - K8S CRD | 中文 | 备注 |
|---|---|---|---|
| certificates | Certificate |
证书 | certificates.cert-manager.io/v1 |
| certificate issuers | Issuer |
证书颁发者 | issuers.cert-manager.io |
ClusterIssuer |
集群证书颁发者 | clusterissuers.cert-manager.io |
|
| certificate request | CertificateRequest |
证书申请 | certificaterequests.cert-manager.io |
| order | Order |
(证书)订单 | orders.acme.cert-manager.io |
| challenge | Challenge |
(证书)挑战 | challenges.acme.cert-manager.io |
| SelfSigned | 自签名 | cert-manager Issuer 的一种 | |
| CA | 证书颁发机构 | Certificate Authority 的缩写; cert-manager Issuer 的一种 |
|
| Vault | 金库 | cert-manager Issuer 的一种,即 Hashicorp Vault | |
| Venafi | Venafi 在线证书办理服务,目前用的不多。 | ||
| External | 外部 | cert-manager Issuer 的一种 | |
| ACME | 自动证书管理环境 | Automated Certificate Management Environment 的缩写; cert-manager Issuer, 包括 HTTP01 和 DNS01 |
书接上回, 接下来看一下 cert-manager 的证书申请和续期流程.
申请 SSL 证书流程
这张图显示了使用 ACME/Let's Encrypt Issuer 的名为cert-1的证书的生命周期:
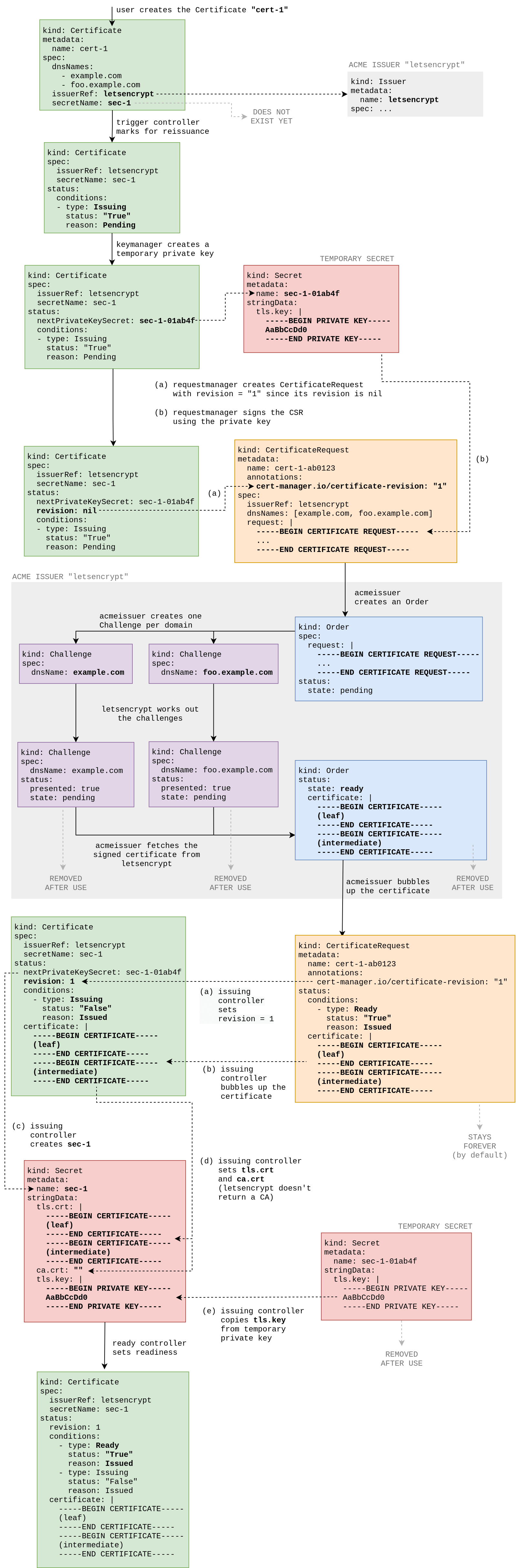
HTTP01 方式
cert-manager 可以用来从使用 ACME 协议的 CA 获得证书。ACME 协议支持各种 challenge 机制,用来证明一个域名的所有权,以便为该域名签发有效的证书。
其中一个 challenge 机制是 HTTP01 challenge。通过 HTTP01 challenge,你可以通过确保一个特定的文件存在于该域中来证明该域的所有权。如果你能够在给定的路径下发布给定的文件,就可以认为你控制了该域。
首先,配置 HTTP01 Issuer, 见上文
https://acme-v02.api.letsencrypt.org/directory 就是 Let's Encrypt 的生产环境。对应的,Staging 环境 的 URL 为:https://acme-staging-v02.api.letsencrypt.org/directory
Staging 环境不会签发可信的证书,但用来确保在转移到生产环境之前,验证过程是正常工作的。Let's Encrypt 的生产环境施加了更严格的 速率限制,所以为了减少你触及这些限制的机会,强烈建议开始时先使用暂存环境。
ACME 协议的第一阶段是由客户向 ACME 服务器注册。这个阶段包括生成一个非对称密钥对,然后将其与发件人中指定的电子邮件地址联系起来 (这里我没有填写邮箱)。请确保将这个电子邮件地址改为你自己的一个有效地址。它通常用于在你的证书即将更新时发送到期通知。生成的私钥被存储在一个名为`letsencrypt-staging'的 Secret 中。示例如下:
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
creationTimestamp: '2022-03-08T14:34:05Z'
generation: 1
labels:
app: rancher
app.kubernetes.io/managed-by: Helm
chart: rancher-2.6.4
heritage: Helm
release: rancher
name: tls-rancher-ingress
namespace: cattle-system
status:
conditions:
- lastTransitionTime: '2022-03-08T14:39:35Z'
message: Certificate is up to date and has not expired
observedGeneration: 1
reason: Ready
status: 'True'
type: Ready
notAfter: '2022-08-05T12:40:37Z'
notBefore: '2022-05-07T12:40:38Z'
renewalTime: '2022-07-06T12:40:37Z'
revision: 2
spec:
dnsNames:
- rancher.ewhisper.cn
issuerRef:
group: cert-manager.io
kind: Issuer
name: rancher
secretName: tls-rancher-ingress
usages:
- digital signature
- key encipherment
我们必须提供一个或多个 Solvers 来处理 ACME challenge。在这种情况下,我们想使用 HTTP 验证,所以我们指定了一个http01 Issuer - rancher。我们可以选择映射不同的域来使用不同的 Solver 配置。
一旦我们创建了上述发行者,我们就可以用它来获取证书。
证书资源描述了我们所需的证书以及可以用来获取证书的可能方法。如果成功获得证书,产生的密钥对将被存储在与证书相同命名空间的名为tls-rancher-ingress的 Secret 中。
该证书的 dnsname 为rancher.ewhisper.cn.
Notes
如果上面的 yaml 删除
dnsNames, 替换为commonName: ewhisper.cn,Subject Alternative Name(SAN) 将是ewhisper.cn和www.ewhisper.cn。
在我们的证书中,我们引用了上面的rancher Issuer。发行人必须与证书处于同一命名空间。如果你想引用ClusterIssuer,这是一个集群范围内的 Issuer,你必须添加kind:ClusterIssuer到 issuerRef 节中。
acme节定义了 ACME challenge 的配置。这里我们定义了 HTTP01 challenge 的配置,它将被用来验证域名所有权。为了验证 http01 节中提到的每个域的所有权,cert-manager 将创建一个 Pod、SVC 和 Ingress,暴露一个满足 HTTP01 challenge 的 HTTP 端点。
http01节中的ingress和ingressClass字段可以用来控制 cert-manager 与 Ingress 资源的交互方式。
- 如果指定了
ingress字段,那么在与证书相同的 NameSpace 中,具有相同名称的 Ingress 资源必须已经存在,它将被修改,只是为了添加适当的规则以解决 challenge 。这个字段对 ingress 控制器以及其他一些为每个 ingress 资源分配一个公共 IP 地址的控制器很有用。如果没有人工干预,创建一个新的 Ingress 资源将导致任何 challenge 失败。 - 如果指定了
ingressClass字段,将创建一个具有随机生成的名称的新入口资源,以解决 challenge 。这个新资源将有一个注释,其 key 是kubernetes.io/ingress.class值设置为ingressClass的 field. 这适用于 NGINX ingress controller 等。 - 如果两者都没有指定,新的 Ingress 资源将以随机生成的名称被创建,但它们不会有 ingressClass 注释的设置。
- 如果两者都被指定,那么
ingress字段将被优先考虑。
一旦域名所有权得到验证,任何受影响的 cert-manager 资源将被清理或删除。
注意:
你有责任将每个域名指向你的入口控制器的正确 IP 地址。(就是配置 DNS 记录的活还是需要你自己来做。)
在创建上述证书后,我们可以使用kubectl describe检查它是否已经成功获得。
$ kubectl describe certificate example-com
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal CreateOrder 57m cert-manager Created new ACME order, attempting validation...
Normal DomainVerified 55m cert-manager Domain "example.com" verified with "http-01" validation
Normal DomainVerified 55m cert-manager Domain "www.example.com" verified with "http-01" validation
Normal IssueCert 55m cert-manager Issuing certificate...
Normal CertObtained 55m cert-manager Obtained certificate from ACME server
Normal CertIssued 55m cert-manager Certificate issued successfully
你也可以用kubectl get secret tls-rancher-ingress -o yaml来检查发行是否成功。你应该看到一个 base64 编码的 TLS 密钥对。
一旦我们获得了证书,cert-manager 将定期检查它的有效性,并在它接近到期时尝试更新。当证书上的 Not After 字段小于当前时间加 30 天时,cert-manager 认为证书接近到期。
证书更新
我的证书之前已经申请到了,前几天更新的过程日志记录如下(可以对照上文的证书生命周期来看):
I0507 13:39:31.141402 1 trigger_controller.go:181] cert-manager/certificates-trigger "msg"="Certificate must be re-issued" "key"="cattle-system/tls-rancher-ingress" "message"="Renewing certificate as renewal was scheduled at 2022-05-07 13:39:31 +0000 UTC" "reason"="Renewing"
I0507 13:39:31.143437 1 conditions.go:201] Setting lastTransitionTime for Certificate "tls-rancher-ingress" condition "Issuing" to 2022-05-07 13:39:31.142484989 +0000 UTC m=+186628.212145824
I0507 13:39:31.807902 1 controller.go:161] cert-manager/certificates-key-manager "msg"="re-queuing item due to optimistic locking on resource" "key"="cattle-system/tls-rancher-ingress" "error"="Operation cannot be fulfilled on certificates.cert-manager.io \"tls-rancher-ingress\": the object has been modified; please apply your changes to the latest version and try again"
I0507 13:39:31.928746 1 conditions.go:261] Setting lastTransitionTime for CertificateRequest "tls-rancher-ingress-5j9mm" condition "Approved" to 2022-05-07 13:39:31.927475704 +0000 UTC m=+186628.997136533
I0507 13:39:32.181390 1 conditions.go:261] Setting lastTransitionTime for CertificateRequest "tls-rancher-ingress-5j9mm" condition "Ready" to 2022-05-07 13:39:32.181379458 +0000 UTC m=+186629.251040270
I0507 13:39:32.263457 1 controller.go:161] cert-manager/certificaterequests-issuer-acme "msg"="re-queuing item due to optimistic locking on resource" "key"="cattle-system/tls-rancher-ingress-5j9mm" "error"="Operation cannot be fulfilled on certificaterequests.cert-manager.io \"tls-rancher-ingress-5j9mm\": the object has been modified; please apply your changes to the latest version and try again"
I0507 13:39:41.306332 1 pod.go:71] cert-manager/challenges/http01/ensurePod "msg"="creating HTTP01 challenge solver pod" "dnsName"="rancher.ewhisper.cn" "resource_kind"="Challenge" "resource_name"="tls-rancher-ingress-5j9mm-2528720963-983401508" "resource_namespace"="cattle-system" "resource_version"="v1" "type"="HTTP-01"
I0507 13:39:41.621639 1 pod.go:59] cert-manager/challenges/http01/selfCheck/http01/ensurePod "msg"="found one existing HTTP01 solver pod" "dnsName"="rancher.ewhisper.cn" "related_resource_kind"="Pod" "related_resource_name"="cm-acme-http-solver-pglxk" "related_resource_namespace"="cattle-system" "related_resource_version"="v1" "resource_kind"="Challenge" "resource_name"="tls-rancher-ingress-5j9mm-2528720963-983401508" "resource_namespace"="cattle-system" "resource_version"="v1" "type"="HTTP-01"
I0507 13:39:41.621784 1 service.go:43] cert-manager/challenges/http01/selfCheck/http01/ensureService "msg"="found one existing HTTP01 solver Service for challenge resource" "dnsName"="rancher.ewhisper.cn" "related_resource_kind"="Service" "related_resource_name"="cm-acme-http-solver-xsqkb" "related_resource_namespace"="cattle-system" "related_resource_version"="v1" "resource_kind"="Challenge" "resource_name"="tls-rancher-ingress-5j9mm-2528720963-983401508" "resource_namespace"="cattle-system" "resource_version"="v1" "type"="HTTP-01"
E0507 13:39:41.837584 1 sync.go:186] cert-manager/challenges "msg"="propagation check failed" "error"="wrong status code '404', expected '200'" "dnsName"="rancher.ewhisper.cn" "resource_kind"="Challenge" "resource_name"="tls-rancher-ingress-5j9mm-2528720963-983401508" "resource_namespace"="cattle-system" "resource_version"="v1" "type"="HTTP-01"
I0507 13:39:42.027681 1 pod.go:59] cert-manager/challenges/http01/selfCheck/http01/ensurePod "msg"="found one existing HTTP01 solver pod" "dnsName"="rancher.ewhisper.cn" "related_resource_kind"="Pod" "related_resource_name"="cm-acme-http-solver-pglxk" "related_resource_namespace"="cattle-system" "related_resource_version"="v1" "resource_kind"="Challenge" "resource_name"="tls-rancher-ingress-5j9mm-2528720963-983401508" "resource_namespace"="cattle-system" "resource_version"="v1" "type"="HTTP-01"
I0507 13:39:42.027757 1 service.go:43] cert-manager/challenges/http01/selfCheck/http01/ensureService "msg"="found one existing HTTP01 solver Service for challenge resource" "dnsName"="rancher.ewhisper.cn" "related_resource_kind"="Service" "related_resource_name"="cm-acme-http-solver-xsqkb" "related_resource_namespace"="cattle-system" "related_resource_version"="v1" "resource_kind"="Challenge" "resource_name"="tls-rancher-ingress-5j9mm-2528720963-983401508" "resource_namespace"="cattle-system" "resource_version"="v1" "type"="HTTP-01"
I0507 13:39:42.027811 1 ingress.go:110] cert-manager/challenges/http01/selfCheck/http01/ensureIngress "msg"="multiple challenge solver ingresses found for challenge. cleaning up all existing ingresses." "dnsName"="rancher.ewhisper.cn" "resource_kind"="Challenge" "resource_name"="tls-rancher-ingress-5j9mm-2528720963-983401508" "resource_namespace"="cattle-system" "resource_version"="v1" "type"="HTTP-01"
E0507 13:39:42.076190 1 controller.go:102] ingress 'cattle-system/cm-acme-http-solver-knwm8' in work queue no longer exists
E0507 13:39:42.100492 1 controller.go:102] ingress 'cattle-system/cm-acme-http-solver-59gvf' in work queue no longer exists
E0507 13:39:42.101020 1 sync.go:186] cert-manager/challenges "msg"="propagation check failed" "error"="multiple existing challenge solver ingresses found and cleaned up. retrying challenge sync" "dnsName"="rancher.ewhisper.cn" "resource_kind"="Challenge" "resource_name"="tls-rancher-ingress-5j9mm-2528720963-983401508" "resource_namespace"="cattle-system" "resource_version"="v1" "type"="HTTP-01"
...
E0507 13:40:22.187779 1 sync.go:386] cert-manager/challenges/acceptChallenge "msg"="error waiting for authorization" "error"="context deadline exceeded" "dnsName"="rancher.ewhisper.cn" "resource_kind"="Challenge" "resource_name"="tls-rancher-ingress-5j9mm-2528720963-983401508" "resource_namespace"="cattle-system" "resource_version"="v1" "type"="HTTP-01"
E0507 13:40:22.188198 1 controller.go:163] cert-manager/challenges "msg"="re-queuing item due to error processing" "error"="context deadline exceeded" "key"="cattle-system/tls-rancher-ingress-5j9mm-2528720963-983401508"
I0507 13:40:27.188948 1 pod.go:59] cert-manager/challenges/http01/selfCheck/http01/ensurePod "msg"="found one existing HTTP01 solver pod" "dnsName"="rancher.ewhisper.cn" "related_resource_kind"="Pod" "related_resource_name"="cm-acme-http-solver-pglxk" "related_resource_namespace"="cattle-system" "related_resource_version"="v1" "resource_kind"="Challenge" "resource_name"="tls-rancher-ingress-5j9mm-2528720963-983401508" "resource_namespace"="cattle-system" "resource_version"="v1" "type"="HTTP-01"
I0507 13:40:27.190011 1 service.go:43] cert-manager/challenges/http01/selfCheck/http01/ensureService "msg"="found one existing HTTP01 solver Service for challenge resource" "dnsName"="rancher.ewhisper.cn" "related_resource_kind"="Service" "related_resource_name"="cm-acme-http-solver-xsqkb" "related_resource_namespace"="cattle-system" "related_resource_version"="v1" "resource_kind"="Challenge" "resource_name"="tls-rancher-ingress-5j9mm-2528720963-983401508" "resource_namespace"="cattle-system" "resource_version"="v1" "type"="HTTP-01"
I0507 13:40:27.190749 1 ingress.go:98] cert-manager/challenges/http01/selfCheck/http01/ensureIngress "msg"="found one existing HTTP01 solver ingress" "dnsName"="rancher.ewhisper.cn" "related_resource_kind"="Ingress" "related_resource_name"="cm-acme-http-solver-cmp2c" "related_resource_namespace"="cattle-system" "related_resource_version"="v1" "resource_kind"="Challenge" "resource_name"="tls-rancher-ingress-5j9mm-2528720963-983401508" "resource_namespace"="cattle-system" "resource_version"="v1" "type"="HTTP-01"
E0507 13:40:38.478817 1 controller.go:102] ingress 'cattle-system/cm-acme-http-solver-cmp2c' in work queue no longer exists
I0507 13:40:39.806118 1 acme.go:209] cert-manager/certificaterequests-issuer-acme/sign "msg"="certificate issued" "related_resource_kind"="Order" "related_resource_name"="tls-rancher-ingress-5j9mm-2528720963" "related_resource_namespace"="cattle-system" "related_resource_version"="v1" "resource_kind"="CertificateRequest" "resource_name"="tls-rancher-ingress-5j9mm" "resource_namespace"="cattle-system" "resource_version"="v1"
I0507 13:40:39.809106 1 conditions.go:250] Found status change for CertificateRequest "tls-rancher-ingress-5j9mm" condition "Ready": "False" -> "True"; setting lastTransitionTime to 2022-05-07 13:40:39.809091738 +0000 UTC m=+186696.878752561
I0507 13:40:40.068059 1 controller.go:161] cert-manager/certificates-issuing "msg"="re-queuing item due to optimistic locking on resource" "key"="cattle-system/tls-rancher-ingress" "error"="Operation cannot be fulfilled on certificates.cert-manager.io \"tls-rancher-ingress\": the object has been modified; please apply your changes to the latest version and try again"
I0507 13:40:40.168307 1 controller.go:161] cert-manager/certificates-key-manager "msg"="re-queuing item due to optimistic locking on resource" "key"="cattle-system/tls-rancher-ingress" "error"="Operation cannot be fulfilled on certificates.cert-manager.io \"tls-rancher-ingress\": the object has been modified; please apply your changes to the latest version and try again"
E0507 13:40:41.298717 1 sync.go:70] cert-manager/orders "msg"="failed to update status" "error"=null "resource_kind"="Order" "resource_name"="tls-rancher-ingress-5j9mm-2528720963" "resource_namespace"="cattle-system" "resource_version"="v1"
I0507 13:40:41.299059 1 controller.go:161] cert-manager/orders "msg"="re-queuing item due to optimistic locking on resource" "key"="cattle-system/tls-rancher-ingress-5j9mm-2528720963" "error"="Operation cannot be fulfilled on orders.acme.cert-manager.io \"tls-rancher-ingress-5j9mm-2528720963\": the object has been modified; please apply your changes to the latest version and try again"
E0507 13:40:41.331531 1 controller.go:211] cert-manager/challenges "msg"="challenge in work queue no longer exists" "error"="challenge.acme.cert-manager.io \"tls-rancher-ingress-5j9mm-2528720963-983401508\" not found"
cert-manager/certificates-trigger触发证书 renew(Certificate里有一个renewalTime字段记录该时间)tls-rancher-ingress证书的状态变为"Issuing"创建了一个新的
CertificateRequest-tls-rancher-ingress-5j9mm, 状态变为"Approved", 具体内容如下:apiVersion: cert-manager.io/v1
kind: CertificateRequest
metadata:
annotations:
cert-manager.io/certificate-name: tls-rancher-ingress
cert-manager.io/certificate-revision: '2'
cert-manager.io/private-key-secret-name: tls-rancher-ingress-nttqs
creationTimestamp: '2022-05-07T13:39:31Z'
generateName: tls-rancher-ingress-
generation: 1
name: tls-rancher-ingress-5j9mm
namespace: cattle-system
ownerReferences:
- apiVersion: cert-manager.io/v1
blockOwnerDeletion: true
controller: true
kind: Certificate
name: tls-rancher-ingress
resourceVersion: '20868343'
status:
certificate: >-
...
conditions:
- lastTransitionTime: '2022-05-07T13:39:31Z'
message: Certificate request has been approved by cert-manager.io
reason: cert-manager.io
status: 'True'
type: Approved
- lastTransitionTime: '2022-05-07T13:40:39Z'
message: Certificate fetched from issuer successfully
reason: Issued
status: 'True'
type: Ready
spec:
extra:
authentication.kubernetes.io/pod-name:
- cert-manager-6d6bb4f487-525q9
authentication.kubernetes.io/pod-uid:
- 857565c8-b05c-4114-8e94-14960476f90e
groups:
- system:serviceaccounts
- system:serviceaccounts:cert-manager
- system:authenticated
issuerRef:
group: cert-manager.io
kind: Issuer
name: rancher
request: >-
<-----BEGIN CERTIFICATE REQUEST-----... 的 base64 编码>
usages:
- digital signature
- key encipherment
username: system:serviceaccount:cert-manager:cert-manager
CertificateRequest-tls-rancher-ingress-5j9mm, 的状态变为"Ready"创建 HTTP01 challenge solver pod -
"resource_kind"="Challenge" "resource_name"="tls-rancher-ingress-5j9mm-2528720963-983401508"前几次 challenge 失败,404:
"msg"="propagation check failed" "error"="wrong status code '404', expected '200'"经过多次,最终成功:
"msg"="certificate issued" "related_resource_kind"="Order"(开始renew 后, 创建完CertificateRequest就开始创建Order)Found status change for CertificateRequest "tls-rancher-ingress-5j9mm" condition "Ready": "False" -> "True"; setting lastTransitionTime to 2022-05-07 13:40:39.809091738 +0000 UTC m=+186696.878752561
成功后,Challenge 被删除,Order 的状态变为 valid, 如下:
apiVersion: acme.cert-manager.io/v1
kind: Order
metadata:
annotations:
cert-manager.io/certificate-name: tls-rancher-ingress
cert-manager.io/certificate-revision: '2'
cert-manager.io/private-key-secret-name: tls-rancher-ingress-nttqs
creationTimestamp: '2022-05-07T13:39:32Z'
name: tls-rancher-ingress-5j9mm-2528720963
namespace: cattle-system
status:
authorizations:
- challenges:
- token: WkoIW-...
type: http-01
url: >-
https://acme-v02.api.letsencrypt.org/acme/chall-v3/.../...
- token: WkoIW-...
type: dns-01
url: >-
https://acme-v02.api.letsencrypt.org/acme/chall-v3/.../...
- token: WkoIW-...
type: tls-alpn-01
url: >-
https://acme-v02.api.letsencrypt.org/acme/chall-v3/.../...
identifier: rancher.ewhisper.cn
initialState: pending
url: https://acme-v02.api.letsencrypt.org/acme/authz-v3/...
wildcard: false
certificate: >-
...
finalizeURL: https://acme-v02.api.letsencrypt.org/acme/finalize/.../...
state: valid
url: https://acme-v02.api.letsencrypt.org/acme/order/.../...
spec:
dnsNames:
- rancher.ewhisper.cn
issuerRef:
group: cert-manager.io
kind: Issuer
name: rancher
request: >-
...
最终 Certificate 的状态也发生更新,新的证书更新进对应的 Secret 中。如下:
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
name: tls-rancher-ingress
namespace: cattle-system
status:
notAfter: '2022-08-05T12:40:37Z'
notBefore: '2022-05-07T12:40:38Z'
renewalTime: '2022-07-06T12:40:37Z'
revision: 2
...
DNS01 方式
cert-manager 可以用来从使用 ACME 协议的 CA 获得证书。ACME 协议支持各种 challenge 机制,用来证明一个域名的所有权,以便为该域名签发有效的证书。
其中一个 challenge 机制是 DNS01。通过 DNS01 challenge ,你可以通过证明你控制了一个域名的 DNS 记录来证明它的所有权。这是通过创建一个具有特定内容的 TXT 记录来实现的,该记录证明你对该域名的 DNS 记录有控制权。
之前的 Issuer 定义了启用 DNS 验证的一些必要信息。指定的还是 Let's Encrypt 的生产环境:https://acme-v02.api.letsencrypt.org/directory
dns01 字段包含一个 DNS01 提供者的列表,可用于解决 DNS challenge。这里我只定义了一个 webhook 实现的提供者 - dnspod。
只要我们创建了上述发行者,我们就可以用它来获得证书:
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
name: ewhisper-crt
namespace: cert-manager
spec:
dnsNames:
- ewhisper.cn
- '*.ewhisper.cn'
issuerRef:
group: cert-manager.io
kind: ClusterIssuer
name: dnspod
secretName: ewhisper-crt-secret
证书 CRD 描述了我们所需的证书以及可以用来获取证书的可能方法。你可以像其他域名一样获得通配符域名的证书。请确保在你的 YAML 资源中用星号包裹通配符域名,以避免格式问题。这里我在同一个证书上同时指定ewhisper.cn和*.ewhisper.cn,那么执行验证的时间会稍微长一些,因为每个域名必须一个一个地被验证。
Thinking:
我的通配符证书,在 2022.4.30 开始更新,然后直到 2022.5.8 才更新成功,不知道是不是因为这个原因。
如果成功获得证书,产生的密钥对将被存储在与证书相同命名空间的名为ewhisper-crt-secret的 Secret 中。
该证书的通用名称为*.ewhisper.cn。
在我们的证书中,我们引用了上面的dnspod ClusterIssuer, 这种情况下 Issuer 可以与证书不处于同一命名空间。
acme 节定义了我们的 ACME challenge 的配置。这里我们定义了 DNS challenge 的配置,它将被用来验证域名所有权。对于dns01节中提到的每个域名,cert-manager 将使用被引用的 Issue 的提供者的证书来创建一个名为_acme-challenge的 TXT 记录。这条记录将由 ACME 服务器验证,以便签发证书。一旦域名所有权被验证,任何受 cert-manager 影响的记录都将被清理掉。
DNS 服务器我用的是 DNSPod, 这里创建 TXT 的记录如下:
2022-05-08 19:05:39: (<my-public-ip>) 删除记录 TXT 记录 默认 线路 _acme-challenge 值 mfaEFIBPUFzh1ub7Ek05v-bN-fwsdfwdfwdfwedw (1117684179) Uin:<my-uin> Real Client IP:<my-public-ip> API FROM:YUNAPI
2022-05-08 19:04:27: (<my-public-ip>) 添加 TXT 记录 默认 线路 _acme-challenge 值 mfaEFIBPUFzh1ub7Ek05v-bN-fwsdfwdfwdfwedw (1117684179) Uin:<my-uin> Real Client IP:<my-public-ip> API FROM:YUNAPI
2022-05-08 19:04:26: (<my-public-ip>) 删除记录 TXT 记录 默认 线路 _acme-challenge 值 cVxv2s9P_UvThEB2DLcZxfwdfwdfwdwds8Ogv_k (1117683586) Uin:<my-uin> Real Client IP:<my-public-ip> API FROM:YUNAPI
2022-05-08 19:03:12: (<my-public-ip>) 添加 TXT 记录 默认 线路 _acme-challenge 值 cVxv2s9P_UvThEB2DLcZxfwdfwdfwdwds8Ogv_k (1117683586) Uin:<my-uin> Real Client IP:<my-public-ip> API FROM:YUNAPI
2022-05-08 18:04:21: (<my-public-ip>) 删除记录 TXT 记录 默认 线路 _acme-challenge 值 QYLKuSmlK6aWmD64hhExOwdfwdfwdfwdcwdk5bfRCLAI (1117656075) Uin:<my-uin> Real Client IP:<my-public-ip> API FROM:YUNAPI
2022-05-08 18:03:07: (<my-public-ip>) 添加 TXT 记录 默认 线路 _acme-challenge 值 QYLKuSmlK6aWmD64hhExOwdfwdfwdfwdcwdk5bfRCLAI (1117656075) Uin:<my-uin> Real Client IP:<my-public-ip> API FROM:YUNAPI
其他方面就和 HTTP01 是类似的,这里不再做过多的说明。
在这里,用的是 <imroc.cc> 开发的 cert-manager 插件 - cert-manager-webhook-dnspod.
参考的是 这篇文章配置的 dnspod 的 cert-manager webhook
结合上面的流程, 下面来了解一下 cert-manager 的相关概念
系列文章
️ 参考文档
- cert-manager - cert-manager Documentation
- 使用 cert-manager 为 dnspod 的域名签发免费证书 | kubernetes 学习笔记 (imroc.cc)
Cert Manager 申请SSL证书流程及相关概念-二的更多相关文章
- Cert Manager 申请 SSL 证书流程及相关概念 - 一
2022.3.9 用 cert-manager 申请成功通配符证书 (*.ewhisper.cn), 2022.4.30 该证书距离过期还有 30 天,cert-manager 进行自动续期,但是却失 ...
- Cert Manager 申请SSL证书流程及相关概念-三
中英文对照表 英文 英文 - K8S CRD 中文 备注 certificates Certificate 证书 certificates.cert-manager.io/v1 certificate ...
- 【原创】免费申请SSL证书【用于HTTPS,即是把网站从HTTP改为HTTPS,加密传输数据,保护敏感数据】
今天公司有个网站需要改用https访问,所以就用到SSL证书.由于沃通(以前我是在这里申请的)暂停了免费的SSL证书之后,其网站推荐了新的一个网站来申请证书,所以,今天因为刚好又要申请一个证书,所以, ...
- 阿里云申请ssl证书配置tomcat访问https
首先去阿里云上面申请ssl证书,免费的,自己百度去. 申请完ok之后会让你下载一个压缩包,里面有四个文件. 在tomcat安装目录下创建cert文件夹,把这四个文件扔进去 在conf/server.x ...
- 使用acme.sh从Let's Encrypt申请SSL证书
Let's Encrypt 简介 Let's Encrypt是一个于2015年三季度推出的数字证书认证机构,旨在以自动化流程消除手动创建和安装证书的复杂流程,并推广使万维网服务器的加密连接无所不在,为 ...
- 超详细网站博客域名和二级域名、子域名升级HTTPS免费申请SSL证书配置nginx指南
随着互联网的飞速发展,我们的工作生活已经离不开互联网,HTTP虽然使用极为广泛, 但是存在不小的安全缺陷, 主要是其数据的明文传送和消息完整性检测的缺乏, 而这两点恰好是网络支付,网络交易等网站应用中 ...
- .io域名在申请SSL证书时被坑
注:标题其实与最后内容不符,只是描述一个事实 - 遇到坑了,不代表观点 - io域名坑我. .io后缀的域名是英属印度洋领地的国别域名,由NIC.io(runby Internet Computer ...
- 申请ssl证书报提示caa提示
申请ssl证书报下面提示caa提示,这和dns有关,换一组dns重新申请 send challenge err[acme error 'urn:acme:error:connection': DNS ...
- 腾讯云域名申请+ssl证书申请+springboot配置https
阿里云域名申请 域名申请比较简单,使用微信注册阿里云账号并登陆,点击产品,选择域名注册 输入你想注册的域名 进入域名购买页面,搜索可用的后缀及价格,越热门的后缀(.com,.cn)越贵一般,并且很可能 ...
- 申请SSL证书
1.为什么需要申请SSL证书呢? 因为之前公司网站是通过http访问的,现在要通过https方式访问,前面多了一个s,那就需要SSL证书,用https方式访问的,会加密用户上传和下载的数据,使访问更加 ...
随机推荐
- D3.js 力导向图的显示优化(二)- 自定义功能
摘要: 在本文中,我们将借助 D3.js 的灵活性这一优势,去新增一些 D3.js 本身并不支持但我们想要的一些常见的功能:Nebula Graph 图探索的删除节点和缩放功能. 文章首发于 Nebu ...
- mysql找出不包含某些关键字的结果
比如公司业务是和房产相关的,但是库里存在和房产不相关的内容时就需要筛选并删除. 如何筛选才能不误伤呢? 这是我的一个初步的SQL: 意思是如果name.desc字段都不包含房.盘.楼.地产关键字才找出 ...
- C1. Good Subarrays (Easy Version)
思路:我们枚举每一个左端点,对于每一个左端点,寻找最长的满足条件的区间,这个区间长度就是左端点对答案的贡献,可以发现具有单调性,右端点只会前进不会倒退.所以我们两个指针各扫一遍区间就可以. #incl ...
- 上来就对标 20k Star 的开源项目,是自不量力还是后起之秀?
先来一段紧箍咒:nvm.fvm.gvm.sdkman.fnm.n.g.rvm.jenv.phpbrew.rustup.swiftenv.pyenv.rbenv... 这些都是用来解决编程语言多版本管理 ...
- Python函数对象与闭包函数
[一]函数对象 函数对象指的是函数可以被当做 数据 来处理,具体可以分为四个方面的使用 [1]函数可以被引用 def add(x,y): return x + y func = add res = f ...
- python 生成虚拟环境requirement.txt
# 在项目根目录中,打开终端执行以下命令 # 生成 requirements.txt 文件 pip3 freeze > requirements.txt # 安装依赖文件 pip3 instal ...
- 一文搞懂Vue的MVVM模式与双向绑定
v-model 是 Vue.js 框架中用于实现双向数据绑定的指令.它充分体现了 MVVM(Model-View-ViewModel)模式中的双向数据绑定特性.下面我们将详细解释 v-model 如何 ...
- vscode 注释后 光标下移(注释后光标快速定位下一行) 仿照idea
VSCode 注释后光标快速定位下一行 1. 安装插件 Multi-command Multi-command 2.打开 Keybinding.json Keybinding.json 左下角齿轮图标 ...
- linux 无法找到“/usr/bin/core_perl/gcc” vscode
解决问题的思路 查看有没有gcc,没有安装 有的话就是,修改安装路径就可以? "/usr/bin/core_perl/gcc".修改成Gcc的绝对路径 我的修改是./usr/bin ...
- SpringMVC异常之The request sent by the client was syntactically incorrect解决方案
最近在做SpringMVC开发的时候,直接访问后台的controller,出现如下异常 这个问题是什么原因造成的呢? 后来经过测试发现,是表单提交的内容数据类型与实体的(也就是数据表字段)的数据类型不 ...
